mirror of
https://github.com/ChristianLempa/boilerplates.git
synced 2025-02-22 13:30:47 +01:00
formatting update
This commit is contained in:
parent
907b39f549
commit
0c30f62cbe
@ -1 +0,0 @@
|
||||
TODO: #14 Insert Authelia Readme
|
||||
@ -1 +0,0 @@
|
||||
# TODO: ...
|
||||
@ -1,26 +0,0 @@
|
||||
version: '3'
|
||||
|
||||
networks:
|
||||
frontend:
|
||||
external: true
|
||||
|
||||
services:
|
||||
authelia:
|
||||
image: authelia/authelia
|
||||
container_name: authelia
|
||||
volumes:
|
||||
- /etc/authelia:/config
|
||||
labels:
|
||||
- 'traefik.enable=true'
|
||||
- 'traefik.http.routers.authelia.rule=Host(`your-domain.com`)'
|
||||
- 'traefik.http.routers.authelia.entrypoints=websecure'
|
||||
- 'traefik.http.routers.authelia.tls=true'
|
||||
- 'traefik.http.middlewares.authelia.forwardauth.address=http://authelia:9091/api/verify?rd=https://your-domain.com' # yamllint disable-line rule:line-length
|
||||
- 'traefik.http.middlewares.authelia.forwardauth.trustForwardHeader=true'
|
||||
- 'traefik.http.middlewares.authelia.forwardauth.authResponseHeaders=Remote-User,Remote-Groups,Remote-Name,Remote-Email' # yamllint disable-line rule:line-length
|
||||
expose:
|
||||
- 9091
|
||||
restart: unless-stopped
|
||||
healthcheck:
|
||||
disable: true
|
||||
|
||||
@ -1,5 +1,4 @@
|
||||
version: '3'
|
||||
|
||||
---
|
||||
services:
|
||||
bind9:
|
||||
image: ubuntu/bind9:latest
|
||||
@ -10,4 +9,4 @@ services:
|
||||
- /etc/bind/:/etc/bind/
|
||||
- /var/cache/bind:/var/cache/bind
|
||||
- /var/lib/bind:/var/lib/bind
|
||||
restart: unless-stopped
|
||||
restart: unless-stopped
|
||||
@ -1,10 +1,7 @@
|
||||
---
|
||||
version: '3'
|
||||
|
||||
services:
|
||||
cadvisor:
|
||||
# TODO: latest tag is not updated, check latest release https://github.com/google/cadvisor/releases
|
||||
image: gcr.io/cadvisor/cadvisor:v0.45.0
|
||||
image: gcr.io/cadvisor/cadvisor:v0.47.0
|
||||
container_name: cadvisor
|
||||
ports:
|
||||
- "8080:8080"
|
||||
@ -17,5 +14,5 @@ services:
|
||||
- /dev/disk/:/dev/disk:ro
|
||||
devices:
|
||||
- /dev/kmsg
|
||||
restart: unless-stopped
|
||||
privileged: true
|
||||
privileged: true
|
||||
restart: unless-stopped
|
||||
@ -1 +0,0 @@
|
||||
TODO: #16 Insert Duplicati Readme and backup scripts
|
||||
@ -1,8 +1,5 @@
|
||||
---
|
||||
version: '2.1'
|
||||
|
||||
services:
|
||||
|
||||
duplicati:
|
||||
image: ghcr.io/linuxserver/duplicati
|
||||
container_name: duplicati
|
||||
@ -1,25 +0,0 @@
|
||||
# Installation
|
||||
|
||||
## Deployment
|
||||
|
||||
Copy the `docker-compose.yml` template into your project folder and start the container.
|
||||
|
||||
## Configuration
|
||||
|
||||
Visit the Grafana Web Interface `http://localhost:3000`, and login with Grafana's default username and password: `admin`.
|
||||
|
||||
*For more info visit:* [Official Grafana Getting started Documentation](https://grafana.com/docs/grafana/latest/getting-started/getting-started/)
|
||||
|
||||
# Best-Practices & Post-Installation
|
||||
|
||||
## Disable HTTP
|
||||
|
||||
It's not secure to expose Grafana via the HTTP protocol.
|
||||
|
||||
### Use a Reverse Proxy
|
||||
|
||||
- [ ] Use a Reverse Proxy to securely expose administrative services.
|
||||
|
||||
# Additional Referfences
|
||||
|
||||
[Official Grafana Documentation](https://grafana.com/docs/grafana/latest/)
|
||||
@ -1,9 +1,7 @@
|
||||
version: '3'
|
||||
|
||||
---
|
||||
volumes:
|
||||
grafana-data:
|
||||
driver: local
|
||||
|
||||
services:
|
||||
grafana:
|
||||
image: grafana/grafana-oss:latest
|
||||
@ -12,4 +10,4 @@ services:
|
||||
- "3000:3000"
|
||||
volumes:
|
||||
- grafana-data:/var/lib/grafana
|
||||
restart: unless-stopped
|
||||
restart: unless-stopped
|
||||
@ -1,8 +1,7 @@
|
||||
---
|
||||
version: "2.1"
|
||||
services:
|
||||
heimdall:
|
||||
image: lscr.io/linuxserver/heimdall:latest
|
||||
image: lscr.io/linuxserver/heimdall:2.5.6
|
||||
container_name: heimdall
|
||||
environment:
|
||||
- PUID=1000
|
||||
@ -12,4 +11,4 @@ services:
|
||||
ports:
|
||||
- 80:80
|
||||
- 443:443
|
||||
restart: unless-stopped
|
||||
restart: unless-stopped
|
||||
@ -1,26 +0,0 @@
|
||||
# Installation
|
||||
|
||||
## Deployment
|
||||
|
||||
1. Copy the configuration file from the `assets` folder into your project's asset folder.
|
||||
2. Copy the `docker-compose.yml` template into your project folder and start the container.
|
||||
|
||||
## Configuration
|
||||
|
||||
Edit the configuration file according to the examples and documentation.
|
||||
|
||||
*For more info visit:* [Official Homer Documentation](https://github.com/bastienwirtz/homer/blob/main/docs/configuration.md)
|
||||
|
||||
# Best-Practices & Post-Installation
|
||||
|
||||
## Disable HTTP
|
||||
|
||||
Although Homer is not using any authentication data that needs to be explicitly encrypted, it's recommended to use HTTPS whenever it's possible.
|
||||
|
||||
### Use a Reverse Proxy
|
||||
|
||||
- [ ] Use a Reverse Proxy to securely expose administrative services.
|
||||
|
||||
# Additional Referfences
|
||||
|
||||
[GitHub Project](https://github.com/bastienwirtz/homer)
|
||||
@ -1,11 +1,10 @@
|
||||
version: '3'
|
||||
|
||||
---
|
||||
services:
|
||||
homer:
|
||||
image: b4bz/homer:latest
|
||||
image: b4bz/homer:v23.05.1
|
||||
container_name: homer
|
||||
ports:
|
||||
- "8080:8080"
|
||||
volumes:
|
||||
- /etc/homer/assets/:/www/assets
|
||||
restart: unless-stopped
|
||||
restart: unless-stopped
|
||||
@ -1,32 +0,0 @@
|
||||
# Installation
|
||||
|
||||
## Deployment
|
||||
|
||||
Copy the `docker-compose.yml` template into your project folder and start the container.
|
||||
|
||||
## Configuration
|
||||
|
||||
The initial configuration can be done automatically through docker instructions, or post-installation via the InfluxDB UI or CLI setup.
|
||||
|
||||
*For more info visit:* [Official InfluxDB Installation Documentation](https://docs.influxdata.com/influxdb/v2.1/install/)
|
||||
|
||||
# Best-Practices & Post-Installation
|
||||
|
||||
## Disable HTTP
|
||||
|
||||
It's not secure to expose InfluxDB via the HTTP protocol. Follow these steps to enable HTTPS only.
|
||||
|
||||
### (Option 1): Upload custom certificates
|
||||
|
||||
TODO: #15 Test Docker-Compose for InfluxDB2
|
||||
|
||||
- [ ] Run the container with tls parameters
|
||||
`influxd --tls-cert=/etc/ssl/cert.pem --tls-key=/etc/ssl/cert-key.pem`
|
||||
|
||||
### (Option 2): Use a Reverse Proxy
|
||||
|
||||
- [ ] Use a Reverse Proxy to securely expose administrative services.
|
||||
|
||||
# Additional Referfences
|
||||
|
||||
[Official InfluxDB Documentation](https://docs.influxdata.com/influxdb/v2.1/)
|
||||
24
docker-compose/influxdb/docker-compose.yaml
Normal file
24
docker-compose/influxdb/docker-compose.yaml
Normal file
@ -0,0 +1,24 @@
|
||||
---
|
||||
volumes:
|
||||
influxdb-data:
|
||||
services:
|
||||
influxdb:
|
||||
container_name: influxdb
|
||||
image: influxdb:2.1-alpine
|
||||
ports:
|
||||
- '8086:8086'
|
||||
volumes:
|
||||
- influxdb-data:/var/lib/influxdb2
|
||||
- /etc/influxdb2:/etc/influxdb2
|
||||
# - /etc/ssl/cert.pem/:/etc/ssl/cert.pem # (optional) if you're using self-signed certs
|
||||
# - /etc/ssl/cert-key.pem/:/etc/ssl/cert-key.pem # (optional) if you're using self-signed certs
|
||||
# command: influxd --tls-cert=/etc/ssl/cert.pem --tls-key=/etc/ssl/cert-key.pem # (optional) if you're using self-signed certs
|
||||
environment:
|
||||
- DOCKER_INFLUXDB_INIT_MODE=setup
|
||||
- DOCKER_INFLUXDB_INIT_USERNAME=my-user
|
||||
- DOCKER_INFLUXDB_INIT_PASSWORD=my-password
|
||||
- DOCKER_INFLUXDB_INIT_ORG=my-org
|
||||
- DOCKER_INFLUXDB_INIT_BUCKET=my-bucket
|
||||
# - DOCKER_INFLUXDB_INIT_RETENTION=1w # (optional) configure data retention 1 week
|
||||
# - DOCKER_INFLUXDB_INIT_ADMIN_TOKEN=my-super-secret-auth-token # (optional) set admin token
|
||||
restart: unless-stopped
|
||||
@ -1,32 +0,0 @@
|
||||
version: '3'
|
||||
|
||||
volumes:
|
||||
influxdb-data:
|
||||
|
||||
services:
|
||||
influxdb:
|
||||
container_name: influxdb
|
||||
image: influxdb:2.1-alpine
|
||||
ports:
|
||||
- '8086:8086'
|
||||
volumes:
|
||||
- influxdb-data:/var/lib/influxdb2
|
||||
- /etc/influxdb2:/etc/influxdb2
|
||||
|
||||
# (Optional) If you're using self-signed certs
|
||||
# - /etc/ssl/cert.pem/:/etc/ssl/cert.pem
|
||||
# - /etc/ssl/cert-key.pem/:/etc/ssl/cert-key.pem
|
||||
# (Optional) If you're using self-signed certs
|
||||
# command: influxd --tls-cert=/etc/ssl/cert.pem --tls-key=/etc/ssl/cert-key.pem
|
||||
|
||||
# (Optional) Automatic Setup
|
||||
# environment:
|
||||
# - DOCKER_INFLUXDB_INIT_MODE=setup
|
||||
# - DOCKER_INFLUXDB_INIT_USERNAME=my-user
|
||||
# - DOCKER_INFLUXDB_INIT_PASSWORD=my-password
|
||||
# - DOCKER_INFLUXDB_INIT_ORG=my-org
|
||||
# - DOCKER_INFLUXDB_INIT_BUCKET=my-bucket
|
||||
# # (Optional) Configure Data Retention
|
||||
# - DOCKER_INFLUXDB_INIT_RETENTION=1w
|
||||
# # (Optional) Admin Token
|
||||
# - DOCKER_INFLUXDB_INIT_ADMIN_TOKEN=my-super-secret-auth-token
|
||||
@ -1,23 +0,0 @@
|
||||
---
|
||||
version: '2.1'
|
||||
|
||||
services:
|
||||
|
||||
jellyfin:
|
||||
image: ghcr.io/linuxserver/jellyfin
|
||||
container_name: jellyfin
|
||||
environment:
|
||||
- PUID=1000
|
||||
- PGID=1000
|
||||
- TZ=Europe/Berlin
|
||||
- JELLYFIN_PublishedServerUrl=192.168.0.32 #optional
|
||||
volumes:
|
||||
- /AmberPRO/jellyfin/config:/config
|
||||
- /AmberPRO/jellyfin/tvshows:/data/tvshows
|
||||
- /AmberPRO/jellyfin/movies:/data/movies
|
||||
ports:
|
||||
- 8096:8096
|
||||
- 8920:8920 #optional
|
||||
- 7359:7359/udp #optional
|
||||
- 1900:1900/udp #optional
|
||||
restart: unless-stopped
|
||||
@ -1,10 +1,7 @@
|
||||
version: '3.1'
|
||||
|
||||
---
|
||||
volumes:
|
||||
mariadb-data:
|
||||
|
||||
services:
|
||||
|
||||
mariadb:
|
||||
container_name: mariadb
|
||||
image: mariadb:latest
|
||||
@ -15,4 +12,4 @@ services:
|
||||
MARIADB_ROOT_PASSWORD: your-root-password
|
||||
volumes:
|
||||
- mariadb-data:/var/lib/mysql
|
||||
restart: always
|
||||
restart: unless-stopped
|
||||
@ -1 +0,0 @@
|
||||
TODO: #17 Insert nextcloud readme
|
||||
@ -1,14 +1,13 @@
|
||||
version: '3'
|
||||
|
||||
---
|
||||
volumes:
|
||||
nextcloud-data:
|
||||
nextcloud-db:
|
||||
|
||||
services:
|
||||
|
||||
nextcloud-app:
|
||||
image: nextcloud:latest
|
||||
restart: unless-stopped
|
||||
container_name: nextcloud-app
|
||||
ports:
|
||||
- 80:80
|
||||
volumes:
|
||||
- nextcloud-data:/var/www/html
|
||||
environment:
|
||||
@ -16,12 +15,10 @@ services:
|
||||
- MYSQL_DATABASE=$MYSQL_DATABASE
|
||||
- MYSQL_USER=$MYSQL_USER
|
||||
- MYSQL_HOST=nextcloud-db
|
||||
ports:
|
||||
- 80:80
|
||||
|
||||
restart: unless-stopped
|
||||
nextcloud-db:
|
||||
image: mariadb:latest
|
||||
restart: unless-stopped
|
||||
container_name: nextcloud-db
|
||||
command: --transaction-isolation=READ-COMMITTED --binlog-format=ROW
|
||||
volumes:
|
||||
- nextcloud-db:/var/lib/mysql
|
||||
@ -30,3 +27,4 @@ services:
|
||||
- MYSQL_PASSWORD=$MYSQL_PASSWORD
|
||||
- MYSQL_DATABASE=$MYSQL_DATABASE
|
||||
- MYSQL_USER=$MYSQL_USER
|
||||
restart: unless-stopped
|
||||
@ -1,27 +0,0 @@
|
||||
# Installation
|
||||
|
||||
## Deployment
|
||||
|
||||
Copy the `docker-compose.yml` template into your project folder and start the container.
|
||||
|
||||
## Configuration
|
||||
|
||||
Visit the Nginxproxymanager Web Interface `http://localhost:81`, and login with Nginxproxymanager's default username `admin@example.com` and password: `changeme`.
|
||||
|
||||
*For more info visit:* [Official Nginxproxymanager Installation Documentation](https://nginxproxymanager.com/guide/)
|
||||
|
||||
# Best-Practices & Post-Installation
|
||||
|
||||
## Disable HTTP
|
||||
|
||||
It's not secure to expose Nginxproxymanager via the HTTP protocol. Follow these steps to enable HTTPS only.
|
||||
|
||||
### Don't expose Nginxproxymanager's UI on port 81
|
||||
|
||||
- [ ] Add a Proxy Host for Nginxproxymanager's WebUI to target `127.0.0.1:81`
|
||||
- [ ] Remove port `:81` from the `docker-compose` file
|
||||
|
||||
|
||||
# Additional Referfences
|
||||
|
||||
[Official Nginxproxymanager Installation Documentation](https://nginxproxymanager.com/guide/)
|
||||
@ -1,32 +1,30 @@
|
||||
version: '3'
|
||||
|
||||
---
|
||||
volumes:
|
||||
nginxproxymanager-data:
|
||||
nginxproxymanager-ssl:
|
||||
nginxproxymanager-db:
|
||||
|
||||
services:
|
||||
nginxproxymanager:
|
||||
image: 'jc21/nginx-proxy-manager:latest'
|
||||
image: jc21/nginx-proxy-manager:2.10.3
|
||||
ports:
|
||||
- '80:80'
|
||||
- '81:81'
|
||||
- '443:443'
|
||||
- 80:80
|
||||
- 81:81
|
||||
- 443:443
|
||||
environment:
|
||||
DB_MYSQL_HOST: "nginxproxymanager-db"
|
||||
DB_MYSQL_PORT: 3306
|
||||
DB_MYSQL_USER: "npm"
|
||||
DB_MYSQL_PASSWORD: "npm"
|
||||
DB_MYSQL_NAME: "npm"
|
||||
- DB_MYSQL_HOST=nginxproxymanager-db
|
||||
- DB_MYSQL_PORT=3306
|
||||
- DB_MYSQL_USER=npm
|
||||
- DB_MYSQL_PASSWORD=npm
|
||||
- DB_MYSQL_NAME=npm
|
||||
volumes:
|
||||
- nginxproxymanager-data:/data
|
||||
- nginxproxymanager-ssl:/etc/letsencrypt
|
||||
nginxproxymanager-db:
|
||||
image: 'jc21/mariadb-aria:latest'
|
||||
image: jc21/mariadb-aria:10.4.15
|
||||
environment:
|
||||
MYSQL_ROOT_PASSWORD: 'npm'
|
||||
MYSQL_DATABASE: 'npm'
|
||||
MYSQL_USER: 'npm'
|
||||
MYSQL_PASSWORD: 'npm'
|
||||
- MYSQL_ROOT_PASSWORD=npm
|
||||
- MYSQL_DATABASE=npm
|
||||
- MYSQL_USER=npm
|
||||
- MYSQL_PASSWORD=npm
|
||||
volumes:
|
||||
- nginxproxymanager-db:/var/lib/mysql
|
||||
- nginxproxymanager-db:/var/lib/mysql
|
||||
@ -1,9 +1,7 @@
|
||||
---
|
||||
version: '3.8'
|
||||
|
||||
services:
|
||||
node_exporter:
|
||||
image: quay.io/prometheus/node-exporter:latest
|
||||
image: quay.io/prometheus/node-exporter:v1.5.0
|
||||
container_name: node_exporter
|
||||
command:
|
||||
- '--path.rootfs=/host'
|
||||
@ -1,35 +0,0 @@
|
||||
# Prerequisite
|
||||
|
||||
NVIDIA container toolkit
|
||||
sudo apt -y install build-essential nvidia-cuda-toolkit nvidia-headless-495 nvidia-utils-495 libnvidia-encode-495 \
|
||||
&& distribution=$(. /etc/os-release;echo $ID$VERSION_ID) \
|
||||
&& curl -s -L https://nvidia.github.io/nvidia-docker/gpgkey | sudo apt-key add - \
|
||||
&& curl -s -L https://nvidia.github.io/nvidia-docker/$distribution/nvidia-docker.list | sudo tee /etc/apt/sources.list.d/nvidia-docker.list \
|
||||
&& sudo apt update \
|
||||
&& sudo apt -y install nvidia-container-toolkit nvidia-container-runtime nvidia-docker2
|
||||
|
||||
|
||||
DCGM on host machine running Nvidia GPU
|
||||
wget https://developer.download.nvidia.com/compute/cuda/repos/ubuntu2004/x86_64/cuda-ubuntu2004.pin \
|
||||
&& sudo mv cuda-ubuntu2004.pin /etc/apt/preferences.d/cuda-repository-pin-600 \
|
||||
&& sudo apt-key adv --fetch-keys https://developer.download.nvidia.com/compute/cuda/repos/ubuntu2004/x86_64/7fa2af80.pub \
|
||||
&& sudo add-apt-repository "deb https://developer.download.nvidia.com/compute/cuda/repos/ubuntu2004/x86_64/ /" \
|
||||
&& sudo apt update \
|
||||
&& sudo apt install -y datacenter-gpu-manager \
|
||||
&& sudo systemctl --now enable nvidia-dcgm
|
||||
|
||||
## Deployment
|
||||
|
||||
1. Modify the prometheus configuration template `/etc/prometheus/prometheus.yml` location.
|
||||
# Job for Nvidia DCGM exporter in prometheus config file
|
||||
- job_name: 'nvidia_exporter'
|
||||
static_configs:
|
||||
- targets: ['nvidia_exporter:9400'] # if nvidia_exporter container is not on same docker network , change this line to "- targets: ['whichever ip your host is:9400']"
|
||||
|
||||
# Additional Referfences
|
||||
[Official DCGM Documentations](https://github.com/NVIDIA/DCGM)
|
||||
[Nvidia container toolkit](https://docs.nvidia.com/datacenter/cloud-native/container-toolkit/install-guide.html#install-guide)
|
||||
[Nvidia DCGM exporter Documentation](https://github.com/NVIDIA/dcgm-exporter)
|
||||
[Nvidia DCGM exporter Documentation-2](https://docs.nvidia.com/datacenter/cloud-native/gpu-telemetry/dcgm-exporter.html)
|
||||
[Official Prometheus Documentation](https://prometheus.io/docs/introduction/overview/)
|
||||
[Some grafana dashboard, not perfect, old, but configurable](https://grafana.com/grafana/dashboards/11578)
|
||||
14
docker-compose/nvidiadgcm/docker-compose.yaml
Normal file
14
docker-compose/nvidiadgcm/docker-compose.yaml
Normal file
@ -0,0 +1,14 @@
|
||||
---
|
||||
services:
|
||||
nvidia_exporter:
|
||||
image: nvcr.io/nvidia/k8s/dcgm-exporter:2.3.2-2.6.2-ubuntu20.04
|
||||
container_name: nvidia_exporter
|
||||
runtime: nvidia
|
||||
cap_add:
|
||||
- SYS_ADMIN
|
||||
environment:
|
||||
- NVIDIA_VISIBLE_DEVICES=all
|
||||
- NVIDIA_DRIVER_CAPABILITIES=all
|
||||
ports:
|
||||
- 9400:9400
|
||||
restart: unless-stopped
|
||||
@ -1,21 +0,0 @@
|
||||
---
|
||||
version: '3'
|
||||
services:
|
||||
|
||||
nvidia_exporter: #to export data from DCGM host, need DCGM installed of an equal or newer version to the container on the host system https://github.com/NVIDIA/DCGM
|
||||
image: nvcr.io/nvidia/k8s/dcgm-exporter:2.3.2-2.6.2-ubuntu20.04
|
||||
container_name: nvidia_exporter
|
||||
runtime: nvidia
|
||||
cap_add:
|
||||
- SYS_ADMIN
|
||||
environment:
|
||||
- NVIDIA_VISIBLE_DEVICES=all
|
||||
- NVIDIA_DRIVER_CAPABILITIES=all
|
||||
ports:
|
||||
- "9400:9400"
|
||||
restart: unless-stopped
|
||||
|
||||
#NVIDIA Data Center GPU Manager: To export data from DCGM host to prometheus, you need DCGM installed on host as well as nvidia container toolkit
|
||||
#https://github.com/NVIDIA/DCGM
|
||||
#https://docs.nvidia.com/datacenter/cloud-native/container-toolkit/install-guide.html#install-guide
|
||||
#https://github.com/NVIDIA/dcgm-exporter and https://docs.nvidia.com/datacenter/cloud-native/gpu-telemetry/dcgm-exporter.html
|
||||
@ -1,23 +0,0 @@
|
||||
# Prerequisite
|
||||
|
||||
NVIDIA container toolkit
|
||||
sudo apt -y install build-essential nvidia-cuda-toolkit nvidia-headless-495 nvidia-utils-495 libnvidia-encode-495 \
|
||||
&& distribution=$(. /etc/os-release;echo $ID$VERSION_ID) \
|
||||
&& curl -s -L https://nvidia.github.io/nvidia-docker/gpgkey | sudo apt-key add - \
|
||||
&& curl -s -L https://nvidia.github.io/nvidia-docker/$distribution/nvidia-docker.list | sudo tee /etc/apt/sources.list.d/nvidia-docker.list \
|
||||
&& sudo apt update \
|
||||
&& sudo apt -y install nvidia-container-toolkit nvidia-container-runtime nvidia-docker2
|
||||
|
||||
## Deployment
|
||||
|
||||
1. Modify the prometheus configuration template `/etc/prometheus/prometheus.yml` location.
|
||||
# Job for Nvidia SMI exporter in prometheus config file
|
||||
- job_name: 'nvidia_smi_exporter'
|
||||
static_configs:
|
||||
- targets: ['nvidia_smi_exporter:9835'] # if nvidia_smi_exporter container is not on same docker network , change this line to "- targets: ['whichever ip your host is:9835']"
|
||||
|
||||
# Additional Referfences
|
||||
[Nvidia container toolkit](https://docs.nvidia.com/datacenter/cloud-native/container-toolkit/install-guide.html#install-guide)
|
||||
[Nvidia GPU exporter Documentation](https://github.com/utkuozdemir/nvidia_gpu_exporter)
|
||||
[Official Prometheus Documentation](https://prometheus.io/docs/introduction/overview/)
|
||||
[Some grafana dashboard, not perfect, old, but configurable](https://grafana.com/grafana/dashboards/14574)
|
||||
@ -1,7 +1,6 @@
|
||||
---
|
||||
version: '3'
|
||||
services:
|
||||
nvidia_smi_exporter: #To export data from nvidia-smi, needs nvidia-smi and nvidia-container-toolkit installed on host.
|
||||
nvidia_smi_exporter:
|
||||
image: utkuozdemir/nvidia_gpu_exporter:0.3.0
|
||||
container_name: nvidia_smi_exporter
|
||||
runtime: nvidia
|
||||
@ -14,6 +13,4 @@ services:
|
||||
- /usr/bin/nvidia-smi:/usr/bin/nvidia-smi
|
||||
- /usr/lib/x86_64-linux-gnu/libnvidia-ml.so:/usr/lib/x86_64-linux-gnu/libnvidia-ml.so
|
||||
- /usr/lib/x86_64-linux-gnu/libnvidia-ml.so.1:/usr/lib/x86_64-linux-gnu/libnvidia-ml.so.1
|
||||
restart: unless-stopped
|
||||
|
||||
#Mount points for volume work on Ubuntu 20.04
|
||||
restart: unless-stopped
|
||||
@ -1,15 +1,12 @@
|
||||
version: '3.9'
|
||||
|
||||
---
|
||||
volumes:
|
||||
passbolt-db:
|
||||
passbolt-data-gpg:
|
||||
passbolt-data-jwt:
|
||||
|
||||
services:
|
||||
passbolt-db:
|
||||
container_name: passbolt-db
|
||||
image: mariadb:10.3
|
||||
restart: unless-stopped
|
||||
environment:
|
||||
- MYSQL_RANDOM_ROOT_PASSWORD=true
|
||||
- MYSQL_DATABASE=$PASSBOLT_DB_NAME
|
||||
@ -17,11 +14,10 @@ services:
|
||||
- MYSQL_PASSWORD=$PASSBOLT_DB_PASS
|
||||
volumes:
|
||||
- passbolt-db:/var/lib/mysql
|
||||
|
||||
restart: unless-stopped
|
||||
passbolt:
|
||||
container_name: passbolt-app
|
||||
image: passbolt/passbolt:latest-ce
|
||||
restart: unless-stopped
|
||||
depends_on:
|
||||
- passbolt-db
|
||||
environment:
|
||||
@ -40,3 +36,4 @@ services:
|
||||
- passbolt-data-gpg:/etc/passbolt/gpg
|
||||
- passbolt-data-jwt:/etc/passbolt/jwt
|
||||
command: ["/usr/bin/wait-for.sh", "-t", "0", "passbolt-db:3306", "--", "/docker-entrypoint.sh"]
|
||||
restart: unless-stopped
|
||||
@ -1,15 +0,0 @@
|
||||
# Installation
|
||||
|
||||
## Deployment
|
||||
|
||||
Copy the `docker-compose.yml` template into your project folder and start the container.
|
||||
|
||||
## Configuration
|
||||
|
||||
|
||||
# Best-Practices & Post-Installation
|
||||
|
||||
## Disable HTTP
|
||||
|
||||
# Additional Referfences
|
||||
|
||||
@ -5,14 +5,14 @@ services:
|
||||
container_name: pihole
|
||||
image: pihole/pihole:latest
|
||||
ports:
|
||||
- "53:53/tcp"
|
||||
- "53:53/udp"
|
||||
- "67:67/udp"
|
||||
- "80:80/tcp"
|
||||
- "443:443/tcp"
|
||||
- 53:53/tcp
|
||||
- 53:53/udp
|
||||
- 67:67/udp
|
||||
- 80:80/tcp
|
||||
- 443:443/tcp
|
||||
environment:
|
||||
TZ: 'Europe/Berlin'
|
||||
WEBPASSWORD: 'your-secret-password'
|
||||
- TZ=Europe/Berlin
|
||||
- WEBPASSWORD=your-secret-password
|
||||
volumes:
|
||||
- etcd:/etc/pihole
|
||||
- dnsmasq:/etc/dnsmasq.d
|
||||
|
||||
@ -1,29 +0,0 @@
|
||||
version: '2'
|
||||
|
||||
services:
|
||||
|
||||
linuxserver-plex:
|
||||
container_name: linuxserver-plex
|
||||
restart: unless-stopped
|
||||
image: linuxserver/plex:latest
|
||||
environment:
|
||||
- TZ=Europe/Berlin
|
||||
- PUID=1000
|
||||
- PGID=1000
|
||||
- VERSION=docker
|
||||
ports:
|
||||
- "32400:32400" #(for access to the Plex Media Server) [required]
|
||||
- "32400:32400/udp"
|
||||
- "32410:32410/udp" #(for current GDM network discovery)
|
||||
- "32412:32412/udp"
|
||||
- "32413:32413/udp"
|
||||
- "32414:32414/udp"
|
||||
- "32469:32469" #(for access to the Plex DLNA Server)
|
||||
- "32469:32469/udp"
|
||||
- "5353:5353" # (for older Bonjour/Avahi network discovery)
|
||||
#- "1900:1900/udp" #(for access to the Plex DLNA Server)
|
||||
|
||||
volumes:
|
||||
- /AmberPRO/plex/config:/config
|
||||
- /AmberPRO/plex/media1:/data/movies
|
||||
- /AmberPRO/plex/transcode:/transcode
|
||||
@ -1,22 +1,15 @@
|
||||
version: '3'
|
||||
|
||||
networks:
|
||||
portainer-agent_default:
|
||||
driver: bridge
|
||||
# (Optional) When setting up in swarm mode replace with
|
||||
# driver: overlay
|
||||
|
||||
---
|
||||
services:
|
||||
app:
|
||||
container_name: portainer-agent
|
||||
deploy:
|
||||
mode: global
|
||||
image: 'portainer/agent:latest'
|
||||
image: portainer/agent:latest
|
||||
ports:
|
||||
- '9001:9001'
|
||||
- 9001:9001
|
||||
volumes:
|
||||
- /var/run/docker.sock:/var/run/docker.sock
|
||||
- /var/lib/docker/volumes:/var/lib/docker/volumes
|
||||
networks:
|
||||
- portainer-agent_default
|
||||
restart: always
|
||||
restart: unless-stopped
|
||||
@ -1,46 +0,0 @@
|
||||
# Installation
|
||||
|
||||
## Deployment
|
||||
|
||||
1. Copy the `docker-compose.yml` template into your project folder and start the container.
|
||||
|
||||
### Manage local environment
|
||||
|
||||
Allows Portainer to manage the local Docker Environment
|
||||
```yaml
|
||||
volumes:
|
||||
- /var/run/docker.sock:/var/run/docker.sock
|
||||
```
|
||||
|
||||
### Data Persistence
|
||||
|
||||
Storing Data in a `portainer-data` volume on docker
|
||||
```yaml
|
||||
volumes:
|
||||
- portainer-data:/data
|
||||
```
|
||||
|
||||
## Configuration
|
||||
|
||||
|
||||
|
||||
# Best-Practices & Post-Installation
|
||||
|
||||
## Disable HTTP
|
||||
|
||||
It's not secure to expose Portainer via the HTTP protocol. Follow these steps to enable HTTPS only.
|
||||
|
||||
### (Option 1): Upload custom certificates
|
||||
|
||||
- [ ] Upload your custom certificates
|
||||
- [ ] Force HTTPS only
|
||||
- [ ] Expose Port `9443`
|
||||
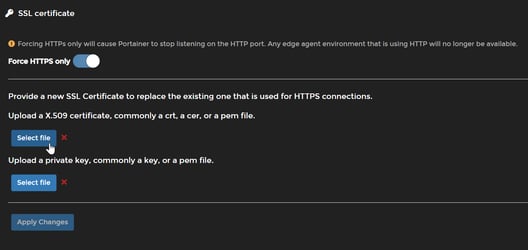
|
||||
|
||||
### (Option 2): Use a Reverse Proxy
|
||||
|
||||
- [ ] Use a Reverse Proxy to securely expose administrative services.
|
||||
|
||||
# Additional Referfences
|
||||
|
||||
[Official Portainer Documentation](https://docs.portainer.io/)
|
||||
@ -1,17 +1,16 @@
|
||||
version: '3'
|
||||
|
||||
---
|
||||
volumes:
|
||||
portainer-data:
|
||||
driver: local
|
||||
|
||||
services:
|
||||
app:
|
||||
container_name: portainer
|
||||
image: 'portainer/portainer-ce:latest'
|
||||
image: portainer/portainer-ce:latest
|
||||
ports:
|
||||
- '9000:9000'
|
||||
- '9443:9443'
|
||||
- '8000:8000'
|
||||
- 9000:9000
|
||||
- 9443:9443
|
||||
- 8000:8000
|
||||
volumes:
|
||||
- /var/run/docker.sock:/var/run/docker.sock
|
||||
- portainer-data:/data
|
||||
restart: unless-stopped
|
||||
@ -1,35 +0,0 @@
|
||||
# Installation
|
||||
|
||||
## Deployment
|
||||
|
||||
1. Copy the configuration template into the `/etc/prometheus/prometheus.yml` location.
|
||||
2. Copy the `docker-compose.yml` template into your project folder and start the container.
|
||||
|
||||
## Configuration
|
||||
|
||||
Configure your settings in the `/etc/prometheus/prometheus.yml` file.
|
||||
|
||||
*For more info visit:* [Official Prometheus Installation Documentation](https://prometheus.io/docs/prometheus/latest/installation/)
|
||||
|
||||
# Exporters
|
||||
|
||||
TODO: WIP
|
||||
|
||||
- cadvisor
|
||||
- nodeexporter
|
||||
- nvidiadgcm
|
||||
- nvidiasmi
|
||||
|
||||
# Best-Practices & Post-Installation
|
||||
|
||||
## Disable HTTP
|
||||
|
||||
It's not secure to expose Prometheus via the HTTP protocol.
|
||||
|
||||
### Use a Reverse Proxy
|
||||
|
||||
- [ ] Use a Reverse Proxy to securely expose administrative services.
|
||||
|
||||
# Additional Referfences
|
||||
|
||||
[Official Prometheus Documentation](https://prometheus.io/docs/introduction/overview/)
|
||||
@ -1,18 +1,15 @@
|
||||
version: '3'
|
||||
|
||||
---
|
||||
volumes:
|
||||
prometheus-data:
|
||||
driver: local
|
||||
|
||||
services:
|
||||
prometheus:
|
||||
image: prom/prometheus:latest
|
||||
container_name: prometheus
|
||||
ports:
|
||||
- "9090:9090"
|
||||
- 9090:9090
|
||||
volumes:
|
||||
- /etc/prometheus:/etc/prometheus
|
||||
- prometheus-data:/prometheus
|
||||
restart: unless-stopped
|
||||
command:
|
||||
- "--config.file=/etc/prometheus/prometheus.yml"
|
||||
command: "--config.file=/etc/prometheus/prometheus.yml"
|
||||
restart: unless-stopped
|
||||
@ -1,16 +0,0 @@
|
||||
version: '3'
|
||||
|
||||
services:
|
||||
app:
|
||||
image: registry:2
|
||||
container_name: docker-registry
|
||||
restart: unless-stopped
|
||||
environment:
|
||||
REGISTRY_AUTH: htpasswd
|
||||
REGISTRY_AUTH_HTPASSWD_PATH: /auth/htpasswd
|
||||
REGISTRY_AUTH_HTPASSWD_REALM: Local Registry Realm
|
||||
ports:
|
||||
- 5000
|
||||
volumes:
|
||||
- ./data:/var/lib/registry
|
||||
- ./auth:/auth:ro
|
||||
@ -1,8 +1,5 @@
|
||||
---
|
||||
version: '2'
|
||||
|
||||
services:
|
||||
|
||||
mariadb:
|
||||
image: linuxserver/mariadb
|
||||
container_name: mariadb
|
||||
@ -17,7 +14,6 @@ services:
|
||||
volumes:
|
||||
- /opt/webserver_swag/config/mariadb:/config
|
||||
restart: unless-stopped
|
||||
|
||||
swag:
|
||||
image: linuxserver/swag
|
||||
container_name: swag
|
||||
@ -34,7 +30,7 @@ services:
|
||||
- /opt/webserver_swag/config:/config
|
||||
ports:
|
||||
- 443:443
|
||||
- 80:80 #optional
|
||||
- 80:80 # optional
|
||||
depends_on:
|
||||
- mariadb
|
||||
restart: unless-stopped
|
||||
@ -1,23 +0,0 @@
|
||||
---
|
||||
version: '2'
|
||||
|
||||
services:
|
||||
|
||||
swag:
|
||||
image: linuxserver/swag
|
||||
container_name: swag
|
||||
cap_add:
|
||||
- NET_ADMIN
|
||||
environment:
|
||||
- PUID=1001
|
||||
- PGID=1001
|
||||
- TZ=Europe/Berlin
|
||||
- URL=do-test-1.the-digital-life.com
|
||||
- SUBDOMAINS=www
|
||||
- VALIDATION=http
|
||||
volumes:
|
||||
- /opt/webserver_swag/config:/config
|
||||
ports:
|
||||
- 443:443
|
||||
- 80:80 #optional
|
||||
restart: unless-stopped
|
||||
@ -1,29 +0,0 @@
|
||||
# Teleport Boilerplates
|
||||
|
||||
//TODO Add Description
|
||||
|
||||
Tested with teleport 10
|
||||
|
||||
## Deployment
|
||||
|
||||
Copy the `docker-compose.yml`, and `config/teleport.yml` files into your project folder and start the container.
|
||||
|
||||
## Configuration
|
||||
|
||||
### Create a new user
|
||||
|
||||
```bash
|
||||
|
||||
```
|
||||
|
||||
## Best-Practices & Post-Installation
|
||||
|
||||
### Enable passwordless
|
||||
|
||||
To enable passwordless feature remove the **(Optional) Passwordless Authentication** statements from the `config/teleport.yml` file and re-start the container.
|
||||
|
||||
### Get a trusted SSL cert from Letsencrypt
|
||||
|
||||
To get a trusted SSL cert from Letsnecrypt remove the **(Optional) ACME** statements from the `config/teleport.yml` file and re-start the container.
|
||||
|
||||
*Note, you need a public DNS Record that points to your-server-url.*
|
||||
@ -1,10 +1,7 @@
|
||||
version: '3'
|
||||
|
||||
---
|
||||
volumes:
|
||||
teleport-data:
|
||||
|
||||
services:
|
||||
|
||||
teleport:
|
||||
image: quay.io/gravitational/teleport:10.0.2
|
||||
user: 1000:1000
|
||||
@ -12,10 +9,11 @@ services:
|
||||
entrypoint: /bin/sh
|
||||
command: -c "/usr/bin/dumb-init teleport start -d -c /etc/teleport/teleport.yml"
|
||||
ports:
|
||||
- "3023:3023"
|
||||
- "3024:3024"
|
||||
- "3025:3025"
|
||||
- "443:443"
|
||||
- 3023:3023
|
||||
- 3024:3024
|
||||
- 3025:3025
|
||||
- 443:443
|
||||
volumes:
|
||||
- .config:/etc/teleport
|
||||
- teleport-data:/var/lib/teleport
|
||||
restart: unless-stopped
|
||||
@ -1,41 +0,0 @@
|
||||
# Installation
|
||||
|
||||
TODO: #21 Improve traefik docu
|
||||
|
||||
## Data Persistence
|
||||
... Storing Data in the `/etc/traefik` directory on the host, passing through...
|
||||
```yaml
|
||||
volumes:
|
||||
- /etc/traefik:/etc/traefik
|
||||
```
|
||||
|
||||
## Self-Signed Certificates
|
||||
According to traefik's documentation it will automatically generate self-signed Certificates if no Default Certificate is provided. If you'd like to overwrite the self-signed Certificate with your own, uncomment the section for
|
||||
```yaml
|
||||
# (Optional) Overwrite Default Certificates
|
||||
tls:
|
||||
stores:
|
||||
default:
|
||||
defaultCertificate:
|
||||
certFile: /etc/traefik/certs/cert.pem
|
||||
keyFile: /etc/traefik/certs/cert-key.pem
|
||||
```
|
||||
Replace the `/etc/traefik/certs/cert.pem` with your certificate file, and the `/etc/traefik/certs/cert-key.pem` with your certificate key.
|
||||
|
||||
|
||||
# Best-Practices & Post-Installation
|
||||
|
||||
|
||||
## MinTLS Version
|
||||
TLS 1.0 and 1.1 are not longer secure! Consider disabling it in the Traefik Configuration.
|
||||
|
||||
|
||||
```yaml
|
||||
providers:
|
||||
docker:
|
||||
exposedByDefault: false # Default is true
|
||||
file:
|
||||
# watch for dynamic configuration changes
|
||||
directory: /etc/traefik
|
||||
watch: true
|
||||
```
|
||||
13
docker-compose/traefik/docker-compose.yaml
Normal file
13
docker-compose/traefik/docker-compose.yaml
Normal file
@ -0,0 +1,13 @@
|
||||
---
|
||||
services:
|
||||
traefik:
|
||||
image: traefik:v2.5
|
||||
container_name: traefik
|
||||
ports:
|
||||
- 80:80
|
||||
- 443:443
|
||||
# - 8080:8080 # (optional) expose the dashboard !don't use in production!
|
||||
volumes:
|
||||
- /etc/traefik:/etc/traefik
|
||||
- /var/run/docker.sock:/var/run/docker.sock:ro
|
||||
restart: unless-stopped
|
||||
@ -1,14 +0,0 @@
|
||||
version: '3'
|
||||
|
||||
services:
|
||||
traefik:
|
||||
image: "traefik:v2.5"
|
||||
container_name: "traefik"
|
||||
ports:
|
||||
- "80:80"
|
||||
- "443:443"
|
||||
# (Optional) Expose Dashboard
|
||||
- "8080:8080" # Don't do this in production!
|
||||
volumes:
|
||||
- /etc/traefik:/etc/traefik
|
||||
- /var/run/docker.sock:/var/run/docker.sock:ro
|
||||
@ -1,15 +1,13 @@
|
||||
version: '3'
|
||||
|
||||
---
|
||||
volumes:
|
||||
uptimekuma-data:
|
||||
driver: local
|
||||
|
||||
services:
|
||||
uptimekuma:
|
||||
image: louislam/uptime-kuma:latest
|
||||
container_name: uptimekuma
|
||||
ports:
|
||||
- "3001:3001"
|
||||
- 3001:3001
|
||||
volumes:
|
||||
- uptimekuma-data:/app/data
|
||||
restart: unless-stopped
|
||||
@ -1 +0,0 @@
|
||||
# TODO: #20 Insert whoami readme
|
||||
@ -1,18 +0,0 @@
|
||||
version: '3'
|
||||
|
||||
networks:
|
||||
frontend:
|
||||
external: true
|
||||
|
||||
services:
|
||||
whoami:
|
||||
image: traefik/whoami
|
||||
container_name: whoami
|
||||
networks:
|
||||
- frontend
|
||||
labels:
|
||||
- 'traefik.enable=true'
|
||||
- 'traefik.http.routers.public.rule=Host(`your-domain.com`)'
|
||||
- 'traefik.http.routers.public.entrypoints=websecure'
|
||||
- 'traefik.http.routers.public.tls=true'
|
||||
restart: unless-stopped
|
||||
Loading…
Reference in New Issue
Block a user