mirror of
https://github.com/ChristianLempa/boilerplates.git
synced 2025-01-12 17:28:55 +01:00
some general updates
This commit is contained in:
parent
2b925bf08e
commit
0083bc01a1
0
docker-compose/authelia/README.md
Normal file
0
docker-compose/authelia/README.md
Normal file
22
docker-compose/authelia/docker-compose.yml
Normal file
22
docker-compose/authelia/docker-compose.yml
Normal file
@ -0,0 +1,22 @@
|
||||
version: '3'
|
||||
|
||||
services:
|
||||
authelia:
|
||||
image: authelia/authelia
|
||||
container_name: authelia
|
||||
volumes:
|
||||
- /etc/authelia:/config
|
||||
labels:
|
||||
- 'traefik.enable=true'
|
||||
- 'traefik.http.routers.authelia.rule=Host(`authelia.example.com`)'
|
||||
- 'traefik.http.routers.authelia.entrypoints=https'
|
||||
- 'traefik.http.routers.authelia.tls=true'
|
||||
# - 'traefik.http.routers.authelia.tls.certresolver=letsencrypt'
|
||||
- 'traefik.http.middlewares.authelia.forwardauth.address=http://authelia:9091/api/verify?rd=https://authelia.example.com' # yamllint disable-line rule:line-length
|
||||
- 'traefik.http.middlewares.authelia.forwardauth.trustForwardHeader=true'
|
||||
- 'traefik.http.middlewares.authelia.forwardauth.authResponseHeaders=Remote-User,Remote-Groups,Remote-Name,Remote-Email' # yamllint disable-line rule:line-length
|
||||
expose:
|
||||
- 9091
|
||||
restart: unless-stopped
|
||||
healthcheck:
|
||||
disable: true
|
||||
3
docker-compose/grafana/README.md
Normal file
3
docker-compose/grafana/README.md
Normal file
@ -0,0 +1,3 @@
|
||||
## tmp
|
||||
|
||||
Grafana default username and password: `admin`
|
||||
15
docker-compose/grafana/docker-compose.yml
Normal file
15
docker-compose/grafana/docker-compose.yml
Normal file
@ -0,0 +1,15 @@
|
||||
version: '3'
|
||||
|
||||
volumes:
|
||||
grafana-data:
|
||||
driver: local
|
||||
|
||||
services:
|
||||
grafana:
|
||||
image: grafana/grafana-oss:latest
|
||||
container_name: grafana
|
||||
ports:
|
||||
- "3000:3000"
|
||||
volumes:
|
||||
- grafana-data:/var/lib/grafana
|
||||
restart: unless-stopped
|
||||
0
docker-compose/influxdb/README.md
Normal file
0
docker-compose/influxdb/README.md
Normal file
0
docker-compose/influxdb/docker-compose.yml
Normal file
0
docker-compose/influxdb/docker-compose.yml
Normal file
34
docker-compose/portainer/README.md
Normal file
34
docker-compose/portainer/README.md
Normal file
@ -0,0 +1,34 @@
|
||||
# Installing
|
||||
|
||||
## Manage local environment
|
||||
|
||||
Allows Portainer to manage the local Docker Environment
|
||||
|
||||
```yaml
|
||||
volumes:
|
||||
- /var/run/docker.sock:/var/run/docker.sock
|
||||
```
|
||||
|
||||
## Data Persistence
|
||||
|
||||
Storing Data in a `portainer-data` volume on docker
|
||||
|
||||
```yaml
|
||||
volumes:
|
||||
- portainer-data:/data
|
||||
```
|
||||
|
||||
# Best-Practices
|
||||
|
||||
### (Option 1): Upload custom certificates
|
||||
|
||||
- [ ] Upload your custom certificates
|
||||
- [ ] Force HTTPS only
|
||||
- [ ] Expose Port `9443`
|
||||
|
||||
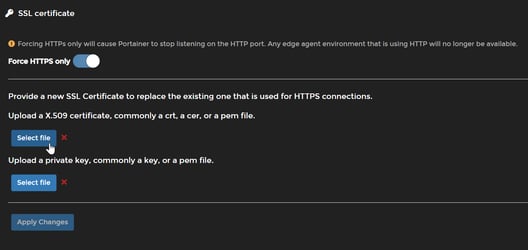
|
||||
|
||||
|
||||
### (Option 2): Use a Reverse Proxy
|
||||
|
||||
Use a Reverse Proxy to securely expose administrative services.
|
||||
@ -2,10 +2,12 @@ version: '3'
|
||||
|
||||
services:
|
||||
app:
|
||||
container_name: portainer
|
||||
image: 'portainer/portainer-ce:latest'
|
||||
ports:
|
||||
- '9000:9000'
|
||||
- '9443:9443'
|
||||
- '8000:8000'
|
||||
volumes:
|
||||
- /var/run/docker.sock:/var/run/docker.sock
|
||||
- /AmberPro/portainer/data:/data
|
||||
- portainer-data:/data
|
||||
|
||||
0
docker-compose/prometheus/README.md
Normal file
0
docker-compose/prometheus/README.md
Normal file
18
docker-compose/prometheus/docker-compose.yml
Normal file
18
docker-compose/prometheus/docker-compose.yml
Normal file
@ -0,0 +1,18 @@
|
||||
version: '3'
|
||||
|
||||
volumes:
|
||||
prometheus-data:
|
||||
driver: local
|
||||
|
||||
services:
|
||||
prometheus:
|
||||
image: prom/prometheus:latest
|
||||
container_name: prometheus
|
||||
ports:
|
||||
- "9090:9090"
|
||||
volumes:
|
||||
- /etc/prometheus:/etc/prometheus
|
||||
- prometheus-data:/prometheus
|
||||
restart: unless-stopped
|
||||
command:
|
||||
- "--config.file=/etc/prometheus/prometheus.yml"
|
||||
@ -0,0 +1,37 @@
|
||||
# Installing
|
||||
|
||||
|
||||
# Customization
|
||||
|
||||
## Data Persistence
|
||||
... Storing Data in the `/etc/traefik` directory on the host, passing through...
|
||||
```yaml
|
||||
volumes:
|
||||
- /etc/traefik:/etc/traefik
|
||||
```
|
||||
|
||||
## Self-Signed Certificates
|
||||
According to traefik's documentation it will automatically generate self-signed Certificates if no Default Certificate is provided. If you'd like to overwrite the self-signed Certificate with your own, uncomment the section for
|
||||
```yaml
|
||||
# (Optional) Overwrite Default Certificates
|
||||
tls:
|
||||
stores:
|
||||
default:
|
||||
defaultCertificate:
|
||||
certFile: /etc/traefik/certs/cert.pem
|
||||
keyFile: /etc/traefik/certs/cert-key.pem
|
||||
```
|
||||
Replace the `/etc/traefik/certs/cert.pem` with your certificate file, and the `/etc/traefik/certs/cert-key.pem` with your certificate key.
|
||||
|
||||
|
||||
# Best-Practices
|
||||
|
||||
```yaml
|
||||
providers:
|
||||
docker:
|
||||
exposedByDefault: false # Default is true
|
||||
file:
|
||||
# watch for dynamic configuration changes
|
||||
directory: /etc/traefik
|
||||
watch: true
|
||||
```
|
||||
Loading…
Reference in New Issue
Block a user