diff --git a/content/client/_index.es.md b/content/client/_index.es.md
index f5cfe09..b4bc60c 100644
--- a/content/client/_index.es.md
+++ b/content/client/_index.es.md
@@ -5,117 +5,135 @@ pre: "1. "
---
## Introducción
-El cliente RustDesk es utilizado en dispositivos para conectar con los servidores de RustDesk, tanto el servidor Pro como el de código abierto. El cliente esta disponible en [GitHub](https://github.com/rustdesk/rustdesk/releases/latest).
+El cliente RustDesk se utiliza en dispositivos para conectarse a través de nuestro servidor RustDesk, ya sea de código abierto o Pro. Está disponible para descargar desde [GitHub](https://github.com/rustdesk/rustdesk/releases/latest).
## Plataformas compatibles
- Microsoft Windows
- macOS
-- Derivados de Debian (Ubuntu, Mint, etc.)
-- Derivados de Redhat (Centos, Rocky, etc.)
-- Arch/Manjaro
+- Derivados de Debian (Ubuntu ≥ 16, Linux Mint, etc.)
+- Derivados de Red Hat (CentOS, Fedora ≥ 18, Rocky Linux, etc.)
+- Arch Linux/Manjaro
- openSUSE
+- NixOS
- AppImage / Flatpak
- Android
-- iOS (no soporta control remoto)
-- Web (1.1.9 Beta)
+- iOS (no soporta ser controlado)
+- Web
## Instalación
### Windows
-Descarga el .exe de Github y ejecútalo.
-
-Para instalar silenciosamente ejecuta el .exe con el parámetro `--silent-install`.
+Descarga el exe de GitHub e instálalo.
+Para instalar silenciosamente ejecuta el exe de instalación con `--silent-install`.
### macOS
-Descarga el archivo .dmg de Github, mas información en la [pagina de macOS](/docs/es/client/mac/).
+Descarga el archivo dmg de GitHub, más información se puede encontrar en la [página de macOS](https://rustdesk.com/docs/es/client/mac/).
-Abri el archivo .dmg, arrastra `RustDesk` a `Aplicaciones`.
+Abre el archivo dmg y arrastra `RustDesk` a `Aplicaciones`.
-Permite la ejecución de RustDesk
+Permite la ejecución de RustDesk.
-Habilita la petición de permisos y seguí las instrucciones del lado inquiero del cliente de RustDesk para terminar la configuración.
-Enable permissions requested and follow prompts on the left hand side of RustDesk to finish setup.
+Habilita los permisos solicitados y sigue las instrucciones en el lado izquierdo de RustDesk para terminar la configuración.
### Linux
-Por favor lee las instrucciones de abajo para instalar en los distintos "sabores" de Linux, todos los instaladores están en GitHub
+Por favor, consulta las siguientes instrucciones para instalar en las distintas "distribuciones" de Linux (los instaladores están en GitHub o disponibles en el repositorio de la distribución).
-
-### Derivados de Debian (>= 16)
+#### Derivados de Debian
```sh
-# Ignora el reporte de uso incorrecto del disco {wrong disk usage}.
+# por favor ignora el reporte erróneo de uso del disco
sudo apt install -fy ./rustdesk-.deb
```
-### CentOS/Fedora (>= 18)
+#### Derivados de Red Hat
```sh
sudo yum localinstall ./rustdesk-.rpm
```
-### Arch/Manjaro
+#### Arch Linux/Manjaro
```sh
sudo pacman -U ./rustdesk-.pkg.tar.zst
```
-### openSUSE (>= Leap 15.0)
+#### openSUSE (≥ Leap 15.0)
```sh
sudo zypper install --allow-unsigned-rpm ./rustdesk--suse.rpm
```
+
+#### Nix / NixOS (≥ 22.05)
+
+Entrar temporalmente en un shell con `rustdesk` listo para ejecutar:
+
+```sh
+nix shell nixpkgs#rustdesk
+```
+
+Instalar en el perfil del usuario actual:
+
+```sh
+nix profile install nixpkgs#rustdesk
+```
+
+Para instalar en todo el sistema en NixOS, ejecuta `nixos-rebuild switch --flake /etc/nixos` después de editar `configuration.nix`:
+
+```
+ environment.systemPackages = with pkgs; [
+ ...
+ rustdesk
+ ];
+```
+
### Android
-Instala el archivo .apk de nuestro GitHub, mas información en la [Pagina de android](/docs/es/client/android/)
+Instala el apk desde nuestro GitHub, más información se puede encontrar en la [página de Android](https://rustdesk.com/docs/es/client/android/).
### iOS (iPhone, iPad)
-Descarga la app de la [App Store](https://apps.apple.com/us/app/rustdesk-remote-desktop/id1581225015).
+Descarga la aplicación desde la [App Store](https://apps.apple.com/us/app/rustdesk-remote-desktop/id1581225015).
+## Uso
+Una vez instalado (o ejecutado como un ejecutable temporal) RustDesk se conectará a los servidores públicos. Verás un mensaje en la parte inferior que dice (1) "Listo, para una conexión más rápida, por favor configure su propio servidor". En la parte superior izquierda verás tu (2) ID, (3) Contraseña de un solo uso y a la derecha un (4) cuadro para conectarte a otra computadora si conoces su ID.
-## Utilización
-Una vez instalado(o ejecutado de manera temporal) RustDesk se conectara a los servidores públicos. Veras un mensaje en la parte inferior con el texto (1) "Listo, Para una conexión mas rápida, configure su propio servidor". En la parte superior izquierda veras (2) ID, (3) Contraseña de un solo uso, (4) entrada de texto para conectar a otra computadora mediante su ID
+
-
-
-Para acceder a los ajustes, hace click en el (5) botón de menu [ ⋮ ] a la derecha de la ID.
-
-En ajustes encontraras:
-- General - Control del servicio, Temas, Codec de Hardware, Audio, Grabación e Idioma.
-- Seguridad - Permisos para alguien tomando el control, Opciones de contraseña, Posibilidad de cambiar tu ID y Opciones avanzadas de seguridad.
-- Red - Configuración de tu propio servidor y Proxy.
-- Pantalla - Controla la configuración de la pantalla de conexiones remotas y otras opciones por defecto, sincronización del portapapeles,etc.
-- Cuenta - Puede ser usado en conjunto con el Pro Server para ingresar a la API.
-- About - Muestra información sobre el software.
+Para acceder a la configuración, haz clic en el (5) botón de Menú [ ⋮ ] a la derecha del ID.
+En Configuración encontrarás:
+- General - Control del servicio, tema, códec de hardware, audio, grabación e idioma
+- Seguridad - Permisos para alguien tomando el control, opciones de contraseña, capacidad de cambiar tu ID y configuración avanzada de seguridad
+- Red - Configura aquí tu propia configuración del servidor y proxy
+- Pantalla - Controla la configuración de pantalla para sesiones remotas y otras opciones predeterminadas, sincronizar portapapeles, etc.
+- Cuenta - Esto se puede usar junto con el servidor Pro para iniciar sesión en la API
+- Acerca de - Muestra información sobre el software.
## Configurando RustDesk
+Hay varias formas de configurar RustDesk.
-Hay varias maneras de configurar RUstDesk
+La forma más fácil es usando RustDesk Server Pro, puedes obtener una cadena de configuración encriptada, esto se puede usar junto con `--config` para importar configuraciones. Para hacer esto:
+1. Abre la línea de comandos en cualquier sistema operativo que uses, en la carpeta donde está instalado RustDesk, es decir, `C:\Program Files\RustDesk` en Windows, `/usr/bin` en Linux.
+2. Usa el comando `rustdesk.exe --config tu-cadena-encriptada` por ejemplo `rustdesk.exe --config 9JSPSvJzNrBDasJjNSdXOVVBlERDlleoNWZzIHcOJiOikXZr8mcw5yazVGZ0NXdy5CdyciojI0N3boJye`.
-La manera mas fácil es usando RusDesk Server Pro (servidor profesional de RustDesk) para obtener una cadena encriptada, Esto puede ser usado en conjunto con `--config` para importar los ajustes. para hacer esto:
-1. Abri la interfaz de linea de comandos de tu sistema operativo, en la carpeta de instalación de RustDesk `C:\Program Files\RustDesk` en Windows, `/usr/bin` en Linux.
-2. Usa el comando `rustdesk.exe --config tu-cadena-encriptada` ej. `rustdesk.exe --config 9JSPSvJzNrBDasJjNSdXOVVBlERDlleoNWZzIHcOJiOikXZr8mcw5yazVGZ0NXdy5CdyciojI0N3boJye`.
-
-Podes configurar el cliente manualmente también, para hacerlo:
-1. Hace click en Ajustes
-2. Hace click en Red
-3. Hace click en Desbloquear Ajustes de Red
-4. Ingresa las direcciones de los servidores IDs, Relay y Api(si estas usando Pro) y tu "key"
-
-
+Puedes configurar manualmente un cliente. Para hacer esto:
+1. Haz clic en Configuración.
+2. Haz clic en Red.
+3. Haz clic en Desbloquear configuración de red.
+4. Ingresa tu ID, Relay, API (si usas servidor pro) y tu clave.
-Si configuras el cliente manualmente, podes usar el archivo `RustDesk2.toml` (en la carpeta de usuarios) y usar `--import-config` de manera similar al ejemplo de arriba.
+
-## Parámetros de la linea de comandos
-- `--password` Puede ser usado para establecer un parámetro de contraseña
-- `--get-id` Puede ser usado para obtener la ID
-- `--set-id` Puede ser usado para establecer una ID, tenga en cuenta que las ID necesitan empezar con una letra.
-- `--silent-install` Puede ser usado para instalar RustDesk de manera silenciosa en Windows.
+Si configuras manualmente un cliente, puedes recuperar el archivo `RustDesk2.toml` (en la carpeta de usuarios) y usar `--import-config` de manera similar al ejemplo anterior.
-Parámetros adicionales avanzados se pueden encontrar [aquí](https://github.com/rustdesk/rustdesk/blob/bdc5cded221af9697eb29aa30babce75e987fcc9/src/core_main.rs#L242).
+## Parámetros de línea de comandos
+- `--password` se puede usar para establecer una contraseña permanente.
+- `--get-id` se puede usar para obtener el ID.
+- `--set-id` se puede usar para establecer un ID, ten en cuenta que los IDs deben comenzar con una letra.
+- `--silent-install` se puede usar para instalar RustDesk silenciosamente en Windows.
+Los parámetros avanzados adicionales se pueden encontrar [aquí](https://github.com/rustdesk/rustdesk/blob/bdc5cded221af9697eb29aa30babce75e987fcc9/src/core_main.rs#L242).
-{{% children depth="1" showhidden="true" %}}
+{{% children depth="3" showhidden="true" %}}
\ No newline at end of file
diff --git a/content/client/linux/SELinux/_index.de.md b/content/client/linux/SELinux/_index.de.md
deleted file mode 100644
index 0f7a1c3..0000000
--- a/content/client/linux/SELinux/_index.de.md
+++ /dev/null
@@ -1,1837 +0,0 @@
----
-title: SELinux
-weight: 100
----
-
-Einige Distributionen (z. B. Fedora) aktivieren standardmäßig SELinux, was dazu führt, dass der RustDesk-Dienst nicht normal gestartet und ausgeführt werden kann.
-
-Sie können `sestatus` im Terminal ausführen, um zu überprüfen, ob SELinux aktiviert ist.
-
-Je nachdem, ob sie aktiviert ist oder nicht, sehen Sie zwei verschiedene Ausgaben:
-
-```sh
-# Aktiviert
-SELinux status: enabled
-...
-
-# Deaktiviert
-SELinux status: disabled
-...
-```
-
-## SELinux-Richtlinien hinzufügen
-
-Eine Einführung in SELinux finden Sie unter [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials).
-
-Hier nehmen wir Fedora 38 als Beispiel, um zu zeigen, wie man SELinux-Richtlinien hinzufügt.
-
-```sh
-sudo dnf install selinux-policy-devel make
-```
-
-Das Hinzufügen von SELinux-Richtlinien erfordert die Bestimmung des Diensttyps, der sich im Sicherheitskontext des Prozesses befindet.
-
-```sh
-$ ps -eZ | grep rustdesk
-system_u:system_r:init_t:s0 80439 ? 00:00:02 rustdesk
-```
-
-`system_u:system_r:init_t:s0` ist der Sicherheitskontext des RustDesk-Prozesses, wobei das dritte Feld `init_t` der Typ des Prozesses ist.
-
-Es gibt zwei Möglichkeiten, SELinux-Typregeln zu schreiben:
-
-1. Hinzufügen von Regeln zum Standard `init_t`.
-2. Hinzufügen eines neuen Typs `rustdesk_t` und Hinzufügen von Regeln.
-
-Bei der ersten Methode sind die Änderungen relativ gering, aber da der Standardtyp `init_t` geändert wird, ist sie gleichbedeutend mit dem Hinzufügen von Berechtigungen zu anderen Diensten, die den Typ `init_t` verwenden. **Nicht zur Verwendung empfohlen.**
-
-Die zweite Methode besteht darin, Regeln von Grund auf neu hinzuzufügen. Es gibt viele Regeln, die hinzugefügt werden müssen, und verschiedene Systeme können Unterschiede aufweisen. Es kann notwendig sein, einige Anpassungen während der praktischen Nutzung vorzunehmen.
-
-### Den Standardtyp verwenden
-
-Der Standardtyp des RustDesk-Dienstes ist `init_t`, der durch die [Kontextvererbungsregeln von SELinux](https://wiki.gentoo.org/wiki/SELinux/Tutorials/How_does_a_process_get_into_a_certain_context) bestimmt wird.
-
-**Achtung**: Die Änderung des Standardtyps bedeutet, dass sich auch die Richtlinien anderer Dienste ändern können. Bitte verwenden Sie diese Methode mit Bedacht!
-
-Bearbeiten Sie die Regeldatei `rustdesk.te`:
-
-```text
-module rustdesk 1.0;
-
-require {
- type event_device_t;
- type xserver_t;
- type xserver_port_t;
- type sudo_exec_t;
- type init_t;
- type ephemeral_port_t;
- type user_tmp_t;
- type user_fonts_cache_t;
- type pulseaudio_home_t;
- type session_dbusd_tmp_t;
- type unconfined_dbusd_t;
- class process execmem;
- class file { open read create write execute execute_no_trans map setattr lock link unlink };
- class unix_stream_socket connectto;
- class tcp_socket name_connect;
- class dir { add_name remove_name };
- class sock_file write;
- class chr_file { open read write } ;
-}
-
-#============= init_t ==============
-allow init_t xserver_t:unix_stream_socket connectto;
-allow init_t sudo_exec_t:file { open read execute execute_no_trans };
-allow init_t user_tmp_t:file { open write setattr };
-allow init_t self:process execmem;
-allow init_t user_fonts_cache_t:dir { add_name remove_name };
-allow init_t user_fonts_cache_t:file { read write create open link lock unlink };
-allow init_t xserver_port_t:tcp_socket name_connect;
-allow init_t pulseaudio_home_t:file { read write open lock };
-allow init_t session_dbusd_tmp_t:sock_file write;
-allow init_t unconfined_dbusd_t:unix_stream_socket connectto;
-
-#!!!! Dieser AVC kann mit dem booleschen Wert 'nis_enabled' zugelassen werden
-allow init_t ephemeral_port_t:tcp_socket name_connect;
-
-#!!!! Dieser AVC kann mit dem Booleschen Wert 'domain_can_mmap_files' zugelassen werden
-allow init_t sudo_exec_t:file map;
-
-
-#============= init_t Wayland ==============
-allow init_t event_device_t:chr_file { open read write };
-
-#!!!! Dieser AVC kann mit dem Booleschen Wert 'domain_can_mmap_files' zugelassen werden
-allow init_t user_tmp_t:file map;
-
-```
-
-Ausführen mit:
-
-```sh
-$ checkmodule -M -m -o rustdesk.mod rustdesk.te && semodule_package -o rustdesk.pp -m rustdesk.mod && sudo semodule -i rustdesk.pp
-$ sudo semodule -l | grep rustdesk
-```
-
-### Einen Typ `rustdesk_t` erstellen
-
-1. Ein neues Verzeichnis erstellen: `mkdir rustdesk-selinux-1.0`.
-2. SELinux-Richtliniendateien erstellen: `touch Makefile rustdesk.te rustdesk.fc rustdesk.if`.
-
-```text
-.
-├── Makefile
-├── rustdesk.fc
-├── rustdesk.if
-└── rustdesk.te
-```
-
-`rustdesk.te` ist die wichtigste Richtliniendatei.
-In diesem Beispiel besteht die Datei hauptsächlich aus 3 Teilen:
-
-1. [`init.te`](https://github.com/fedora-selinux/selinux-policy/blob/rawhide/policy/modules/system/init.te) im GitHub-Repository selinux-policy.
-2. Audit-Protokoll, `grep rustdesk /var/log/audit/audit.log | audit2allow -a -M test`.
-3. Die Richtlinie `init_t` des Testsystems, `sesearch -A | grep 'allow init_t ' | sed 's/allow init_t /allow rustdesk_t /g'`.
-
-Einige Richtlinien sind doppelt und einige sind redundant, aber das ist in Ordnung, da es auf `rustdesk_t` funktioniert.
-
-Der Inhalt der einzelnen Dateien ist wie folgt.
-
-`rustdesk.te`:
-
-```text
-
-policy_module(rustdesk, 1.0)
-
-type rustdesk_t;
-type rustdesk_exec_t;
-
-gen_require(`
- # für die direkte Ausführung von Init-Skripten verwendet
- # durch Domainadmins
- attribute direct_run_init;
- attribute direct_init;
- attribute direct_init_entry;
-
- attribute init_script_domain_type;
- attribute initrc_transition_domain;
- # Attribut, das für systemd verwendet wird, damit Domänen systemd erlauben können, sock_files zu erstellen
- attribute init_sock_file_type;
- # Attribut für Verzeichnisse, die systemd anhand von Pfadeinstellungen überwachen soll
- # (siehe systemd.path(5) für weitere Informationen) (veraltet)
- attribute init_watch_path_type;
-
- # Prozesstypen als Daemons markieren
- attribute daemon;
- attribute systemprocess;
- attribute systemprocess_entry;
-
- # Dateityp als Daemon-Ausführungsverzeichnis markieren
- attribute daemonrundir;
-
- class passwd rootok;
- class dbus { acquire_svc send_msg };
- class process execmem;
-
- type abrt_dump_oops_t;
- type abrt_upload_watch_t;
- type adjtime_t;
- type aiccu_t;
- type amanda_inetd_exec_t;
- type amanda_t;
- type antivirus_t;
- type apcupsd_power_t;
- type auditd_etc_t;
- type autofs_device_t;
- type binfmt_misc_fs_t;
- type bitlbee_exec_t;
- type bitlbee_t;
- type boltd_var_lib_t;
- type boltd_var_run_t;
- type boothd_t;
- type bootloader_exec_t;
- type bootloader_t;
- type bpf_t;
- type bugzilla_script_t;
- type certwatch_t;
- type cgroup_t;
- type chkpwd_exec_t;
- type chkpwd_t;
- type chronyc_t;
- type chronyd_exec_t;
- type chronyd_keys_t;
- type chronyd_restricted_t;
- type chroot_exec_t;
- type cifs_helper_t;
- type cinder_domain;
- type cloudform_domain;
- type collectd_script_t;
- type comsat_exec_t;
- type comsat_t;
- type config_home_t;
- type console_device_t;
- type consolekit_log_t;
- type container_kvm_t;
- type container_runtime_domain;
- type container_runtime_tmpfs_t;
- type container_var_lib_t;
- type crack_t;
- type cups_brf_t;
- type cupsd_exec_t;
- type cupsd_lpd_exec_t;
- type cupsd_lpd_t;
- type cupsd_t;
- type cvs_exec_t;
- type cvs_t;
- type data_home_t;
- type dbskkd_exec_t;
- type dbskkd_t;
- type default_context_t;
- type default_t;
- type devicekit_disk_t;
- type devicekit_power_t;
- type devicekit_t;
- type device_t;
- type devlog_t;
- type devpts_t;
- type dhcpc_state_t;
- type dhcp_state_t;
- type dirsrvadmin_script_t;
- type dri_device_t;
- type dspam_script_t;
- type efivarfs_t;
- type ephemeral_port_t;
- type etc_aliases_t;
- type etc_runtime_t;
- type etc_t;
- type event_device_t;
- type faillog_t;
- type fetchmail_t;
- type fingerd_exec_t;
- type fingerd_t;
- type fixed_disk_device_t;
- type flatpak_helper_t;
- type fprintd_exec_t;
- type fprintd_t;
- type fprintd_var_lib_t;
- type fsadm_t;
- type ftpd_exec_t;
- type ftpd_t;
- type fwupd_cache_t;
- type fwupd_t;
- type gconfdefaultsm_t;
- type geoclue_t;
- type getty_exec_t;
- type getty_t;
- type gitd_exec_t;
- type git_system_t;
- type gnome_home_type;
- type gnomesystemmm_t;
- type guest_t;
- type home_bin_t;
- type home_root_t;
- type hostname_etc_t;
- type httpd_log_t;
- type httpd_t;
- type httpd_tmp_t;
- type hugetlbfs_t;
- type ibacm_t;
- type ibacm_var_run_t;
- type inetd_child_exec_t;
- type inetd_child_t;
- type initctl_t;
- type init_exec_t;
- type initrc_state_t;
- type initrc_t;
- type initrc_var_run_t;
- type init_t;
- type init_tmp_t;
- type init_var_lib_t;
- type init_var_run_t;
- type insights_client_t;
- type install_exec_t;
- type install_t;
- type ipsec_conf_file_t;
- type ipsec_t;
- type ipsec_var_run_t;
- type irqbalance_t;
- type iscsi_var_lib_t;
- type jockey_t;
- type journalctl_exec_t;
- type kadmind_t;
- type kdump_crash_t;
- type kdumpctl_t;
- type kdump_t;
- type keepalived_unconfined_script_t;
- type kernel_t;
- type kmod_exec_t;
- type kmod_t;
- type kmscon_t;
- type kmsg_device_t;
- type krb5_keytab_t;
- type ktalkd_exec_t;
- type ktalkd_t;
- type l2tpd_t;
- type lastlog_t;
- type ld_so_cache_t;
- type lldpad_t;
- type loadkeys_t;
- type locale_t;
- type lvm_control_t;
- type lvm_etc_t;
- type lvm_t;
- type lvm_var_run_t;
- type machineid_t;
- type mail_spool_t;
- type mandb_t;
- type mdadm_t;
- type mdadm_var_run_t;
- type memcached_t;
- type memory_device_t;
- type mnt_t;
- type modemmanager_t;
- type modules_dep_t;
- type modules_object_t;
- type mon_procd_t;
- type mount_t;
- type mount_var_run_t;
- type mptcpd_t;
- type munin_plugin_domain;
- type munin_t;
- type mysqld_t;
- type mythtv_script_t;
- type naemon_t;
- type nagios_plugin_domain;
- type nagios_system_plugin_t;
- type named_conf_t;
- type named_zone_t;
- type net_conf_t;
- type netlabel_mgmt_t;
- type networkmanager_dispatcher_plugin;
- type NetworkManager_dispatcher_t;
- type NetworkManager_priv_helper_t;
- type NetworkManager_t;
- type nfsd_fs_t;
- type nfsidmap_t;
- type ninfod_t;
- type nrpe_exec_t;
- type nrpe_t;
- type nsfs_t;
- type openshift_cgroup_read_t;
- type openshift_net_read_t;
- type oracleasm_t;
- type passwd_file_t;
- type pcscd_t;
- type pdns_t;
- type pegasus_openlmi_domain;
- type pkcs_slotd_t;
- type pkcs_slotd_tmpfs_t;
- type plymouthd_t;
- type plymouth_exec_t;
- type policykit_t;
- type postfix_exec_t;
- type print_spool_t;
- type proc_net_t;
- type proc_security_t;
- type ptchown_t;
- type pulseaudio_home_t;
- type qmail_tcp_env_exec_t;
- type qmail_tcp_env_t;
- type qpidd_t;
- type quota_exec_t;
- type quota_t;
- type radiusd_t;
- type random_device_t;
- type random_seed_t;
- type rdisc_t;
- type rhsmcertd_t;
- type rlogind_exec_t;
- type rlogind_t;
- type root_t;
- type rpm_script_t;
- type rpm_var_cache_t;
- type rpm_var_lib_t;
- type rshd_exec_t;
- type rshd_t;
- type rsync_exec_t;
- type rsync_t;
- type rustdesk_exec_t;
- type rustdesk_t;
- type sblim_domain;
- type security_t;
- type selinux_config_t;
- type selinux_login_config_t;
- type semanage_store_t;
- type session_dbusd_tmp_t;
- type shell_exec_t;
- type smbcontrol_t;
- type smokeping_cgi_script_t;
- type spc_t;
- type speech_dispatcher_t;
- type sshd_exec_t;
- type sshd_t;
- type ssh_keysign_t;
- type sslh_t;
- type sssd_var_lib_t;
- type staff_t;
- type stratisd_data_t;
- type stunnel_exec_t;
- type stunnel_t;
- type sudo_exec_t;
- type sulogin_exec_t;
- type sulogin_t;
- type svc_start_exec_t;
- type svc_start_t;
- type svirt_file_type;
- type svirt_sandbox_domain;
- type svirt_t;
- type svirt_tcg_t;
- type swat_exec_t;
- type swat_t;
- type sysctl_kernel_t;
- type sysfs_t;
- type syslogd_t;
- type systemd_bootchart_t;
- type system_dbusd_t;
- type system_dbusd_var_run_t;
- type systemd_coredump_t;
- type systemd_gpt_generator_t;
- type systemd_home_t;
- type systemd_hostnamed_t;
- type systemd_hwdb_t;
- type systemd_importd_t;
- type systemd_initctl_t;
- type systemd_journal_upload_t;
- type systemd_localed_t;
- type systemd_logger_t;
- type systemd_logind_inhibit_var_run_t;
- type systemd_logind_sessions_t;
- type systemd_logind_t;
- type systemd_logind_var_run_t;
- type systemd_machined_t;
- type systemd_modules_load_t;
- type systemd_mount_directory;
- type systemd_networkd_exec_t;
- type systemd_networkd_t;
- type systemd_network_generator_t;
- type systemd_notify_t;
- type systemd_passwd_agent_exec_t;
- type systemd_passwd_agent_t;
- type systemd_passwd_var_run_t;
- type systemd_pstore_t;
- type systemd_resolved_exec_t;
- type systemd_resolved_t;
- type systemd_rfkill_t;
- type systemd_rfkill_var_lib_t;
- type systemd_sleep_t;
- type systemd_socket_proxyd_t;
- type systemd_sysctl_t;
- type systemd_systemctl_exec_t;
- type systemd_timedated_t;
- type systemd_timedated_var_lib_t;
- type systemd_tmpfiles_t;
- type systemd_userdbd_runtime_t;
- type systemd_userdbd_t;
- type tangd_db_t;
- type tangd_t;
- type targetclid_t;
- type tcpd_exec_t;
- type tcpd_t;
- type telnetd_exec_t;
- type telnetd_t;
- type tftpd_exec_t;
- type tftpd_t;
- type thin_domain;
- type thumb_t;
- type timedatex_t;
- type tlp_t;
- type tmpfs_t;
- type tmpreaper_t;
- type tmp_t;
- type tpm_device_t;
- type tty_device_t;
- type udev_rules_t;
- type udev_t;
- type unconfined_dbusd_t;
- type unconfined_service_t;
- type unconfined_t;
- type unlabeled_t;
- type unreserved_port_t;
- type updpwd_exec_t;
- type updpwd_t;
- type urandom_device_t;
- type usbtty_device_t;
- type user_devpts_t;
- type user_fonts_cache_t;
- type user_home_dir_t;
- type user_home_t;
- type user_t;
- type user_tmp_t;
- type user_tty_device_t;
- type usr_t;
- type uucpd_exec_t;
- type uucpd_t;
- type uuidd_t;
- type uuidd_var_run_t;
- type var_lib_nfs_t;
- type var_lib_t;
- type var_log_t;
- type var_run_t;
- type var_spool_t;
- type var_t;
- type virsh_t;
- type virtd_t;
- type virt_etc_rw_t;
- type virtio_device_t;
- type vnstatd_t;
- type watchdog_device_t;
- type watchdog_t;
- type wireguard_t;
- type wireless_device_t;
- type wtmp_t;
- type xdm_exec_t;
- type xdm_t;
- type xdm_var_lib_t;
- type xenconsoled_t;
- type xend_t;
- type xguest_t;
- type xserver_port_t;
- type xserver_t;
-')
-
-##############################################################################
-#
-# Teil 1. Die folgenden Regeln stammen hauptsächlich aus der Open-Source-Datei `init.te`.
-# https://github.com/fedora-selinux/selinux-policy/blob/rawhide/policy/modules/system/init.te
-#
-# Hinweis: Teil 1 wird wahrscheinlich weitgehend mit Teil 3 identisch sein. Aber für den Moment ist es akzeptabel.
-#
-
-init_daemon_domain(rustdesk_t, rustdesk_exec_t)
-
-domain_role_change_exemption(rustdesk_t)
-domain_subj_id_change_exemption(rustdesk_t)
-domain_obj_id_change_exemption(rustdesk_t)
-role system_r types rustdesk_t;
-corecmd_shell_entry_type(rustdesk_t)
-typeattribute rustdesk_t init_script_domain_type;
-
-
-#######################################
-
-# Möglichkeiten nutzen, alte Regel:
-allow rustdesk_t self:capability ~{ audit_control audit_write sys_module };
-allow rustdesk_t self:capability2 ~{ mac_admin mac_override };
-allow rustdesk_t self:cap_userns all_cap_userns_perms;
-allow rustdesk_t self:tcp_socket { listen accept };
-allow rustdesk_t self:packet_socket create_socket_perms;
-allow rustdesk_t self:key manage_key_perms;
-allow rustdesk_t self:bpf { map_create map_read map_write prog_load prog_run };
-
-allow rustdesk_t self:file mounton;
-allow rustdesk_t self:fifo_file rw_fifo_file_perms;
-
-allow rustdesk_t self:service manage_service_perms;
-allow rustdesk_t self:user_namespace create;
-
-# Sich selbst erneut ausführen
-can_exec(rustdesk_t, rustdesk_exec_t)
-# Ausführen des Inhalts von /run/initramfs
-manage_files_pattern(rustdesk_t, initrc_state_t, initrc_state_t)
-can_exec(rustdesk_t, initrc_state_t)
-
-allow rustdesk_t initrc_t:unix_stream_socket { connectto create_stream_socket_perms };
-allow rustdesk_t initrc_t:tcp_socket create_stream_socket_perms;
-allow initrc_t rustdesk_t:unix_stream_socket { connectto rw_stream_socket_perms sendto };
-allow initrc_t rustdesk_t:fifo_file rw_fifo_file_perms;
-
-manage_files_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-manage_dirs_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-manage_lnk_files_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-manage_sock_files_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-files_tmp_filetrans(rustdesk_t, init_tmp_t, { file sock_file })
-allow rustdesk_t init_tmp_t:file map;
-
-manage_dirs_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-manage_files_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-manage_lnk_files_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-manage_sock_files_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-files_var_lib_filetrans(rustdesk_t, init_var_lib_t, { dir file })
-allow rustdesk_t init_var_lib_t:dir mounton;
-allow rustdesk_t init_var_lib_t:file map;
-
-manage_dirs_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_lnk_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_sock_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_fifo_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_blk_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_chr_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-files_pid_filetrans(rustdesk_t, init_var_run_t, { dir file blk_file chr_file fifo_file})
-allow rustdesk_t init_var_run_t:dir mounton;
-allow rustdesk_t init_var_run_t:file mounton;
-allow rustdesk_t init_var_run_t:sock_file relabelto;
-allow rustdesk_t init_var_run_t:blk_file { getattr relabelto };
-allow rustdesk_t init_var_run_t:chr_file { getattr relabelto };
-allow rustdesk_t init_var_run_t:fifo_file { getattr relabelto };
-
-allow rustdesk_t machineid_t:file manage_file_perms;
-files_pid_filetrans(rustdesk_t, machineid_t, file, "machine-id")
-files_etc_filetrans(rustdesk_t, machineid_t, file, "machine-id")
-allow rustdesk_t machineid_t:file mounton;
-
-allow rustdesk_t initctl_t:fifo_file manage_fifo_file_perms;
-dev_filetrans(rustdesk_t, initctl_t, fifo_file)
-
-# utmp ändern
-allow rustdesk_t initrc_var_run_t:file { rw_file_perms setattr };
-
-kernel_read_system_state(rustdesk_t)
-kernel_share_state(rustdesk_t)
-kernel_stream_connect(rustdesk_t)
-kernel_rw_stream_socket_perms(rustdesk_t)
-kernel_rw_unix_dgram_sockets(rustdesk_t)
-kernel_mounton_systemd_ProtectKernelTunables(rustdesk_t)
-kernel_read_core_if(rustdesk_t)
-kernel_mounton_core_if(rustdesk_t)
-kernel_mounton_all_sysctls(rustdesk_t)
-kernel_get_sysvipc_info(rustdesk_t)
-kernel_load_module(rustdesk_t)
-kernel_read_all_proc(rustdesk_t)
-kernel_list_all_proc(rustdesk_t)
-kernel_mounton_all_proc(rustdesk_t)
-
-# Es gibt einen Fehler im Kernel 4.16, bei dem viele Domains module_request anfordern, also vorerst kein Auditing
-kernel_dontaudit_request_load_module(rustdesk_t)
-
-corecmd_exec_chroot(rustdesk_t)
-corecmd_exec_bin(rustdesk_t)
-
-corenet_all_recvfrom_netlabel(rustdesk_t)
-corenet_tcp_bind_all_ports(rustdesk_t)
-corenet_udp_bind_all_ports(rustdesk_t)
-
-dev_create_all_files(rustdesk_t)
-dev_create_all_chr_files(rustdesk_t)
-dev_list_sysfs(rustdesk_t)
-dev_manage_sysfs(rustdesk_t)
-dev_mounton_all_device_nodes(rustdesk_t)
-dev_setattr_all_blk_files(rustdesk_t)
-dev_setattr_all_chr_files(rustdesk_t)
-dev_read_urand(rustdesk_t)
-dev_read_raw_memory(rustdesk_t)
-# Frühes devtmpfs
-dev_rw_generic_chr_files(rustdesk_t)
-dev_filetrans_all_named_dev(rustdesk_t)
-dev_write_watchdog(rustdesk_t)
-dev_rw_inherited_input_dev(rustdesk_t)
-dev_rw_dri(rustdesk_t)
-dev_rw_tpm(rustdesk_t)
-
-domain_getpgid_all_domains(rustdesk_t)
-domain_kill_all_domains(rustdesk_t)
-domain_signal_all_domains(rustdesk_t)
-domain_signull_all_domains(rustdesk_t)
-domain_sigstop_all_domains(rustdesk_t)
-domain_sigchld_all_domains(rustdesk_t)
-domain_read_all_domains_state(rustdesk_t)
-domain_getattr_all_domains(rustdesk_t)
-domain_setrlimit_all_domains(rustdesk_t)
-domain_rlimitinh_all_domains(rustdesk_t)
-domain_noatsecure_all_domains(rustdesk_t)
-domain_setpriority_all_domains(rustdesk_t)
-
-files_read_config_files(rustdesk_t)
-files_read_all_pids(rustdesk_t)
-files_map_all_pids(rustdesk_t)
-files_read_system_conf_files(rustdesk_t)
-files_rw_generic_pids(rustdesk_t)
-files_dontaudit_search_isid_type_dirs(rustdesk_t)
-files_read_isid_type_files(rustdesk_t)
-files_read_etc_runtime_files(rustdesk_t)
-files_manage_all_locks(rustdesk_t)
-files_manage_etc_runtime_files(rustdesk_t)
-files_manage_etc_symlinks(rustdesk_t)
-files_etc_filetrans_etc_runtime(rustdesk_t, file)
-# /etc/X11/prefdm ausführen
-files_exec_etc_files(rustdesk_t)
-files_read_usr_files(rustdesk_t)
-files_write_root_dirs(rustdesk_t)
-# Dateideskriptoren, die von rootfs geerbt wurden
-files_dontaudit_rw_root_files(rustdesk_t)
-files_dontaudit_rw_root_chr_files(rustdesk_t)
-files_dontaudit_mounton_modules_object(rustdesk_t)
-files_manage_mnt_dirs(rustdesk_t)
-files_manage_mnt_files(rustdesk_t)
-files_read_mnt_symlinks(rustdesk_t)
-files_mounton_etc(rustdesk_t)
-files_create_default_dir(rustdesk_t)
-files_remount_rootfs(rustdesk_t)
-files_create_var_dirs(rustdesk_t)
-files_watch_non_security_dirs(rustdesk_t)
-files_watch_non_security_files(rustdesk_t)
-files_watch_non_security_lnk_files(rustdesk_t)
-
-fs_read_efivarfs_files(rustdesk_t)
-fs_setattr_efivarfs_files(rustdesk_t)
-fs_read_nfsd_files(rustdesk_t)
-
-fstools_getattr_swap_files(rustdesk_t)
-
-mcs_process_set_categories(rustdesk_t)
-
-mls_file_read_all_levels(rustdesk_t)
-mls_file_write_all_levels(rustdesk_t)
-mls_file_downgrade(rustdesk_t)
-mls_file_upgrade(rustdesk_t)
-mls_fd_use_all_levels(rustdesk_t)
-mls_fd_share_all_levels(rustdesk_t)
-mls_process_set_level(rustdesk_t)
-mls_process_write_down(rustdesk_t)
-mls_socket_read_all_levels(rustdesk_t)
-mls_socket_write_all_levels(rustdesk_t)
-mls_rangetrans_source(rustdesk_t)
-
-selinux_set_all_booleans(rustdesk_t)
-selinux_load_policy(rustdesk_t)
-selinux_mounton_fs(rustdesk_t)
-allow rustdesk_t security_t:security load_policy;
-
-selinux_compute_access_vector(rustdesk_t)
-selinux_compute_create_context(rustdesk_t)
-selinux_compute_user_contexts(rustdesk_t)
-selinux_validate_context(rustdesk_t)
-selinux_compute_relabel_context(rustdesk_t)
-selinux_unmount_fs(rustdesk_t)
-
-term_create_pty_dir(rustdesk_t)
-term_use_unallocated_ttys(rustdesk_t)
-term_setattr_unallocated_ttys(rustdesk_t)
-term_use_console(rustdesk_t)
-term_use_all_inherited_terms(rustdesk_t)
-term_use_usb_ttys(rustdesk_t)
-term_use_all_ptys(rustdesk_t)
-term_setattr_all_ptys(rustdesk_t)
-term_use_virtio_console(rustdesk_t)
-term_watch_console_dev(rustdesk_t)
-term_watch_reads_console_dev(rustdesk_t)
-term_watch_unallocated_ttys(rustdesk_t)
-term_watch_reads_unallocated_ttys(rustdesk_t)
-term_watch_user_ttys(rustdesk_t)
-term_watch_reads_user_ttys(rustdesk_t)
-
-# Init-Skripte ausführen
-init_domtrans_script(rustdesk_t)
-init_exec_notrans_direct_init_entry(rustdesk_t)
-
-libs_rw_ld_so_cache(rustdesk_t)
-
-logging_create_devlog_dev(rustdesk_t)
-logging_send_syslog_msg(rustdesk_t)
-logging_send_audit_msgs(rustdesk_t)
-logging_manage_generic_logs(rustdesk_t)
-logging_mmap_generic_logs(rustdesk_t)
-logging_relabel_devlog_dev(rustdesk_t)
-logging_manage_audit_config(rustdesk_t)
-logging_create_syslog_netlink_audit_socket(rustdesk_t)
-logging_write_var_log_dirs(rustdesk_t)
-logging_manage_var_log_symlinks(rustdesk_t)
-
-seutil_read_config(rustdesk_t)
-seutil_read_login_config(rustdesk_t)
-seutil_read_default_contexts(rustdesk_t)
-seutil_read_module_store(rustdesk_t)
-
-miscfiles_manage_localization(rustdesk_t)
-miscfiles_filetrans_named_content(rustdesk_t)
-
-udev_manage_rules_files(rustdesk_t)
-
-userdom_use_user_ttys(rustdesk_t)
-userdom_manage_tmp_dirs(rustdesk_t)
-userdom_manage_tmp_sockets(rustdesk_t)
-userdom_delete_user_tmp_files(rustdesk_t)
-userdom_delete_user_home_content_files(rustdesk_t)
-userdom_connectto_stream(rustdesk_t)
-userdom_rw_inherited_user_pipes(rustdesk_t)
-userdom_transition_login_userdomain(rustdesk_t)
-userdom_nnp_transition_login_userdomain(rustdesk_t)
-userdom_noatsecure_login_userdomain(rustdesk_t)
-userdom_sigchld_login_userdomain(rustdesk_t)
-userdom_use_user_ptys(rustdesk_t)
-userdom_watch_user_ptys(rustdesk_t)
-userdom_watch_reads_user_ptys(rustdesk_t)
-
-allow rustdesk_t self:process setsched;
-
-ifdef(`distro_redhat',`
- fs_manage_tmpfs_files(rustdesk_t)
- fs_manage_tmpfs_symlinks(rustdesk_t)
- fs_manage_tmpfs_sockets(rustdesk_t)
- fs_manage_tmpfs_chr_files(rustdesk_t)
- fs_exec_tmpfs_files(rustdesk_t)
- fs_read_tmpfs_symlinks(rustdesk_t)
- fs_tmpfs_filetrans(rustdesk_t, initctl_t, fifo_file)
- fs_tmpfs_filetrans_named_content(rustdesk_t)
- fs_relabelfrom_tmpfs_lnk_files(rustdesk_t)
-
- logging_stream_connect_syslog(rustdesk_t)
- logging_relabel_syslog_pid_socket(rustdesk_t)
-')
-
-corecmd_shell_domtrans(rustdesk_t, initrc_t)
-
-storage_raw_rw_fixed_disk(rustdesk_t)
-
-sysnet_read_dhcpc_state(rustdesk_t)
-
-allow rustdesk_t self:system all_system_perms;
-allow rustdesk_t self:system module_load;
-allow rustdesk_t self:unix_dgram_socket { create_socket_perms sendto };
-allow rustdesk_t self:process { setkeycreate setsockcreate setfscreate setrlimit setexec };
-allow rustdesk_t self:process { getcap setcap };
-allow rustdesk_t self:unix_stream_socket { create_stream_socket_perms connectto recvfrom };
-allow rustdesk_t self:netlink_kobject_uevent_socket create_socket_perms;
-allow rustdesk_t self:netlink_selinux_socket create_socket_perms;
-allow rustdesk_t self:unix_dgram_socket lock;
-# Bis systemd repariert ist
-allow daemon rustdesk_t:socket_class_set { getopt read getattr ioctl setopt write };
-allow rustdesk_t self:udp_socket create_socket_perms;
-allow rustdesk_t self:netlink_route_socket create_netlink_socket_perms;
-
-allow rustdesk_t initrc_t:unix_dgram_socket create_socket_perms;
-
-kernel_list_unlabeled(rustdesk_t)
-kernel_read_unlabeled_lnk_files(rustdesk_t)
-kernel_read_network_state(rustdesk_t)
-kernel_rw_all_sysctls(rustdesk_t)
-kernel_rw_security_state(rustdesk_t)
-kernel_rw_usermodehelper_state(rustdesk_t)
-kernel_read_software_raid_state(rustdesk_t)
-kernel_unmount_debugfs(rustdesk_t)
-kernel_setsched(rustdesk_t)
-kernel_mounton_kernel_sysctl(rustdesk_t)
-
-dev_write_kmsg(rustdesk_t)
-dev_write_urand(rustdesk_t)
-dev_rw_lvm_control(rustdesk_t)
-dev_rw_autofs(rustdesk_t)
-dev_manage_generic_symlinks(rustdesk_t)
-dev_manage_generic_dirs(rustdesk_t)
-dev_manage_generic_files(rustdesk_t)
-dev_read_generic_chr_files(rustdesk_t)
-dev_relabel_generic_dev_dirs(rustdesk_t)
-dev_relabel_all_dev_nodes(rustdesk_t)
-dev_relabel_all_dev_files(rustdesk_t)
-dev_manage_sysfs_dirs(rustdesk_t)
-dev_relabel_sysfs_dirs(rustdesk_t)
-dev_rw_wireless(rustdesk_t)
-
-files_search_all(rustdesk_t)
-files_mounton_all_mountpoints(rustdesk_t)
-files_unmount_all_file_type_fs(rustdesk_t)
-files_remount_all_file_type_fs(rustdesk_t)
-files_mounton_kernel_symbol_table(rustdesk_t)
-files_manage_all_pid_dirs(rustdesk_t)
-files_write_all_pid_sockets(rustdesk_t)
-files_manage_etc_dirs(rustdesk_t)
-files_manage_generic_tmp_dirs(rustdesk_t)
-files_relabel_all_pid_dirs(rustdesk_t)
-files_relabel_all_pid_files(rustdesk_t)
-files_create_all_pid_sockets(rustdesk_t)
-files_delete_all_pids(rustdesk_t)
-files_exec_generic_pid_files(rustdesk_t)
-files_create_all_pid_pipes(rustdesk_t)
-files_create_all_spool_sockets(rustdesk_t)
-files_delete_all_spool_sockets(rustdesk_t)
-files_create_var_lib_dirs(rustdesk_t)
-files_create_var_lib_symlinks(rustdesk_t)
-files_read_var_lib_symlinks(rustdesk_t)
-files_manage_urandom_seed(rustdesk_t)
-files_list_locks(rustdesk_t)
-files_list_spool(rustdesk_t)
-files_list_var(rustdesk_t)
-files_write_var_dirs(rustdesk_t)
-files_manage_var_symlinks(rustdesk_t)
-files_setattr_var_dirs(rustdesk_t)
-files_list_boot(rustdesk_t)
-files_list_home(rustdesk_t)
-files_create_lock_dirs(rustdesk_t)
-files_relabel_all_files(rustdesk_t)
-files_read_kernel_modules(rustdesk_t)
-files_map_kernel_modules(rustdesk_t)
-files_dontaudit_mounton_isid(rustdesk_t)
-files_delete_tmp_files(rustdesk_t)
-files_delete_tmp_pipes(rustdesk_t)
-files_delete_tmp_sockets(rustdesk_t)
-fs_getattr_all_fs(rustdesk_t)
-fs_manage_cgroup_dirs(rustdesk_t)
-fs_manage_cgroup_files(rustdesk_t)
-fs_manage_bpf_dirs(rustdesk_t)
-fs_manage_bpf_files(rustdesk_t)
-fs_manage_hugetlbfs_dirs(rustdesk_t)
-fs_manage_tmpfs_dirs(rustdesk_t)
-fs_relabel_tmpfs_blk_file(rustdesk_t)
-fs_relabel_tmpfs_chr_file(rustdesk_t)
-fs_relabel_pstore_dirs(rustdesk_t)
-fs_relabel_tmpfs_dirs(rustdesk_t)
-fs_relabel_tmpfs_files(rustdesk_t)
-fs_relabel_tmpfs_fifo_files(rustdesk_t)
-fs_mount_all_fs(rustdesk_t)
-fs_unmount_all_fs(rustdesk_t)
-fs_remount_all_fs(rustdesk_t)
-fs_list_all(rustdesk_t)
-fs_list_auto_mountpoints(rustdesk_t)
-fs_register_binary_executable_type(rustdesk_t)
-fs_relabel_tmpfs_sock_file(rustdesk_t)
-fs_rw_tmpfs_files(rustdesk_t)
-fs_relabel_cgroup_dirs(rustdesk_t)
-fs_search_cgroup_dirs(rustdesk_t)
-# Für Netzwerk-Namensräume
-fs_read_nsfs_files(rustdesk_t)
-
-storage_getattr_removable_dev(rustdesk_t)
-
-term_relabel_ptys_dirs(rustdesk_t)
-
-auth_relabel_login_records(rustdesk_t)
-auth_relabel_pam_console_data_dirs(rustdesk_t)
-auth_manage_faillog(rustdesk_t)
-
-clock_read_adjtime(rustdesk_t)
-
-init_read_script_state(rustdesk_t)
-
-seutil_read_file_contexts(rustdesk_t)
-
-systemd_exec_systemctl(rustdesk_t)
-systemd_manage_home_content(rustdesk_t)
-systemd_manage_unit_dirs(rustdesk_t)
-systemd_manage_random_seed(rustdesk_t)
-systemd_manage_all_unit_files(rustdesk_t)
-systemd_logger_stream_connect(rustdesk_t)
-systemd_login_manage_pid_files(rustdesk_t)
-systemd_config_all_services(rustdesk_t)
-systemd_relabelto_fifo_file_passwd_run(rustdesk_t)
-systemd_relabel_unit_dirs(rustdesk_t)
-systemd_relabel_unit_files(rustdesk_t)
-systemd_relabel_unit_symlinks(rustdesk_t)
-systemd_login_status(rustdesk_t)
-systemd_map_networkd_exec_files(rustdesk_t)
-systemd_map_resolved_exec_files(rustdesk_t)
-systemd_rfkill_setattr_lib(rustdesk_t)
-systemd_rfkill_mounton_var_lib(rustdesk_t)
-systemd_rfkill_manage_lib_dirs(rustdesk_t)
-systemd_timedated_mounton_var_lib(rustdesk_t)
-systemd_mounton_inhibit_dir(rustdesk_t)
-systemd_timedated_manage_lib_dirs(rustdesk_t)
-systemd_login_mounton_pid_dirs(rustdesk_t)
-systemd_mounton_inherited_logind_sessions_dirs(rustdesk_t)
-systemd_delete_private_tmp(rustdesk_t)
-systemd_userdbd_stream_connect(rustdesk_t)
-systemd_userdbd_runtime_filetrans(rustdesk_t)
-systemd_userdbd_runtime_manage_symlinks(rustdesk_t)
-systemd_write_inherited_logind_sessions_pipes(rustdesk_t)
-
-create_sock_files_pattern(rustdesk_t, init_sock_file_type, init_sock_file_type)
-
-create_dirs_pattern(rustdesk_t, var_log_t, var_log_t)
-
-auth_use_nsswitch(rustdesk_t)
-auth_rw_login_records(rustdesk_t)
-auth_rw_lastlog(rustdesk_t)
-auth_domtrans_chk_passwd(rustdesk_t)
-auth_manage_passwd(rustdesk_t)
-
-allow rustdesk_t var_run_t:dir relabelto;
-
-allow rustdesk_t daemon:unix_stream_socket create_stream_socket_perms;
-allow rustdesk_t daemon:unix_dgram_socket create_socket_perms;
-allow rustdesk_t daemon:tcp_socket create_stream_socket_perms;
-allow rustdesk_t daemon:udp_socket create_socket_perms;
-allow daemon rustdesk_t:unix_dgram_socket sendto;
-# Muss in /var/run/systemd/notify schreiben
-init_write_pid_socket(daemon)
-allow daemon rustdesk_t:unix_stream_socket { append write read getattr ioctl };
-
-allow rustdesk_t daemon:process siginh;
-
-ifdef(`hide_broken_symptoms',`
- # RHEL4-Systeme scheinen einen Fehler zu haben
- # fds aus der initrd öffnen
- ifdef(`distro_rhel4',`
- kernel_dontaudit_use_fds(daemon)
- ')
-
- dontaudit daemon rustdesk_t:dir search_dir_perms;
- dontaudit daemon rustdesk_t:file read_file_perms;
-')
-
-dontaudit systemprocess rustdesk_t:unix_stream_socket getattr;
-
-allow rustdesk_t daemon:unix_stream_socket create_stream_socket_perms;
-allow rustdesk_t daemon:unix_dgram_socket create_socket_perms;
-allow daemon rustdesk_t:unix_stream_socket ioctl;
-allow daemon rustdesk_t:unix_dgram_socket sendto;
-
-# Handhabung des direkten Übergangs von upstart/systemd zu einer ausführbaren Datei
-allow rustdesk_t systemprocess:process { dyntransition siginh };
-allow rustdesk_t systemprocess:unix_stream_socket create_stream_socket_perms;
-allow rustdesk_t systemprocess:unix_dgram_socket create_socket_perms;
-allow systemprocess rustdesk_t:unix_dgram_socket sendto;
-allow systemprocess rustdesk_t:unix_stream_socket { append write read getattr ioctl };
-
-
-##############################################################################
-#
-# Teil 2. Die folgenden Regeln werden erstellt von
-# `grep rustdesk /var/log/audit/audit.log | audit2allow -a -M test`
-#
-
-#============= rustdesk_t ==============
-corenet_tcp_connect_unreserved_ports(rustdesk_t)
-
-allow rustdesk_t self:process execmem;
-allow rustdesk_t data_home_t:dir { add_name create remove_name write };
-allow rustdesk_t config_home_t:dir { write add_name remove_name };
-allow rustdesk_t data_home_t:file { create link open read rename setattr unlink write };
-allow rustdesk_t config_home_t:file { create link open read rename setattr unlink write };
-allow rustdesk_t sudo_exec_t:file { execute execute_no_trans map open read } ;
-allow rustdesk_t systemd_logind_t:dbus send_msg;
-allow rustdesk_t tmp_t:file { setattr open setattr unlink write unlink };
-allow rustdesk_t user_tmp_t:file { open write read link unlink map };
-allow systemd_coredump_t rustdesk_exec_t:file read;
-allow rustdesk_t event_device_t:chr_file { append open ioctl lock read write };
-allow rustdesk_t session_dbusd_tmp_t:sock_file write;
-allow rustdesk_t unconfined_dbusd_t:unix_stream_socket connectto;
-allow unconfined_t rustdesk_exec_t:file { execute getattr open read };
-allow init_t rustdesk_exec_t:file getattr;
-allow rustdesk_t pulseaudio_home_t:file { read open write lock };
-allow rustdesk_t user_fonts_cache_t:dir { add_name remove_name } ;
-allow rustdesk_t user_fonts_cache_t:file { create open read write lock unlink };
-
-#!!!! Dieser AVC kann mit dem booleschen Wert 'nis_enabled' zugelassen werden
-allow rustdesk_t unreserved_port_t:tcp_socket name_connect;
-allow rustdesk_t xserver_port_t:tcp_socket name_connect;
-allow rustdesk_t xserver_t:unix_stream_socket connectto;
-allow rustdesk_t ephemeral_port_t:tcp_socket name_connect;
-
-
-##############################################################################
-#
-# Teil 3. Die folgenden Regeln gehören zu den vom System installierten Regeln.
-# `dnf install setools-console`
-# `sesearch -A | grep 'allow init_t ' | sed 's/allow init_t /allow rustdesk_t /g'`
-#
-
-#============= Zusammenführen von init_t ==============
-allow rustdesk_t abrt_dump_oops_t:dbus send_msg;
-allow rustdesk_t abrt_upload_watch_t:dbus send_msg;
-allow rustdesk_t adjtime_t:file { ioctl lock open read };
-allow rustdesk_t aiccu_t:dbus send_msg;
-allow rustdesk_t amanda_inetd_exec_t:file ioctl;
-allow rustdesk_t amanda_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t antivirus_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t apcupsd_power_t:file { ioctl lock open read };
-allow rustdesk_t auditd_etc_t:dir { add_name remove_name write };
-allow rustdesk_t auditd_etc_t:file { append create ioctl link lock open read rename setattr unlink watch watch_reads write };
-allow rustdesk_t autofs_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t base_ro_file_type:file { execute execute_no_trans map };
-allow rustdesk_t binfmt_misc_fs_t:file { append ioctl lock open read write };
-allow rustdesk_t bitlbee_exec_t:file ioctl;
-allow rustdesk_t bitlbee_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t boltd_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t boltd_var_lib_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t boltd_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t boltd_var_lib_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t boltd_var_run_t:dir mounton;
-allow rustdesk_t boolean_type:dir { getattr ioctl lock open read search };
-allow rustdesk_t boolean_type:file { append getattr ioctl lock open read write };
-allow rustdesk_t boothd_t:dbus send_msg;
-allow rustdesk_t bootloader_exec_t:file { execute ioctl map open read };
-allow rustdesk_t bootloader_t:process transition;
-allow rustdesk_t bpf_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t bpf_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t bpf_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t bugzilla_script_t:dbus send_msg;
-allow rustdesk_t certwatch_t:dbus send_msg;
-allow rustdesk_t cgroup_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t cgroup_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t cgroup_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t cgroup_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t chkpwd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t chkpwd_t:process transition;
-allow rustdesk_t chronyc_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t chronyd_exec_t:file ioctl;
-allow rustdesk_t chronyd_keys_t:file { ioctl lock open read };
-allow rustdesk_t chronyd_restricted_t:dbus send_msg;
-allow rustdesk_t chronyd_restricted_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t chronyd_restricted_t:process transition;
-allow rustdesk_t chroot_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t cifs_helper_t:dbus send_msg;
-allow rustdesk_t cinder_domain:dbus send_msg;
-allow rustdesk_t cloudform_domain:dbus send_msg;
-allow rustdesk_t collectd_script_t:dbus send_msg;
-allow rustdesk_t comsat_exec_t:file { execute ioctl map open read };
-allow rustdesk_t comsat_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t comsat_t:process transition;
-allow rustdesk_t comsat_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t configfile:file { ioctl lock open read };
-allow rustdesk_t configfile:lnk_file read;
-allow rustdesk_t console_device_t:chr_file { read watch watch_reads };
-allow rustdesk_t consolekit_log_t:dir { add_name remove_name write };
-allow rustdesk_t consolekit_log_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t container_kvm_t:dbus send_msg;
-allow rustdesk_t container_runtime_domain:dbus send_msg;
-allow rustdesk_t container_runtime_tmpfs_t:file { ioctl lock open read };
-allow rustdesk_t container_runtime_tmpfs_t:lnk_file read;
-allow rustdesk_t container_var_lib_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t container_var_lib_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t container_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t crack_t:dbus send_msg;
-allow rustdesk_t cups_brf_t:dbus send_msg;
-allow rustdesk_t cupsd_exec_t:file ioctl;
-allow rustdesk_t cupsd_lpd_exec_t:file ioctl;
-allow rustdesk_t cupsd_lpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t cupsd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t cvs_exec_t:file ioctl;
-allow rustdesk_t cvs_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t daemon:fifo_file { append getattr ioctl lock open write };
-allow rustdesk_t daemon:process siginh;
-allow rustdesk_t daemon:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t daemon:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t daemon:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t daemon:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t dbskkd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t dbskkd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t dbskkd_t:process transition;
-allow rustdesk_t dbskkd_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t default_context_t:file { ioctl lock open read };
-allow rustdesk_t default_t:dir create;
-allow rustdesk_t devicekit_disk_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t devicekit_power_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t devicekit_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t device_node:blk_file { getattr mounton relabelfrom relabelto setattr };
-allow rustdesk_t device_node:chr_file { create getattr mounton relabelfrom relabelto setattr };
-allow rustdesk_t device_node:dir { getattr relabelfrom relabelto };
-allow rustdesk_t device_node:fifo_file { getattr relabelfrom relabelto };
-allow rustdesk_t device_node:file { create getattr mounton open relabelfrom relabelto };
-allow rustdesk_t device_node:lnk_file { getattr relabelfrom relabelto };
-allow rustdesk_t device_node:sock_file { getattr relabelfrom relabelto };
-allow rustdesk_t device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t device_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t device_t:file { append ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t device_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t devlog_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t devlog_t:sock_file { create ioctl link lock read rename setattr unlink };
-allow rustdesk_t devpts_t:chr_file { append ioctl lock read write };
-allow rustdesk_t devpts_t:dir create;
-allow rustdesk_t dhcpc_state_t:file { ioctl lock open read };
-allow rustdesk_t dhcp_state_t:file setattr;
-allow rustdesk_t direct_init_entry:file execute_no_trans;
-allow rustdesk_t dirsrvadmin_script_t:dbus send_msg;
-allow rustdesk_t domain:dir { getattr ioctl lock open read search };
-allow rustdesk_t domain:file { getattr ioctl lock open read };
-allow rustdesk_t domain:lnk_file { getattr read };
-allow rustdesk_t domain:process { getattr getpgid noatsecure rlimitinh setrlimit setsched sigchld sigkill signal signull sigstop };
-allow rustdesk_t dri_device_t:chr_file { append ioctl lock map open read write };
-allow rustdesk_t dspam_script_t:dbus send_msg;
-allow rustdesk_t efivarfs_t:file { ioctl lock open read setattr };
-allow rustdesk_t etc_aliases_t:dir { add_name remove_name write };
-allow rustdesk_t etc_aliases_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t etc_aliases_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t etc_runtime_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t etc_runtime_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t etc_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t etc_t:dir { create link mounton rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t etc_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t faillog_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t faillog_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t faillog_t:file { create link open read rename setattr unlink watch_reads write };
-allow rustdesk_t fetchmail_t:dbus send_msg;
-allow rustdesk_t filesystem_type:dir { getattr ioctl lock open read search write };
-allow rustdesk_t filesystem_type:filesystem { getattr mount remount unmount };
-allow rustdesk_t file_type:blk_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:chr_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:dir { getattr ioctl lock open read relabelfrom relabelto search };
-allow rustdesk_t file_type:fifo_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:filesystem { getattr remount unmount };
-allow rustdesk_t file_type:lnk_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:sock_file { getattr relabelfrom relabelto };
-allow rustdesk_t fingerd_exec_t:file ioctl;
-allow rustdesk_t fingerd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t fixed_disk_device_t:blk_file { append ioctl lock open read write };
-allow rustdesk_t fixed_disk_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t fixed_disk_device_t:lnk_file read;
-allow rustdesk_t flatpak_helper_t:dbus send_msg;
-allow rustdesk_t fprintd_exec_t:file { ioctl lock };
-allow rustdesk_t fprintd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t fprintd_var_lib_t:dir { mounton setattr };
-allow rustdesk_t fsadm_t:dbus send_msg;
-allow rustdesk_t fsadm_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t ftpd_exec_t:file ioctl;
-allow rustdesk_t ftpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t fwupd_cache_t:dir { remove_name rmdir write };
-allow rustdesk_t fwupd_cache_t:file unlink;
-allow rustdesk_t fwupd_t:dbus send_msg;
-allow rustdesk_t gconfdefaultsm_t:dbus send_msg;
-allow rustdesk_t geoclue_t:dbus send_msg;
-allow rustdesk_t geoclue_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t getty_exec_t:file ioctl;
-allow rustdesk_t getty_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t gitd_exec_t:file ioctl;
-allow rustdesk_t git_system_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t gnome_home_type:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t gnome_home_type:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t gnome_home_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t gnome_home_type:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t gnomesystemmm_t:dbus send_msg;
-allow rustdesk_t guest_t:dbus send_msg;
-allow rustdesk_t home_bin_t:file { execute execute_no_trans ioctl map open read };
-allow rustdesk_t home_root_t:lnk_file read;
-allow rustdesk_t hostname_etc_t:file unlink;
-allow rustdesk_t httpd_log_t:dir { add_name create setattr write };
-allow rustdesk_t httpd_tmp_t:file unlink;
-allow rustdesk_t httpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t hugetlbfs_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t hugetlbfs_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t ibacm_t:netlink_rdma_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t ibacm_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t ibacm_var_run_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t ibacm_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t inetd_child_exec_t:file ioctl;
-allow rustdesk_t inetd_child_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t initctl_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_exec_t:file { entrypoint execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t initrc_state_t:dir { add_name remove_name write };
-allow rustdesk_t initrc_state_t:file { append create execute execute_no_trans ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t initrc_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t initrc_t:process transition;
-allow rustdesk_t initrc_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t initrc_t:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t initrc_t:unix_stream_socket { accept append bind connect connectto create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t initrc_var_run_t:file { append setattr write };
-allow rustdesk_t init_script_file_type:file { execute ioctl map open read };
-allow rustdesk_t init_script_file_type:service { disable enable reload start status stop };
-allow rustdesk_t init_t:association sendto;
-allow rustdesk_t init_t:bpf { map_create map_read map_write prog_load prog_run };
-allow rustdesk_t init_t:capability2 { audit_read block_suspend bpf checkpoint_restore epolwakeup perfmon syslog wake_alarm };
-allow rustdesk_t init_t:capability { audit_write audit_control sys_module chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t init_t:cap_userns { audit_control audit_write chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_module sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t init_t:dir watch;
-allow rustdesk_t init_t:fifo_file { create link rename setattr unlink append getattr ioctl lock open read write };
-allow rustdesk_t init_t:file { append mounton write };
-allow rustdesk_t init_t:key { create read setattr view write };
-allow rustdesk_t init_t:lnk_file { ioctl lock };
-allow rustdesk_t init_t:lockdown { confidentiality integrity };
-allow rustdesk_t init_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t init_tmp_t:file { create link map open rename setattr unlink watch_reads write };
-allow rustdesk_t init_tmp_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t init_tmp_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_t:netlink_audit_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_relay nlmsg_tty_audit read setattr setopt shutdown write };
-allow rustdesk_t init_t:netlink_kobject_uevent_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:netlink_route_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_write read setattr setopt shutdown write };
-allow rustdesk_t init_t:netlink_selinux_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:packet_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:peer recv;
-allow rustdesk_t init_t:process { fork getcap getsched setcap setexec setfscreate setkeycreate setsockcreate };
-allow rustdesk_t init_t:sem { associate create destroy getattr read setattr unix_read unix_write write };
-allow rustdesk_t init_t:service { disable enable reload start status stop };
-allow rustdesk_t init_t:shm { associate create destroy getattr lock read setattr unix_read unix_write write };
-allow rustdesk_t init_t:system { disable enable halt ipc_info module_load module_request reboot reload start status stop syslog_console syslog_mod syslog_read undefined };
-allow rustdesk_t init_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read sendto setattr setopt shutdown write };
-allow rustdesk_t init_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read recvfrom sendto setattr setopt shutdown write };
-allow rustdesk_t init_t:user_namespace create;
-allow rustdesk_t init_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t init_var_lib_t:dir { create link mounton rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t init_var_lib_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t init_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t init_var_lib_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_var_run_t:blk_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_var_run_t:chr_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_var_run_t:dir mounton;
-allow rustdesk_t init_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t init_var_run_t:file { append create link mounton rename setattr watch_reads write };
-allow rustdesk_t init_var_run_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t init_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t init_var_run_t:sock_file { ioctl link lock rename };
-allow rustdesk_t insights_client_t:fifo_file read;
-allow rustdesk_t install_exec_t:file { execute ioctl map open read };
-allow rustdesk_t install_t:dbus send_msg;
-allow rustdesk_t install_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t install_t:process transition;
-allow rustdesk_t install_t:unix_stream_socket { accept append bind connect connectto create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t ipsec_conf_file_t:file { ioctl lock open read };
-allow rustdesk_t ipsec_t:unix_stream_socket connectto;
-allow rustdesk_t ipsec_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t irqbalance_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t iscsi_var_lib_t:file { ioctl lock open read };
-allow rustdesk_t jockey_t:dbus send_msg;
-allow rustdesk_t journalctl_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t kadmind_t:dbus send_msg;
-allow rustdesk_t kdump_crash_t:file { ioctl lock open read };
-allow rustdesk_t kdumpctl_t:dbus send_msg;
-allow rustdesk_t kdump_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t keepalived_unconfined_script_t:dbus send_msg;
-allow rustdesk_t kernel_t:dbus send_msg;
-allow rustdesk_t kernel_t:fd use;
-allow rustdesk_t kernel_t:fifo_file { append getattr ioctl lock read write };
-allow rustdesk_t kernel_t:system ipc_info;
-allow rustdesk_t kernel_t:unix_dgram_socket { getattr ioctl read write };
-allow rustdesk_t kernel_t:unix_stream_socket { append bind connect getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t kmod_exec_t:file ioctl;
-allow rustdesk_t kmod_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t kmscon_t:dbus send_msg;
-allow rustdesk_t kmsg_device_t:chr_file { append ioctl lock open write };
-allow rustdesk_t krb5_keytab_t:file { ioctl lock open read };
-allow rustdesk_t ktalkd_exec_t:file ioctl;
-allow rustdesk_t ktalkd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t l2tpd_t:dbus send_msg;
-allow rustdesk_t lastlog_t:file { append ioctl lock open read setattr write };
-allow rustdesk_t lastlog_t:file { open read setattr write };
-allow rustdesk_t ld_so_cache_t:file { append write };
-allow rustdesk_t lldpad_t:dbus send_msg;
-allow rustdesk_t loadkeys_t:dbus send_msg;
-allow rustdesk_t locale_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t locale_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t locale_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t lockfile:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t lockfile:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t lockfile:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t login_userdomain:process2 nnp_transition;
-allow rustdesk_t login_userdomain:process transition;
-allow rustdesk_t lvm_control_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t lvm_etc_t:file map;
-allow rustdesk_t lvm_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t lvm_var_run_t:fifo_file { append ioctl lock read write };
-allow rustdesk_t machineid_t:file { append create link mounton rename setattr unlink watch_reads write };
-allow rustdesk_t mail_spool_t:lnk_file read;
-allow rustdesk_t mandb_t:dbus send_msg;
-allow rustdesk_t mdadm_t:unix_stream_socket connectto;
-allow rustdesk_t mdadm_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t memcached_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t memory_device_t:chr_file { ioctl lock map open read };
-allow rustdesk_t mnt_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t mnt_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t mnt_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t mnt_t:lnk_file read;
-allow rustdesk_t modemmanager_t:dbus send_msg;
-allow rustdesk_t modemmanager_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t modules_dep_t:file { ioctl lock map open read };
-allow rustdesk_t modules_object_t:dir mounton;
-allow rustdesk_t modules_object_t:file { ioctl lock map open read };
-allow rustdesk_t modules_object_t:lnk_file read;
-allow rustdesk_t mon_procd_t:dbus send_msg;
-allow rustdesk_t mountpoint:dir mounton;
-allow rustdesk_t mountpoint:file mounton;
-allow rustdesk_t mount_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t mount_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t mptcpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t munin_plugin_domain:dbus send_msg;
-allow rustdesk_t munin_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t mysqld_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t mythtv_script_t:dbus send_msg;
-allow rustdesk_t naemon_t:dbus send_msg;
-allow rustdesk_t nagios_plugin_domain:dbus send_msg;
-allow rustdesk_t nagios_system_plugin_t:dbus send_msg;
-allow rustdesk_t named_conf_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t named_conf_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t named_zone_t:dir setattr;
-allow rustdesk_t net_conf_t:dir { add_name remove_name write };
-allow rustdesk_t net_conf_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t netlabel_mgmt_t:dbus send_msg;
-allow rustdesk_t networkmanager_dispatcher_plugin:dbus send_msg;
-allow rustdesk_t NetworkManager_dispatcher_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t NetworkManager_priv_helper_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t NetworkManager_t:unix_stream_socket connectto;
-allow rustdesk_t nfsd_fs_t:file { ioctl lock open read };
-allow rustdesk_t nfsidmap_t:dbus send_msg;
-allow rustdesk_t ninfod_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t non_security_file_type:dir create;
-allow rustdesk_t non_security_file_type:dir { mounton setattr write };
-allow rustdesk_t non_security_file_type:dir setattr;
-allow rustdesk_t non_security_file_type:dir watch;
-allow rustdesk_t non_security_file_type:file mounton;
-allow rustdesk_t non_security_file_type:file watch;
-allow rustdesk_t non_security_file_type:lnk_file watch;
-allow rustdesk_t nrpe_exec_t:file ioctl;
-allow rustdesk_t nrpe_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t nsfs_t:file { getattr ioctl lock open read };
-allow rustdesk_t nsswitch_domain:dbus send_msg;
-allow rustdesk_t openshift_cgroup_read_t:dbus send_msg;
-allow rustdesk_t openshift_net_read_t:dbus send_msg;
-allow rustdesk_t oracleasm_t:dbus send_msg;
-allow rustdesk_t passwd_file_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t pcscd_t:unix_stream_socket connectto;
-allow rustdesk_t pdns_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t pegasus_openlmi_domain:dbus send_msg;
-allow rustdesk_t pidfile:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t pidfile:fifo_file { create open unlink };
-allow rustdesk_t pidfile:file { ioctl lock map open read unlink };
-allow rustdesk_t pidfile:lnk_file read;
-allow rustdesk_t pidfile:sock_file { append create open setattr unlink write };
-allow rustdesk_t pkcs_slotd_tmpfs_t:file unlink;
-allow rustdesk_t pkcs_slotd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t pkcs_slotd_t:shm destroy;
-allow rustdesk_t plymouthd_t:unix_stream_socket connectto;
-allow rustdesk_t plymouth_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t policykit_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t port_type:tcp_socket name_bind;
-allow rustdesk_t port_type:udp_socket name_bind;
-allow rustdesk_t postfix_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t print_spool_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t print_spool_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t print_spool_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t print_spool_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t proc_net_t:lnk_file { getattr read };
-allow rustdesk_t proc_security_t:file { append write };
-allow rustdesk_t proc_type:dir { getattr ioctl lock mounton open read search };
-allow rustdesk_t proc_type:file { getattr ioctl lock mounton open read };
-allow rustdesk_t ptchown_t:dbus send_msg;
-allow rustdesk_t ptynode:chr_file { append ioctl lock open read write };
-allow rustdesk_t qmail_tcp_env_exec_t:file { execute ioctl map open read };
-allow rustdesk_t qmail_tcp_env_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t qmail_tcp_env_t:process transition;
-allow rustdesk_t qmail_tcp_env_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t qpidd_t:dbus send_msg;
-allow rustdesk_t quota_exec_t:file { execute ioctl map open read };
-allow rustdesk_t quota_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t quota_t:process transition;
-allow rustdesk_t quota_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t radiusd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t random_device_t:chr_file { ioctl lock open read };
-allow rustdesk_t random_seed_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t rdisc_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t rhsmcertd_t:dbus send_msg;
-allow rustdesk_t rlogind_exec_t:file ioctl;
-allow rustdesk_t rlogind_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t root_t:dir write;
-allow rustdesk_t rpm_script_t:unix_stream_socket { append bind connect getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t rpm_var_cache_t:file { ioctl lock open read };
-allow rustdesk_t rpm_var_cache_t:lnk_file read;
-allow rustdesk_t rpm_var_lib_t:file { ioctl lock map open read };
-allow rustdesk_t rpm_var_lib_t:lnk_file read;
-allow rustdesk_t rshd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t rshd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t rshd_t:process transition;
-allow rustdesk_t rshd_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t rshd_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t rsync_exec_t:file ioctl;
-allow rustdesk_t rsync_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t rustdesk_exec_t:file { entrypoint execute ioctl lock map open read };
-allow rustdesk_t rustdesk_t:association sendto;
-allow rustdesk_t rustdesk_t:bpf { map_create map_read map_write prog_load prog_run };
-allow rustdesk_t rustdesk_t:capability2 { audit_read block_suspend bpf checkpoint_restore epolwakeup perfmon syslog wake_alarm };
-allow rustdesk_t rustdesk_t:capability { audit_write chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t rustdesk_t:capability sys_module;
-allow rustdesk_t rustdesk_t:cap_userns { audit_control audit_write chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_module sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t rustdesk_t:dbus send_msg;
-allow rustdesk_t rustdesk_t:dir watch;
-allow rustdesk_t rustdesk_t:fifo_file { create link rename setattr unlink };
-allow rustdesk_t rustdesk_t:fifo_file open;
-allow rustdesk_t rustdesk_t:file { append mounton write };
-allow rustdesk_t rustdesk_t:key { create read setattr view write };
-allow rustdesk_t rustdesk_t:lnk_file { ioctl lock };
-allow rustdesk_t rustdesk_t:lockdown { confidentiality integrity };
-allow rustdesk_t rustdesk_t:netlink_audit_socket { append bind connect create lock nlmsg_read nlmsg_relay nlmsg_tty_audit setattr shutdown };
-allow rustdesk_t rustdesk_t:netlink_kobject_uevent_socket { append bind connect create lock setattr shutdown };
-allow rustdesk_t rustdesk_t:netlink_route_socket { append bind connect create lock nlmsg_read nlmsg_write setattr shutdown };
-allow rustdesk_t rustdesk_t:netlink_selinux_socket { append bind connect create lock setattr shutdown };
-allow rustdesk_t rustdesk_t:packet_socket { append bind connect create lock setattr shutdown };
-allow rustdesk_t rustdesk_t:peer recv;
-allow rustdesk_t rustdesk_t:process { fork getcap getsched setcap setexec setfscreate setkeycreate setsockcreate };
-allow rustdesk_t rustdesk_t:sem { associate create destroy getattr read setattr unix_read unix_write write };
-allow rustdesk_t rustdesk_t:service { disable enable reload start status stop };
-allow rustdesk_t rustdesk_t:shm { associate create destroy getattr lock read setattr unix_read unix_write write };
-allow rustdesk_t rustdesk_t:system { disable enable halt ipc_info module_load module_request reboot reload start status stop syslog_console syslog_mod syslog_read undefined };
-allow rustdesk_t rustdesk_t:unix_stream_socket { connectto recvfrom };
-allow rustdesk_t rustdesk_t:user_namespace create;
-allow rustdesk_t sblim_domain:dbus send_msg;
-allow rustdesk_t security_t:file map;
-allow rustdesk_t security_t:security { check_context compute_av compute_create compute_relabel compute_user load_policy };
-allow rustdesk_t selinux_config_t:file { ioctl lock open read };
-allow rustdesk_t selinux_config_t:lnk_file read;
-allow rustdesk_t selinux_login_config_t:file { ioctl lock open read };
-allow rustdesk_t selinux_login_config_t:lnk_file read;
-allow rustdesk_t semanage_store_t:file { ioctl lock open read };
-allow rustdesk_t semanage_store_t:lnk_file read;
-allow rustdesk_t session_dbusd_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t shell_exec_t:file entrypoint;
-allow rustdesk_t smbcontrol_t:dbus send_msg;
-allow rustdesk_t smokeping_cgi_script_t:dbus send_msg;
-allow rustdesk_t spc_t:dbus send_msg;
-allow rustdesk_t speech_dispatcher_t:dbus send_msg;
-allow rustdesk_t spoolfile:sock_file { create open setattr unlink };
-allow rustdesk_t sshd_exec_t:file ioctl;
-allow rustdesk_t sshd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t ssh_keysign_t:dbus send_msg;
-allow rustdesk_t sslh_t:dbus send_msg;
-allow rustdesk_t sssd_var_lib_t:sock_file { create setattr unlink };
-allow rustdesk_t staff_t:fd use;
-allow rustdesk_t stratisd_data_t:lnk_file read;
-allow rustdesk_t stunnel_exec_t:file ioctl;
-allow rustdesk_t stunnel_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t sulogin_exec_t:file ioctl;
-allow rustdesk_t sulogin_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t svc_start_exec_t:file ioctl;
-allow rustdesk_t svc_start_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t svirt_file_type:chr_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t svirt_file_type:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t svirt_file_type:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t svirt_file_type:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t svirt_file_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t svirt_sandbox_domain:process transition;
-allow rustdesk_t svirt_sandbox_domain:unix_dgram_socket sendto;
-allow rustdesk_t svirt_tcg_t:dbus send_msg;
-allow rustdesk_t svirt_t:dbus send_msg;
-allow rustdesk_t swat_exec_t:file { execute ioctl map open read };
-allow rustdesk_t swat_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t swat_t:process transition;
-allow rustdesk_t swat_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t sysctl_kernel_t:file mounton;
-allow rustdesk_t sysctl_type:dir { getattr ioctl lock mounton open read search };
-allow rustdesk_t sysctl_type:file { append getattr ioctl lock open read setattr write };
-allow rustdesk_t sysfs_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t sysfs_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t sysfs_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t sysfs_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t syslogd_t:netlink_audit_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_write read setattr setopt shutdown write };
-allow rustdesk_t syslogd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_bootchart_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t system_dbusd_t:dbus acquire_svc;
-allow rustdesk_t system_dbusd_var_run_t:sock_file { read watch };
-allow rustdesk_t systemd_coredump_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_gpt_generator_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_home_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_home_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_home_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_hostnamed_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_hwdb_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_importd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_initctl_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_journal_upload_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_localed_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_logger_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_logger_t:unix_stream_socket connectto;
-allow rustdesk_t systemd_logind_inhibit_var_run_t:dir mounton;
-allow rustdesk_t systemd_logind_inhibit_var_run_t:fifo_file write;
-allow rustdesk_t systemd_logind_sessions_t:dir mounton;
-allow rustdesk_t systemd_logind_sessions_t:fifo_file write;
-allow rustdesk_t systemd_logind_t:fd use;
-allow rustdesk_t systemd_logind_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_logind_t:system status;
-allow rustdesk_t systemd_logind_var_run_t:dir mounton;
-allow rustdesk_t systemd_logind_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t systemd_machined_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_modules_load_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_mount_directory:dir { create mounton };
-allow rustdesk_t systemd_networkd_exec_t:file map;
-allow rustdesk_t systemd_networkd_t:netlink_route_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_write read setattr setopt shutdown write };
-allow rustdesk_t systemd_networkd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_network_generator_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_notify_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_passwd_agent_exec_t:file { execute ioctl lock map open read };
-allow rustdesk_t systemd_passwd_agent_exec_t:file { ioctl lock };
-allow rustdesk_t systemd_passwd_agent_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_passwd_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t systemd_passwd_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t systemd_passwd_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t systemd_private_tmp_type:dir { remove_name rmdir write };
-allow rustdesk_t systemd_private_tmp_type:fifo_file unlink;
-allow rustdesk_t systemd_private_tmp_type:file unlink;
-allow rustdesk_t systemd_private_tmp_type:lnk_file unlink;
-allow rustdesk_t systemd_private_tmp_type:sock_file unlink;
-allow rustdesk_t systemd_pstore_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_resolved_exec_t:file map;
-allow rustdesk_t systemd_resolved_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_rfkill_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_rfkill_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_sleep_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_socket_proxyd_t:unix_stream_socket connectto;
-allow rustdesk_t systemd_sysctl_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_systemctl_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t systemd_timedated_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_timedated_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_timedated_var_lib_t:lnk_file read;
-allow rustdesk_t systemd_tmpfiles_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_unit_file_type:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_unit_file_type:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_unit_file_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_unit_file_type:service { disable enable reload start status stop };
-allow rustdesk_t systemd_userdbd_runtime_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_userdbd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemprocess:process { dyntransition siginh };
-allow rustdesk_t systemprocess:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t systemprocess:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t tangd_db_t:file { ioctl lock open read };
-allow rustdesk_t tangd_t:dbus send_msg;
-allow rustdesk_t targetclid_t:dbus send_msg;
-allow rustdesk_t tcpd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t tcpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t tcpd_t:process transition;
-allow rustdesk_t tcpd_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t tcpd_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t telnetd_exec_t:file ioctl;
-allow rustdesk_t telnetd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t tftpd_exec_t:file ioctl;
-allow rustdesk_t tftpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t thin_domain:dbus send_msg;
-allow rustdesk_t thumb_t:dbus send_msg;
-allow rustdesk_t timedatex_t:dbus send_msg;
-allow rustdesk_t tlp_t:dbus send_msg;
-allow rustdesk_t tmpfs_t:chr_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t tmpfs_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t tmpfs_t:file { append create execute execute_no_trans ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t tmpfs_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t tmpfs_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t tmpreaper_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t tmp_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t tmp_t:fifo_file unlink;
-allow rustdesk_t tmp_t:sock_file unlink;
-allow rustdesk_t tpm_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t tty_device_t:chr_file { append ioctl lock open read watch watch_reads write };
-allow rustdesk_t ttynode:chr_file { append ioctl lock read write };
-allow rustdesk_t udev_rules_t:dir { add_name remove_name write };
-allow rustdesk_t udev_rules_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t udev_t:netlink_kobject_uevent_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:fifo_file { append getattr ioctl lock open write };
-allow rustdesk_t unconfined_service_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t unconfined_service_t:process { siginh transition };
-allow rustdesk_t unconfined_service_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t unlabeled_t:file { ioctl lock open read };
-allow rustdesk_t unlabeled_t:lnk_file read;
-allow rustdesk_t updpwd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t updpwd_t:process transition;
-allow rustdesk_t urandom_device_t:chr_file { append write };
-allow rustdesk_t usbtty_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t user_devpts_t:chr_file { watch watch_reads };
-allow rustdesk_t userdomain:fifo_file { append getattr ioctl lock read write };
-allow rustdesk_t userdomain:unix_stream_socket { append bind connect connectto getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t userdomain:unix_stream_socket connectto;
-allow rustdesk_t user_home_dir_t:lnk_file read;
-allow rustdesk_t user_home_t:file unlink;
-allow rustdesk_t user_t:fd use;
-allow rustdesk_t user_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t user_tmp_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t user_tmp_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t user_tty_device_t:chr_file { open watch watch_reads };
-allow rustdesk_t usr_t:dir { add_name remove_name write };
-allow rustdesk_t uucpd_exec_t:file ioctl;
-allow rustdesk_t uucpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t uuidd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t uuidd_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t uuidd_var_run_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t uuidd_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t var_lib_nfs_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_lib_t:dir { add_name create remove_name setattr write };
-allow rustdesk_t var_lib_t:dir { create setattr };
-allow rustdesk_t var_lib_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_lib_t:lnk_file { create read write };
-allow rustdesk_t var_log_t:dir { add_name create remove_name setattr write };
-allow rustdesk_t var_log_t:dir { create setattr };
-allow rustdesk_t var_log_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_log_t:file { create link map open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_log_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t var_run_t:file { append execute execute_no_trans write };
-allow rustdesk_t var_run_t:lnk_file unlink;
-allow rustdesk_t var_spool_t:dir { add_name remove_name write };
-allow rustdesk_t var_t:dir { add_name create remove_name setattr write };
-allow rustdesk_t var_t:dir { create setattr };
-allow rustdesk_t var_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t virsh_t:dbus send_msg;
-allow rustdesk_t virtd_t:unix_stream_socket connectto;
-allow rustdesk_t virt_etc_rw_t:file { ioctl lock open read };
-allow rustdesk_t virt_etc_rw_t:lnk_file read;
-allow rustdesk_t virtio_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t vnstatd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t watchdog_device_t:chr_file { append ioctl lock open write };
-allow rustdesk_t watchdog_t:dbus send_msg;
-allow rustdesk_t wireguard_t:dbus send_msg;
-allow rustdesk_t wireless_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t wtmp_t:file { append ioctl lock open read write };
-allow rustdesk_t wtmp_t:file { open read write };
-allow rustdesk_t xdm_exec_t:file ioctl;
-allow rustdesk_t xdm_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t xdm_var_lib_t:file { ioctl lock open read };
-allow rustdesk_t xdm_var_lib_t:lnk_file read;
-allow rustdesk_t xenconsoled_t:dbus send_msg;
-allow rustdesk_t xend_t:dbus send_msg;
-allow rustdesk_t xguest_t:dbus send_msg;
-allow rustdesk_t xserver_port_t:tcp_socket name_connect;
-allow rustdesk_t xserver_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t xserver_t:unix_stream_socket connectto;
-
-
-```
-
-`rustdesk.fc`:
-
-```text
-
-/usr/bin/rustdesk -- gen_context(system_u:object_r:rustdesk_exec_t,s0)
-```
-
-`rustdesk.if`:
-
-```text
-
-# RustDesk
-```
-
-`Makefile`:
-
-```makefile
-
-TARGET?=rustdesk
-MODULES?=${TARGET:=.pp.bz2}
-SHAREDIR?=/usr/share
-SELINUXTYPE?=targeted
-
-all: ${TARGET:=.pp.bz2}
-
-%.pp.bz2: %.pp
- @echo Compressing $^ -\> $@
- bzip2 -9 $^
-
-%.pp: %.te
- make -f ${SHAREDIR}/selinux/devel/Makefile $@
-
-clean:
- rm -f *~ *.tc *.pp *.pp.bz2
- rm -rf tmp *.tar.gz
-
-man: install-policy
- sepolicy manpage --path . --domain ${TARGET}_t
-
-install-policy: all
- semodule -i ${TARGET}.pp.bz2
-
-install: man
- install -D -m 644 ${TARGET}.pp.bz2 ${DESTDIR}${SHAREDIR}/selinux/packages/${SELINUXTYPE}/${TARGET}.pp.bz2
- install -D -m 644 ${TARGET}_selinux.8 ${DESTDIR}${SHAREDIR}/man/man8/
-
-```
-
-#### Direkt aktivieren
-
-Zeigen Sie den Sicherheitskontext von RustDesk vor der Änderung an:
-
-```sh
-$ ls -lZ /usr/lib/rustdesk/rustdesk
--rwxr-xr-x. 1 root root system_u:object_r:lib_t:s0 25456 Oct 8 19:58 /usr/lib/rustdesk/rustdesk
-$ ps -eZ | grep rustdesk
-system_u:system_r:init_t:s0 80439 ? 00:00:02 rustdesk
-```
-
-Führen Sie aus:
-
-```sh
-
-$ cd rustdesk-selinux-1.0
-$ make
-$ sudo make install-policy
-$ semodule -l | grep rustdesk
-rustdesk
-$ sudo chcon -t rustdesk_exec_t /usr/bin/rustdesk
-$ sudo systemctl restart rustdesk
-
-```
-
-Zeigen Sie den Sicherheitskontext erneut an:
-
-```sh
-$ ls -lZ /usr/lib/rustdesk/rustdesk
--rwxr-xr-x. 1 root root system_u:object_r:rustdesk_exec_t:s0 25456 Oct 8 19:58 /usr/lib/rustdesk/rustdesk
-$ ps -eZ | grep rustdesk
-system_u:system_r:rustdesk_t:s0 110565 ? 00:00:00 rustdesk
-```
-
-#### Durch RPM-Installation aktivieren
-
-Sie können den Befehl `sepolicy generate` verwenden:
-
-```sh
-$ # Abhängigkeiten installieren
-$ sudo dnf install -y rpm rpm-build binutils
-$ # Richtlinie erzeugen
-$ sepolicy generate --init /usr/lib/rustdesk/rustdesk
-$ tree
-.
-├── rustdesk.fc
-├── rustdesk.if
-├── rustdesk_selinux.spec
-├── rustdesk.sh
-└── rustdesk.te
-$ # rustdesk.te bearbeiten
-$
-$
-$ # RPM-Paket rustdesk_selinux-1.0-1.fc38.src.rpm erzeugen
-$ sudo ./rustdesk.sh
-$ # Paket installieren
-$ sudo dnf install -y rustdesk_selinux-1.0-1.fc38.src.rpm
-$ # Dienst neu starten
-$ sudo systemctl restart rustdesk
-```
-
-### Richtlinien iterativ hinzufügen
-
-```sh
-$ cd /tmp
-$ grep rustdesk_t /var/log/audit/audit.log | audit2allow -a -M rustdesk_tmp
-$ cd
-$ # rustdesk_tmp.te zu rustdesk.te zusammenführen
-$ make clean && make && sudo make install-policy
-```
-
-## Referenzen
-
-- [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials)
-- [SELinux Policy module installation](https://fedoraproject.org/wiki/SELinux/IndependentPolicy#SELinux_Policy_module_installation)
-- [How to create SELinux custom policy rpm package](https://lukas-vrabec.com/index.php/2015/07/07/how-to-create-selinux-custom-policy-rpm-package/)
-
diff --git a/content/client/linux/SELinux/_index.en.md b/content/client/linux/SELinux/_index.en.md
deleted file mode 100644
index c247124..0000000
--- a/content/client/linux/SELinux/_index.en.md
+++ /dev/null
@@ -1,1837 +0,0 @@
----
-title: SELinux
-weight: 100
----
-
-Some distros (such as Fedora) enable SELinux by default, which will cause the RustDesk service to fail to start and run normally.
-
-You can run `sestatus` in the terminal to check whether SELinux is enabled.
-
-Depending on whether it is enabled or not, you can see two different outputs as follows:
-
-```sh
-# Enabled
-SELinux status: enabled
-...
-
-# Disabled
-SELinux status: disabled
-...
-```
-
-## Add SELinux Policies
-
-For an introduction to SELinux, please refer to [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials).
-
-Here we take Fedora 38 as an example to introduce how to add SELinux policies.
-
-```sh
-sudo dnf install selinux-policy-devel make
-```
-
-Adding SELinux policies requires determining the type of service, which is in the security context of the process.
-
-```sh
-$ ps -eZ | grep rustdesk
-system_u:system_r:init_t:s0 80439 ? 00:00:02 rustdesk
-```
-
-`system_u:system_r:init_t:s0` is the security context of the RustDesk process, where the third field `init_t` is the type of the process.
-
-There are two ways to write SELinux type rules:
-
-1. Add rules to the default `init_t`.
-2. Add a new type `rustdesk_t` and add rules.
-
-The first method has relatively minor modifications, but because the default `init_t` is changed, it is equivalent to adding authorization to other services using the `init_t` type. **Not recommended for use.**
-
-The second method is to add rules from scratch. There will be many rules that need to be added, and different systems may have differences. It may be necessary to make some adjustments during actual use.
-
-### Use The Default Type
-
-The default type of the RustDesk service is `init_t`, which is determined by [the context inheritance rules of SELinux](https://wiki.gentoo.org/wiki/SELinux/Tutorials/How_does_a_process_get_into_a_certain_context).
-
-**Caution**: Modifying the default type means that the policies of other services may also change. Please use this method with caution!
-
-Edit the rule file `rustdesk.te`:
-
-```text
-module rustdesk 1.0;
-
-require {
- type event_device_t;
- type xserver_t;
- type xserver_port_t;
- type sudo_exec_t;
- type init_t;
- type ephemeral_port_t;
- type user_tmp_t;
- type user_fonts_cache_t;
- type pulseaudio_home_t;
- type session_dbusd_tmp_t;
- type unconfined_dbusd_t;
- class process execmem;
- class file { open read create write execute execute_no_trans map setattr lock link unlink };
- class unix_stream_socket connectto;
- class tcp_socket name_connect;
- class dir { add_name remove_name };
- class sock_file write;
- class chr_file { open read write } ;
-}
-
-#============= init_t ==============
-allow init_t xserver_t:unix_stream_socket connectto;
-allow init_t sudo_exec_t:file { open read execute execute_no_trans };
-allow init_t user_tmp_t:file { open write setattr };
-allow init_t self:process execmem;
-allow init_t user_fonts_cache_t:dir { add_name remove_name };
-allow init_t user_fonts_cache_t:file { read write create open link lock unlink };
-allow init_t xserver_port_t:tcp_socket name_connect;
-allow init_t pulseaudio_home_t:file { read write open lock };
-allow init_t session_dbusd_tmp_t:sock_file write;
-allow init_t unconfined_dbusd_t:unix_stream_socket connectto;
-
-#!!!! This AVC can be allowed using the boolean 'nis_enabled'
-allow init_t ephemeral_port_t:tcp_socket name_connect;
-
-#!!!! This AVC can be allowed using the boolean 'domain_can_mmap_files'
-allow init_t sudo_exec_t:file map;
-
-
-#============= init_t Wayland ==============
-allow init_t event_device_t:chr_file { open read write };
-
-#!!!! This AVC can be allowed using the boolean 'domain_can_mmap_files'
-allow init_t user_tmp_t:file map;
-
-```
-
-Run:
-
-```sh
-$ checkmodule -M -m -o rustdesk.mod rustdesk.te && semodule_package -o rustdesk.pp -m rustdesk.mod && sudo semodule -i rustdesk.pp
-$ sudo semodule -l | grep rustdesk
-```
-
-### Create a type `rustdesk_t`
-
-1. Create a new directory: `mkdir rustdesk-selinux-1.0`.
-2. Create SELinux policy files: `touch Makefile rustdesk.te rustdesk.fc rustdesk.if`.
-
-```text
-.
-├── Makefile
-├── rustdesk.fc
-├── rustdesk.if
-└── rustdesk.te
-```
-
-`rustdesk.te` is the main policy file.
-In this example, this file mainly comes from 3 parts:
-
-1. [`init.te`](https://github.com/fedora-selinux/selinux-policy/blob/rawhide/policy/modules/system/init.te) in GitHub’s selinux-policy repository.
-2. Audit log, `grep rustdesk /var/log/audit/audit.log | audit2allow -a -M test`.
-3. The test system's `init_t` policy, `sesearch -A | grep 'allow init_t ' | sed 's/allow init_t /allow rustdesk_t /g'`.
-
-Some policies are duplicates and some are redundant, but this is ok since it works on `rustdesk_t`.
-
-The contents of each file are as follows.
-
-`rustdesk.te`:
-
-```text
-
-policy_module(rustdesk, 1.0)
-
-type rustdesk_t;
-type rustdesk_exec_t;
-
-gen_require(`
- # used for direct running of init scripts
- # by admin domains
- attribute direct_run_init;
- attribute direct_init;
- attribute direct_init_entry;
-
- attribute init_script_domain_type;
- attribute initrc_transition_domain;
- # Attribute used for systemd so domains can allow systemd to create sock_files
- attribute init_sock_file_type;
- # Attribute for directories that systemd will watch based on path units
- # (see systemd.path(5) for more info) (Deprecated)
- attribute init_watch_path_type;
-
- # Mark process types as daemons
- attribute daemon;
- attribute systemprocess;
- attribute systemprocess_entry;
-
- # Mark file type as a daemon run directory
- attribute daemonrundir;
-
- class passwd rootok;
- class dbus { acquire_svc send_msg };
- class process execmem;
-
- type abrt_dump_oops_t;
- type abrt_upload_watch_t;
- type adjtime_t;
- type aiccu_t;
- type amanda_inetd_exec_t;
- type amanda_t;
- type antivirus_t;
- type apcupsd_power_t;
- type auditd_etc_t;
- type autofs_device_t;
- type binfmt_misc_fs_t;
- type bitlbee_exec_t;
- type bitlbee_t;
- type boltd_var_lib_t;
- type boltd_var_run_t;
- type boothd_t;
- type bootloader_exec_t;
- type bootloader_t;
- type bpf_t;
- type bugzilla_script_t;
- type certwatch_t;
- type cgroup_t;
- type chkpwd_exec_t;
- type chkpwd_t;
- type chronyc_t;
- type chronyd_exec_t;
- type chronyd_keys_t;
- type chronyd_restricted_t;
- type chroot_exec_t;
- type cifs_helper_t;
- type cinder_domain;
- type cloudform_domain;
- type collectd_script_t;
- type comsat_exec_t;
- type comsat_t;
- type config_home_t;
- type console_device_t;
- type consolekit_log_t;
- type container_kvm_t;
- type container_runtime_domain;
- type container_runtime_tmpfs_t;
- type container_var_lib_t;
- type crack_t;
- type cups_brf_t;
- type cupsd_exec_t;
- type cupsd_lpd_exec_t;
- type cupsd_lpd_t;
- type cupsd_t;
- type cvs_exec_t;
- type cvs_t;
- type data_home_t;
- type dbskkd_exec_t;
- type dbskkd_t;
- type default_context_t;
- type default_t;
- type devicekit_disk_t;
- type devicekit_power_t;
- type devicekit_t;
- type device_t;
- type devlog_t;
- type devpts_t;
- type dhcpc_state_t;
- type dhcp_state_t;
- type dirsrvadmin_script_t;
- type dri_device_t;
- type dspam_script_t;
- type efivarfs_t;
- type ephemeral_port_t;
- type etc_aliases_t;
- type etc_runtime_t;
- type etc_t;
- type event_device_t;
- type faillog_t;
- type fetchmail_t;
- type fingerd_exec_t;
- type fingerd_t;
- type fixed_disk_device_t;
- type flatpak_helper_t;
- type fprintd_exec_t;
- type fprintd_t;
- type fprintd_var_lib_t;
- type fsadm_t;
- type ftpd_exec_t;
- type ftpd_t;
- type fwupd_cache_t;
- type fwupd_t;
- type gconfdefaultsm_t;
- type geoclue_t;
- type getty_exec_t;
- type getty_t;
- type gitd_exec_t;
- type git_system_t;
- type gnome_home_type;
- type gnomesystemmm_t;
- type guest_t;
- type home_bin_t;
- type home_root_t;
- type hostname_etc_t;
- type httpd_log_t;
- type httpd_t;
- type httpd_tmp_t;
- type hugetlbfs_t;
- type ibacm_t;
- type ibacm_var_run_t;
- type inetd_child_exec_t;
- type inetd_child_t;
- type initctl_t;
- type init_exec_t;
- type initrc_state_t;
- type initrc_t;
- type initrc_var_run_t;
- type init_t;
- type init_tmp_t;
- type init_var_lib_t;
- type init_var_run_t;
- type insights_client_t;
- type install_exec_t;
- type install_t;
- type ipsec_conf_file_t;
- type ipsec_t;
- type ipsec_var_run_t;
- type irqbalance_t;
- type iscsi_var_lib_t;
- type jockey_t;
- type journalctl_exec_t;
- type kadmind_t;
- type kdump_crash_t;
- type kdumpctl_t;
- type kdump_t;
- type keepalived_unconfined_script_t;
- type kernel_t;
- type kmod_exec_t;
- type kmod_t;
- type kmscon_t;
- type kmsg_device_t;
- type krb5_keytab_t;
- type ktalkd_exec_t;
- type ktalkd_t;
- type l2tpd_t;
- type lastlog_t;
- type ld_so_cache_t;
- type lldpad_t;
- type loadkeys_t;
- type locale_t;
- type lvm_control_t;
- type lvm_etc_t;
- type lvm_t;
- type lvm_var_run_t;
- type machineid_t;
- type mail_spool_t;
- type mandb_t;
- type mdadm_t;
- type mdadm_var_run_t;
- type memcached_t;
- type memory_device_t;
- type mnt_t;
- type modemmanager_t;
- type modules_dep_t;
- type modules_object_t;
- type mon_procd_t;
- type mount_t;
- type mount_var_run_t;
- type mptcpd_t;
- type munin_plugin_domain;
- type munin_t;
- type mysqld_t;
- type mythtv_script_t;
- type naemon_t;
- type nagios_plugin_domain;
- type nagios_system_plugin_t;
- type named_conf_t;
- type named_zone_t;
- type net_conf_t;
- type netlabel_mgmt_t;
- type networkmanager_dispatcher_plugin;
- type NetworkManager_dispatcher_t;
- type NetworkManager_priv_helper_t;
- type NetworkManager_t;
- type nfsd_fs_t;
- type nfsidmap_t;
- type ninfod_t;
- type nrpe_exec_t;
- type nrpe_t;
- type nsfs_t;
- type openshift_cgroup_read_t;
- type openshift_net_read_t;
- type oracleasm_t;
- type passwd_file_t;
- type pcscd_t;
- type pdns_t;
- type pegasus_openlmi_domain;
- type pkcs_slotd_t;
- type pkcs_slotd_tmpfs_t;
- type plymouthd_t;
- type plymouth_exec_t;
- type policykit_t;
- type postfix_exec_t;
- type print_spool_t;
- type proc_net_t;
- type proc_security_t;
- type ptchown_t;
- type pulseaudio_home_t;
- type qmail_tcp_env_exec_t;
- type qmail_tcp_env_t;
- type qpidd_t;
- type quota_exec_t;
- type quota_t;
- type radiusd_t;
- type random_device_t;
- type random_seed_t;
- type rdisc_t;
- type rhsmcertd_t;
- type rlogind_exec_t;
- type rlogind_t;
- type root_t;
- type rpm_script_t;
- type rpm_var_cache_t;
- type rpm_var_lib_t;
- type rshd_exec_t;
- type rshd_t;
- type rsync_exec_t;
- type rsync_t;
- type rustdesk_exec_t;
- type rustdesk_t;
- type sblim_domain;
- type security_t;
- type selinux_config_t;
- type selinux_login_config_t;
- type semanage_store_t;
- type session_dbusd_tmp_t;
- type shell_exec_t;
- type smbcontrol_t;
- type smokeping_cgi_script_t;
- type spc_t;
- type speech_dispatcher_t;
- type sshd_exec_t;
- type sshd_t;
- type ssh_keysign_t;
- type sslh_t;
- type sssd_var_lib_t;
- type staff_t;
- type stratisd_data_t;
- type stunnel_exec_t;
- type stunnel_t;
- type sudo_exec_t;
- type sulogin_exec_t;
- type sulogin_t;
- type svc_start_exec_t;
- type svc_start_t;
- type svirt_file_type;
- type svirt_sandbox_domain;
- type svirt_t;
- type svirt_tcg_t;
- type swat_exec_t;
- type swat_t;
- type sysctl_kernel_t;
- type sysfs_t;
- type syslogd_t;
- type systemd_bootchart_t;
- type system_dbusd_t;
- type system_dbusd_var_run_t;
- type systemd_coredump_t;
- type systemd_gpt_generator_t;
- type systemd_home_t;
- type systemd_hostnamed_t;
- type systemd_hwdb_t;
- type systemd_importd_t;
- type systemd_initctl_t;
- type systemd_journal_upload_t;
- type systemd_localed_t;
- type systemd_logger_t;
- type systemd_logind_inhibit_var_run_t;
- type systemd_logind_sessions_t;
- type systemd_logind_t;
- type systemd_logind_var_run_t;
- type systemd_machined_t;
- type systemd_modules_load_t;
- type systemd_mount_directory;
- type systemd_networkd_exec_t;
- type systemd_networkd_t;
- type systemd_network_generator_t;
- type systemd_notify_t;
- type systemd_passwd_agent_exec_t;
- type systemd_passwd_agent_t;
- type systemd_passwd_var_run_t;
- type systemd_pstore_t;
- type systemd_resolved_exec_t;
- type systemd_resolved_t;
- type systemd_rfkill_t;
- type systemd_rfkill_var_lib_t;
- type systemd_sleep_t;
- type systemd_socket_proxyd_t;
- type systemd_sysctl_t;
- type systemd_systemctl_exec_t;
- type systemd_timedated_t;
- type systemd_timedated_var_lib_t;
- type systemd_tmpfiles_t;
- type systemd_userdbd_runtime_t;
- type systemd_userdbd_t;
- type tangd_db_t;
- type tangd_t;
- type targetclid_t;
- type tcpd_exec_t;
- type tcpd_t;
- type telnetd_exec_t;
- type telnetd_t;
- type tftpd_exec_t;
- type tftpd_t;
- type thin_domain;
- type thumb_t;
- type timedatex_t;
- type tlp_t;
- type tmpfs_t;
- type tmpreaper_t;
- type tmp_t;
- type tpm_device_t;
- type tty_device_t;
- type udev_rules_t;
- type udev_t;
- type unconfined_dbusd_t;
- type unconfined_service_t;
- type unconfined_t;
- type unlabeled_t;
- type unreserved_port_t;
- type updpwd_exec_t;
- type updpwd_t;
- type urandom_device_t;
- type usbtty_device_t;
- type user_devpts_t;
- type user_fonts_cache_t;
- type user_home_dir_t;
- type user_home_t;
- type user_t;
- type user_tmp_t;
- type user_tty_device_t;
- type usr_t;
- type uucpd_exec_t;
- type uucpd_t;
- type uuidd_t;
- type uuidd_var_run_t;
- type var_lib_nfs_t;
- type var_lib_t;
- type var_log_t;
- type var_run_t;
- type var_spool_t;
- type var_t;
- type virsh_t;
- type virtd_t;
- type virt_etc_rw_t;
- type virtio_device_t;
- type vnstatd_t;
- type watchdog_device_t;
- type watchdog_t;
- type wireguard_t;
- type wireless_device_t;
- type wtmp_t;
- type xdm_exec_t;
- type xdm_t;
- type xdm_var_lib_t;
- type xenconsoled_t;
- type xend_t;
- type xguest_t;
- type xserver_port_t;
- type xserver_t;
-')
-
-##############################################################################
-#
-# Part 1. The following rules are mainly from the open source `init.te`.
-# https://github.com/fedora-selinux/selinux-policy/blob/rawhide/policy/modules/system/init.te
-#
-# Note: Part 1 will probably be mostly the same as Part 3. But it's acceptable for now.
-#
-
-init_daemon_domain(rustdesk_t, rustdesk_exec_t)
-
-domain_role_change_exemption(rustdesk_t)
-domain_subj_id_change_exemption(rustdesk_t)
-domain_obj_id_change_exemption(rustdesk_t)
-role system_r types rustdesk_t;
-corecmd_shell_entry_type(rustdesk_t)
-typeattribute rustdesk_t init_script_domain_type;
-
-
-#######################################
-
-# Use capabilities, old rule:
-allow rustdesk_t self:capability ~{ audit_control audit_write sys_module };
-allow rustdesk_t self:capability2 ~{ mac_admin mac_override };
-allow rustdesk_t self:cap_userns all_cap_userns_perms;
-allow rustdesk_t self:tcp_socket { listen accept };
-allow rustdesk_t self:packet_socket create_socket_perms;
-allow rustdesk_t self:key manage_key_perms;
-allow rustdesk_t self:bpf { map_create map_read map_write prog_load prog_run };
-
-allow rustdesk_t self:file mounton;
-allow rustdesk_t self:fifo_file rw_fifo_file_perms;
-
-allow rustdesk_t self:service manage_service_perms;
-allow rustdesk_t self:user_namespace create;
-
-# Re-exec itself
-can_exec(rustdesk_t, rustdesk_exec_t)
-# executing content in /run/initramfs
-manage_files_pattern(rustdesk_t, initrc_state_t, initrc_state_t)
-can_exec(rustdesk_t, initrc_state_t)
-
-allow rustdesk_t initrc_t:unix_stream_socket { connectto create_stream_socket_perms };
-allow rustdesk_t initrc_t:tcp_socket create_stream_socket_perms;
-allow initrc_t rustdesk_t:unix_stream_socket { connectto rw_stream_socket_perms sendto };
-allow initrc_t rustdesk_t:fifo_file rw_fifo_file_perms;
-
-manage_files_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-manage_dirs_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-manage_lnk_files_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-manage_sock_files_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-files_tmp_filetrans(rustdesk_t, init_tmp_t, { file sock_file })
-allow rustdesk_t init_tmp_t:file map;
-
-manage_dirs_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-manage_files_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-manage_lnk_files_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-manage_sock_files_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-files_var_lib_filetrans(rustdesk_t, init_var_lib_t, { dir file })
-allow rustdesk_t init_var_lib_t:dir mounton;
-allow rustdesk_t init_var_lib_t:file map;
-
-manage_dirs_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_lnk_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_sock_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_fifo_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_blk_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_chr_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-files_pid_filetrans(rustdesk_t, init_var_run_t, { dir file blk_file chr_file fifo_file})
-allow rustdesk_t init_var_run_t:dir mounton;
-allow rustdesk_t init_var_run_t:file mounton;
-allow rustdesk_t init_var_run_t:sock_file relabelto;
-allow rustdesk_t init_var_run_t:blk_file { getattr relabelto };
-allow rustdesk_t init_var_run_t:chr_file { getattr relabelto };
-allow rustdesk_t init_var_run_t:fifo_file { getattr relabelto };
-
-allow rustdesk_t machineid_t:file manage_file_perms;
-files_pid_filetrans(rustdesk_t, machineid_t, file, "machine-id")
-files_etc_filetrans(rustdesk_t, machineid_t, file, "machine-id")
-allow rustdesk_t machineid_t:file mounton;
-
-allow rustdesk_t initctl_t:fifo_file manage_fifo_file_perms;
-dev_filetrans(rustdesk_t, initctl_t, fifo_file)
-
-# Modify utmp
-allow rustdesk_t initrc_var_run_t:file { rw_file_perms setattr };
-
-kernel_read_system_state(rustdesk_t)
-kernel_share_state(rustdesk_t)
-kernel_stream_connect(rustdesk_t)
-kernel_rw_stream_socket_perms(rustdesk_t)
-kernel_rw_unix_dgram_sockets(rustdesk_t)
-kernel_mounton_systemd_ProtectKernelTunables(rustdesk_t)
-kernel_read_core_if(rustdesk_t)
-kernel_mounton_core_if(rustdesk_t)
-kernel_mounton_all_sysctls(rustdesk_t)
-kernel_get_sysvipc_info(rustdesk_t)
-kernel_load_module(rustdesk_t)
-kernel_read_all_proc(rustdesk_t)
-kernel_list_all_proc(rustdesk_t)
-kernel_mounton_all_proc(rustdesk_t)
-
-# There is bug in kernel 4.16 where lot of domains requesting module_request, for now dontauditing
-kernel_dontaudit_request_load_module(rustdesk_t)
-
-corecmd_exec_chroot(rustdesk_t)
-corecmd_exec_bin(rustdesk_t)
-
-corenet_all_recvfrom_netlabel(rustdesk_t)
-corenet_tcp_bind_all_ports(rustdesk_t)
-corenet_udp_bind_all_ports(rustdesk_t)
-
-dev_create_all_files(rustdesk_t)
-dev_create_all_chr_files(rustdesk_t)
-dev_list_sysfs(rustdesk_t)
-dev_manage_sysfs(rustdesk_t)
-dev_mounton_all_device_nodes(rustdesk_t)
-dev_setattr_all_blk_files(rustdesk_t)
-dev_setattr_all_chr_files(rustdesk_t)
-dev_read_urand(rustdesk_t)
-dev_read_raw_memory(rustdesk_t)
-# Early devtmpfs
-dev_rw_generic_chr_files(rustdesk_t)
-dev_filetrans_all_named_dev(rustdesk_t)
-dev_write_watchdog(rustdesk_t)
-dev_rw_inherited_input_dev(rustdesk_t)
-dev_rw_dri(rustdesk_t)
-dev_rw_tpm(rustdesk_t)
-
-domain_getpgid_all_domains(rustdesk_t)
-domain_kill_all_domains(rustdesk_t)
-domain_signal_all_domains(rustdesk_t)
-domain_signull_all_domains(rustdesk_t)
-domain_sigstop_all_domains(rustdesk_t)
-domain_sigchld_all_domains(rustdesk_t)
-domain_read_all_domains_state(rustdesk_t)
-domain_getattr_all_domains(rustdesk_t)
-domain_setrlimit_all_domains(rustdesk_t)
-domain_rlimitinh_all_domains(rustdesk_t)
-domain_noatsecure_all_domains(rustdesk_t)
-domain_setpriority_all_domains(rustdesk_t)
-
-files_read_config_files(rustdesk_t)
-files_read_all_pids(rustdesk_t)
-files_map_all_pids(rustdesk_t)
-files_read_system_conf_files(rustdesk_t)
-files_rw_generic_pids(rustdesk_t)
-files_dontaudit_search_isid_type_dirs(rustdesk_t)
-files_read_isid_type_files(rustdesk_t)
-files_read_etc_runtime_files(rustdesk_t)
-files_manage_all_locks(rustdesk_t)
-files_manage_etc_runtime_files(rustdesk_t)
-files_manage_etc_symlinks(rustdesk_t)
-files_etc_filetrans_etc_runtime(rustdesk_t, file)
-# Run /etc/X11/prefdm
-files_exec_etc_files(rustdesk_t)
-files_read_usr_files(rustdesk_t)
-files_write_root_dirs(rustdesk_t)
-# file descriptors inherited from the rootfs
-files_dontaudit_rw_root_files(rustdesk_t)
-files_dontaudit_rw_root_chr_files(rustdesk_t)
-files_dontaudit_mounton_modules_object(rustdesk_t)
-files_manage_mnt_dirs(rustdesk_t)
-files_manage_mnt_files(rustdesk_t)
-files_read_mnt_symlinks(rustdesk_t)
-files_mounton_etc(rustdesk_t)
-files_create_default_dir(rustdesk_t)
-files_remount_rootfs(rustdesk_t)
-files_create_var_dirs(rustdesk_t)
-files_watch_non_security_dirs(rustdesk_t)
-files_watch_non_security_files(rustdesk_t)
-files_watch_non_security_lnk_files(rustdesk_t)
-
-fs_read_efivarfs_files(rustdesk_t)
-fs_setattr_efivarfs_files(rustdesk_t)
-fs_read_nfsd_files(rustdesk_t)
-
-fstools_getattr_swap_files(rustdesk_t)
-
-mcs_process_set_categories(rustdesk_t)
-
-mls_file_read_all_levels(rustdesk_t)
-mls_file_write_all_levels(rustdesk_t)
-mls_file_downgrade(rustdesk_t)
-mls_file_upgrade(rustdesk_t)
-mls_fd_use_all_levels(rustdesk_t)
-mls_fd_share_all_levels(rustdesk_t)
-mls_process_set_level(rustdesk_t)
-mls_process_write_down(rustdesk_t)
-mls_socket_read_all_levels(rustdesk_t)
-mls_socket_write_all_levels(rustdesk_t)
-mls_rangetrans_source(rustdesk_t)
-
-selinux_set_all_booleans(rustdesk_t)
-selinux_load_policy(rustdesk_t)
-selinux_mounton_fs(rustdesk_t)
-allow rustdesk_t security_t:security load_policy;
-
-selinux_compute_access_vector(rustdesk_t)
-selinux_compute_create_context(rustdesk_t)
-selinux_compute_user_contexts(rustdesk_t)
-selinux_validate_context(rustdesk_t)
-selinux_compute_relabel_context(rustdesk_t)
-selinux_unmount_fs(rustdesk_t)
-
-term_create_pty_dir(rustdesk_t)
-term_use_unallocated_ttys(rustdesk_t)
-term_setattr_unallocated_ttys(rustdesk_t)
-term_use_console(rustdesk_t)
-term_use_all_inherited_terms(rustdesk_t)
-term_use_usb_ttys(rustdesk_t)
-term_use_all_ptys(rustdesk_t)
-term_setattr_all_ptys(rustdesk_t)
-term_use_virtio_console(rustdesk_t)
-term_watch_console_dev(rustdesk_t)
-term_watch_reads_console_dev(rustdesk_t)
-term_watch_unallocated_ttys(rustdesk_t)
-term_watch_reads_unallocated_ttys(rustdesk_t)
-term_watch_user_ttys(rustdesk_t)
-term_watch_reads_user_ttys(rustdesk_t)
-
-# Run init scripts
-init_domtrans_script(rustdesk_t)
-init_exec_notrans_direct_init_entry(rustdesk_t)
-
-libs_rw_ld_so_cache(rustdesk_t)
-
-logging_create_devlog_dev(rustdesk_t)
-logging_send_syslog_msg(rustdesk_t)
-logging_send_audit_msgs(rustdesk_t)
-logging_manage_generic_logs(rustdesk_t)
-logging_mmap_generic_logs(rustdesk_t)
-logging_relabel_devlog_dev(rustdesk_t)
-logging_manage_audit_config(rustdesk_t)
-logging_create_syslog_netlink_audit_socket(rustdesk_t)
-logging_write_var_log_dirs(rustdesk_t)
-logging_manage_var_log_symlinks(rustdesk_t)
-
-seutil_read_config(rustdesk_t)
-seutil_read_login_config(rustdesk_t)
-seutil_read_default_contexts(rustdesk_t)
-seutil_read_module_store(rustdesk_t)
-
-miscfiles_manage_localization(rustdesk_t)
-miscfiles_filetrans_named_content(rustdesk_t)
-
-udev_manage_rules_files(rustdesk_t)
-
-userdom_use_user_ttys(rustdesk_t)
-userdom_manage_tmp_dirs(rustdesk_t)
-userdom_manage_tmp_sockets(rustdesk_t)
-userdom_delete_user_tmp_files(rustdesk_t)
-userdom_delete_user_home_content_files(rustdesk_t)
-userdom_connectto_stream(rustdesk_t)
-userdom_rw_inherited_user_pipes(rustdesk_t)
-userdom_transition_login_userdomain(rustdesk_t)
-userdom_nnp_transition_login_userdomain(rustdesk_t)
-userdom_noatsecure_login_userdomain(rustdesk_t)
-userdom_sigchld_login_userdomain(rustdesk_t)
-userdom_use_user_ptys(rustdesk_t)
-userdom_watch_user_ptys(rustdesk_t)
-userdom_watch_reads_user_ptys(rustdesk_t)
-
-allow rustdesk_t self:process setsched;
-
-ifdef(`distro_redhat',`
- fs_manage_tmpfs_files(rustdesk_t)
- fs_manage_tmpfs_symlinks(rustdesk_t)
- fs_manage_tmpfs_sockets(rustdesk_t)
- fs_manage_tmpfs_chr_files(rustdesk_t)
- fs_exec_tmpfs_files(rustdesk_t)
- fs_read_tmpfs_symlinks(rustdesk_t)
- fs_tmpfs_filetrans(rustdesk_t, initctl_t, fifo_file)
- fs_tmpfs_filetrans_named_content(rustdesk_t)
- fs_relabelfrom_tmpfs_lnk_files(rustdesk_t)
-
- logging_stream_connect_syslog(rustdesk_t)
- logging_relabel_syslog_pid_socket(rustdesk_t)
-')
-
-corecmd_shell_domtrans(rustdesk_t, initrc_t)
-
-storage_raw_rw_fixed_disk(rustdesk_t)
-
-sysnet_read_dhcpc_state(rustdesk_t)
-
-allow rustdesk_t self:system all_system_perms;
-allow rustdesk_t self:system module_load;
-allow rustdesk_t self:unix_dgram_socket { create_socket_perms sendto };
-allow rustdesk_t self:process { setkeycreate setsockcreate setfscreate setrlimit setexec };
-allow rustdesk_t self:process { getcap setcap };
-allow rustdesk_t self:unix_stream_socket { create_stream_socket_perms connectto recvfrom };
-allow rustdesk_t self:netlink_kobject_uevent_socket create_socket_perms;
-allow rustdesk_t self:netlink_selinux_socket create_socket_perms;
-allow rustdesk_t self:unix_dgram_socket lock;
-# Until systemd is fixed
-allow daemon rustdesk_t:socket_class_set { getopt read getattr ioctl setopt write };
-allow rustdesk_t self:udp_socket create_socket_perms;
-allow rustdesk_t self:netlink_route_socket create_netlink_socket_perms;
-
-allow rustdesk_t initrc_t:unix_dgram_socket create_socket_perms;
-
-kernel_list_unlabeled(rustdesk_t)
-kernel_read_unlabeled_lnk_files(rustdesk_t)
-kernel_read_network_state(rustdesk_t)
-kernel_rw_all_sysctls(rustdesk_t)
-kernel_rw_security_state(rustdesk_t)
-kernel_rw_usermodehelper_state(rustdesk_t)
-kernel_read_software_raid_state(rustdesk_t)
-kernel_unmount_debugfs(rustdesk_t)
-kernel_setsched(rustdesk_t)
-kernel_mounton_kernel_sysctl(rustdesk_t)
-
-dev_write_kmsg(rustdesk_t)
-dev_write_urand(rustdesk_t)
-dev_rw_lvm_control(rustdesk_t)
-dev_rw_autofs(rustdesk_t)
-dev_manage_generic_symlinks(rustdesk_t)
-dev_manage_generic_dirs(rustdesk_t)
-dev_manage_generic_files(rustdesk_t)
-dev_read_generic_chr_files(rustdesk_t)
-dev_relabel_generic_dev_dirs(rustdesk_t)
-dev_relabel_all_dev_nodes(rustdesk_t)
-dev_relabel_all_dev_files(rustdesk_t)
-dev_manage_sysfs_dirs(rustdesk_t)
-dev_relabel_sysfs_dirs(rustdesk_t)
-dev_rw_wireless(rustdesk_t)
-
-files_search_all(rustdesk_t)
-files_mounton_all_mountpoints(rustdesk_t)
-files_unmount_all_file_type_fs(rustdesk_t)
-files_remount_all_file_type_fs(rustdesk_t)
-files_mounton_kernel_symbol_table(rustdesk_t)
-files_manage_all_pid_dirs(rustdesk_t)
-files_write_all_pid_sockets(rustdesk_t)
-files_manage_etc_dirs(rustdesk_t)
-files_manage_generic_tmp_dirs(rustdesk_t)
-files_relabel_all_pid_dirs(rustdesk_t)
-files_relabel_all_pid_files(rustdesk_t)
-files_create_all_pid_sockets(rustdesk_t)
-files_delete_all_pids(rustdesk_t)
-files_exec_generic_pid_files(rustdesk_t)
-files_create_all_pid_pipes(rustdesk_t)
-files_create_all_spool_sockets(rustdesk_t)
-files_delete_all_spool_sockets(rustdesk_t)
-files_create_var_lib_dirs(rustdesk_t)
-files_create_var_lib_symlinks(rustdesk_t)
-files_read_var_lib_symlinks(rustdesk_t)
-files_manage_urandom_seed(rustdesk_t)
-files_list_locks(rustdesk_t)
-files_list_spool(rustdesk_t)
-files_list_var(rustdesk_t)
-files_write_var_dirs(rustdesk_t)
-files_manage_var_symlinks(rustdesk_t)
-files_setattr_var_dirs(rustdesk_t)
-files_list_boot(rustdesk_t)
-files_list_home(rustdesk_t)
-files_create_lock_dirs(rustdesk_t)
-files_relabel_all_files(rustdesk_t)
-files_read_kernel_modules(rustdesk_t)
-files_map_kernel_modules(rustdesk_t)
-files_dontaudit_mounton_isid(rustdesk_t)
-files_delete_tmp_files(rustdesk_t)
-files_delete_tmp_pipes(rustdesk_t)
-files_delete_tmp_sockets(rustdesk_t)
-fs_getattr_all_fs(rustdesk_t)
-fs_manage_cgroup_dirs(rustdesk_t)
-fs_manage_cgroup_files(rustdesk_t)
-fs_manage_bpf_dirs(rustdesk_t)
-fs_manage_bpf_files(rustdesk_t)
-fs_manage_hugetlbfs_dirs(rustdesk_t)
-fs_manage_tmpfs_dirs(rustdesk_t)
-fs_relabel_tmpfs_blk_file(rustdesk_t)
-fs_relabel_tmpfs_chr_file(rustdesk_t)
-fs_relabel_pstore_dirs(rustdesk_t)
-fs_relabel_tmpfs_dirs(rustdesk_t)
-fs_relabel_tmpfs_files(rustdesk_t)
-fs_relabel_tmpfs_fifo_files(rustdesk_t)
-fs_mount_all_fs(rustdesk_t)
-fs_unmount_all_fs(rustdesk_t)
-fs_remount_all_fs(rustdesk_t)
-fs_list_all(rustdesk_t)
-fs_list_auto_mountpoints(rustdesk_t)
-fs_register_binary_executable_type(rustdesk_t)
-fs_relabel_tmpfs_sock_file(rustdesk_t)
-fs_rw_tmpfs_files(rustdesk_t)
-fs_relabel_cgroup_dirs(rustdesk_t)
-fs_search_cgroup_dirs(rustdesk_t)
-# for network namespaces
-fs_read_nsfs_files(rustdesk_t)
-
-storage_getattr_removable_dev(rustdesk_t)
-
-term_relabel_ptys_dirs(rustdesk_t)
-
-auth_relabel_login_records(rustdesk_t)
-auth_relabel_pam_console_data_dirs(rustdesk_t)
-auth_manage_faillog(rustdesk_t)
-
-clock_read_adjtime(rustdesk_t)
-
-init_read_script_state(rustdesk_t)
-
-seutil_read_file_contexts(rustdesk_t)
-
-systemd_exec_systemctl(rustdesk_t)
-systemd_manage_home_content(rustdesk_t)
-systemd_manage_unit_dirs(rustdesk_t)
-systemd_manage_random_seed(rustdesk_t)
-systemd_manage_all_unit_files(rustdesk_t)
-systemd_logger_stream_connect(rustdesk_t)
-systemd_login_manage_pid_files(rustdesk_t)
-systemd_config_all_services(rustdesk_t)
-systemd_relabelto_fifo_file_passwd_run(rustdesk_t)
-systemd_relabel_unit_dirs(rustdesk_t)
-systemd_relabel_unit_files(rustdesk_t)
-systemd_relabel_unit_symlinks(rustdesk_t)
-systemd_login_status(rustdesk_t)
-systemd_map_networkd_exec_files(rustdesk_t)
-systemd_map_resolved_exec_files(rustdesk_t)
-systemd_rfkill_setattr_lib(rustdesk_t)
-systemd_rfkill_mounton_var_lib(rustdesk_t)
-systemd_rfkill_manage_lib_dirs(rustdesk_t)
-systemd_timedated_mounton_var_lib(rustdesk_t)
-systemd_mounton_inhibit_dir(rustdesk_t)
-systemd_timedated_manage_lib_dirs(rustdesk_t)
-systemd_login_mounton_pid_dirs(rustdesk_t)
-systemd_mounton_inherited_logind_sessions_dirs(rustdesk_t)
-systemd_delete_private_tmp(rustdesk_t)
-systemd_userdbd_stream_connect(rustdesk_t)
-systemd_userdbd_runtime_filetrans(rustdesk_t)
-systemd_userdbd_runtime_manage_symlinks(rustdesk_t)
-systemd_write_inherited_logind_sessions_pipes(rustdesk_t)
-
-create_sock_files_pattern(rustdesk_t, init_sock_file_type, init_sock_file_type)
-
-create_dirs_pattern(rustdesk_t, var_log_t, var_log_t)
-
-auth_use_nsswitch(rustdesk_t)
-auth_rw_login_records(rustdesk_t)
-auth_rw_lastlog(rustdesk_t)
-auth_domtrans_chk_passwd(rustdesk_t)
-auth_manage_passwd(rustdesk_t)
-
-allow rustdesk_t var_run_t:dir relabelto;
-
-allow rustdesk_t daemon:unix_stream_socket create_stream_socket_perms;
-allow rustdesk_t daemon:unix_dgram_socket create_socket_perms;
-allow rustdesk_t daemon:tcp_socket create_stream_socket_perms;
-allow rustdesk_t daemon:udp_socket create_socket_perms;
-allow daemon rustdesk_t:unix_dgram_socket sendto;
-# need write to /var/run/systemd/notify
-init_write_pid_socket(daemon)
-allow daemon rustdesk_t:unix_stream_socket { append write read getattr ioctl };
-
-allow rustdesk_t daemon:process siginh;
-
-ifdef(`hide_broken_symptoms',`
- # RHEL4 systems seem to have a stray
- # fds open from the initrd
- ifdef(`distro_rhel4',`
- kernel_dontaudit_use_fds(daemon)
- ')
-
- dontaudit daemon rustdesk_t:dir search_dir_perms;
- dontaudit daemon rustdesk_t:file read_file_perms;
-')
-
-dontaudit systemprocess rustdesk_t:unix_stream_socket getattr;
-
-allow rustdesk_t daemon:unix_stream_socket create_stream_socket_perms;
-allow rustdesk_t daemon:unix_dgram_socket create_socket_perms;
-allow daemon rustdesk_t:unix_stream_socket ioctl;
-allow daemon rustdesk_t:unix_dgram_socket sendto;
-
-# Handle upstart/systemd direct transition to a executable
-allow rustdesk_t systemprocess:process { dyntransition siginh };
-allow rustdesk_t systemprocess:unix_stream_socket create_stream_socket_perms;
-allow rustdesk_t systemprocess:unix_dgram_socket create_socket_perms;
-allow systemprocess rustdesk_t:unix_dgram_socket sendto;
-allow systemprocess rustdesk_t:unix_stream_socket { append write read getattr ioctl };
-
-
-##############################################################################
-#
-# Part 2. The following rules are generated by
-# `grep rustdesk /var/log/audit/audit.log | audit2allow -a -M test`
-#
-
-#============= rustdesk_t ==============
-corenet_tcp_connect_unreserved_ports(rustdesk_t)
-
-allow rustdesk_t self:process execmem;
-allow rustdesk_t data_home_t:dir { add_name create remove_name write };
-allow rustdesk_t config_home_t:dir { write add_name remove_name };
-allow rustdesk_t data_home_t:file { create link open read rename setattr unlink write };
-allow rustdesk_t config_home_t:file { create link open read rename setattr unlink write };
-allow rustdesk_t sudo_exec_t:file { execute execute_no_trans map open read } ;
-allow rustdesk_t systemd_logind_t:dbus send_msg;
-allow rustdesk_t tmp_t:file { setattr open setattr unlink write unlink };
-allow rustdesk_t user_tmp_t:file { open write read link unlink map };
-allow systemd_coredump_t rustdesk_exec_t:file read;
-allow rustdesk_t event_device_t:chr_file { append open ioctl lock read write };
-allow rustdesk_t session_dbusd_tmp_t:sock_file write;
-allow rustdesk_t unconfined_dbusd_t:unix_stream_socket connectto;
-allow unconfined_t rustdesk_exec_t:file { execute getattr open read };
-allow init_t rustdesk_exec_t:file getattr;
-allow rustdesk_t pulseaudio_home_t:file { read open write lock };
-allow rustdesk_t user_fonts_cache_t:dir { add_name remove_name } ;
-allow rustdesk_t user_fonts_cache_t:file { create open read write lock unlink };
-
-#!!!! This AVC can be allowed using the boolean 'nis_enabled'
-allow rustdesk_t unreserved_port_t:tcp_socket name_connect;
-allow rustdesk_t xserver_port_t:tcp_socket name_connect;
-allow rustdesk_t xserver_t:unix_stream_socket connectto;
-allow rustdesk_t ephemeral_port_t:tcp_socket name_connect;
-
-
-##############################################################################
-#
-# Part 3. The following rules are from the system installed rules.
-# `dnf install setools-console`
-# `sesearch -A | grep 'allow init_t ' | sed 's/allow init_t /allow rustdesk_t /g'`
-#
-
-#============= merge from init_t ==============
-allow rustdesk_t abrt_dump_oops_t:dbus send_msg;
-allow rustdesk_t abrt_upload_watch_t:dbus send_msg;
-allow rustdesk_t adjtime_t:file { ioctl lock open read };
-allow rustdesk_t aiccu_t:dbus send_msg;
-allow rustdesk_t amanda_inetd_exec_t:file ioctl;
-allow rustdesk_t amanda_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t antivirus_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t apcupsd_power_t:file { ioctl lock open read };
-allow rustdesk_t auditd_etc_t:dir { add_name remove_name write };
-allow rustdesk_t auditd_etc_t:file { append create ioctl link lock open read rename setattr unlink watch watch_reads write };
-allow rustdesk_t autofs_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t base_ro_file_type:file { execute execute_no_trans map };
-allow rustdesk_t binfmt_misc_fs_t:file { append ioctl lock open read write };
-allow rustdesk_t bitlbee_exec_t:file ioctl;
-allow rustdesk_t bitlbee_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t boltd_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t boltd_var_lib_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t boltd_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t boltd_var_lib_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t boltd_var_run_t:dir mounton;
-allow rustdesk_t boolean_type:dir { getattr ioctl lock open read search };
-allow rustdesk_t boolean_type:file { append getattr ioctl lock open read write };
-allow rustdesk_t boothd_t:dbus send_msg;
-allow rustdesk_t bootloader_exec_t:file { execute ioctl map open read };
-allow rustdesk_t bootloader_t:process transition;
-allow rustdesk_t bpf_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t bpf_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t bpf_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t bugzilla_script_t:dbus send_msg;
-allow rustdesk_t certwatch_t:dbus send_msg;
-allow rustdesk_t cgroup_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t cgroup_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t cgroup_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t cgroup_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t chkpwd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t chkpwd_t:process transition;
-allow rustdesk_t chronyc_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t chronyd_exec_t:file ioctl;
-allow rustdesk_t chronyd_keys_t:file { ioctl lock open read };
-allow rustdesk_t chronyd_restricted_t:dbus send_msg;
-allow rustdesk_t chronyd_restricted_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t chronyd_restricted_t:process transition;
-allow rustdesk_t chroot_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t cifs_helper_t:dbus send_msg;
-allow rustdesk_t cinder_domain:dbus send_msg;
-allow rustdesk_t cloudform_domain:dbus send_msg;
-allow rustdesk_t collectd_script_t:dbus send_msg;
-allow rustdesk_t comsat_exec_t:file { execute ioctl map open read };
-allow rustdesk_t comsat_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t comsat_t:process transition;
-allow rustdesk_t comsat_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t configfile:file { ioctl lock open read };
-allow rustdesk_t configfile:lnk_file read;
-allow rustdesk_t console_device_t:chr_file { read watch watch_reads };
-allow rustdesk_t consolekit_log_t:dir { add_name remove_name write };
-allow rustdesk_t consolekit_log_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t container_kvm_t:dbus send_msg;
-allow rustdesk_t container_runtime_domain:dbus send_msg;
-allow rustdesk_t container_runtime_tmpfs_t:file { ioctl lock open read };
-allow rustdesk_t container_runtime_tmpfs_t:lnk_file read;
-allow rustdesk_t container_var_lib_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t container_var_lib_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t container_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t crack_t:dbus send_msg;
-allow rustdesk_t cups_brf_t:dbus send_msg;
-allow rustdesk_t cupsd_exec_t:file ioctl;
-allow rustdesk_t cupsd_lpd_exec_t:file ioctl;
-allow rustdesk_t cupsd_lpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t cupsd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t cvs_exec_t:file ioctl;
-allow rustdesk_t cvs_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t daemon:fifo_file { append getattr ioctl lock open write };
-allow rustdesk_t daemon:process siginh;
-allow rustdesk_t daemon:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t daemon:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t daemon:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t daemon:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t dbskkd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t dbskkd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t dbskkd_t:process transition;
-allow rustdesk_t dbskkd_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t default_context_t:file { ioctl lock open read };
-allow rustdesk_t default_t:dir create;
-allow rustdesk_t devicekit_disk_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t devicekit_power_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t devicekit_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t device_node:blk_file { getattr mounton relabelfrom relabelto setattr };
-allow rustdesk_t device_node:chr_file { create getattr mounton relabelfrom relabelto setattr };
-allow rustdesk_t device_node:dir { getattr relabelfrom relabelto };
-allow rustdesk_t device_node:fifo_file { getattr relabelfrom relabelto };
-allow rustdesk_t device_node:file { create getattr mounton open relabelfrom relabelto };
-allow rustdesk_t device_node:lnk_file { getattr relabelfrom relabelto };
-allow rustdesk_t device_node:sock_file { getattr relabelfrom relabelto };
-allow rustdesk_t device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t device_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t device_t:file { append ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t device_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t devlog_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t devlog_t:sock_file { create ioctl link lock read rename setattr unlink };
-allow rustdesk_t devpts_t:chr_file { append ioctl lock read write };
-allow rustdesk_t devpts_t:dir create;
-allow rustdesk_t dhcpc_state_t:file { ioctl lock open read };
-allow rustdesk_t dhcp_state_t:file setattr;
-allow rustdesk_t direct_init_entry:file execute_no_trans;
-allow rustdesk_t dirsrvadmin_script_t:dbus send_msg;
-allow rustdesk_t domain:dir { getattr ioctl lock open read search };
-allow rustdesk_t domain:file { getattr ioctl lock open read };
-allow rustdesk_t domain:lnk_file { getattr read };
-allow rustdesk_t domain:process { getattr getpgid noatsecure rlimitinh setrlimit setsched sigchld sigkill signal signull sigstop };
-allow rustdesk_t dri_device_t:chr_file { append ioctl lock map open read write };
-allow rustdesk_t dspam_script_t:dbus send_msg;
-allow rustdesk_t efivarfs_t:file { ioctl lock open read setattr };
-allow rustdesk_t etc_aliases_t:dir { add_name remove_name write };
-allow rustdesk_t etc_aliases_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t etc_aliases_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t etc_runtime_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t etc_runtime_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t etc_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t etc_t:dir { create link mounton rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t etc_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t faillog_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t faillog_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t faillog_t:file { create link open read rename setattr unlink watch_reads write };
-allow rustdesk_t fetchmail_t:dbus send_msg;
-allow rustdesk_t filesystem_type:dir { getattr ioctl lock open read search write };
-allow rustdesk_t filesystem_type:filesystem { getattr mount remount unmount };
-allow rustdesk_t file_type:blk_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:chr_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:dir { getattr ioctl lock open read relabelfrom relabelto search };
-allow rustdesk_t file_type:fifo_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:filesystem { getattr remount unmount };
-allow rustdesk_t file_type:lnk_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:sock_file { getattr relabelfrom relabelto };
-allow rustdesk_t fingerd_exec_t:file ioctl;
-allow rustdesk_t fingerd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t fixed_disk_device_t:blk_file { append ioctl lock open read write };
-allow rustdesk_t fixed_disk_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t fixed_disk_device_t:lnk_file read;
-allow rustdesk_t flatpak_helper_t:dbus send_msg;
-allow rustdesk_t fprintd_exec_t:file { ioctl lock };
-allow rustdesk_t fprintd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t fprintd_var_lib_t:dir { mounton setattr };
-allow rustdesk_t fsadm_t:dbus send_msg;
-allow rustdesk_t fsadm_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t ftpd_exec_t:file ioctl;
-allow rustdesk_t ftpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t fwupd_cache_t:dir { remove_name rmdir write };
-allow rustdesk_t fwupd_cache_t:file unlink;
-allow rustdesk_t fwupd_t:dbus send_msg;
-allow rustdesk_t gconfdefaultsm_t:dbus send_msg;
-allow rustdesk_t geoclue_t:dbus send_msg;
-allow rustdesk_t geoclue_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t getty_exec_t:file ioctl;
-allow rustdesk_t getty_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t gitd_exec_t:file ioctl;
-allow rustdesk_t git_system_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t gnome_home_type:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t gnome_home_type:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t gnome_home_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t gnome_home_type:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t gnomesystemmm_t:dbus send_msg;
-allow rustdesk_t guest_t:dbus send_msg;
-allow rustdesk_t home_bin_t:file { execute execute_no_trans ioctl map open read };
-allow rustdesk_t home_root_t:lnk_file read;
-allow rustdesk_t hostname_etc_t:file unlink;
-allow rustdesk_t httpd_log_t:dir { add_name create setattr write };
-allow rustdesk_t httpd_tmp_t:file unlink;
-allow rustdesk_t httpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t hugetlbfs_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t hugetlbfs_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t ibacm_t:netlink_rdma_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t ibacm_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t ibacm_var_run_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t ibacm_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t inetd_child_exec_t:file ioctl;
-allow rustdesk_t inetd_child_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t initctl_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_exec_t:file { entrypoint execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t initrc_state_t:dir { add_name remove_name write };
-allow rustdesk_t initrc_state_t:file { append create execute execute_no_trans ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t initrc_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t initrc_t:process transition;
-allow rustdesk_t initrc_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t initrc_t:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t initrc_t:unix_stream_socket { accept append bind connect connectto create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t initrc_var_run_t:file { append setattr write };
-allow rustdesk_t init_script_file_type:file { execute ioctl map open read };
-allow rustdesk_t init_script_file_type:service { disable enable reload start status stop };
-allow rustdesk_t init_t:association sendto;
-allow rustdesk_t init_t:bpf { map_create map_read map_write prog_load prog_run };
-allow rustdesk_t init_t:capability2 { audit_read block_suspend bpf checkpoint_restore epolwakeup perfmon syslog wake_alarm };
-allow rustdesk_t init_t:capability { audit_write audit_control sys_module chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t init_t:cap_userns { audit_control audit_write chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_module sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t init_t:dir watch;
-allow rustdesk_t init_t:fifo_file { create link rename setattr unlink append getattr ioctl lock open read write };
-allow rustdesk_t init_t:file { append mounton write };
-allow rustdesk_t init_t:key { create read setattr view write };
-allow rustdesk_t init_t:lnk_file { ioctl lock };
-allow rustdesk_t init_t:lockdown { confidentiality integrity };
-allow rustdesk_t init_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t init_tmp_t:file { create link map open rename setattr unlink watch_reads write };
-allow rustdesk_t init_tmp_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t init_tmp_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_t:netlink_audit_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_relay nlmsg_tty_audit read setattr setopt shutdown write };
-allow rustdesk_t init_t:netlink_kobject_uevent_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:netlink_route_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_write read setattr setopt shutdown write };
-allow rustdesk_t init_t:netlink_selinux_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:packet_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:peer recv;
-allow rustdesk_t init_t:process { fork getcap getsched setcap setexec setfscreate setkeycreate setsockcreate };
-allow rustdesk_t init_t:sem { associate create destroy getattr read setattr unix_read unix_write write };
-allow rustdesk_t init_t:service { disable enable reload start status stop };
-allow rustdesk_t init_t:shm { associate create destroy getattr lock read setattr unix_read unix_write write };
-allow rustdesk_t init_t:system { disable enable halt ipc_info module_load module_request reboot reload start status stop syslog_console syslog_mod syslog_read undefined };
-allow rustdesk_t init_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read sendto setattr setopt shutdown write };
-allow rustdesk_t init_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read recvfrom sendto setattr setopt shutdown write };
-allow rustdesk_t init_t:user_namespace create;
-allow rustdesk_t init_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t init_var_lib_t:dir { create link mounton rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t init_var_lib_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t init_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t init_var_lib_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_var_run_t:blk_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_var_run_t:chr_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_var_run_t:dir mounton;
-allow rustdesk_t init_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t init_var_run_t:file { append create link mounton rename setattr watch_reads write };
-allow rustdesk_t init_var_run_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t init_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t init_var_run_t:sock_file { ioctl link lock rename };
-allow rustdesk_t insights_client_t:fifo_file read;
-allow rustdesk_t install_exec_t:file { execute ioctl map open read };
-allow rustdesk_t install_t:dbus send_msg;
-allow rustdesk_t install_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t install_t:process transition;
-allow rustdesk_t install_t:unix_stream_socket { accept append bind connect connectto create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t ipsec_conf_file_t:file { ioctl lock open read };
-allow rustdesk_t ipsec_t:unix_stream_socket connectto;
-allow rustdesk_t ipsec_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t irqbalance_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t iscsi_var_lib_t:file { ioctl lock open read };
-allow rustdesk_t jockey_t:dbus send_msg;
-allow rustdesk_t journalctl_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t kadmind_t:dbus send_msg;
-allow rustdesk_t kdump_crash_t:file { ioctl lock open read };
-allow rustdesk_t kdumpctl_t:dbus send_msg;
-allow rustdesk_t kdump_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t keepalived_unconfined_script_t:dbus send_msg;
-allow rustdesk_t kernel_t:dbus send_msg;
-allow rustdesk_t kernel_t:fd use;
-allow rustdesk_t kernel_t:fifo_file { append getattr ioctl lock read write };
-allow rustdesk_t kernel_t:system ipc_info;
-allow rustdesk_t kernel_t:unix_dgram_socket { getattr ioctl read write };
-allow rustdesk_t kernel_t:unix_stream_socket { append bind connect getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t kmod_exec_t:file ioctl;
-allow rustdesk_t kmod_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t kmscon_t:dbus send_msg;
-allow rustdesk_t kmsg_device_t:chr_file { append ioctl lock open write };
-allow rustdesk_t krb5_keytab_t:file { ioctl lock open read };
-allow rustdesk_t ktalkd_exec_t:file ioctl;
-allow rustdesk_t ktalkd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t l2tpd_t:dbus send_msg;
-allow rustdesk_t lastlog_t:file { append ioctl lock open read setattr write };
-allow rustdesk_t lastlog_t:file { open read setattr write };
-allow rustdesk_t ld_so_cache_t:file { append write };
-allow rustdesk_t lldpad_t:dbus send_msg;
-allow rustdesk_t loadkeys_t:dbus send_msg;
-allow rustdesk_t locale_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t locale_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t locale_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t lockfile:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t lockfile:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t lockfile:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t login_userdomain:process2 nnp_transition;
-allow rustdesk_t login_userdomain:process transition;
-allow rustdesk_t lvm_control_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t lvm_etc_t:file map;
-allow rustdesk_t lvm_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t lvm_var_run_t:fifo_file { append ioctl lock read write };
-allow rustdesk_t machineid_t:file { append create link mounton rename setattr unlink watch_reads write };
-allow rustdesk_t mail_spool_t:lnk_file read;
-allow rustdesk_t mandb_t:dbus send_msg;
-allow rustdesk_t mdadm_t:unix_stream_socket connectto;
-allow rustdesk_t mdadm_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t memcached_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t memory_device_t:chr_file { ioctl lock map open read };
-allow rustdesk_t mnt_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t mnt_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t mnt_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t mnt_t:lnk_file read;
-allow rustdesk_t modemmanager_t:dbus send_msg;
-allow rustdesk_t modemmanager_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t modules_dep_t:file { ioctl lock map open read };
-allow rustdesk_t modules_object_t:dir mounton;
-allow rustdesk_t modules_object_t:file { ioctl lock map open read };
-allow rustdesk_t modules_object_t:lnk_file read;
-allow rustdesk_t mon_procd_t:dbus send_msg;
-allow rustdesk_t mountpoint:dir mounton;
-allow rustdesk_t mountpoint:file mounton;
-allow rustdesk_t mount_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t mount_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t mptcpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t munin_plugin_domain:dbus send_msg;
-allow rustdesk_t munin_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t mysqld_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t mythtv_script_t:dbus send_msg;
-allow rustdesk_t naemon_t:dbus send_msg;
-allow rustdesk_t nagios_plugin_domain:dbus send_msg;
-allow rustdesk_t nagios_system_plugin_t:dbus send_msg;
-allow rustdesk_t named_conf_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t named_conf_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t named_zone_t:dir setattr;
-allow rustdesk_t net_conf_t:dir { add_name remove_name write };
-allow rustdesk_t net_conf_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t netlabel_mgmt_t:dbus send_msg;
-allow rustdesk_t networkmanager_dispatcher_plugin:dbus send_msg;
-allow rustdesk_t NetworkManager_dispatcher_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t NetworkManager_priv_helper_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t NetworkManager_t:unix_stream_socket connectto;
-allow rustdesk_t nfsd_fs_t:file { ioctl lock open read };
-allow rustdesk_t nfsidmap_t:dbus send_msg;
-allow rustdesk_t ninfod_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t non_security_file_type:dir create;
-allow rustdesk_t non_security_file_type:dir { mounton setattr write };
-allow rustdesk_t non_security_file_type:dir setattr;
-allow rustdesk_t non_security_file_type:dir watch;
-allow rustdesk_t non_security_file_type:file mounton;
-allow rustdesk_t non_security_file_type:file watch;
-allow rustdesk_t non_security_file_type:lnk_file watch;
-allow rustdesk_t nrpe_exec_t:file ioctl;
-allow rustdesk_t nrpe_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t nsfs_t:file { getattr ioctl lock open read };
-allow rustdesk_t nsswitch_domain:dbus send_msg;
-allow rustdesk_t openshift_cgroup_read_t:dbus send_msg;
-allow rustdesk_t openshift_net_read_t:dbus send_msg;
-allow rustdesk_t oracleasm_t:dbus send_msg;
-allow rustdesk_t passwd_file_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t pcscd_t:unix_stream_socket connectto;
-allow rustdesk_t pdns_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t pegasus_openlmi_domain:dbus send_msg;
-allow rustdesk_t pidfile:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t pidfile:fifo_file { create open unlink };
-allow rustdesk_t pidfile:file { ioctl lock map open read unlink };
-allow rustdesk_t pidfile:lnk_file read;
-allow rustdesk_t pidfile:sock_file { append create open setattr unlink write };
-allow rustdesk_t pkcs_slotd_tmpfs_t:file unlink;
-allow rustdesk_t pkcs_slotd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t pkcs_slotd_t:shm destroy;
-allow rustdesk_t plymouthd_t:unix_stream_socket connectto;
-allow rustdesk_t plymouth_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t policykit_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t port_type:tcp_socket name_bind;
-allow rustdesk_t port_type:udp_socket name_bind;
-allow rustdesk_t postfix_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t print_spool_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t print_spool_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t print_spool_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t print_spool_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t proc_net_t:lnk_file { getattr read };
-allow rustdesk_t proc_security_t:file { append write };
-allow rustdesk_t proc_type:dir { getattr ioctl lock mounton open read search };
-allow rustdesk_t proc_type:file { getattr ioctl lock mounton open read };
-allow rustdesk_t ptchown_t:dbus send_msg;
-allow rustdesk_t ptynode:chr_file { append ioctl lock open read write };
-allow rustdesk_t qmail_tcp_env_exec_t:file { execute ioctl map open read };
-allow rustdesk_t qmail_tcp_env_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t qmail_tcp_env_t:process transition;
-allow rustdesk_t qmail_tcp_env_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t qpidd_t:dbus send_msg;
-allow rustdesk_t quota_exec_t:file { execute ioctl map open read };
-allow rustdesk_t quota_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t quota_t:process transition;
-allow rustdesk_t quota_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t radiusd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t random_device_t:chr_file { ioctl lock open read };
-allow rustdesk_t random_seed_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t rdisc_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t rhsmcertd_t:dbus send_msg;
-allow rustdesk_t rlogind_exec_t:file ioctl;
-allow rustdesk_t rlogind_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t root_t:dir write;
-allow rustdesk_t rpm_script_t:unix_stream_socket { append bind connect getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t rpm_var_cache_t:file { ioctl lock open read };
-allow rustdesk_t rpm_var_cache_t:lnk_file read;
-allow rustdesk_t rpm_var_lib_t:file { ioctl lock map open read };
-allow rustdesk_t rpm_var_lib_t:lnk_file read;
-allow rustdesk_t rshd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t rshd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t rshd_t:process transition;
-allow rustdesk_t rshd_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t rshd_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t rsync_exec_t:file ioctl;
-allow rustdesk_t rsync_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t rustdesk_exec_t:file { entrypoint execute ioctl lock map open read };
-allow rustdesk_t rustdesk_t:association sendto;
-allow rustdesk_t rustdesk_t:bpf { map_create map_read map_write prog_load prog_run };
-allow rustdesk_t rustdesk_t:capability2 { audit_read block_suspend bpf checkpoint_restore epolwakeup perfmon syslog wake_alarm };
-allow rustdesk_t rustdesk_t:capability { audit_write chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t rustdesk_t:capability sys_module;
-allow rustdesk_t rustdesk_t:cap_userns { audit_control audit_write chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_module sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t rustdesk_t:dbus send_msg;
-allow rustdesk_t rustdesk_t:dir watch;
-allow rustdesk_t rustdesk_t:fifo_file { create link rename setattr unlink };
-allow rustdesk_t rustdesk_t:fifo_file open;
-allow rustdesk_t rustdesk_t:file { append mounton write };
-allow rustdesk_t rustdesk_t:key { create read setattr view write };
-allow rustdesk_t rustdesk_t:lnk_file { ioctl lock };
-allow rustdesk_t rustdesk_t:lockdown { confidentiality integrity };
-allow rustdesk_t rustdesk_t:netlink_audit_socket { append bind connect create lock nlmsg_read nlmsg_relay nlmsg_tty_audit setattr shutdown };
-allow rustdesk_t rustdesk_t:netlink_kobject_uevent_socket { append bind connect create lock setattr shutdown };
-allow rustdesk_t rustdesk_t:netlink_route_socket { append bind connect create lock nlmsg_read nlmsg_write setattr shutdown };
-allow rustdesk_t rustdesk_t:netlink_selinux_socket { append bind connect create lock setattr shutdown };
-allow rustdesk_t rustdesk_t:packet_socket { append bind connect create lock setattr shutdown };
-allow rustdesk_t rustdesk_t:peer recv;
-allow rustdesk_t rustdesk_t:process { fork getcap getsched setcap setexec setfscreate setkeycreate setsockcreate };
-allow rustdesk_t rustdesk_t:sem { associate create destroy getattr read setattr unix_read unix_write write };
-allow rustdesk_t rustdesk_t:service { disable enable reload start status stop };
-allow rustdesk_t rustdesk_t:shm { associate create destroy getattr lock read setattr unix_read unix_write write };
-allow rustdesk_t rustdesk_t:system { disable enable halt ipc_info module_load module_request reboot reload start status stop syslog_console syslog_mod syslog_read undefined };
-allow rustdesk_t rustdesk_t:unix_stream_socket { connectto recvfrom };
-allow rustdesk_t rustdesk_t:user_namespace create;
-allow rustdesk_t sblim_domain:dbus send_msg;
-allow rustdesk_t security_t:file map;
-allow rustdesk_t security_t:security { check_context compute_av compute_create compute_relabel compute_user load_policy };
-allow rustdesk_t selinux_config_t:file { ioctl lock open read };
-allow rustdesk_t selinux_config_t:lnk_file read;
-allow rustdesk_t selinux_login_config_t:file { ioctl lock open read };
-allow rustdesk_t selinux_login_config_t:lnk_file read;
-allow rustdesk_t semanage_store_t:file { ioctl lock open read };
-allow rustdesk_t semanage_store_t:lnk_file read;
-allow rustdesk_t session_dbusd_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t shell_exec_t:file entrypoint;
-allow rustdesk_t smbcontrol_t:dbus send_msg;
-allow rustdesk_t smokeping_cgi_script_t:dbus send_msg;
-allow rustdesk_t spc_t:dbus send_msg;
-allow rustdesk_t speech_dispatcher_t:dbus send_msg;
-allow rustdesk_t spoolfile:sock_file { create open setattr unlink };
-allow rustdesk_t sshd_exec_t:file ioctl;
-allow rustdesk_t sshd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t ssh_keysign_t:dbus send_msg;
-allow rustdesk_t sslh_t:dbus send_msg;
-allow rustdesk_t sssd_var_lib_t:sock_file { create setattr unlink };
-allow rustdesk_t staff_t:fd use;
-allow rustdesk_t stratisd_data_t:lnk_file read;
-allow rustdesk_t stunnel_exec_t:file ioctl;
-allow rustdesk_t stunnel_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t sulogin_exec_t:file ioctl;
-allow rustdesk_t sulogin_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t svc_start_exec_t:file ioctl;
-allow rustdesk_t svc_start_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t svirt_file_type:chr_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t svirt_file_type:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t svirt_file_type:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t svirt_file_type:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t svirt_file_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t svirt_sandbox_domain:process transition;
-allow rustdesk_t svirt_sandbox_domain:unix_dgram_socket sendto;
-allow rustdesk_t svirt_tcg_t:dbus send_msg;
-allow rustdesk_t svirt_t:dbus send_msg;
-allow rustdesk_t swat_exec_t:file { execute ioctl map open read };
-allow rustdesk_t swat_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t swat_t:process transition;
-allow rustdesk_t swat_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t sysctl_kernel_t:file mounton;
-allow rustdesk_t sysctl_type:dir { getattr ioctl lock mounton open read search };
-allow rustdesk_t sysctl_type:file { append getattr ioctl lock open read setattr write };
-allow rustdesk_t sysfs_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t sysfs_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t sysfs_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t sysfs_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t syslogd_t:netlink_audit_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_write read setattr setopt shutdown write };
-allow rustdesk_t syslogd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_bootchart_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t system_dbusd_t:dbus acquire_svc;
-allow rustdesk_t system_dbusd_var_run_t:sock_file { read watch };
-allow rustdesk_t systemd_coredump_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_gpt_generator_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_home_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_home_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_home_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_hostnamed_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_hwdb_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_importd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_initctl_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_journal_upload_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_localed_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_logger_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_logger_t:unix_stream_socket connectto;
-allow rustdesk_t systemd_logind_inhibit_var_run_t:dir mounton;
-allow rustdesk_t systemd_logind_inhibit_var_run_t:fifo_file write;
-allow rustdesk_t systemd_logind_sessions_t:dir mounton;
-allow rustdesk_t systemd_logind_sessions_t:fifo_file write;
-allow rustdesk_t systemd_logind_t:fd use;
-allow rustdesk_t systemd_logind_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_logind_t:system status;
-allow rustdesk_t systemd_logind_var_run_t:dir mounton;
-allow rustdesk_t systemd_logind_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t systemd_machined_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_modules_load_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_mount_directory:dir { create mounton };
-allow rustdesk_t systemd_networkd_exec_t:file map;
-allow rustdesk_t systemd_networkd_t:netlink_route_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_write read setattr setopt shutdown write };
-allow rustdesk_t systemd_networkd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_network_generator_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_notify_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_passwd_agent_exec_t:file { execute ioctl lock map open read };
-allow rustdesk_t systemd_passwd_agent_exec_t:file { ioctl lock };
-allow rustdesk_t systemd_passwd_agent_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_passwd_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t systemd_passwd_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t systemd_passwd_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t systemd_private_tmp_type:dir { remove_name rmdir write };
-allow rustdesk_t systemd_private_tmp_type:fifo_file unlink;
-allow rustdesk_t systemd_private_tmp_type:file unlink;
-allow rustdesk_t systemd_private_tmp_type:lnk_file unlink;
-allow rustdesk_t systemd_private_tmp_type:sock_file unlink;
-allow rustdesk_t systemd_pstore_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_resolved_exec_t:file map;
-allow rustdesk_t systemd_resolved_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_rfkill_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_rfkill_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_sleep_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_socket_proxyd_t:unix_stream_socket connectto;
-allow rustdesk_t systemd_sysctl_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_systemctl_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t systemd_timedated_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_timedated_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_timedated_var_lib_t:lnk_file read;
-allow rustdesk_t systemd_tmpfiles_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_unit_file_type:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_unit_file_type:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_unit_file_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_unit_file_type:service { disable enable reload start status stop };
-allow rustdesk_t systemd_userdbd_runtime_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_userdbd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemprocess:process { dyntransition siginh };
-allow rustdesk_t systemprocess:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t systemprocess:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t tangd_db_t:file { ioctl lock open read };
-allow rustdesk_t tangd_t:dbus send_msg;
-allow rustdesk_t targetclid_t:dbus send_msg;
-allow rustdesk_t tcpd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t tcpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t tcpd_t:process transition;
-allow rustdesk_t tcpd_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t tcpd_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t telnetd_exec_t:file ioctl;
-allow rustdesk_t telnetd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t tftpd_exec_t:file ioctl;
-allow rustdesk_t tftpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t thin_domain:dbus send_msg;
-allow rustdesk_t thumb_t:dbus send_msg;
-allow rustdesk_t timedatex_t:dbus send_msg;
-allow rustdesk_t tlp_t:dbus send_msg;
-allow rustdesk_t tmpfs_t:chr_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t tmpfs_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t tmpfs_t:file { append create execute execute_no_trans ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t tmpfs_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t tmpfs_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t tmpreaper_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t tmp_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t tmp_t:fifo_file unlink;
-allow rustdesk_t tmp_t:sock_file unlink;
-allow rustdesk_t tpm_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t tty_device_t:chr_file { append ioctl lock open read watch watch_reads write };
-allow rustdesk_t ttynode:chr_file { append ioctl lock read write };
-allow rustdesk_t udev_rules_t:dir { add_name remove_name write };
-allow rustdesk_t udev_rules_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t udev_t:netlink_kobject_uevent_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:fifo_file { append getattr ioctl lock open write };
-allow rustdesk_t unconfined_service_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t unconfined_service_t:process { siginh transition };
-allow rustdesk_t unconfined_service_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t unlabeled_t:file { ioctl lock open read };
-allow rustdesk_t unlabeled_t:lnk_file read;
-allow rustdesk_t updpwd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t updpwd_t:process transition;
-allow rustdesk_t urandom_device_t:chr_file { append write };
-allow rustdesk_t usbtty_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t user_devpts_t:chr_file { watch watch_reads };
-allow rustdesk_t userdomain:fifo_file { append getattr ioctl lock read write };
-allow rustdesk_t userdomain:unix_stream_socket { append bind connect connectto getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t userdomain:unix_stream_socket connectto;
-allow rustdesk_t user_home_dir_t:lnk_file read;
-allow rustdesk_t user_home_t:file unlink;
-allow rustdesk_t user_t:fd use;
-allow rustdesk_t user_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t user_tmp_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t user_tmp_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t user_tty_device_t:chr_file { open watch watch_reads };
-allow rustdesk_t usr_t:dir { add_name remove_name write };
-allow rustdesk_t uucpd_exec_t:file ioctl;
-allow rustdesk_t uucpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t uuidd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t uuidd_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t uuidd_var_run_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t uuidd_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t var_lib_nfs_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_lib_t:dir { add_name create remove_name setattr write };
-allow rustdesk_t var_lib_t:dir { create setattr };
-allow rustdesk_t var_lib_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_lib_t:lnk_file { create read write };
-allow rustdesk_t var_log_t:dir { add_name create remove_name setattr write };
-allow rustdesk_t var_log_t:dir { create setattr };
-allow rustdesk_t var_log_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_log_t:file { create link map open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_log_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t var_run_t:file { append execute execute_no_trans write };
-allow rustdesk_t var_run_t:lnk_file unlink;
-allow rustdesk_t var_spool_t:dir { add_name remove_name write };
-allow rustdesk_t var_t:dir { add_name create remove_name setattr write };
-allow rustdesk_t var_t:dir { create setattr };
-allow rustdesk_t var_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t virsh_t:dbus send_msg;
-allow rustdesk_t virtd_t:unix_stream_socket connectto;
-allow rustdesk_t virt_etc_rw_t:file { ioctl lock open read };
-allow rustdesk_t virt_etc_rw_t:lnk_file read;
-allow rustdesk_t virtio_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t vnstatd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t watchdog_device_t:chr_file { append ioctl lock open write };
-allow rustdesk_t watchdog_t:dbus send_msg;
-allow rustdesk_t wireguard_t:dbus send_msg;
-allow rustdesk_t wireless_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t wtmp_t:file { append ioctl lock open read write };
-allow rustdesk_t wtmp_t:file { open read write };
-allow rustdesk_t xdm_exec_t:file ioctl;
-allow rustdesk_t xdm_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t xdm_var_lib_t:file { ioctl lock open read };
-allow rustdesk_t xdm_var_lib_t:lnk_file read;
-allow rustdesk_t xenconsoled_t:dbus send_msg;
-allow rustdesk_t xend_t:dbus send_msg;
-allow rustdesk_t xguest_t:dbus send_msg;
-allow rustdesk_t xserver_port_t:tcp_socket name_connect;
-allow rustdesk_t xserver_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t xserver_t:unix_stream_socket connectto;
-
-
-```
-## rustdesk.fc
-This file defines the file context for RustDesk in SELinux. It ensures that RustDesk executes with the correct security context:
-```text
-
-/usr/bin/rustdesk -- gen_context(system_u:object_r:rustdesk_exec_t,s0)
-```
-
-
-## rustdesk.if
-This interface file contains metadata about RustDesk’s SELinux policy:
-```text
-
-# RustDesk
-```
-
-
-## Makefile
-The Makefile is used to compile and apply the SELinux module for RustDesk, ensuring that necessary security policies are enforced.
-```makefile
-
-TARGET?=rustdesk
-MODULES?=${TARGET:=.pp.bz2}
-SHAREDIR?=/usr/share
-SELINUXTYPE?=targeted
-
-all: ${TARGET:=.pp.bz2}
-
-%.pp.bz2: %.pp
- @echo Compressing $^ -\> $@
- bzip2 -9 $^
-
-%.pp: %.te
- make -f ${SHAREDIR}/selinux/devel/Makefile $@
-
-clean:
- rm -f *~ *.tc *.pp *.pp.bz2
- rm -rf tmp *.tar.gz
-
-man: install-policy
- sepolicy manpage --path . --domain ${TARGET}_t
-
-install-policy: all
- semodule -i ${TARGET}.pp.bz2
-
-install: man
- install -D -m 644 ${TARGET}.pp.bz2 ${DESTDIR}${SHAREDIR}/selinux/packages/${SELINUXTYPE}/${TARGET}.pp.bz2
- install -D -m 644 ${TARGET}_selinux.8 ${DESTDIR}${SHAREDIR}/man/man8/
-
-```
-
-#### Enable directly
-
-View the security context of RustDesk before modification:
-
-```sh
-$ ls -lZ /usr/lib/rustdesk/rustdesk
--rwxr-xr-x. 1 root root system_u:object_r:lib_t:s0 25456 Oct 8 19:58 /usr/lib/rustdesk/rustdesk
-$ ps -eZ | grep rustdesk
-system_u:system_r:init_t:s0 80439 ? 00:00:02 rustdesk
-```
-
-Run:
-
-```sh
-
-$ cd rustdesk-selinux-1.0
-$ make
-$ sudo make install-policy
-$ semodule -l | grep rustdesk
-rustdesk
-$ sudo chcon -t rustdesk_exec_t /usr/bin/rustdesk
-$ sudo systemctl restart rustdesk
-
-```
-
-View the security context again:
-
-```sh
-$ ls -lZ /usr/lib/rustdesk/rustdesk
--rwxr-xr-x. 1 root root system_u:object_r:rustdesk_exec_t:s0 25456 Oct 8 19:58 /usr/lib/rustdesk/rustdesk
-$ ps -eZ | grep rustdesk
-system_u:system_r:rustdesk_t:s0 110565 ? 00:00:00 rustdesk
-```
-
-#### Enable through rpm installation
-
-You can use the `sepolicy generate` command:
-
-```sh
-$ # install dependencies
-$ sudo dnf install -y rpm rpm-build binutils
-$ # generate policy
-$ sepolicy generate --init /usr/lib/rustdesk/rustdesk
-$ tree
-.
-├── rustdesk.fc
-├── rustdesk.if
-├── rustdesk_selinux.spec
-├── rustdesk.sh
-└── rustdesk.te
-$ # Edit the rustdesk.te
-$
-$
-$ # generate rpm package rustdesk_selinux-1.0-1.fc38.src.rpm
-$ sudo ./rustdesk.sh
-$ # install package
-$ sudo dnf install -y rustdesk_selinux-1.0-1.fc38.src.rpm
-$ # restart the service
-$ sudo systemctl restart rustdesk
-```
-
-### Iteratively Add Policies
-
-```sh
-$ cd /tmp
-$ grep rustdesk_t /var/log/audit/audit.log | audit2allow -a -M rustdesk_tmp
-$ cd
-$ # merge rustdesk_tmp.te to rustdesk.te
-$ make clean && make && sudo make install-policy
-```
-
-## References
-
-- [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials)
-- [SELinux Policy module installation](https://fedoraproject.org/wiki/SELinux/IndependentPolicy#SELinux_Policy_module_installation)
-- [How to create SELinux custom policy rpm package](https://lukas-vrabec.com/index.php/2015/07/07/how-to-create-selinux-custom-policy-rpm-package/)
diff --git a/content/client/linux/SELinux/_index.es.md b/content/client/linux/SELinux/_index.es.md
deleted file mode 100644
index 0dffbd6..0000000
--- a/content/client/linux/SELinux/_index.es.md
+++ /dev/null
@@ -1,1893 +0,0 @@
----
-title: SELinux
-weight: 100
----
-
-Algunas distribuciones (como Fedora) tienen activo SELinux por defecto, lo que puede causar que el servicio de RustDesk falle en iniciar y correr normalmente.
-
-Puedes ejecutar `sestatus` en la terminal para chequear si SELinux esta habilitado o no.
-
-Dependiendo del estado de SELinux podes recibir dos de estas salidas:
-
-```bash
-# Habilitado
-SELinux status: enabled
-...
-
-# Deshabilitado
-SELinux status: disabled
-...
-```
-
-# Añadir Políticas de SELinux
-
-Para una introducción a SELinux, consulte [SELinux/Tutorials (ingles)](https://wiki.gentoo.org/wiki/SELinux/Tutorials).
-
-Vamos a tomar Fedora 38 como un ejemplo para introducirte a como añadir políticas SELinux.
-
-```bash
-sudo dnf install selinux-policy-devel make
-```
-
-Al agregar políticas de SELinux se requiere determinar el tipo de servicio, el tipo de servicio se encuentra en el contexto de seguridad del proceso.
-
-```bash
-$ ps -eZ | grep rustdesk
-system_u:system_r:init_t:s0 80439 ? 00:00:02 rustdesk
-```
-`system_u:system_r:init_t:s0` es el contexto de seguridad del proceso de RustDesk, el tercer campo "init_t" es el tipo de proceso.
-
-Hay dos maneras de escribir reglas de tipo SELinux :
-
-1. Añadir las reglas al tipo `init_t` que existe por defecto.
-2. Añadir un nuevo tipo `rustdesk_t` y añadir las reglas a este.
-
-Con el primer método vas a tener que hacer modificaciones menores, pero como el `int_t` es modificado en este método, estas modificaciones se aplicaran a otros servicios que usen el tipo `int_t`. **Su uso no es recomendado**.
-
-El segundo método se basa en crear un nuevo tipo de cero con todas las reglas. Va a ser necesario añadir muchas reglas y según el sistema estas reglas serán diferentes. Quizás sea necesario hacer ajustes durante el uso del programa.
-
-
-## Usa el Tipo Por Defecto
-
-El tipo por defecto del servicio de RustDesk es `init_t`, que es de determinado por [las reglas de herencia de contexto de SELinux (ingles)](https://wiki.gentoo.org/wiki/SELinux/Tutorials/How_does_a_process_get_into_a_certain_context).
-
-**PRECAUCIÓN**: Modificar los tipos por defecto significa que las políticas de otros servicios también puedan cambiar. Usa este método con precaución!
-
-Modifica el archivo de reglas rustdesk.te:
-
-```text
-module rustdesk 1.0;
-
-require {
- type event_device_t;
- type xserver_t;
- type xserver_port_t;
- type sudo_exec_t;
- type init_t;
- type ephemeral_port_t;
- type user_tmp_t;
- type user_fonts_cache_t;
- type pulseaudio_home_t;
- type session_dbusd_tmp_t;
- type unconfined_dbusd_t;
- class process execmem;
- class file { open read create write execute execute_no_trans map setattr lock link unlink };
- class unix_stream_socket connectto;
- class tcp_socket name_connect;
- class dir { add_name remove_name };
- class sock_file write;
- class chr_file { open read write } ;
-}
-
-#============= init_t ==============
-allow init_t xserver_t:unix_stream_socket connectto;
-allow init_t sudo_exec_t:file { open read execute execute_no_trans };
-allow init_t user_tmp_t:file { open write setattr };
-allow init_t self:process execmem;
-allow init_t user_fonts_cache_t:dir { add_name remove_name };
-allow init_t user_fonts_cache_t:file { read write create open link lock unlink };
-allow init_t xserver_port_t:tcp_socket name_connect;
-allow init_t pulseaudio_home_t:file { read write open lock };
-allow init_t session_dbusd_tmp_t:sock_file write;
-allow init_t unconfined_dbusd_t:unix_stream_socket connectto;
-
-#!!!! Este avc puede ser permitido usando el booleano 'nis_enabled'
-allow init_t ephemeral_port_t:tcp_socket name_connect;
-
-#!!!! Este avc puede ser permitido usando el booleano 'domain_can_mmap_files'
-allow init_t sudo_exec_t:file map;
-
-
-#============= init_t wayland ==============
-allow init_t event_device_t:chr_file { open read write };
-
-#!!!! Este avc puede ser permitido usando el booleano 'domain_can_mmap_files'
-allow init_t user_tmp_t:file map;
-
-```
-
-Ejecuta:
-
-```bash
-checkmodule -M -m -o rustdesk.mod rustdesk.te && semodule_package -o rustdesk.pp -m rustdesk.mod && sudo semodule -i rustdesk.pp
-sudo semodule -l | grep rustdesk
-```
-
-## Crea un tipo "rustdesk_t"
-
-1. Crea un nuevo directorio. `mkdir rustdesk-selinux-1.0`
-2. Crea los archivos de políticas de SELinux. `touch Makefile rustdesk.te rustdesk.fc rustdesk.if`.
-
-
-El contenido de `rustdesk-selinux-1.0` debería verse asi:
-```text
-.
-├── Makefile
-├── rustdesk.fc
-├── rustdesk.if
-└── rustdesk.te
-```
-
-El contenido de cada archivo debería ser asi:
-
-rustdes.te:
-
-```text
-
-policy_module(rustdesk, 1.0)
-
-type rustdesk_t;
-type rustdesk_exec_t;
-
-gen_require(`
- # usado para la ejecución directa de los
- # script init por los administradores de dominio
-
- attribute direct_run_init;
- attribute direct_init;
- attribute direct_init_entry;
-
- attribute init_script_domain_type;
- attribute initrc_transition_domain;
- # Atributo utilizado por systemd para que los dominios permitan a systemd crear sock_files
- attribute init_sock_file_type;
- # Atributo para los directorios que systemd va a monitorear basado en path units
- # (leer systemd.path(5) para mas información) (Deprecado)
- attribute init_watch_path_type;
-
- # Marca tipo de proceso como daemons
- attribute daemon;
- attribute systemprocess;
- attribute systemprocess_entry;
-
- # Marca el tipo de archivo como directorio de ejecución del daemon
- attribute daemonrundir;
-
- class passwd rootok;
- class dbus { acquire_svc send_msg };
- class process execmem;
-
- type abrt_dump_oops_t;
- type abrt_upload_watch_t;
- type adjtime_t;
- type aiccu_t;
- type amanda_inetd_exec_t;
- type amanda_t;
- type antivirus_t;
- type apcupsd_power_t;
- type auditd_etc_t;
- type autofs_device_t;
- type binfmt_misc_fs_t;
- type bitlbee_exec_t;
- type bitlbee_t;
- type boltd_var_lib_t;
- type boltd_var_run_t;
- type boothd_t;
- type bootloader_exec_t;
- type bootloader_t;
- type bpf_t;
- type bugzilla_script_t;
- type certwatch_t;
- type cgroup_t;
- type chkpwd_exec_t;
- type chkpwd_t;
- type chronyc_t;
- type chronyd_exec_t;
- type chronyd_keys_t;
- type chronyd_restricted_t;
- type chroot_exec_t;
- type cifs_helper_t;
- type cinder_domain;
- type cloudform_domain;
- type collectd_script_t;
- type comsat_exec_t;
- type comsat_t;
- type config_home_t;
- type console_device_t;
- type consolekit_log_t;
- type container_kvm_t;
- type container_runtime_domain;
- type container_runtime_tmpfs_t;
- type container_var_lib_t;
- type crack_t;
- type cups_brf_t;
- type cupsd_exec_t;
- type cupsd_lpd_exec_t;
- type cupsd_lpd_t;
- type cupsd_t;
- type cvs_exec_t;
- type cvs_t;
- type data_home_t;
- type dbskkd_exec_t;
- type dbskkd_t;
- type default_context_t;
- type default_t;
- type devicekit_disk_t;
- type devicekit_power_t;
- type devicekit_t;
- type device_t;
- type devlog_t;
- type devpts_t;
- type dhcpc_state_t;
- type dhcp_state_t;
- type dirsrvadmin_script_t;
- type dri_device_t;
- type dspam_script_t;
- type efivarfs_t;
- type ephemeral_port_t;
- type etc_aliases_t;
- type etc_runtime_t;
- type etc_t;
- type event_device_t;
- type faillog_t;
- type fetchmail_t;
- type fingerd_exec_t;
- type fingerd_t;
- type fixed_disk_device_t;
- type flatpak_helper_t;
- type fprintd_exec_t;
- type fprintd_t;
- type fprintd_var_lib_t;
- type fsadm_t;
- type ftpd_exec_t;
- type ftpd_t;
- type fwupd_cache_t;
- type fwupd_t;
- type gconfdefaultsm_t;
- type geoclue_t;
- type getty_exec_t;
- type getty_t;
- type gitd_exec_t;
- type git_system_t;
- type gnome_home_type;
- type gnomesystemmm_t;
- type guest_t;
- type home_bin_t;
- type home_root_t;
- type hostname_etc_t;
- type httpd_log_t;
- type httpd_t;
- type httpd_tmp_t;
- type hugetlbfs_t;
- type ibacm_t;
- type ibacm_var_run_t;
- type inetd_child_exec_t;
- type inetd_child_t;
- type initctl_t;
- type init_exec_t;
- type initrc_state_t;
- type initrc_t;
- type initrc_var_run_t;
- type init_t;
- type init_tmp_t;
- type init_var_lib_t;
- type init_var_run_t;
- type insights_client_t;
- type install_exec_t;
- type install_t;
- type ipsec_conf_file_t;
- type ipsec_t;
- type ipsec_var_run_t;
- type irqbalance_t;
- type iscsi_var_lib_t;
- type jockey_t;
- type journalctl_exec_t;
- type kadmind_t;
- type kdump_crash_t;
- type kdumpctl_t;
- type kdump_t;
- type keepalived_unconfined_script_t;
- type kernel_t;
- type kmod_exec_t;
- type kmod_t;
- type kmscon_t;
- type kmsg_device_t;
- type krb5_keytab_t;
- type ktalkd_exec_t;
- type ktalkd_t;
- type l2tpd_t;
- type lastlog_t;
- type ld_so_cache_t;
- type lldpad_t;
- type loadkeys_t;
- type locale_t;
- type lvm_control_t;
- type lvm_etc_t;
- type lvm_t;
- type lvm_var_run_t;
- type machineid_t;
- type mail_spool_t;
- type mandb_t;
- type mdadm_t;
- type mdadm_var_run_t;
- type memcached_t;
- type memory_device_t;
- type mnt_t;
- type modemmanager_t;
- type modules_dep_t;
- type modules_object_t;
- type mon_procd_t;
- type mount_t;
- type mount_var_run_t;
- type mptcpd_t;
- type munin_plugin_domain;
- type munin_t;
- type mysqld_t;
- type mythtv_script_t;
- type naemon_t;
- type nagios_plugin_domain;
- type nagios_system_plugin_t;
- type named_conf_t;
- type named_zone_t;
- type net_conf_t;
- type netlabel_mgmt_t;
- type networkmanager_dispatcher_plugin;
- type NetworkManager_dispatcher_t;
- type NetworkManager_priv_helper_t;
- type NetworkManager_t;
- type nfsd_fs_t;
- type nfsidmap_t;
- type ninfod_t;
- type nrpe_exec_t;
- type nrpe_t;
- type nsfs_t;
- type openshift_cgroup_read_t;
- type openshift_net_read_t;
- type oracleasm_t;
- type passwd_file_t;
- type pcscd_t;
- type pdns_t;
- type pegasus_openlmi_domain;
- type pkcs_slotd_t;
- type pkcs_slotd_tmpfs_t;
- type plymouthd_t;
- type plymouth_exec_t;
- type policykit_t;
- type postfix_exec_t;
- type print_spool_t;
- type proc_net_t;
- type proc_security_t;
- type ptchown_t;
- type pulseaudio_home_t;
- type qmail_tcp_env_exec_t;
- type qmail_tcp_env_t;
- type qpidd_t;
- type quota_exec_t;
- type quota_t;
- type radiusd_t;
- type random_device_t;
- type random_seed_t;
- type rdisc_t;
- type rhsmcertd_t;
- type rlogind_exec_t;
- type rlogind_t;
- type root_t;
- type rpm_script_t;
- type rpm_var_cache_t;
- type rpm_var_lib_t;
- type rshd_exec_t;
- type rshd_t;
- type rsync_exec_t;
- type rsync_t;
- type rustdesk_exec_t;
- type rustdesk_t;
- type sblim_domain;
- type security_t;
- type selinux_config_t;
- type selinux_login_config_t;
- type semanage_store_t;
- type session_dbusd_tmp_t;
- type shell_exec_t;
- type smbcontrol_t;
- type smokeping_cgi_script_t;
- type spc_t;
- type speech_dispatcher_t;
- type sshd_exec_t;
- type sshd_t;
- type ssh_keysign_t;
- type sslh_t;
- type sssd_var_lib_t;
- type staff_t;
- type stratisd_data_t;
- type stunnel_exec_t;
- type stunnel_t;
- type sudo_exec_t;
- type sulogin_exec_t;
- type sulogin_t;
- type svc_start_exec_t;
- type svc_start_t;
- type svirt_file_type;
- type svirt_sandbox_domain;
- type svirt_t;
- type svirt_tcg_t;
- type swat_exec_t;
- type swat_t;
- type sysctl_kernel_t;
- type sysfs_t;
- type syslogd_t;
- type systemd_bootchart_t;
- type system_dbusd_t;
- type system_dbusd_var_run_t;
- type systemd_coredump_t;
- type systemd_gpt_generator_t;
- type systemd_home_t;
- type systemd_hostnamed_t;
- type systemd_hwdb_t;
- type systemd_importd_t;
- type systemd_initctl_t;
- type systemd_journal_upload_t;
- type systemd_localed_t;
- type systemd_logger_t;
- type systemd_logind_inhibit_var_run_t;
- type systemd_logind_sessions_t;
- type systemd_logind_t;
- type systemd_logind_var_run_t;
- type systemd_machined_t;
- type systemd_modules_load_t;
- type systemd_mount_directory;
- type systemd_networkd_exec_t;
- type systemd_networkd_t;
- type systemd_network_generator_t;
- type systemd_notify_t;
- type systemd_passwd_agent_exec_t;
- type systemd_passwd_agent_t;
- type systemd_passwd_var_run_t;
- type systemd_pstore_t;
- type systemd_resolved_exec_t;
- type systemd_resolved_t;
- type systemd_rfkill_t;
- type systemd_rfkill_var_lib_t;
- type systemd_sleep_t;
- type systemd_socket_proxyd_t;
- type systemd_sysctl_t;
- type systemd_systemctl_exec_t;
- type systemd_timedated_t;
- type systemd_timedated_var_lib_t;
- type systemd_tmpfiles_t;
- type systemd_userdbd_runtime_t;
- type systemd_userdbd_t;
- type tangd_db_t;
- type tangd_t;
- type targetclid_t;
- type tcpd_exec_t;
- type tcpd_t;
- type telnetd_exec_t;
- type telnetd_t;
- type tftpd_exec_t;
- type tftpd_t;
- type thin_domain;
- type thumb_t;
- type timedatex_t;
- type tlp_t;
- type tmpfs_t;
- type tmpreaper_t;
- type tmp_t;
- type tpm_device_t;
- type tty_device_t;
- type udev_rules_t;
- type udev_t;
- type unconfined_dbusd_t;
- type unconfined_service_t;
- type unconfined_t;
- type unlabeled_t;
- type unreserved_port_t;
- type updpwd_exec_t;
- type updpwd_t;
- type urandom_device_t;
- type usbtty_device_t;
- type user_devpts_t;
- type user_fonts_cache_t;
- type user_home_dir_t;
- type user_home_t;
- type user_t;
- type user_tmp_t;
- type user_tty_device_t;
- type usr_t;
- type uucpd_exec_t;
- type uucpd_t;
- type uuidd_t;
- type uuidd_var_run_t;
- type var_lib_nfs_t;
- type var_lib_t;
- type var_log_t;
- type var_run_t;
- type var_spool_t;
- type var_t;
- type virsh_t;
- type virtd_t;
- type virt_etc_rw_t;
- type virtio_device_t;
- type vnstatd_t;
- type watchdog_device_t;
- type watchdog_t;
- type wireguard_t;
- type wireless_device_t;
- type wtmp_t;
- type xdm_exec_t;
- type xdm_t;
- type xdm_var_lib_t;
- type xenconsoled_t;
- type xend_t;
- type xguest_t;
- type xserver_port_t;
- type xserver_t;
-')
-
-##############################################################################
-#
-# Parte 1. Las reglas siguientes son mayormente para el `init.te` de codigo abierto.
-# https://github.com/fedora-selinux/selinux-policy/blob/rawhide/policy/modules/system/init.te
-#
-# Nota: Parte 1 probablemente sea mayormente lo mismo que parte 3. pero es aceptable por ahora.
-#
-
-init_daemon_domain(rustdesk_t, rustdesk_exec_t)
-
-domain_role_change_exemption(rustdesk_t)
-domain_subj_id_change_exemption(rustdesk_t)
-domain_obj_id_change_exemption(rustdesk_t)
-role system_r types rustdesk_t;
-corecmd_shell_entry_type(rustdesk_t)
-typeattribute rustdesk_t init_script_domain_type;
-
-
-#######################################
-
-# Use capabilities. old rule:
-allow rustdesk_t self:capability ~{ audit_control audit_write sys_module };
-allow rustdesk_t self:capability2 ~{ mac_admin mac_override };
-allow rustdesk_t self:cap_userns all_cap_userns_perms;
-allow rustdesk_t self:tcp_socket { listen accept };
-allow rustdesk_t self:packet_socket create_socket_perms;
-allow rustdesk_t self:key manage_key_perms;
-allow rustdesk_t self:bpf { map_create map_read map_write prog_load prog_run };
-
-allow rustdesk_t self:file mounton;
-allow rustdesk_t self:fifo_file rw_fifo_file_perms;
-
-allow rustdesk_t self:service manage_service_perms;
-allow rustdesk_t self:user_namespace create;
-
-# Re-ejecutandose a si mismo
-can_exec(rustdesk_t, rustdesk_exec_t)
-# Ejecutando contenidos de /run/initramfs
-manage_files_pattern(rustdesk_t, initrc_state_t, initrc_state_t)
-can_exec(rustdesk_t, initrc_state_t)
-
-allow rustdesk_t initrc_t:unix_stream_socket { connectto create_stream_socket_perms };
-allow rustdesk_t initrc_t:tcp_socket create_stream_socket_perms;
-allow initrc_t rustdesk_t:unix_stream_socket { connectto rw_stream_socket_perms sendto };
-allow initrc_t rustdesk_t:fifo_file rw_fifo_file_perms;
-
-manage_files_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-manage_dirs_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-manage_lnk_files_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-manage_sock_files_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-files_tmp_filetrans(rustdesk_t, init_tmp_t, { file sock_file })
-allow rustdesk_t init_tmp_t:file map;
-
-manage_dirs_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-manage_files_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-manage_lnk_files_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-manage_sock_files_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-files_var_lib_filetrans(rustdesk_t, init_var_lib_t, { dir file })
-allow rustdesk_t init_var_lib_t:dir mounton;
-allow rustdesk_t init_var_lib_t:file map;
-
-manage_dirs_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_lnk_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_sock_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_fifo_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_blk_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_chr_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-files_pid_filetrans(rustdesk_t, init_var_run_t, { dir file blk_file chr_file fifo_file})
-allow rustdesk_t init_var_run_t:dir mounton;
-allow rustdesk_t init_var_run_t:file mounton;
-allow rustdesk_t init_var_run_t:sock_file relabelto;
-allow rustdesk_t init_var_run_t:blk_file { getattr relabelto };
-allow rustdesk_t init_var_run_t:chr_file { getattr relabelto };
-allow rustdesk_t init_var_run_t:fifo_file { getattr relabelto };
-
-allow rustdesk_t machineid_t:file manage_file_perms;
-files_pid_filetrans(rustdesk_t, machineid_t, file, "machine-id")
-files_etc_filetrans(rustdesk_t, machineid_t, file, "machine-id")
-allow rustdesk_t machineid_t:file mounton;
-
-allow rustdesk_t initctl_t:fifo_file manage_fifo_file_perms;
-dev_filetrans(rustdesk_t, initctl_t, fifo_file)
-
-# Modifica utmp.
-allow rustdesk_t initrc_var_run_t:file { rw_file_perms setattr };
-
-kernel_read_system_state(rustdesk_t)
-kernel_share_state(rustdesk_t)
-kernel_stream_connect(rustdesk_t)
-kernel_rw_stream_socket_perms(rustdesk_t)
-kernel_rw_unix_dgram_sockets(rustdesk_t)
-kernel_mounton_systemd_ProtectKernelTunables(rustdesk_t)
-kernel_read_core_if(rustdesk_t)
-kernel_mounton_core_if(rustdesk_t)
-kernel_mounton_all_sysctls(rustdesk_t)
-kernel_get_sysvipc_info(rustdesk_t)
-kernel_load_module(rustdesk_t)
-kernel_read_all_proc(rustdesk_t)
-kernel_list_all_proc(rustdesk_t)
-kernel_mounton_all_proc(rustdesk_t)
-
-# Hay un error(bug) en el kernel 4.16. muchos dominios piden module_request, por ahora no auditar
-kernel_dontaudit_request_load_module(rustdesk_t)
-
-corecmd_exec_chroot(rustdesk_t)
-corecmd_exec_bin(rustdesk_t)
-
-corenet_all_recvfrom_netlabel(rustdesk_t)
-corenet_tcp_bind_all_ports(rustdesk_t)
-corenet_udp_bind_all_ports(rustdesk_t)
-
-dev_create_all_files(rustdesk_t)
-dev_create_all_chr_files(rustdesk_t)
-dev_list_sysfs(rustdesk_t)
-dev_manage_sysfs(rustdesk_t)
-dev_mounton_all_device_nodes(rustdesk_t)
-dev_setattr_all_blk_files(rustdesk_t)
-dev_setattr_all_chr_files(rustdesk_t)
-dev_read_urand(rustdesk_t)
-dev_read_raw_memory(rustdesk_t)
-# Early devtmpfs
-dev_rw_generic_chr_files(rustdesk_t)
-dev_filetrans_all_named_dev(rustdesk_t)
-dev_write_watchdog(rustdesk_t)
-dev_rw_inherited_input_dev(rustdesk_t)
-dev_rw_dri(rustdesk_t)
-dev_rw_tpm(rustdesk_t)
-
-domain_getpgid_all_domains(rustdesk_t)
-domain_kill_all_domains(rustdesk_t)
-domain_signal_all_domains(rustdesk_t)
-domain_signull_all_domains(rustdesk_t)
-domain_sigstop_all_domains(rustdesk_t)
-domain_sigchld_all_domains(rustdesk_t)
-domain_read_all_domains_state(rustdesk_t)
-domain_getattr_all_domains(rustdesk_t)
-domain_setrlimit_all_domains(rustdesk_t)
-domain_rlimitinh_all_domains(rustdesk_t)
-domain_noatsecure_all_domains(rustdesk_t)
-domain_setpriority_all_domains(rustdesk_t)
-
-files_read_config_files(rustdesk_t)
-files_read_all_pids(rustdesk_t)
-files_map_all_pids(rustdesk_t)
-files_read_system_conf_files(rustdesk_t)
-files_rw_generic_pids(rustdesk_t)
-files_dontaudit_search_isid_type_dirs(rustdesk_t)
-files_read_isid_type_files(rustdesk_t)
-files_read_etc_runtime_files(rustdesk_t)
-files_manage_all_locks(rustdesk_t)
-files_manage_etc_runtime_files(rustdesk_t)
-files_manage_etc_symlinks(rustdesk_t)
-files_etc_filetrans_etc_runtime(rustdesk_t, file)
-# Run /etc/X11/prefdm:
-files_exec_etc_files(rustdesk_t)
-files_read_usr_files(rustdesk_t)
-files_write_root_dirs(rustdesk_t)
-# file descriptors inherited from the rootfs:
-files_dontaudit_rw_root_files(rustdesk_t)
-files_dontaudit_rw_root_chr_files(rustdesk_t)
-files_dontaudit_mounton_modules_object(rustdesk_t)
-files_manage_mnt_dirs(rustdesk_t)
-files_manage_mnt_files(rustdesk_t)
-files_read_mnt_symlinks(rustdesk_t)
-files_mounton_etc(rustdesk_t)
-files_create_default_dir(rustdesk_t)
-files_remount_rootfs(rustdesk_t)
-files_create_var_dirs(rustdesk_t)
-files_watch_non_security_dirs(rustdesk_t)
-files_watch_non_security_files(rustdesk_t)
-files_watch_non_security_lnk_files(rustdesk_t)
-
-fs_read_efivarfs_files(rustdesk_t)
-fs_setattr_efivarfs_files(rustdesk_t)
-fs_read_nfsd_files(rustdesk_t)
-
-fstools_getattr_swap_files(rustdesk_t)
-
-mcs_process_set_categories(rustdesk_t)
-
-mls_file_read_all_levels(rustdesk_t)
-mls_file_write_all_levels(rustdesk_t)
-mls_file_downgrade(rustdesk_t)
-mls_file_upgrade(rustdesk_t)
-mls_fd_use_all_levels(rustdesk_t)
-mls_fd_share_all_levels(rustdesk_t)
-mls_process_set_level(rustdesk_t)
-mls_process_write_down(rustdesk_t)
-mls_socket_read_all_levels(rustdesk_t)
-mls_socket_write_all_levels(rustdesk_t)
-mls_rangetrans_source(rustdesk_t)
-
-selinux_set_all_booleans(rustdesk_t)
-selinux_load_policy(rustdesk_t)
-selinux_mounton_fs(rustdesk_t)
-allow rustdesk_t security_t:security load_policy;
-
-selinux_compute_access_vector(rustdesk_t)
-selinux_compute_create_context(rustdesk_t)
-selinux_compute_user_contexts(rustdesk_t)
-selinux_validate_context(rustdesk_t)
-selinux_compute_relabel_context(rustdesk_t)
-selinux_unmount_fs(rustdesk_t)
-
-term_create_pty_dir(rustdesk_t)
-term_use_unallocated_ttys(rustdesk_t)
-term_setattr_unallocated_ttys(rustdesk_t)
-term_use_console(rustdesk_t)
-term_use_all_inherited_terms(rustdesk_t)
-term_use_usb_ttys(rustdesk_t)
-term_use_all_ptys(rustdesk_t)
-term_setattr_all_ptys(rustdesk_t)
-term_use_virtio_console(rustdesk_t)
-term_watch_console_dev(rustdesk_t)
-term_watch_reads_console_dev(rustdesk_t)
-term_watch_unallocated_ttys(rustdesk_t)
-term_watch_reads_unallocated_ttys(rustdesk_t)
-term_watch_user_ttys(rustdesk_t)
-term_watch_reads_user_ttys(rustdesk_t)
-
-# Ejecuta init scripts
-init_domtrans_script(rustdesk_t)
-init_exec_notrans_direct_init_entry(rustdesk_t)
-
-libs_rw_ld_so_cache(rustdesk_t)
-
-logging_create_devlog_dev(rustdesk_t)
-logging_send_syslog_msg(rustdesk_t)
-logging_send_audit_msgs(rustdesk_t)
-logging_manage_generic_logs(rustdesk_t)
-logging_mmap_generic_logs(rustdesk_t)
-logging_relabel_devlog_dev(rustdesk_t)
-logging_manage_audit_config(rustdesk_t)
-logging_create_syslog_netlink_audit_socket(rustdesk_t)
-logging_write_var_log_dirs(rustdesk_t)
-logging_manage_var_log_symlinks(rustdesk_t)
-
-seutil_read_config(rustdesk_t)
-seutil_read_login_config(rustdesk_t)
-seutil_read_default_contexts(rustdesk_t)
-seutil_read_module_store(rustdesk_t)
-
-miscfiles_manage_localization(rustdesk_t)
-miscfiles_filetrans_named_content(rustdesk_t)
-
-udev_manage_rules_files(rustdesk_t)
-
-userdom_use_user_ttys(rustdesk_t)
-userdom_manage_tmp_dirs(rustdesk_t)
-userdom_manage_tmp_sockets(rustdesk_t)
-userdom_delete_user_tmp_files(rustdesk_t)
-userdom_delete_user_home_content_files(rustdesk_t)
-userdom_connectto_stream(rustdesk_t)
-userdom_rw_inherited_user_pipes(rustdesk_t)
-userdom_transition_login_userdomain(rustdesk_t)
-userdom_nnp_transition_login_userdomain(rustdesk_t)
-userdom_noatsecure_login_userdomain(rustdesk_t)
-userdom_sigchld_login_userdomain(rustdesk_t)
-userdom_use_user_ptys(rustdesk_t)
-userdom_watch_user_ptys(rustdesk_t)
-userdom_watch_reads_user_ptys(rustdesk_t)
-
-allow rustdesk_t self:process setsched;
-
-ifdef(`distro_redhat',`
- fs_manage_tmpfs_files(rustdesk_t)
- fs_manage_tmpfs_symlinks(rustdesk_t)
- fs_manage_tmpfs_sockets(rustdesk_t)
- fs_manage_tmpfs_chr_files(rustdesk_t)
- fs_exec_tmpfs_files(rustdesk_t)
- fs_read_tmpfs_symlinks(rustdesk_t)
- fs_tmpfs_filetrans(rustdesk_t, initctl_t, fifo_file)
- fs_tmpfs_filetrans_named_content(rustdesk_t)
- fs_relabelfrom_tmpfs_lnk_files(rustdesk_t)
-
- logging_stream_connect_syslog(rustdesk_t)
- logging_relabel_syslog_pid_socket(rustdesk_t)
-')
-
-corecmd_shell_domtrans(rustdesk_t, initrc_t)
-
-storage_raw_rw_fixed_disk(rustdesk_t)
-
-sysnet_read_dhcpc_state(rustdesk_t)
-
-allow rustdesk_t self:system all_system_perms;
-allow rustdesk_t self:system module_load;
-allow rustdesk_t self:unix_dgram_socket { create_socket_perms sendto };
-allow rustdesk_t self:process { setkeycreate setsockcreate setfscreate setrlimit setexec };
-allow rustdesk_t self:process { getcap setcap };
-allow rustdesk_t self:unix_stream_socket { create_stream_socket_perms connectto recvfrom };
-allow rustdesk_t self:netlink_kobject_uevent_socket create_socket_perms;
-allow rustdesk_t self:netlink_selinux_socket create_socket_perms;
-allow rustdesk_t self:unix_dgram_socket lock;
-# Until systemd is fixed
-allow daemon rustdesk_t:socket_class_set { getopt read getattr ioctl setopt write };
-allow rustdesk_t self:udp_socket create_socket_perms;
-allow rustdesk_t self:netlink_route_socket create_netlink_socket_perms;
-
-allow rustdesk_t initrc_t:unix_dgram_socket create_socket_perms;
-
-kernel_list_unlabeled(rustdesk_t)
-kernel_read_unlabeled_lnk_files(rustdesk_t)
-kernel_read_network_state(rustdesk_t)
-kernel_rw_all_sysctls(rustdesk_t)
-kernel_rw_security_state(rustdesk_t)
-kernel_rw_usermodehelper_state(rustdesk_t)
-kernel_read_software_raid_state(rustdesk_t)
-kernel_unmount_debugfs(rustdesk_t)
-kernel_setsched(rustdesk_t)
-kernel_mounton_kernel_sysctl(rustdesk_t)
-
-dev_write_kmsg(rustdesk_t)
-dev_write_urand(rustdesk_t)
-dev_rw_lvm_control(rustdesk_t)
-dev_rw_autofs(rustdesk_t)
-dev_manage_generic_symlinks(rustdesk_t)
-dev_manage_generic_dirs(rustdesk_t)
-dev_manage_generic_files(rustdesk_t)
-dev_read_generic_chr_files(rustdesk_t)
-dev_relabel_generic_dev_dirs(rustdesk_t)
-dev_relabel_all_dev_nodes(rustdesk_t)
-dev_relabel_all_dev_files(rustdesk_t)
-dev_manage_sysfs_dirs(rustdesk_t)
-dev_relabel_sysfs_dirs(rustdesk_t)
-dev_rw_wireless(rustdesk_t)
-
-files_search_all(rustdesk_t)
-files_mounton_all_mountpoints(rustdesk_t)
-files_unmount_all_file_type_fs(rustdesk_t)
-files_remount_all_file_type_fs(rustdesk_t)
-files_mounton_kernel_symbol_table(rustdesk_t)
-files_manage_all_pid_dirs(rustdesk_t)
-files_write_all_pid_sockets(rustdesk_t)
-files_manage_etc_dirs(rustdesk_t)
-files_manage_generic_tmp_dirs(rustdesk_t)
-files_relabel_all_pid_dirs(rustdesk_t)
-files_relabel_all_pid_files(rustdesk_t)
-files_create_all_pid_sockets(rustdesk_t)
-files_delete_all_pids(rustdesk_t)
-files_exec_generic_pid_files(rustdesk_t)
-files_create_all_pid_pipes(rustdesk_t)
-files_create_all_spool_sockets(rustdesk_t)
-files_delete_all_spool_sockets(rustdesk_t)
-files_create_var_lib_dirs(rustdesk_t)
-files_create_var_lib_symlinks(rustdesk_t)
-files_read_var_lib_symlinks(rustdesk_t)
-files_manage_urandom_seed(rustdesk_t)
-files_list_locks(rustdesk_t)
-files_list_spool(rustdesk_t)
-files_list_var(rustdesk_t)
-files_write_var_dirs(rustdesk_t)
-files_manage_var_symlinks(rustdesk_t)
-files_setattr_var_dirs(rustdesk_t)
-files_list_boot(rustdesk_t)
-files_list_home(rustdesk_t)
-files_create_lock_dirs(rustdesk_t)
-files_relabel_all_files(rustdesk_t)
-files_read_kernel_modules(rustdesk_t)
-files_map_kernel_modules(rustdesk_t)
-files_dontaudit_mounton_isid(rustdesk_t)
-files_delete_tmp_files(rustdesk_t)
-files_delete_tmp_pipes(rustdesk_t)
-files_delete_tmp_sockets(rustdesk_t)
-fs_getattr_all_fs(rustdesk_t)
-fs_manage_cgroup_dirs(rustdesk_t)
-fs_manage_cgroup_files(rustdesk_t)
-fs_manage_bpf_dirs(rustdesk_t)
-fs_manage_bpf_files(rustdesk_t)
-fs_manage_hugetlbfs_dirs(rustdesk_t)
-fs_manage_tmpfs_dirs(rustdesk_t)
-fs_relabel_tmpfs_blk_file(rustdesk_t)
-fs_relabel_tmpfs_chr_file(rustdesk_t)
-fs_relabel_pstore_dirs(rustdesk_t)
-fs_relabel_tmpfs_dirs(rustdesk_t)
-fs_relabel_tmpfs_files(rustdesk_t)
-fs_relabel_tmpfs_fifo_files(rustdesk_t)
-fs_mount_all_fs(rustdesk_t)
-fs_unmount_all_fs(rustdesk_t)
-fs_remount_all_fs(rustdesk_t)
-fs_list_all(rustdesk_t)
-fs_list_auto_mountpoints(rustdesk_t)
-fs_register_binary_executable_type(rustdesk_t)
-fs_relabel_tmpfs_sock_file(rustdesk_t)
-fs_rw_tmpfs_files(rustdesk_t)
-fs_relabel_cgroup_dirs(rustdesk_t)
-fs_search_cgroup_dirs(rustdesk_t)
-# for network namespaces
-fs_read_nsfs_files(rustdesk_t)
-
-storage_getattr_removable_dev(rustdesk_t)
-
-term_relabel_ptys_dirs(rustdesk_t)
-
-auth_relabel_login_records(rustdesk_t)
-auth_relabel_pam_console_data_dirs(rustdesk_t)
-auth_manage_faillog(rustdesk_t)
-
-clock_read_adjtime(rustdesk_t)
-
-init_read_script_state(rustdesk_t)
-
-seutil_read_file_contexts(rustdesk_t)
-
-systemd_exec_systemctl(rustdesk_t)
-systemd_manage_home_content(rustdesk_t)
-systemd_manage_unit_dirs(rustdesk_t)
-systemd_manage_random_seed(rustdesk_t)
-systemd_manage_all_unit_files(rustdesk_t)
-systemd_logger_stream_connect(rustdesk_t)
-systemd_login_manage_pid_files(rustdesk_t)
-systemd_config_all_services(rustdesk_t)
-systemd_relabelto_fifo_file_passwd_run(rustdesk_t)
-systemd_relabel_unit_dirs(rustdesk_t)
-systemd_relabel_unit_files(rustdesk_t)
-systemd_relabel_unit_symlinks(rustdesk_t)
-systemd_login_status(rustdesk_t)
-systemd_map_networkd_exec_files(rustdesk_t)
-systemd_map_resolved_exec_files(rustdesk_t)
-systemd_rfkill_setattr_lib(rustdesk_t)
-systemd_rfkill_mounton_var_lib(rustdesk_t)
-systemd_rfkill_manage_lib_dirs(rustdesk_t)
-systemd_timedated_mounton_var_lib(rustdesk_t)
-systemd_mounton_inhibit_dir(rustdesk_t)
-systemd_timedated_manage_lib_dirs(rustdesk_t)
-systemd_login_mounton_pid_dirs(rustdesk_t)
-systemd_mounton_inherited_logind_sessions_dirs(rustdesk_t)
-systemd_delete_private_tmp(rustdesk_t)
-systemd_userdbd_stream_connect(rustdesk_t)
-systemd_userdbd_runtime_filetrans(rustdesk_t)
-systemd_userdbd_runtime_manage_symlinks(rustdesk_t)
-systemd_write_inherited_logind_sessions_pipes(rustdesk_t)
-
-create_sock_files_pattern(rustdesk_t, init_sock_file_type, init_sock_file_type)
-
-create_dirs_pattern(rustdesk_t, var_log_t, var_log_t)
-
-auth_use_nsswitch(rustdesk_t)
-auth_rw_login_records(rustdesk_t)
-auth_rw_lastlog(rustdesk_t)
-auth_domtrans_chk_passwd(rustdesk_t)
-auth_manage_passwd(rustdesk_t)
-
-allow rustdesk_t var_run_t:dir relabelto;
-
-allow rustdesk_t daemon:unix_stream_socket create_stream_socket_perms;
-allow rustdesk_t daemon:unix_dgram_socket create_socket_perms;
-allow rustdesk_t daemon:tcp_socket create_stream_socket_perms;
-allow rustdesk_t daemon:udp_socket create_socket_perms;
-allow daemon rustdesk_t:unix_dgram_socket sendto;
-# need write to /var/run/systemd/notify
-init_write_pid_socket(daemon)
-allow daemon rustdesk_t:unix_stream_socket { append write read getattr ioctl };
-
-allow rustdesk_t daemon:process siginh;
-
-ifdef(`hide_broken_symptoms',`
- # RHEL4 systems seem to have a stray
- # fds open from the initrd
- ifdef(`distro_rhel4',`
- kernel_dontaudit_use_fds(daemon)
- ')
-
- dontaudit daemon rustdesk_t:dir search_dir_perms;
- dontaudit daemon rustdesk_t:file read_file_perms;
-')
-
-dontaudit systemprocess rustdesk_t:unix_stream_socket getattr;
-
-allow rustdesk_t daemon:unix_stream_socket create_stream_socket_perms;
-allow rustdesk_t daemon:unix_dgram_socket create_socket_perms;
-allow daemon rustdesk_t:unix_stream_socket ioctl;
-allow daemon rustdesk_t:unix_dgram_socket sendto;
-
-# Handle upstart/systemd direct transition to a executable
-allow rustdesk_t systemprocess:process { dyntransition siginh };
-allow rustdesk_t systemprocess:unix_stream_socket create_stream_socket_perms;
-allow rustdesk_t systemprocess:unix_dgram_socket create_socket_perms;
-allow systemprocess rustdesk_t:unix_dgram_socket sendto;
-allow systemprocess rustdesk_t:unix_stream_socket { append write read getattr ioctl };
-
-
-##############################################################################
-#
-# parte 2. Las siguientes reglas son generadas por:
-# `grep rustdesk /var/log/audit/audit.log | audit2allow -a -M test`
-#
-
-#============= rustdesk_t ==============
-allow rustdesk_t self:process execmem;
-allow rustdesk_t data_home_t:dir { add_name create remove_name write };
-allow rustdesk_t config_home_t:dir { write add_name remove_name };
-allow rustdesk_t data_home_t:file { create link open read rename setattr unlink write };
-allow rustdesk_t config_home_t:file { create link open read rename setattr unlink write };
-allow rustdesk_t sudo_exec_t:file { execute execute_no_trans map open read } ;
-allow rustdesk_t systemd_logind_t:dbus send_msg;
-allow rustdesk_t tmp_t:file { setattr open setattr unlink write unlink };
-allow rustdesk_t user_tmp_t:file { open write read link unlink map };
-allow systemd_coredump_t rustdesk_exec_t:file read;
-allow rustdesk_t event_device_t:chr_file { append open ioctl lock read write };
-allow rustdesk_t session_dbusd_tmp_t:sock_file write;
-allow rustdesk_t unconfined_dbusd_t:unix_stream_socket connectto;
-allow unconfined_t rustdesk_exec_t:file { execute getattr open read };
-allow init_t rustdesk_exec_t:file getattr;
-allow rustdesk_t pulseaudio_home_t:file { read open write lock };
-allow rustdesk_t user_fonts_cache_t:dir { add_name remove_name } ;
-allow rustdesk_t user_fonts_cache_t:file { create open read write lock unlink };
-
-#!!!! This avc can be allowed using the boolean 'nis_enabled'
-allow rustdesk_t unreserved_port_t:tcp_socket name_connect;
-allow rustdesk_t xserver_port_t:tcp_socket name_connect;
-allow rustdesk_t xserver_t:unix_stream_socket connectto;
-allow rustdesk_t ephemeral_port_t:tcp_socket name_connect;
-
-
-##############################################################################
-#
-# Parte 3. Las siguientes reglas son para las reglas instaladas por el sistema
-# `dnf install setools-console`
-# `sesearch -A | grep 'allow init_t ' | sed 's/allow init_t /allow rustdesk_t /g'`
-#
-
-#============= merge from init_t ==============
-allow rustdesk_t abrt_dump_oops_t:dbus send_msg;
-allow rustdesk_t abrt_upload_watch_t:dbus send_msg;
-allow rustdesk_t adjtime_t:file { ioctl lock open read };
-allow rustdesk_t aiccu_t:dbus send_msg;
-allow rustdesk_t amanda_inetd_exec_t:file ioctl;
-allow rustdesk_t amanda_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t antivirus_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t apcupsd_power_t:file { ioctl lock open read };
-allow rustdesk_t auditd_etc_t:dir { add_name remove_name write };
-allow rustdesk_t auditd_etc_t:file { append create ioctl link lock open read rename setattr unlink watch watch_reads write };
-allow rustdesk_t autofs_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t base_ro_file_type:file { execute execute_no_trans map };
-allow rustdesk_t binfmt_misc_fs_t:file { append ioctl lock open read write };
-allow rustdesk_t bitlbee_exec_t:file ioctl;
-allow rustdesk_t bitlbee_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t boltd_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t boltd_var_lib_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t boltd_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t boltd_var_lib_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t boltd_var_run_t:dir mounton;
-allow rustdesk_t boolean_type:dir { getattr ioctl lock open read search };
-allow rustdesk_t boolean_type:file { append getattr ioctl lock open read write };
-allow rustdesk_t boothd_t:dbus send_msg;
-allow rustdesk_t bootloader_exec_t:file { execute ioctl map open read };
-allow rustdesk_t bootloader_t:process transition;
-allow rustdesk_t bpf_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t bpf_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t bpf_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t bugzilla_script_t:dbus send_msg;
-allow rustdesk_t certwatch_t:dbus send_msg;
-allow rustdesk_t cgroup_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t cgroup_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t cgroup_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t cgroup_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t chkpwd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t chkpwd_t:process transition;
-allow rustdesk_t chronyc_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t chronyd_exec_t:file ioctl;
-allow rustdesk_t chronyd_keys_t:file { ioctl lock open read };
-allow rustdesk_t chronyd_restricted_t:dbus send_msg;
-allow rustdesk_t chronyd_restricted_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t chronyd_restricted_t:process transition;
-allow rustdesk_t chroot_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t cifs_helper_t:dbus send_msg;
-allow rustdesk_t cinder_domain:dbus send_msg;
-allow rustdesk_t cloudform_domain:dbus send_msg;
-allow rustdesk_t collectd_script_t:dbus send_msg;
-allow rustdesk_t comsat_exec_t:file { execute ioctl map open read };
-allow rustdesk_t comsat_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t comsat_t:process transition;
-allow rustdesk_t comsat_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t configfile:file { ioctl lock open read };
-allow rustdesk_t configfile:lnk_file read;
-allow rustdesk_t console_device_t:chr_file { read watch watch_reads };
-allow rustdesk_t consolekit_log_t:dir { add_name remove_name write };
-allow rustdesk_t consolekit_log_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t container_kvm_t:dbus send_msg;
-allow rustdesk_t container_runtime_domain:dbus send_msg;
-allow rustdesk_t container_runtime_tmpfs_t:file { ioctl lock open read };
-allow rustdesk_t container_runtime_tmpfs_t:lnk_file read;
-allow rustdesk_t container_var_lib_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t container_var_lib_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t container_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t crack_t:dbus send_msg;
-allow rustdesk_t cups_brf_t:dbus send_msg;
-allow rustdesk_t cupsd_exec_t:file ioctl;
-allow rustdesk_t cupsd_lpd_exec_t:file ioctl;
-allow rustdesk_t cupsd_lpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t cupsd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t cvs_exec_t:file ioctl;
-allow rustdesk_t cvs_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t daemon:fifo_file { append getattr ioctl lock open write };
-allow rustdesk_t daemon:process siginh;
-allow rustdesk_t daemon:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t daemon:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t daemon:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t daemon:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t dbskkd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t dbskkd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t dbskkd_t:process transition;
-allow rustdesk_t dbskkd_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t default_context_t:file { ioctl lock open read };
-allow rustdesk_t default_t:dir create;
-allow rustdesk_t devicekit_disk_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t devicekit_power_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t devicekit_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t device_node:blk_file { getattr mounton relabelfrom relabelto setattr };
-allow rustdesk_t device_node:chr_file { create getattr mounton relabelfrom relabelto setattr };
-allow rustdesk_t device_node:dir { getattr relabelfrom relabelto };
-allow rustdesk_t device_node:fifo_file { getattr relabelfrom relabelto };
-allow rustdesk_t device_node:file { create getattr mounton open relabelfrom relabelto };
-allow rustdesk_t device_node:lnk_file { getattr relabelfrom relabelto };
-allow rustdesk_t device_node:sock_file { getattr relabelfrom relabelto };
-allow rustdesk_t device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t device_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t device_t:file { append ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t device_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t devlog_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t devlog_t:sock_file { create ioctl link lock read rename setattr unlink };
-allow rustdesk_t devpts_t:chr_file { append ioctl lock read write };
-allow rustdesk_t devpts_t:dir create;
-allow rustdesk_t dhcpc_state_t:file { ioctl lock open read };
-allow rustdesk_t dhcp_state_t:file setattr;
-allow rustdesk_t direct_init_entry:file execute_no_trans;
-allow rustdesk_t dirsrvadmin_script_t:dbus send_msg;
-allow rustdesk_t domain:dir { getattr ioctl lock open read search };
-allow rustdesk_t domain:file { getattr ioctl lock open read };
-allow rustdesk_t domain:lnk_file { getattr read };
-allow rustdesk_t domain:process { getattr getpgid noatsecure rlimitinh setrlimit setsched sigchld sigkill signal signull sigstop };
-allow rustdesk_t dri_device_t:chr_file { append ioctl lock map open read write };
-allow rustdesk_t dspam_script_t:dbus send_msg;
-allow rustdesk_t efivarfs_t:file { ioctl lock open read setattr };
-allow rustdesk_t etc_aliases_t:dir { add_name remove_name write };
-allow rustdesk_t etc_aliases_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t etc_aliases_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t etc_runtime_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t etc_runtime_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t etc_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t etc_t:dir { create link mounton rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t etc_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t faillog_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t faillog_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t faillog_t:file { create link open read rename setattr unlink watch_reads write };
-allow rustdesk_t fetchmail_t:dbus send_msg;
-allow rustdesk_t filesystem_type:dir { getattr ioctl lock open read search write };
-allow rustdesk_t filesystem_type:filesystem { getattr mount remount unmount };
-allow rustdesk_t file_type:blk_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:chr_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:dir { getattr ioctl lock open read relabelfrom relabelto search };
-allow rustdesk_t file_type:fifo_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:filesystem { getattr remount unmount };
-allow rustdesk_t file_type:lnk_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:sock_file { getattr relabelfrom relabelto };
-allow rustdesk_t fingerd_exec_t:file ioctl;
-allow rustdesk_t fingerd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t fixed_disk_device_t:blk_file { append ioctl lock open read write };
-allow rustdesk_t fixed_disk_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t fixed_disk_device_t:lnk_file read;
-allow rustdesk_t flatpak_helper_t:dbus send_msg;
-allow rustdesk_t fprintd_exec_t:file { ioctl lock };
-allow rustdesk_t fprintd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t fprintd_var_lib_t:dir { mounton setattr };
-allow rustdesk_t fsadm_t:dbus send_msg;
-allow rustdesk_t fsadm_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t ftpd_exec_t:file ioctl;
-allow rustdesk_t ftpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t fwupd_cache_t:dir { remove_name rmdir write };
-allow rustdesk_t fwupd_cache_t:file unlink;
-allow rustdesk_t fwupd_t:dbus send_msg;
-allow rustdesk_t gconfdefaultsm_t:dbus send_msg;
-allow rustdesk_t geoclue_t:dbus send_msg;
-allow rustdesk_t geoclue_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t getty_exec_t:file ioctl;
-allow rustdesk_t getty_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t gitd_exec_t:file ioctl;
-allow rustdesk_t git_system_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t gnome_home_type:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t gnome_home_type:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t gnome_home_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t gnome_home_type:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t gnomesystemmm_t:dbus send_msg;
-allow rustdesk_t guest_t:dbus send_msg;
-allow rustdesk_t home_bin_t:file { execute execute_no_trans ioctl map open read };
-allow rustdesk_t home_root_t:lnk_file read;
-allow rustdesk_t hostname_etc_t:file unlink;
-allow rustdesk_t httpd_log_t:dir { add_name create setattr write };
-allow rustdesk_t httpd_tmp_t:file unlink;
-allow rustdesk_t httpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t hugetlbfs_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t hugetlbfs_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t ibacm_t:netlink_rdma_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t ibacm_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t ibacm_var_run_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t ibacm_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t inetd_child_exec_t:file ioctl;
-allow rustdesk_t inetd_child_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t initctl_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_exec_t:file { entrypoint execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t initrc_state_t:dir { add_name remove_name write };
-allow rustdesk_t initrc_state_t:file { append create execute execute_no_trans ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t initrc_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t initrc_t:process transition;
-allow rustdesk_t initrc_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t initrc_t:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t initrc_t:unix_stream_socket { accept append bind connect connectto create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t initrc_var_run_t:file { append setattr write };
-allow rustdesk_t init_script_file_type:file { execute ioctl map open read };
-allow rustdesk_t init_script_file_type:service { disable enable reload start status stop };
-allow rustdesk_t init_t:association sendto;
-allow rustdesk_t init_t:bpf { map_create map_read map_write prog_load prog_run };
-allow rustdesk_t init_t:capability2 { audit_read block_suspend bpf checkpoint_restore epolwakeup perfmon syslog wake_alarm };
-allow rustdesk_t init_t:capability { audit_write audit_control sys_module chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t init_t:cap_userns { audit_control audit_write chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_module sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t init_t:dir watch;
-allow rustdesk_t init_t:fifo_file { create link rename setattr unlink append getattr ioctl lock open read write };
-allow rustdesk_t init_t:file { append mounton write };
-allow rustdesk_t init_t:key { create read setattr view write };
-allow rustdesk_t init_t:lnk_file { ioctl lock };
-allow rustdesk_t init_t:lockdown { confidentiality integrity };
-allow rustdesk_t init_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t init_tmp_t:file { create link map open rename setattr unlink watch_reads write };
-allow rustdesk_t init_tmp_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t init_tmp_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_t:netlink_audit_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_relay nlmsg_tty_audit read setattr setopt shutdown write };
-allow rustdesk_t init_t:netlink_kobject_uevent_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:netlink_route_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_write read setattr setopt shutdown write };
-allow rustdesk_t init_t:netlink_selinux_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:packet_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:peer recv;
-allow rustdesk_t init_t:process { fork getcap getsched setcap setexec setfscreate setkeycreate setsockcreate };
-allow rustdesk_t init_t:sem { associate create destroy getattr read setattr unix_read unix_write write };
-allow rustdesk_t init_t:service { disable enable reload start status stop };
-allow rustdesk_t init_t:shm { associate create destroy getattr lock read setattr unix_read unix_write write };
-allow rustdesk_t init_t:system { disable enable halt ipc_info module_load module_request reboot reload start status stop syslog_console syslog_mod syslog_read undefined };
-allow rustdesk_t init_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read sendto setattr setopt shutdown write };
-allow rustdesk_t init_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read recvfrom sendto setattr setopt shutdown write };
-allow rustdesk_t init_t:user_namespace create;
-allow rustdesk_t init_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t init_var_lib_t:dir { create link mounton rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t init_var_lib_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t init_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t init_var_lib_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_var_run_t:blk_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_var_run_t:chr_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_var_run_t:dir mounton;
-allow rustdesk_t init_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t init_var_run_t:file { append create link mounton rename setattr watch_reads write };
-allow rustdesk_t init_var_run_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t init_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t init_var_run_t:sock_file { ioctl link lock rename };
-allow rustdesk_t insights_client_t:fifo_file read;
-allow rustdesk_t install_exec_t:file { execute ioctl map open read };
-allow rustdesk_t install_t:dbus send_msg;
-allow rustdesk_t install_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t install_t:process transition;
-allow rustdesk_t install_t:unix_stream_socket { accept append bind connect connectto create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t ipsec_conf_file_t:file { ioctl lock open read };
-allow rustdesk_t ipsec_t:unix_stream_socket connectto;
-allow rustdesk_t ipsec_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t irqbalance_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t iscsi_var_lib_t:file { ioctl lock open read };
-allow rustdesk_t jockey_t:dbus send_msg;
-allow rustdesk_t journalctl_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t kadmind_t:dbus send_msg;
-allow rustdesk_t kdump_crash_t:file { ioctl lock open read };
-allow rustdesk_t kdumpctl_t:dbus send_msg;
-allow rustdesk_t kdump_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t keepalived_unconfined_script_t:dbus send_msg;
-allow rustdesk_t kernel_t:dbus send_msg;
-allow rustdesk_t kernel_t:fd use;
-allow rustdesk_t kernel_t:fifo_file { append getattr ioctl lock read write };
-allow rustdesk_t kernel_t:system ipc_info;
-allow rustdesk_t kernel_t:unix_dgram_socket { getattr ioctl read write };
-allow rustdesk_t kernel_t:unix_stream_socket { append bind connect getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t kmod_exec_t:file ioctl;
-allow rustdesk_t kmod_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t kmscon_t:dbus send_msg;
-allow rustdesk_t kmsg_device_t:chr_file { append ioctl lock open write };
-allow rustdesk_t krb5_keytab_t:file { ioctl lock open read };
-allow rustdesk_t ktalkd_exec_t:file ioctl;
-allow rustdesk_t ktalkd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t l2tpd_t:dbus send_msg;
-allow rustdesk_t lastlog_t:file { append ioctl lock open read setattr write };
-allow rustdesk_t lastlog_t:file { open read setattr write };
-allow rustdesk_t ld_so_cache_t:file { append write };
-allow rustdesk_t lldpad_t:dbus send_msg;
-allow rustdesk_t loadkeys_t:dbus send_msg;
-allow rustdesk_t locale_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t locale_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t locale_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t lockfile:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t lockfile:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t lockfile:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t login_userdomain:process2 nnp_transition;
-allow rustdesk_t login_userdomain:process transition;
-allow rustdesk_t lvm_control_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t lvm_etc_t:file map;
-allow rustdesk_t lvm_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t lvm_var_run_t:fifo_file { append ioctl lock read write };
-allow rustdesk_t machineid_t:file { append create link mounton rename setattr unlink watch_reads write };
-allow rustdesk_t mail_spool_t:lnk_file read;
-allow rustdesk_t mandb_t:dbus send_msg;
-allow rustdesk_t mdadm_t:unix_stream_socket connectto;
-allow rustdesk_t mdadm_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t memcached_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t memory_device_t:chr_file { ioctl lock map open read };
-allow rustdesk_t mnt_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t mnt_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t mnt_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t mnt_t:lnk_file read;
-allow rustdesk_t modemmanager_t:dbus send_msg;
-allow rustdesk_t modemmanager_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t modules_dep_t:file { ioctl lock map open read };
-allow rustdesk_t modules_object_t:dir mounton;
-allow rustdesk_t modules_object_t:file { ioctl lock map open read };
-allow rustdesk_t modules_object_t:lnk_file read;
-allow rustdesk_t mon_procd_t:dbus send_msg;
-allow rustdesk_t mountpoint:dir mounton;
-allow rustdesk_t mountpoint:file mounton;
-allow rustdesk_t mount_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t mount_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t mptcpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t munin_plugin_domain:dbus send_msg;
-allow rustdesk_t munin_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t mysqld_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t mythtv_script_t:dbus send_msg;
-allow rustdesk_t naemon_t:dbus send_msg;
-allow rustdesk_t nagios_plugin_domain:dbus send_msg;
-allow rustdesk_t nagios_system_plugin_t:dbus send_msg;
-allow rustdesk_t named_conf_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t named_conf_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t named_zone_t:dir setattr;
-allow rustdesk_t net_conf_t:dir { add_name remove_name write };
-allow rustdesk_t net_conf_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t netlabel_mgmt_t:dbus send_msg;
-allow rustdesk_t networkmanager_dispatcher_plugin:dbus send_msg;
-allow rustdesk_t NetworkManager_dispatcher_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t NetworkManager_priv_helper_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t NetworkManager_t:unix_stream_socket connectto;
-allow rustdesk_t nfsd_fs_t:file { ioctl lock open read };
-allow rustdesk_t nfsidmap_t:dbus send_msg;
-allow rustdesk_t ninfod_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t non_security_file_type:dir create;
-allow rustdesk_t non_security_file_type:dir { mounton setattr write };
-allow rustdesk_t non_security_file_type:dir setattr;
-allow rustdesk_t non_security_file_type:dir watch;
-allow rustdesk_t non_security_file_type:file mounton;
-allow rustdesk_t non_security_file_type:file watch;
-allow rustdesk_t non_security_file_type:lnk_file watch;
-allow rustdesk_t nrpe_exec_t:file ioctl;
-allow rustdesk_t nrpe_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t nsfs_t:file { getattr ioctl lock open read };
-allow rustdesk_t nsswitch_domain:dbus send_msg;
-allow rustdesk_t openshift_cgroup_read_t:dbus send_msg;
-allow rustdesk_t openshift_net_read_t:dbus send_msg;
-allow rustdesk_t oracleasm_t:dbus send_msg;
-allow rustdesk_t passwd_file_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t pcscd_t:unix_stream_socket connectto;
-allow rustdesk_t pdns_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t pegasus_openlmi_domain:dbus send_msg;
-allow rustdesk_t pidfile:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t pidfile:fifo_file { create open unlink };
-allow rustdesk_t pidfile:file { ioctl lock map open read unlink };
-allow rustdesk_t pidfile:lnk_file read;
-allow rustdesk_t pidfile:sock_file { append create open setattr unlink write };
-allow rustdesk_t pkcs_slotd_tmpfs_t:file unlink;
-allow rustdesk_t pkcs_slotd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t pkcs_slotd_t:shm destroy;
-allow rustdesk_t plymouthd_t:unix_stream_socket connectto;
-allow rustdesk_t plymouth_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t policykit_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t port_type:tcp_socket name_bind;
-allow rustdesk_t port_type:udp_socket name_bind;
-allow rustdesk_t postfix_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t print_spool_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t print_spool_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t print_spool_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t print_spool_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t proc_net_t:lnk_file { getattr read };
-allow rustdesk_t proc_security_t:file { append write };
-allow rustdesk_t proc_type:dir { getattr ioctl lock mounton open read search };
-allow rustdesk_t proc_type:file { getattr ioctl lock mounton open read };
-allow rustdesk_t ptchown_t:dbus send_msg;
-allow rustdesk_t ptynode:chr_file { append ioctl lock open read write };
-allow rustdesk_t qmail_tcp_env_exec_t:file { execute ioctl map open read };
-allow rustdesk_t qmail_tcp_env_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t qmail_tcp_env_t:process transition;
-allow rustdesk_t qmail_tcp_env_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t qpidd_t:dbus send_msg;
-allow rustdesk_t quota_exec_t:file { execute ioctl map open read };
-allow rustdesk_t quota_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t quota_t:process transition;
-allow rustdesk_t quota_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t radiusd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t random_device_t:chr_file { ioctl lock open read };
-allow rustdesk_t random_seed_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t rdisc_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t rhsmcertd_t:dbus send_msg;
-allow rustdesk_t rlogind_exec_t:file ioctl;
-allow rustdesk_t rlogind_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t root_t:dir write;
-allow rustdesk_t rpm_script_t:unix_stream_socket { append bind connect getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t rpm_var_cache_t:file { ioctl lock open read };
-allow rustdesk_t rpm_var_cache_t:lnk_file read;
-allow rustdesk_t rpm_var_lib_t:file { ioctl lock map open read };
-allow rustdesk_t rpm_var_lib_t:lnk_file read;
-allow rustdesk_t rshd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t rshd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t rshd_t:process transition;
-allow rustdesk_t rshd_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t rshd_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t rsync_exec_t:file ioctl;
-allow rustdesk_t rsync_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t rustdesk_exec_t:file { entrypoint execute ioctl lock map open read };
-allow rustdesk_t rustdesk_t:association sendto;
-allow rustdesk_t rustdesk_t:bpf { map_create map_read map_write prog_load prog_run };
-allow rustdesk_t rustdesk_t:capability2 { audit_read block_suspend bpf checkpoint_restore epolwakeup perfmon syslog wake_alarm };
-allow rustdesk_t rustdesk_t:capability { audit_write chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t rustdesk_t:capability sys_module;
-allow rustdesk_t rustdesk_t:cap_userns { audit_control audit_write chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_module sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t rustdesk_t:dbus send_msg;
-allow rustdesk_t rustdesk_t:dir watch;
-allow rustdesk_t rustdesk_t:fifo_file { create link rename setattr unlink };
-allow rustdesk_t rustdesk_t:fifo_file open;
-allow rustdesk_t rustdesk_t:file { append mounton write };
-allow rustdesk_t rustdesk_t:key { create read setattr view write };
-allow rustdesk_t rustdesk_t:lnk_file { ioctl lock };
-allow rustdesk_t rustdesk_t:lockdown { confidentiality integrity };
-allow rustdesk_t rustdesk_t:netlink_audit_socket { append bind connect create lock nlmsg_read nlmsg_relay nlmsg_tty_audit setattr shutdown };
-allow rustdesk_t rustdesk_t:netlink_kobject_uevent_socket { append bind connect create lock setattr shutdown };
-allow rustdesk_t rustdesk_t:netlink_route_socket { append bind connect create lock nlmsg_read nlmsg_write setattr shutdown };
-allow rustdesk_t rustdesk_t:netlink_selinux_socket { append bind connect create lock setattr shutdown };
-allow rustdesk_t rustdesk_t:packet_socket { append bind connect create lock setattr shutdown };
-allow rustdesk_t rustdesk_t:peer recv;
-allow rustdesk_t rustdesk_t:process { fork getcap getsched setcap setexec setfscreate setkeycreate setsockcreate };
-allow rustdesk_t rustdesk_t:sem { associate create destroy getattr read setattr unix_read unix_write write };
-allow rustdesk_t rustdesk_t:service { disable enable reload start status stop };
-allow rustdesk_t rustdesk_t:shm { associate create destroy getattr lock read setattr unix_read unix_write write };
-allow rustdesk_t rustdesk_t:system { disable enable halt ipc_info module_load module_request reboot reload start status stop syslog_console syslog_mod syslog_read undefined };
-allow rustdesk_t rustdesk_t:unix_stream_socket { connectto recvfrom };
-allow rustdesk_t rustdesk_t:user_namespace create;
-allow rustdesk_t sblim_domain:dbus send_msg;
-allow rustdesk_t security_t:file map;
-allow rustdesk_t security_t:security { check_context compute_av compute_create compute_relabel compute_user load_policy };
-allow rustdesk_t selinux_config_t:file { ioctl lock open read };
-allow rustdesk_t selinux_config_t:lnk_file read;
-allow rustdesk_t selinux_login_config_t:file { ioctl lock open read };
-allow rustdesk_t selinux_login_config_t:lnk_file read;
-allow rustdesk_t semanage_store_t:file { ioctl lock open read };
-allow rustdesk_t semanage_store_t:lnk_file read;
-allow rustdesk_t session_dbusd_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t shell_exec_t:file entrypoint;
-allow rustdesk_t smbcontrol_t:dbus send_msg;
-allow rustdesk_t smokeping_cgi_script_t:dbus send_msg;
-allow rustdesk_t spc_t:dbus send_msg;
-allow rustdesk_t speech_dispatcher_t:dbus send_msg;
-allow rustdesk_t spoolfile:sock_file { create open setattr unlink };
-allow rustdesk_t sshd_exec_t:file ioctl;
-allow rustdesk_t sshd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t ssh_keysign_t:dbus send_msg;
-allow rustdesk_t sslh_t:dbus send_msg;
-allow rustdesk_t sssd_var_lib_t:sock_file { create setattr unlink };
-allow rustdesk_t staff_t:fd use;
-allow rustdesk_t stratisd_data_t:lnk_file read;
-allow rustdesk_t stunnel_exec_t:file ioctl;
-allow rustdesk_t stunnel_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t sulogin_exec_t:file ioctl;
-allow rustdesk_t sulogin_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t svc_start_exec_t:file ioctl;
-allow rustdesk_t svc_start_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t svirt_file_type:chr_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t svirt_file_type:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t svirt_file_type:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t svirt_file_type:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t svirt_file_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t svirt_sandbox_domain:process transition;
-allow rustdesk_t svirt_sandbox_domain:unix_dgram_socket sendto;
-allow rustdesk_t svirt_tcg_t:dbus send_msg;
-allow rustdesk_t svirt_t:dbus send_msg;
-allow rustdesk_t swat_exec_t:file { execute ioctl map open read };
-allow rustdesk_t swat_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t swat_t:process transition;
-allow rustdesk_t swat_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t sysctl_kernel_t:file mounton;
-allow rustdesk_t sysctl_type:dir { getattr ioctl lock mounton open read search };
-allow rustdesk_t sysctl_type:file { append getattr ioctl lock open read setattr write };
-allow rustdesk_t sysfs_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t sysfs_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t sysfs_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t sysfs_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t syslogd_t:netlink_audit_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_write read setattr setopt shutdown write };
-allow rustdesk_t syslogd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_bootchart_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t system_dbusd_t:dbus acquire_svc;
-allow rustdesk_t system_dbusd_var_run_t:sock_file { read watch };
-allow rustdesk_t systemd_coredump_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_gpt_generator_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_home_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_home_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_home_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_hostnamed_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_hwdb_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_importd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_initctl_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_journal_upload_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_localed_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_logger_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_logger_t:unix_stream_socket connectto;
-allow rustdesk_t systemd_logind_inhibit_var_run_t:dir mounton;
-allow rustdesk_t systemd_logind_inhibit_var_run_t:fifo_file write;
-allow rustdesk_t systemd_logind_sessions_t:dir mounton;
-allow rustdesk_t systemd_logind_sessions_t:fifo_file write;
-allow rustdesk_t systemd_logind_t:fd use;
-allow rustdesk_t systemd_logind_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_logind_t:system status;
-allow rustdesk_t systemd_logind_var_run_t:dir mounton;
-allow rustdesk_t systemd_logind_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t systemd_machined_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_modules_load_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_mount_directory:dir { create mounton };
-allow rustdesk_t systemd_networkd_exec_t:file map;
-allow rustdesk_t systemd_networkd_t:netlink_route_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_write read setattr setopt shutdown write };
-allow rustdesk_t systemd_networkd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_network_generator_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_notify_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_passwd_agent_exec_t:file { execute ioctl lock map open read };
-allow rustdesk_t systemd_passwd_agent_exec_t:file { ioctl lock };
-allow rustdesk_t systemd_passwd_agent_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_passwd_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t systemd_passwd_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t systemd_passwd_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t systemd_private_tmp_type:dir { remove_name rmdir write };
-allow rustdesk_t systemd_private_tmp_type:fifo_file unlink;
-allow rustdesk_t systemd_private_tmp_type:file unlink;
-allow rustdesk_t systemd_private_tmp_type:lnk_file unlink;
-allow rustdesk_t systemd_private_tmp_type:sock_file unlink;
-allow rustdesk_t systemd_pstore_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_resolved_exec_t:file map;
-allow rustdesk_t systemd_resolved_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_rfkill_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_rfkill_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_sleep_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_socket_proxyd_t:unix_stream_socket connectto;
-allow rustdesk_t systemd_sysctl_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_systemctl_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t systemd_timedated_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_timedated_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_timedated_var_lib_t:lnk_file read;
-allow rustdesk_t systemd_tmpfiles_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_unit_file_type:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_unit_file_type:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_unit_file_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_unit_file_type:service { disable enable reload start status stop };
-allow rustdesk_t systemd_userdbd_runtime_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_userdbd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemprocess:process { dyntransition siginh };
-allow rustdesk_t systemprocess:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t systemprocess:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t tangd_db_t:file { ioctl lock open read };
-allow rustdesk_t tangd_t:dbus send_msg;
-allow rustdesk_t targetclid_t:dbus send_msg;
-allow rustdesk_t tcpd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t tcpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t tcpd_t:process transition;
-allow rustdesk_t tcpd_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t tcpd_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t telnetd_exec_t:file ioctl;
-allow rustdesk_t telnetd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t tftpd_exec_t:file ioctl;
-allow rustdesk_t tftpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t thin_domain:dbus send_msg;
-allow rustdesk_t thumb_t:dbus send_msg;
-allow rustdesk_t timedatex_t:dbus send_msg;
-allow rustdesk_t tlp_t:dbus send_msg;
-allow rustdesk_t tmpfs_t:chr_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t tmpfs_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t tmpfs_t:file { append create execute execute_no_trans ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t tmpfs_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t tmpfs_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t tmpreaper_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t tmp_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t tmp_t:fifo_file unlink;
-allow rustdesk_t tmp_t:sock_file unlink;
-allow rustdesk_t tpm_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t tty_device_t:chr_file { append ioctl lock open read watch watch_reads write };
-allow rustdesk_t ttynode:chr_file { append ioctl lock read write };
-allow rustdesk_t udev_rules_t:dir { add_name remove_name write };
-allow rustdesk_t udev_rules_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t udev_t:netlink_kobject_uevent_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:fifo_file { append getattr ioctl lock open write };
-allow rustdesk_t unconfined_service_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t unconfined_service_t:process { siginh transition };
-allow rustdesk_t unconfined_service_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t unlabeled_t:file { ioctl lock open read };
-allow rustdesk_t unlabeled_t:lnk_file read;
-allow rustdesk_t updpwd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t updpwd_t:process transition;
-allow rustdesk_t urandom_device_t:chr_file { append write };
-allow rustdesk_t usbtty_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t user_devpts_t:chr_file { watch watch_reads };
-allow rustdesk_t userdomain:fifo_file { append getattr ioctl lock read write };
-allow rustdesk_t userdomain:unix_stream_socket { append bind connect connectto getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t userdomain:unix_stream_socket connectto;
-allow rustdesk_t user_home_dir_t:lnk_file read;
-allow rustdesk_t user_home_t:file unlink;
-allow rustdesk_t user_t:fd use;
-allow rustdesk_t user_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t user_tmp_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t user_tmp_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t user_tty_device_t:chr_file { open watch watch_reads };
-allow rustdesk_t usr_t:dir { add_name remove_name write };
-allow rustdesk_t uucpd_exec_t:file ioctl;
-allow rustdesk_t uucpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t uuidd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t uuidd_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t uuidd_var_run_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t uuidd_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t var_lib_nfs_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_lib_t:dir { add_name create remove_name setattr write };
-allow rustdesk_t var_lib_t:dir { create setattr };
-allow rustdesk_t var_lib_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_lib_t:lnk_file { create read write };
-allow rustdesk_t var_log_t:dir { add_name create remove_name setattr write };
-allow rustdesk_t var_log_t:dir { create setattr };
-allow rustdesk_t var_log_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_log_t:file { create link map open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_log_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t var_run_t:file { append execute execute_no_trans write };
-allow rustdesk_t var_run_t:lnk_file unlink;
-allow rustdesk_t var_spool_t:dir { add_name remove_name write };
-allow rustdesk_t var_t:dir { add_name create remove_name setattr write };
-allow rustdesk_t var_t:dir { create setattr };
-allow rustdesk_t var_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t virsh_t:dbus send_msg;
-allow rustdesk_t virtd_t:unix_stream_socket connectto;
-allow rustdesk_t virt_etc_rw_t:file { ioctl lock open read };
-allow rustdesk_t virt_etc_rw_t:lnk_file read;
-allow rustdesk_t virtio_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t vnstatd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t watchdog_device_t:chr_file { append ioctl lock open write };
-allow rustdesk_t watchdog_t:dbus send_msg;
-allow rustdesk_t wireguard_t:dbus send_msg;
-allow rustdesk_t wireless_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t wtmp_t:file { append ioctl lock open read write };
-allow rustdesk_t wtmp_t:file { open read write };
-allow rustdesk_t xdm_exec_t:file ioctl;
-allow rustdesk_t xdm_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t xdm_var_lib_t:file { ioctl lock open read };
-allow rustdesk_t xdm_var_lib_t:lnk_file read;
-allow rustdesk_t xenconsoled_t:dbus send_msg;
-allow rustdesk_t xend_t:dbus send_msg;
-allow rustdesk_t xguest_t:dbus send_msg;
-allow rustdesk_t xserver_port_t:tcp_socket name_connect;
-allow rustdesk_t xserver_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t xserver_t:unix_stream_socket connectto;
-
-
-```
-
-rustdesk.fc:
-
-```text
-
-/usr/bin/rustdesk -- gen_context(system_u:object_r:rustdesk_exec_t,s0)
-```
-
-rustdesk.if:
-
-```text
-
-# RustDesk
-```
-
-Makefile:
-
-```makefile
-
-TARGET?=rustdesk
-MODULES?=${TARGET:=.pp.bz2}
-SHAREDIR?=/usr/share
-SELINUXTYPE?=targeted
-
-all: ${TARGET:=.pp.bz2}
-
-%.pp.bz2: %.pp
- @echo Compressing $^ -\> $@
- bzip2 -9 $^
-
-%.pp: %.te
- make -f ${SHAREDIR}/selinux/devel/Makefile $@
-
-clean:
- rm -f *~ *.tc *.pp *.pp.bz2
- rm -rf tmp *.tar.gz
-
-man: install-policy
- sepolicy manpage --path . --domain ${TARGET}_t
-
-install-policy: all
- semodule -i ${TARGET}.pp.bz2
-
-install: man
- install -D -m 644 ${TARGET}.pp.bz2 ${DESTDIR}${SHAREDIR}/selinux/packages/${SELINUXTYPE}/${TARGET}.pp.bz2
- install -D -m 644 ${TARGET}_selinux.8 ${DESTDIR}${SHAREDIR}/man/man8/
-
-```
-
-### Habilitar directamente
-
-Comprueba el contexto de seguridad de RustDesk antes de modificar:
-
-```sh
-$ ls -lZ /usr/lib/rustdesk/rustdesk
--rwxr-xr-x. 1 root root system_u:object_r:lib_t:s0 25456 Oct 8 19:58 /usr/lib/rustdesk/rustdesk
-$ ps -eZ | grep rustdesk
-system_u:system_r:init_t:s0 80439 ? 00:00:02 rustdesk
-```
-
-Ejecuta:
-
-```sh
-
-$ cd rustdesk-selinux-1.0
-$ make
-$ sudo make install-policy
-$ semodule -l | grep rustdesk
-rustdesk
-$ sudo chcon -t rustdesk_exec_t /usr/bin/rustdesk
-$ sudo systemctl restart rustdesk
-
-```
-
-Comprueba el contexto de seguridad de nuevo:
-
-```sh
-$ ls -lZ /usr/lib/rustdesk/rustdesk
--rwxr-xr-x. 1 root root system_u:object_r:rustdesk_exec_t:s0 25456 Oct 8 19:58 /usr/lib/rustdesk/rustdesk
-$ ps -eZ | grep rustdesk
-system_u:system_r:rustdesk_t:s0 110565 ? 00:00:00 rustdesk
-```
-
-## Habilita mediante instalación rpm
-### Enable through rpm installation
-
-Crea un nuevo archivo de spec `rustdesk-selinux.spec`:
-
-```sh
-
-%global modulename rustdesk
-%global selinuxtype targeted
-
-Name: rustdesk-selinux
-Version: 1.0
-Release: 1%{?dist}
-License: AGPL-3.0
-Summary: RustDesk SELinux policy
-BuildArch: noarch
-Requires: selinux-policy-%{selinuxtype}
-Requires(post): selinux-policy-%{selinuxtype}
-BuildRequires: selinux-policy-devel
-
-Source0: %{name}-%{version}.tar.gz
-
-%description
-Custom SELinux policy module
-
-%prep
-%setup -q
-
-%build
-make
-
-
-%install
-install -D -m 0644 %{modulename}.pp.bz2 %{buildroot}%{_datadir}/selinux/packages/%{selinuxtype}/%{modulename}.pp.bz2
-install -D -p -m 0644 %{modulename}.if %{buildroot}%{_datadir}/selinux/devel/include/distributed/%{modulename}.if
-
-
-# Los contextos de SELinux son son guardados, de esta manera
-# los archivos modificados pueden ser renombrados después de
-# la instalación del modulo de políticas
-
-%pre
-%selinux_relabel_pre -s %{selinuxtype}
-
-%post
-semodule -d %{modulename} &> /dev/null || true
-%selinux_modules_install -s %{selinuxtype} %{_datadir}/selinux/packages/%{selinuxtype}/%{modulename}.pp.bz2
-%selinux_relabel_post -s %{selinuxtype}
-chcon -t rustdesk_exec_t /usr/bin/rustdesk
-
-if [ "$1" -le "1" ]; then # Primera instalación
- # daemon necesita ser reiniciada para que las etiquetas personalizadas sean aplicadas
- %systemd_postun_with_restart %{modulename}.service
-fi
-
-%postun
-if [ $1 -eq 0 ]; then
- %selinux_modules_uninstall -s %{selinuxtype} %{modulename}
- semodule -e %{modulename} &> /dev/null || true
- %selinux_relabel_post -s %{selinuxtype}
-fi
-
-%posttrans
-%selinux_relabel_post -s %{selinuxtype}
-
-%files
-%{_datadir}/selinux/packages/%{selinuxtype}/%{modulename}.pp.*
-%{_datadir}/selinux/devel/include/distributed/%{modulename}.if
-%ghost %verify(not md5 size mode mtime) %{_sharedstatedir}/selinux/%{selinuxtype}/active/modules/200/%{modulename}
-
-%changelog
-* Mon Oct 16 2023 test - 0.1.0-1
-- First Build
-
-
-```
-
-Run:
-
-```sh
-
-$ sudo dnf install rpm-build
-$ tar -zcf rustdesk-selinux-1.0.tar.gz rustdesk-selinux-1.0
-$ mkdir -p ~/rpmbuild/SOURCES && mv rustdesk-selinux-1.0.tar.gz ~/rpmbuild/SOURCES/
-$ rpmbuild -ba rustdesk-selinux.spec
-
-```
-
-Después de que el empaquetado es completado, ejecuta la instalación via rpm
-
-# Resolución De Problemas
-
-## Añadir políticas de forma iterativa
-
-```sh
-$ cd /tmp
-$ grep rustdesk_t /var/log/audit/audit.log | audit2allow -a -M rustdesk_tmp
-$ cd
-$ # merge rustdesk_tmp.te a rustdesk.te
-$ make clean && make && sudo make install-policy
-```
-
-# Referencias
-
-1. [SELinux/tutoriales (ingles)](https://wiki.gentoo.org/wiki/SELinux/Tutorials)
-1. [Instalación del modulo de políticas de SELinux (ingles)](https://fedoraproject.org/wiki/SELinux/IndependentPolicy#SELinux_Policy_module_installation)
-1. [Como crear un paquete de políticas personalizadas para rpm (ingles)](https://lukas-vrabec.com/index.php/2015/07/07/how-to-create-selinux-custom-policy-rpm-package/)
diff --git a/content/client/linux/SELinux/_index.fr.md b/content/client/linux/SELinux/_index.fr.md
deleted file mode 100644
index 3fcb7ae..0000000
--- a/content/client/linux/SELinux/_index.fr.md
+++ /dev/null
@@ -1,178 +0,0 @@
----
-title: SELinux
-weight: 100
----
-
-Certaines distributions (comme Fedora) activent SELinux par défaut, ce qui empêchera le service RustDesk de démarrer et de fonctionner normalement.
-
-Vous pouvez exécuter `sestatus` dans le terminal pour vérifier si SELinux est activé.
-
-Selon qu'il soit activé ou non, vous pouvez voir deux sorties différentes comme suit :
-
-```sh
-# Activé
-SELinux status: enabled
-...
-
-# Désactivé
-SELinux status: disabled
-...
-```
-
-## Ajouter des politiques SELinux
-
-Pour une introduction à SELinux, veuillez vous référer à [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials).
-
-Ici, nous prenons Fedora 38 comme exemple pour présenter comment ajouter des politiques SELinux.
-
-```sh
-sudo dnf install selinux-policy-devel make
-```
-
-L'ajout de politiques SELinux nécessite de déterminer le type de service, qui se trouve dans le contexte de sécurité du processus.
-
-```sh
-$ ps -eZ | grep rustdesk
-system_u:system_r:init_t:s0 80439 ? 00:00:02 rustdesk
-```
-
-`system_u:system_r:init_t:s0` est le contexte de sécurité du processus RustDesk, où le troisième champ `init_t` est le type du processus.
-
-Il existe deux façons d'écrire les règles de type SELinux :
-
-1. Ajouter des règles au `init_t` par défaut.
-2. Ajouter un nouveau type `rustdesk_t` et ajouter des règles.
-
-La première méthode a des modifications relativement mineures, mais parce que le `init_t` par défaut est modifié, cela équivaut à ajouter une autorisation à d'autres services utilisant le type `init_t`. **Non recommandé pour l'utilisation.**
-
-La deuxième méthode consiste à ajouter des règles à partir de zéro. Il y aura de nombreuses règles qui doivent être ajoutées, et différents systèmes peuvent avoir des différences. Il peut être nécessaire de faire quelques ajustements lors de l'utilisation réelle.
-
-### Utiliser le type par défaut
-
-Le type par défaut du service RustDesk est `init_t`, qui est déterminé par [les règles d'héritage de contexte de SELinux](https://wiki.gentoo.org/wiki/SELinux/Tutorials/How_does_a_process_get_into_a_certain_context).
-
-**Attention** : Modifier le type par défaut signifie que les politiques d'autres services peuvent également changer. Veuillez utiliser cette méthode avec prudence !
-
-Modifiez le fichier de règles `rustdesk.te` :
-
-```text
-module rustdesk 1.0;
-
-require {
- type event_device_t;
- type xserver_t;
- type xserver_port_t;
- type sudo_exec_t;
- type init_t;
- type ephemeral_port_t;
- type user_tmp_t;
- type user_fonts_cache_t;
- type pulseaudio_home_t;
- type session_dbusd_tmp_t;
- type unconfined_dbusd_t;
- class process execmem;
- class file { open read create write execute execute_no_trans map setattr lock link unlink };
- class unix_stream_socket connectto;
- class tcp_socket name_connect;
- class dir { add_name remove_name };
- class sock_file write;
- class chr_file { open read write } ;
-}
-
-#============= init_t ==============
-allow init_t xserver_t:unix_stream_socket connectto;
-allow init_t sudo_exec_t:file { open read execute execute_no_trans };
-allow init_t user_tmp_t:file { open write setattr };
-allow init_t self:process execmem;
-allow init_t user_fonts_cache_t:dir { add_name remove_name };
-allow init_t user_fonts_cache_t:file { read write create open link lock unlink };
-allow init_t xserver_port_t:tcp_socket name_connect;
-allow init_t pulseaudio_home_t:file { read write open lock };
-allow init_t session_dbusd_tmp_t:sock_file write;
-allow init_t unconfined_dbusd_t:unix_stream_socket connectto;
-
-#!!!! This AVC can be allowed using the boolean 'nis_enabled'
-allow init_t ephemeral_port_t:tcp_socket name_connect;
-
-#!!!! This AVC can be allowed using the boolean 'domain_can_mmap_files'
-allow init_t sudo_exec_t:file map;
-
-#============= init_t Wayland ==============
-allow init_t event_device_t:chr_file { open read write };
-
-#!!!! This AVC can be allowed using the boolean 'domain_can_mmap_files'
-allow init_t user_tmp_t:file map;
-
-```
-
-Exécutez :
-
-```sh
-$ checkmodule -M -m -o rustdesk.mod rustdesk.te && semodule_package -o rustdesk.pp -m rustdesk.mod && sudo semodule -i rustdesk.pp
-$ sudo semodule -l | grep rustdesk
-```
-
-### Créer un type `rustdesk_t`
-
-1. Créer un nouveau répertoire : `mkdir rustdesk-selinux-1.0`.
-2. Créer des fichiers de politique SELinux : `touch Makefile rustdesk.te rustdesk.fc rustdesk.if`.
-
-```text
-.
-├── Makefile
-├── rustdesk.fc
-├── rustdesk.if
-└── rustdesk.te
-```
-
-`rustdesk.te` est le fichier de politique principal.
-Dans cet exemple, ce fichier provient principalement de 3 parties :
-
-1. [`init.te`](https://github.com/fedora-selinux/selinux-policy/blob/rawhide/policy/modules/system/init.te) dans le dépôt selinux-policy de GitHub.
-2. Journal d'audit, `grep rustdesk /var/log/audit/audit.log | audit2allow -a -M test`.
-3. La politique `init_t` du système de test, `sesearch -A | grep 'allow init_t ' | sed 's/allow init_t /allow rustdesk_t /g'`.
-
-Certaines politiques sont dupliquées et certaines sont redondantes, mais c'est correct puisque cela fonctionne sur `rustdesk_t`.
-
-**En raison de la complexité des fichiers de politique SELinux et de leur contenu technique détaillé, le contenu de configuration technique complet est omis ici pour des raisons de concision. Veuillez vous référer à la version anglaise pour la configuration complète.**
-
-## Génération automatique de politique SELinux (sepolicy)
-
-```sh
-$ # installer les dépendances
-$ sudo dnf install -y rpm rpm-build binutils
-$ # générer la politique
-$ sepolicy generate --init /usr/lib/rustdesk/rustdesk
-$ tree
-.
-├── rustdesk.fc
-├── rustdesk.if
-├── rustdesk_selinux.spec
-├── rustdesk.sh
-└── rustdesk.te
-$ # Modifier le rustdesk.te
-$
-$
-$ # générer le package rpm rustdesk_selinux-1.0-1.fc38.src.rpm
-$ sudo ./rustdesk.sh
-$ # installer le package
-$ sudo dnf install -y rustdesk_selinux-1.0-1.fc38.src.rpm
-$ # redémarrer le service
-$ sudo systemctl restart rustdesk
-```
-
-### Ajouter des politiques de manière itérative
-
-```sh
-$ cd /tmp
-$ grep rustdesk_t /var/log/audit/audit.log | audit2allow -a -M rustdesk_tmp
-$ cd
-$ # fusionner rustdesk_tmp.te dans rustdesk.te
-$ make clean && make && sudo make install-policy
-```
-
-## Références
-
-- [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials)
-- [SELinux Policy module installation](https://fedoraproject.org/wiki/SELinux/IndependentPolicy#SELinux_Policy_module_installation)
-- [How to create SELinux custom policy rpm package](https://lukas-vrabec.com/index.php/2015/07/07/how-to-create-selinux-custom-policy-rpm-package/)
\ No newline at end of file
diff --git a/content/client/linux/SELinux/_index.it.md b/content/client/linux/SELinux/_index.it.md
deleted file mode 100644
index 9af6a87..0000000
--- a/content/client/linux/SELinux/_index.it.md
+++ /dev/null
@@ -1,178 +0,0 @@
----
-title: SELinux
-weight: 100
----
-
-Alcune distribuzioni (come Fedora) abilitano SELinux per impostazione predefinita, il che causerà il fallimento dell'avvio e dell'esecuzione normale del servizio RustDesk.
-
-Puoi eseguire `sestatus` nel terminale per verificare se SELinux è abilitato.
-
-A seconda che sia abilitato o meno, puoi vedere due output diversi come segue:
-
-```sh
-# Abilitato
-SELinux status: enabled
-...
-
-# Disabilitato
-SELinux status: disabled
-...
-```
-
-## Aggiungere Politiche SELinux
-
-Per un'introduzione a SELinux, si prega di fare riferimento a [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials).
-
-Qui prendiamo Fedora 38 come esempio per introdurre come aggiungere politiche SELinux.
-
-```sh
-sudo dnf install selinux-policy-devel make
-```
-
-L'aggiunta di politiche SELinux richiede di determinare il tipo di servizio, che si trova nel contesto di sicurezza del processo.
-
-```sh
-$ ps -eZ | grep rustdesk
-system_u:system_r:init_t:s0 80439 ? 00:00:02 rustdesk
-```
-
-`system_u:system_r:init_t:s0` è il contesto di sicurezza del processo RustDesk, dove il terzo campo `init_t` è il tipo del processo.
-
-Ci sono due modi per scrivere le regole di tipo SELinux:
-
-1. Aggiungere regole al `init_t` predefinito.
-2. Aggiungere un nuovo tipo `rustdesk_t` e aggiungere regole.
-
-Il primo metodo ha modifiche relativamente minori, ma poiché il `init_t` predefinito viene modificato, è equivalente ad aggiungere autorizzazione ad altri servizi che utilizzano il tipo `init_t`. **Non raccomandato per l'uso.**
-
-Il secondo metodo è aggiungere regole da zero. Ci saranno molte regole che devono essere aggiunte, e sistemi diversi possono avere differenze. Potrebbe essere necessario fare alcuni aggiustamenti durante l'uso effettivo.
-
-### Usare il Tipo Predefinito
-
-Il tipo predefinito del servizio RustDesk è `init_t`, che è determinato dalle [regole di ereditarietà del contesto di SELinux](https://wiki.gentoo.org/wiki/SELinux/Tutorials/How_does_a_process_get_into_a_certain_context).
-
-**Attenzione**: Modificare il tipo predefinito significa che anche le politiche di altri servizi potrebbero cambiare. Si prega di usare questo metodo con cautela!
-
-Modifica il file delle regole `rustdesk.te`:
-
-```text
-module rustdesk 1.0;
-
-require {
- type event_device_t;
- type xserver_t;
- type xserver_port_t;
- type sudo_exec_t;
- type init_t;
- type ephemeral_port_t;
- type user_tmp_t;
- type user_fonts_cache_t;
- type pulseaudio_home_t;
- type session_dbusd_tmp_t;
- type unconfined_dbusd_t;
- class process execmem;
- class file { open read create write execute execute_no_trans map setattr lock link unlink };
- class unix_stream_socket connectto;
- class tcp_socket name_connect;
- class dir { add_name remove_name };
- class sock_file write;
- class chr_file { open read write } ;
-}
-
-#============= init_t ==============
-allow init_t xserver_t:unix_stream_socket connectto;
-allow init_t sudo_exec_t:file { open read execute execute_no_trans };
-allow init_t user_tmp_t:file { open write setattr };
-allow init_t self:process execmem;
-allow init_t user_fonts_cache_t:dir { add_name remove_name };
-allow init_t user_fonts_cache_t:file { read write create open link lock unlink };
-allow init_t xserver_port_t:tcp_socket name_connect;
-allow init_t pulseaudio_home_t:file { read write open lock };
-allow init_t session_dbusd_tmp_t:sock_file write;
-allow init_t unconfined_dbusd_t:unix_stream_socket connectto;
-
-#!!!! This AVC can be allowed using the boolean 'nis_enabled'
-allow init_t ephemeral_port_t:tcp_socket name_connect;
-
-#!!!! This AVC can be allowed using the boolean 'domain_can_mmap_files'
-allow init_t sudo_exec_t:file map;
-
-#============= init_t Wayland ==============
-allow init_t event_device_t:chr_file { open read write };
-
-#!!!! This AVC can be allowed using the boolean 'domain_can_mmap_files'
-allow init_t user_tmp_t:file map;
-
-```
-
-Esegui:
-
-```sh
-$ checkmodule -M -m -o rustdesk.mod rustdesk.te && semodule_package -o rustdesk.pp -m rustdesk.mod && sudo semodule -i rustdesk.pp
-$ sudo semodule -l | grep rustdesk
-```
-
-### Creare un tipo `rustdesk_t`
-
-1. Creare una nuova directory: `mkdir rustdesk-selinux-1.0`.
-2. Creare file di politica SELinux: `touch Makefile rustdesk.te rustdesk.fc rustdesk.if`.
-
-```text
-.
-├── Makefile
-├── rustdesk.fc
-├── rustdesk.if
-└── rustdesk.te
-```
-
-`rustdesk.te` è il file di politica principale.
-In questo esempio, questo file proviene principalmente da 3 parti:
-
-1. [`init.te`](https://github.com/fedora-selinux/selinux-policy/blob/rawhide/policy/modules/system/init.te) nel repository selinux-policy di GitHub.
-2. Log di audit, `grep rustdesk /var/log/audit/audit.log | audit2allow -a -M test`.
-3. La politica `init_t` del sistema di test, `sesearch -A | grep 'allow init_t ' | sed 's/allow init_t /allow rustdesk_t /g'`.
-
-Alcune politiche sono duplicate e alcune sono ridondanti, ma va bene poiché funziona su `rustdesk_t`.
-
-**A causa della complessità dei file di politica SELinux e del loro contenuto tecnico dettagliato, il contenuto di configurazione tecnica completo è omesso qui per brevità. Si prega di fare riferimento alla versione inglese per la configurazione completa.**
-
-## Generazione Automatica di Politiche SELinux (sepolicy)
-
-```sh
-$ # installare dipendenze
-$ sudo dnf install -y rpm rpm-build binutils
-$ # generare politica
-$ sepolicy generate --init /usr/lib/rustdesk/rustdesk
-$ tree
-.
-├── rustdesk.fc
-├── rustdesk.if
-├── rustdesk_selinux.spec
-├── rustdesk.sh
-└── rustdesk.te
-$ # Modificare il rustdesk.te
-$
-$
-$ # generare pacchetto rpm rustdesk_selinux-1.0-1.fc38.src.rpm
-$ sudo ./rustdesk.sh
-$ # installare pacchetto
-$ sudo dnf install -y rustdesk_selinux-1.0-1.fc38.src.rpm
-$ # riavviare il servizio
-$ sudo systemctl restart rustdesk
-```
-
-### Aggiungere Politiche Iterativamente
-
-```sh
-$ cd /tmp
-$ grep rustdesk_t /var/log/audit/audit.log | audit2allow -a -M rustdesk_tmp
-$ cd
-$ # unire rustdesk_tmp.te in rustdesk.te
-$ make clean && make && sudo make install-policy
-```
-
-## Riferimenti
-
-- [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials)
-- [SELinux Policy module installation](https://fedoraproject.org/wiki/SELinux/IndependentPolicy#SELinux_Policy_module_installation)
-- [How to create SELinux custom policy rpm package](https://lukas-vrabec.com/index.php/2015/07/07/how-to-create-selinux-custom-policy-rpm-package/)
\ No newline at end of file
diff --git a/content/client/linux/SELinux/_index.ja.md b/content/client/linux/SELinux/_index.ja.md
deleted file mode 100644
index d6e4675..0000000
--- a/content/client/linux/SELinux/_index.ja.md
+++ /dev/null
@@ -1,178 +0,0 @@
----
-title: SELinux
-weight: 100
----
-
-一部のディストリビューション(Fedoraなど)では、SELinuxがデフォルトで有効になっており、RustDeskサービスが正常に開始・実行できなくなります。
-
-ターミナルで `sestatus` を実行して、SELinuxが有効になっているかどうかを確認できます。
-
-有効かどうかによって、以下のような2つの異なる出力が表示されます:
-
-```sh
-# 有効
-SELinux status: enabled
-...
-
-# 無効
-SELinux status: disabled
-...
-```
-
-## SELinuxポリシーの追加
-
-SELinuxの紹介については、[SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials)を参照してください。
-
-ここでは、Fedora 38を例にSELinuxポリシーを追加する方法を紹介します。
-
-```sh
-sudo dnf install selinux-policy-devel make
-```
-
-SELinuxポリシーを追加するには、プロセスのセキュリティコンテキストにあるサービスの種類を決定する必要があります。
-
-```sh
-$ ps -eZ | grep rustdesk
-system_u:system_r:init_t:s0 80439 ? 00:00:02 rustdesk
-```
-
-`system_u:system_r:init_t:s0` は RustDeskプロセスのセキュリティコンテキストで、3番目のフィールド `init_t` がプロセスの種類です。
-
-SELinux型ルールを記述する方法は2つあります:
-
-1. デフォルトの `init_t` にルールを追加する。
-2. 新しい型 `rustdesk_t` を追加してルールを追加する。
-
-最初の方法は比較的小さな変更ですが、デフォルトの `init_t` が変更されるため、`init_t` 型を使用する他のサービスに認可を追加することと同等です。**使用は推奨されません。**
-
-2番目の方法は、ゼロからルールを追加することです。追加する必要があるルールが多く、異なるシステムでは違いがある可能性があります。実際の使用中にいくつかの調整が必要になる場合があります。
-
-### デフォルト型の使用
-
-RustDeskサービスのデフォルト型は `init_t` で、これは[SELinuxのコンテキスト継承ルール](https://wiki.gentoo.org/wiki/SELinux/Tutorials/How_does_a_process_get_into_a_certain_context)によって決定されます。
-
-**注意**:デフォルト型を変更すると、他のサービスのポリシーも変更される可能性があります。この方法は慎重に使用してください!
-
-ルールファイル `rustdesk.te` を編集します:
-
-```text
-module rustdesk 1.0;
-
-require {
- type event_device_t;
- type xserver_t;
- type xserver_port_t;
- type sudo_exec_t;
- type init_t;
- type ephemeral_port_t;
- type user_tmp_t;
- type user_fonts_cache_t;
- type pulseaudio_home_t;
- type session_dbusd_tmp_t;
- type unconfined_dbusd_t;
- class process execmem;
- class file { open read create write execute execute_no_trans map setattr lock link unlink };
- class unix_stream_socket connectto;
- class tcp_socket name_connect;
- class dir { add_name remove_name };
- class sock_file write;
- class chr_file { open read write } ;
-}
-
-#============= init_t ==============
-allow init_t xserver_t:unix_stream_socket connectto;
-allow init_t sudo_exec_t:file { open read execute execute_no_trans };
-allow init_t user_tmp_t:file { open write setattr };
-allow init_t self:process execmem;
-allow init_t user_fonts_cache_t:dir { add_name remove_name };
-allow init_t user_fonts_cache_t:file { read write create open link lock unlink };
-allow init_t xserver_port_t:tcp_socket name_connect;
-allow init_t pulseaudio_home_t:file { read write open lock };
-allow init_t session_dbusd_tmp_t:sock_file write;
-allow init_t unconfined_dbusd_t:unix_stream_socket connectto;
-
-#!!!! This AVC can be allowed using the boolean 'nis_enabled'
-allow init_t ephemeral_port_t:tcp_socket name_connect;
-
-#!!!! This AVC can be allowed using the boolean 'domain_can_mmap_files'
-allow init_t sudo_exec_t:file map;
-
-#============= init_t Wayland ==============
-allow init_t event_device_t:chr_file { open read write };
-
-#!!!! This AVC can be allowed using the boolean 'domain_can_mmap_files'
-allow init_t user_tmp_t:file map;
-
-```
-
-実行:
-
-```sh
-$ checkmodule -M -m -o rustdesk.mod rustdesk.te && semodule_package -o rustdesk.pp -m rustdesk.mod && sudo semodule -i rustdesk.pp
-$ sudo semodule -l | grep rustdesk
-```
-
-### 型 `rustdesk_t` の作成
-
-1. 新しいディレクトリを作成:`mkdir rustdesk-selinux-1.0`。
-2. SELinuxポリシーファイルを作成:`touch Makefile rustdesk.te rustdesk.fc rustdesk.if`。
-
-```text
-.
-├── Makefile
-├── rustdesk.fc
-├── rustdesk.if
-└── rustdesk.te
-```
-
-`rustdesk.te` はメインのポリシーファイルです。
-この例では、このファイルは主に3つの部分から構成されています:
-
-1. GitHubのselinux-policyリポジトリの[`init.te`](https://github.com/fedora-selinux/selinux-policy/blob/rawhide/policy/modules/system/init.te)。
-2. 監査ログ、`grep rustdesk /var/log/audit/audit.log | audit2allow -a -M test`。
-3. テストシステムの `init_t` ポリシー、`sesearch -A | grep 'allow init_t ' | sed 's/allow init_t /allow rustdesk_t /g'`。
-
-一部のポリシーは重複しており、一部は冗長ですが、`rustdesk_t` で動作するため問題ありません。
-
-**SELinuxポリシーファイルの複雑さと詳細な技術的内容のため、簡潔性のため完全な技術設定内容はここでは省略されています。完全な設定については英語版を参照してください。**
-
-## SELinuxポリシーの自動生成(sepolicy)
-
-```sh
-$ # 依存関係をインストール
-$ sudo dnf install -y rpm rpm-build binutils
-$ # ポリシーを生成
-$ sepolicy generate --init /usr/lib/rustdesk/rustdesk
-$ tree
-.
-├── rustdesk.fc
-├── rustdesk.if
-├── rustdesk_selinux.spec
-├── rustdesk.sh
-└── rustdesk.te
-$ # rustdesk.teを編集
-$
-$
-$ # rpmパッケージrustdesk_selinux-1.0-1.fc38.src.rpmを生成
-$ sudo ./rustdesk.sh
-$ # パッケージをインストール
-$ sudo dnf install -y rustdesk_selinux-1.0-1.fc38.src.rpm
-$ # サービスを再起動
-$ sudo systemctl restart rustdesk
-```
-
-### 反復的なポリシーの追加
-
-```sh
-$ cd /tmp
-$ grep rustdesk_t /var/log/audit/audit.log | audit2allow -a -M rustdesk_tmp
-$ cd
-$ # rustdesk_tmp.teをrustdesk.teにマージ
-$ make clean && make && sudo make install-policy
-```
-
-## 参考文献
-
-- [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials)
-- [SELinux Policy module installation](https://fedoraproject.org/wiki/SELinux/IndependentPolicy#SELinux_Policy_module_installation)
-- [How to create SELinux custom policy rpm package](https://lukas-vrabec.com/index.php/2015/07/07/how-to-create-selinux-custom-policy-rpm-package/)
\ No newline at end of file
diff --git a/content/client/linux/SELinux/_index.pt.md b/content/client/linux/SELinux/_index.pt.md
deleted file mode 100644
index 9ceb28f..0000000
--- a/content/client/linux/SELinux/_index.pt.md
+++ /dev/null
@@ -1,178 +0,0 @@
----
-title: SELinux
-weight: 100
----
-
-Algumas distribuições (como Fedora) habilitam SELinux por padrão, o que fará com que o serviço RustDesk falhe ao iniciar e executar normalmente.
-
-Você pode executar `sestatus` no terminal para verificar se o SELinux está habilitado.
-
-Dependendo se está habilitado ou não, você pode ver duas saídas diferentes como a seguir:
-
-```sh
-# Habilitado
-SELinux status: enabled
-...
-
-# Desabilitado
-SELinux status: disabled
-...
-```
-
-## Adicionar Políticas SELinux
-
-Para uma introdução ao SELinux, consulte [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials).
-
-Aqui usamos o Fedora 38 como exemplo para introduzir como adicionar políticas SELinux.
-
-```sh
-sudo dnf install selinux-policy-devel make
-```
-
-Adicionar políticas SELinux requer determinar o tipo de serviço, que está no contexto de segurança do processo.
-
-```sh
-$ ps -eZ | grep rustdesk
-system_u:system_r:init_t:s0 80439 ? 00:00:02 rustdesk
-```
-
-`system_u:system_r:init_t:s0` é o contexto de segurança do processo RustDesk, onde o terceiro campo `init_t` é o tipo do processo.
-
-Existem duas maneiras de escrever regras de tipo SELinux:
-
-1. Adicionar regras ao `init_t` padrão.
-2. Adicionar um novo tipo `rustdesk_t` e adicionar regras.
-
-O primeiro método tem modificações relativamente menores, mas porque o `init_t` padrão é alterado, é equivalente a adicionar autorização a outros serviços usando o tipo `init_t`. **Não recomendado para uso.**
-
-O segundo método é adicionar regras do zero. Haverá muitas regras que precisam ser adicionadas, e diferentes sistemas podem ter diferenças. Pode ser necessário fazer alguns ajustes durante o uso real.
-
-### Usar o Tipo Padrão
-
-O tipo padrão do serviço RustDesk é `init_t`, que é determinado pelas [regras de herança de contexto do SELinux](https://wiki.gentoo.org/wiki/SELinux/Tutorials/How_does_a_process_get_into_a_certain_context).
-
-**Cuidado**: Modificar o tipo padrão significa que as políticas de outros serviços também podem mudar. Use este método com cuidado!
-
-Edite o arquivo de regras `rustdesk.te`:
-
-```text
-module rustdesk 1.0;
-
-require {
- type event_device_t;
- type xserver_t;
- type xserver_port_t;
- type sudo_exec_t;
- type init_t;
- type ephemeral_port_t;
- type user_tmp_t;
- type user_fonts_cache_t;
- type pulseaudio_home_t;
- type session_dbusd_tmp_t;
- type unconfined_dbusd_t;
- class process execmem;
- class file { open read create write execute execute_no_trans map setattr lock link unlink };
- class unix_stream_socket connectto;
- class tcp_socket name_connect;
- class dir { add_name remove_name };
- class sock_file write;
- class chr_file { open read write } ;
-}
-
-#============= init_t ==============
-allow init_t xserver_t:unix_stream_socket connectto;
-allow init_t sudo_exec_t:file { open read execute execute_no_trans };
-allow init_t user_tmp_t:file { open write setattr };
-allow init_t self:process execmem;
-allow init_t user_fonts_cache_t:dir { add_name remove_name };
-allow init_t user_fonts_cache_t:file { read write create open link lock unlink };
-allow init_t xserver_port_t:tcp_socket name_connect;
-allow init_t pulseaudio_home_t:file { read write open lock };
-allow init_t session_dbusd_tmp_t:sock_file write;
-allow init_t unconfined_dbusd_t:unix_stream_socket connectto;
-
-#!!!! This AVC can be allowed using the boolean 'nis_enabled'
-allow init_t ephemeral_port_t:tcp_socket name_connect;
-
-#!!!! This AVC can be allowed using the boolean 'domain_can_mmap_files'
-allow init_t sudo_exec_t:file map;
-
-#============= init_t Wayland ==============
-allow init_t event_device_t:chr_file { open read write };
-
-#!!!! This AVC can be allowed using the boolean 'domain_can_mmap_files'
-allow init_t user_tmp_t:file map;
-
-```
-
-Execute:
-
-```sh
-$ checkmodule -M -m -o rustdesk.mod rustdesk.te && semodule_package -o rustdesk.pp -m rustdesk.mod && sudo semodule -i rustdesk.pp
-$ sudo semodule -l | grep rustdesk
-```
-
-### Criar um tipo `rustdesk_t`
-
-1. Criar um novo diretório: `mkdir rustdesk-selinux-1.0`.
-2. Criar arquivos de política SELinux: `touch Makefile rustdesk.te rustdesk.fc rustdesk.if`.
-
-```text
-.
-├── Makefile
-├── rustdesk.fc
-├── rustdesk.if
-└── rustdesk.te
-```
-
-`rustdesk.te` é o arquivo de política principal.
-Neste exemplo, este arquivo vem principalmente de 3 partes:
-
-1. [`init.te`](https://github.com/fedora-selinux/selinux-policy/blob/rawhide/policy/modules/system/init.te) no repositório selinux-policy do GitHub.
-2. Log de auditoria, `grep rustdesk /var/log/audit/audit.log | audit2allow -a -M test`.
-3. A política `init_t` do sistema de teste, `sesearch -A | grep 'allow init_t ' | sed 's/allow init_t /allow rustdesk_t /g'`.
-
-Algumas políticas são duplicadas e algumas são redundantes, mas isso é ok, pois funciona no `rustdesk_t`.
-
-**Devido à complexidade dos arquivos de política SELinux e seu conteúdo técnico detalhado, o conteúdo de configuração técnica completa é omitido aqui para brevidade. Consulte a versão em inglês para a configuração completa.**
-
-## Geração Automática de Política SELinux (sepolicy)
-
-```sh
-$ # instalar dependências
-$ sudo dnf install -y rpm rpm-build binutils
-$ # gerar política
-$ sepolicy generate --init /usr/lib/rustdesk/rustdesk
-$ tree
-.
-├── rustdesk.fc
-├── rustdesk.if
-├── rustdesk_selinux.spec
-├── rustdesk.sh
-└── rustdesk.te
-$ # Editar o rustdesk.te
-$
-$
-$ # gerar pacote rpm rustdesk_selinux-1.0-1.fc38.src.rpm
-$ sudo ./rustdesk.sh
-$ # instalar pacote
-$ sudo dnf install -y rustdesk_selinux-1.0-1.fc38.src.rpm
-$ # reiniciar o serviço
-$ sudo systemctl restart rustdesk
-```
-
-### Adicionar Políticas Iterativamente
-
-```sh
-$ cd /tmp
-$ grep rustdesk_t /var/log/audit/audit.log | audit2allow -a -M rustdesk_tmp
-$ cd
-$ # mesclar rustdesk_tmp.te no rustdesk.te
-$ make clean && make && sudo make install-policy
-```
-
-## Referências
-
-- [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials)
-- [SELinux Policy module installation](https://fedoraproject.org/wiki/SELinux/IndependentPolicy#SELinux_Policy_module_installation)
-- [How to create SELinux custom policy rpm package](https://lukas-vrabec.com/index.php/2015/07/07/how-to-create-selinux-custom-policy-rpm-package/)
\ No newline at end of file
diff --git a/content/client/linux/SELinux/_index.zh-cn.md b/content/client/linux/SELinux/_index.zh-cn.md
deleted file mode 100644
index 88b3ed0..0000000
--- a/content/client/linux/SELinux/_index.zh-cn.md
+++ /dev/null
@@ -1,1837 +0,0 @@
----
-title: SELinux
-weight: 100
----
-
-
-一些发行版(如 Fedora)默认开启了 SELinux ,这将导致 RustDesk 服务无法正常启动和运行。
-
-您可以在终端执行 `sestatus` ,查看 SELinux 是否开启。
-根据是否开启,您可以看到如下两种不同的输出:
-
-```bash
-# Enabled
-SELinux status: enabled
-...
-
-# Disabled
-SELinux status: disabled
-...
-```
-
-# 添加 SELinux 策略
-
-关于 SELinux 的介绍,请参考 [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials) 。
-
-此处以 Fedora 38 为例,介绍如何添加 SELinux 策略。
-
-```bash
-sudo dnf install selinux-policy-devel make
-```
-
-添加 SELinux 策略需要确定服务的类型,服务的类型在进程的安全上下文中。
-
-```bash
-$ ps -eZ | grep rustdesk
-system_u:system_r:init_t:s0 80439 ? 00:00:02 rustdesk
-```
-
-`system_u:system_r:init_t:s0` 是 rustdesk 进程的安全上下文,其中第三个字段 `init_t` 是进程的类型。
-
-有两种方式编写 SELinux 类型规则:
-
-1. 对默认的 `init_t` 添加规则。
-2. 新加一个类型 `rustdesk_t` ,再添加规则。
-
-第一种方式修改比较小,但因为改了默认的 `init_t` ,也相当于给其他使用 `init_t` 类型的服务添加了授权。不建议使用。
-第二种方式是从零添加规则,会有很多需要添加的规则,不同系统可能也有差异。可能实际使用的时候,需要做一些调整。
-
-## 使用默认的类型
-
-RustDesk 服务默认的类型是 `init_t` ,这是由 [SELinux 的上下文继承规则](https://wiki.gentoo.org/wiki/SELinux/Tutorials/How_does_a_process_get_into_a_certain_context)决定的。
-
-**注意**:修改默认的类型,意味着其他服务的策略也可能发生改变。请谨慎使用这种方式!
-
-编辑规则文件 rustdesk.te:
-
-```text
-module rustdesk 1.0;
-
-require {
- type event_device_t;
- type xserver_t;
- type xserver_port_t;
- type sudo_exec_t;
- type init_t;
- type ephemeral_port_t;
- type user_tmp_t;
- type user_fonts_cache_t;
- type pulseaudio_home_t;
- type session_dbusd_tmp_t;
- type unconfined_dbusd_t;
- class process execmem;
- class file { open read create write execute execute_no_trans map setattr lock link unlink };
- class unix_stream_socket connectto;
- class tcp_socket name_connect;
- class dir { add_name remove_name };
- class sock_file write;
- class chr_file { open read write } ;
-}
-
-#============= init_t ==============
-allow init_t xserver_t:unix_stream_socket connectto;
-allow init_t sudo_exec_t:file { open read execute execute_no_trans };
-allow init_t user_tmp_t:file { open write setattr };
-allow init_t self:process execmem;
-allow init_t user_fonts_cache_t:dir { add_name remove_name };
-allow init_t user_fonts_cache_t:file { read write create open link lock unlink };
-allow init_t xserver_port_t:tcp_socket name_connect;
-allow init_t pulseaudio_home_t:file { read write open lock };
-allow init_t session_dbusd_tmp_t:sock_file write;
-allow init_t unconfined_dbusd_t:unix_stream_socket connectto;
-
-#!!!! This avc can be allowed using the boolean 'nis_enabled'
-allow init_t ephemeral_port_t:tcp_socket name_connect;
-
-#!!!! This avc can be allowed using the boolean 'domain_can_mmap_files'
-allow init_t sudo_exec_t:file map;
-
-
-#============= init_t wayland ==============
-allow init_t event_device_t:chr_file { open read write };
-
-#!!!! This avc can be allowed using the boolean 'domain_can_mmap_files'
-allow init_t user_tmp_t:file map;
-
-```
-
-执行:
-
-```bash
-$ checkmodule -M -m -o rustdesk.mod rustdesk.te && semodule_package -o rustdesk.pp -m rustdesk.mod && sudo semodule -i rustdesk.pp
-$ sudo semodule -l | grep rustdesk
-```
-
-## 新建 rustdesk_t 的类型
-
-1. 新建文件夹,如 `mkdir rustdesk-selinux-1.0` 。
-2. 创建 SELinux 策略文件, `touch Makefile rustdesk.te rustdesk.fc rustdesk.if` 。
-
-```text
-.
-├── Makefile
-├── rustdesk.fc
-├── rustdesk.if
-└── rustdesk.te
-```
-
-其中 `rustdesk.te` 是主要的策略文件。
-
-本次示例中,这个文件主要来自3个部分:
-
-1. github 的 selinux-policy 仓库中的 [`init.te`](https://github.com/fedora-selinux/selinux-policy/blob/rawhide/policy/modules/system/init.te)。
-2. audit 日志,`grep rustdesk /var/log/audit/audit.log | audit2allow -a -M test`。
-3. 测试系统的 `init_t` 策略,`sesearch -A | grep 'allow init_t ' | sed 's/allow init_t /allow rustdesk_t /g'`。
-
-一些策略是重复的,一些策略是多余的,但这是可以接受的,因为它对 rustdesk_t 起作用。
-
-各个文件内容如下。
-
-rustdes.te:
-
-```text
-
-policy_module(rustdesk, 1.0)
-
-type rustdesk_t;
-type rustdesk_exec_t;
-
-gen_require(`
- # used for direct running of init scripts
- # by admin domains
- attribute direct_run_init;
- attribute direct_init;
- attribute direct_init_entry;
-
- attribute init_script_domain_type;
- attribute initrc_transition_domain;
- # Attribute used for systemd so domains can allow systemd to create sock_files
- attribute init_sock_file_type;
- # Attribute for directories that systemd will watch based on path units
- # (see systemd.path(5) for more info) (Deprecated)
- attribute init_watch_path_type;
-
- # Mark process types as daemons
- attribute daemon;
- attribute systemprocess;
- attribute systemprocess_entry;
-
- # Mark file type as a daemon run directory
- attribute daemonrundir;
-
- class passwd rootok;
- class dbus { acquire_svc send_msg };
- class process execmem;
-
- type abrt_dump_oops_t;
- type abrt_upload_watch_t;
- type adjtime_t;
- type aiccu_t;
- type amanda_inetd_exec_t;
- type amanda_t;
- type antivirus_t;
- type apcupsd_power_t;
- type auditd_etc_t;
- type autofs_device_t;
- type binfmt_misc_fs_t;
- type bitlbee_exec_t;
- type bitlbee_t;
- type boltd_var_lib_t;
- type boltd_var_run_t;
- type boothd_t;
- type bootloader_exec_t;
- type bootloader_t;
- type bpf_t;
- type bugzilla_script_t;
- type certwatch_t;
- type cgroup_t;
- type chkpwd_exec_t;
- type chkpwd_t;
- type chronyc_t;
- type chronyd_exec_t;
- type chronyd_keys_t;
- type chronyd_restricted_t;
- type chroot_exec_t;
- type cifs_helper_t;
- type cinder_domain;
- type cloudform_domain;
- type collectd_script_t;
- type comsat_exec_t;
- type comsat_t;
- type config_home_t;
- type console_device_t;
- type consolekit_log_t;
- type container_kvm_t;
- type container_runtime_domain;
- type container_runtime_tmpfs_t;
- type container_var_lib_t;
- type crack_t;
- type cups_brf_t;
- type cupsd_exec_t;
- type cupsd_lpd_exec_t;
- type cupsd_lpd_t;
- type cupsd_t;
- type cvs_exec_t;
- type cvs_t;
- type data_home_t;
- type dbskkd_exec_t;
- type dbskkd_t;
- type default_context_t;
- type default_t;
- type devicekit_disk_t;
- type devicekit_power_t;
- type devicekit_t;
- type device_t;
- type devlog_t;
- type devpts_t;
- type dhcpc_state_t;
- type dhcp_state_t;
- type dirsrvadmin_script_t;
- type dri_device_t;
- type dspam_script_t;
- type efivarfs_t;
- type ephemeral_port_t;
- type etc_aliases_t;
- type etc_runtime_t;
- type etc_t;
- type event_device_t;
- type faillog_t;
- type fetchmail_t;
- type fingerd_exec_t;
- type fingerd_t;
- type fixed_disk_device_t;
- type flatpak_helper_t;
- type fprintd_exec_t;
- type fprintd_t;
- type fprintd_var_lib_t;
- type fsadm_t;
- type ftpd_exec_t;
- type ftpd_t;
- type fwupd_cache_t;
- type fwupd_t;
- type gconfdefaultsm_t;
- type geoclue_t;
- type getty_exec_t;
- type getty_t;
- type gitd_exec_t;
- type git_system_t;
- type gnome_home_type;
- type gnomesystemmm_t;
- type guest_t;
- type home_bin_t;
- type home_root_t;
- type hostname_etc_t;
- type httpd_log_t;
- type httpd_t;
- type httpd_tmp_t;
- type hugetlbfs_t;
- type ibacm_t;
- type ibacm_var_run_t;
- type inetd_child_exec_t;
- type inetd_child_t;
- type initctl_t;
- type init_exec_t;
- type initrc_state_t;
- type initrc_t;
- type initrc_var_run_t;
- type init_t;
- type init_tmp_t;
- type init_var_lib_t;
- type init_var_run_t;
- type insights_client_t;
- type install_exec_t;
- type install_t;
- type ipsec_conf_file_t;
- type ipsec_t;
- type ipsec_var_run_t;
- type irqbalance_t;
- type iscsi_var_lib_t;
- type jockey_t;
- type journalctl_exec_t;
- type kadmind_t;
- type kdump_crash_t;
- type kdumpctl_t;
- type kdump_t;
- type keepalived_unconfined_script_t;
- type kernel_t;
- type kmod_exec_t;
- type kmod_t;
- type kmscon_t;
- type kmsg_device_t;
- type krb5_keytab_t;
- type ktalkd_exec_t;
- type ktalkd_t;
- type l2tpd_t;
- type lastlog_t;
- type ld_so_cache_t;
- type lldpad_t;
- type loadkeys_t;
- type locale_t;
- type lvm_control_t;
- type lvm_etc_t;
- type lvm_t;
- type lvm_var_run_t;
- type machineid_t;
- type mail_spool_t;
- type mandb_t;
- type mdadm_t;
- type mdadm_var_run_t;
- type memcached_t;
- type memory_device_t;
- type mnt_t;
- type modemmanager_t;
- type modules_dep_t;
- type modules_object_t;
- type mon_procd_t;
- type mount_t;
- type mount_var_run_t;
- type mptcpd_t;
- type munin_plugin_domain;
- type munin_t;
- type mysqld_t;
- type mythtv_script_t;
- type naemon_t;
- type nagios_plugin_domain;
- type nagios_system_plugin_t;
- type named_conf_t;
- type named_zone_t;
- type net_conf_t;
- type netlabel_mgmt_t;
- type networkmanager_dispatcher_plugin;
- type NetworkManager_dispatcher_t;
- type NetworkManager_priv_helper_t;
- type NetworkManager_t;
- type nfsd_fs_t;
- type nfsidmap_t;
- type ninfod_t;
- type nrpe_exec_t;
- type nrpe_t;
- type nsfs_t;
- type openshift_cgroup_read_t;
- type openshift_net_read_t;
- type oracleasm_t;
- type passwd_file_t;
- type pcscd_t;
- type pdns_t;
- type pegasus_openlmi_domain;
- type pkcs_slotd_t;
- type pkcs_slotd_tmpfs_t;
- type plymouthd_t;
- type plymouth_exec_t;
- type policykit_t;
- type postfix_exec_t;
- type print_spool_t;
- type proc_net_t;
- type proc_security_t;
- type ptchown_t;
- type pulseaudio_home_t;
- type qmail_tcp_env_exec_t;
- type qmail_tcp_env_t;
- type qpidd_t;
- type quota_exec_t;
- type quota_t;
- type radiusd_t;
- type random_device_t;
- type random_seed_t;
- type rdisc_t;
- type rhsmcertd_t;
- type rlogind_exec_t;
- type rlogind_t;
- type root_t;
- type rpm_script_t;
- type rpm_var_cache_t;
- type rpm_var_lib_t;
- type rshd_exec_t;
- type rshd_t;
- type rsync_exec_t;
- type rsync_t;
- type rustdesk_exec_t;
- type rustdesk_t;
- type sblim_domain;
- type security_t;
- type selinux_config_t;
- type selinux_login_config_t;
- type semanage_store_t;
- type session_dbusd_tmp_t;
- type shell_exec_t;
- type smbcontrol_t;
- type smokeping_cgi_script_t;
- type spc_t;
- type speech_dispatcher_t;
- type sshd_exec_t;
- type sshd_t;
- type ssh_keysign_t;
- type sslh_t;
- type sssd_var_lib_t;
- type staff_t;
- type stratisd_data_t;
- type stunnel_exec_t;
- type stunnel_t;
- type sudo_exec_t;
- type sulogin_exec_t;
- type sulogin_t;
- type svc_start_exec_t;
- type svc_start_t;
- type svirt_file_type;
- type svirt_sandbox_domain;
- type svirt_t;
- type svirt_tcg_t;
- type swat_exec_t;
- type swat_t;
- type sysctl_kernel_t;
- type sysfs_t;
- type syslogd_t;
- type systemd_bootchart_t;
- type system_dbusd_t;
- type system_dbusd_var_run_t;
- type systemd_coredump_t;
- type systemd_gpt_generator_t;
- type systemd_home_t;
- type systemd_hostnamed_t;
- type systemd_hwdb_t;
- type systemd_importd_t;
- type systemd_initctl_t;
- type systemd_journal_upload_t;
- type systemd_localed_t;
- type systemd_logger_t;
- type systemd_logind_inhibit_var_run_t;
- type systemd_logind_sessions_t;
- type systemd_logind_t;
- type systemd_logind_var_run_t;
- type systemd_machined_t;
- type systemd_modules_load_t;
- type systemd_mount_directory;
- type systemd_networkd_exec_t;
- type systemd_networkd_t;
- type systemd_network_generator_t;
- type systemd_notify_t;
- type systemd_passwd_agent_exec_t;
- type systemd_passwd_agent_t;
- type systemd_passwd_var_run_t;
- type systemd_pstore_t;
- type systemd_resolved_exec_t;
- type systemd_resolved_t;
- type systemd_rfkill_t;
- type systemd_rfkill_var_lib_t;
- type systemd_sleep_t;
- type systemd_socket_proxyd_t;
- type systemd_sysctl_t;
- type systemd_systemctl_exec_t;
- type systemd_timedated_t;
- type systemd_timedated_var_lib_t;
- type systemd_tmpfiles_t;
- type systemd_userdbd_runtime_t;
- type systemd_userdbd_t;
- type tangd_db_t;
- type tangd_t;
- type targetclid_t;
- type tcpd_exec_t;
- type tcpd_t;
- type telnetd_exec_t;
- type telnetd_t;
- type tftpd_exec_t;
- type tftpd_t;
- type thin_domain;
- type thumb_t;
- type timedatex_t;
- type tlp_t;
- type tmpfs_t;
- type tmpreaper_t;
- type tmp_t;
- type tpm_device_t;
- type tty_device_t;
- type udev_rules_t;
- type udev_t;
- type unconfined_dbusd_t;
- type unconfined_service_t;
- type unconfined_t;
- type unlabeled_t;
- type unreserved_port_t;
- type updpwd_exec_t;
- type updpwd_t;
- type urandom_device_t;
- type usbtty_device_t;
- type user_devpts_t;
- type user_fonts_cache_t;
- type user_home_dir_t;
- type user_home_t;
- type user_t;
- type user_tmp_t;
- type user_tty_device_t;
- type usr_t;
- type uucpd_exec_t;
- type uucpd_t;
- type uuidd_t;
- type uuidd_var_run_t;
- type var_lib_nfs_t;
- type var_lib_t;
- type var_log_t;
- type var_run_t;
- type var_spool_t;
- type var_t;
- type virsh_t;
- type virtd_t;
- type virt_etc_rw_t;
- type virtio_device_t;
- type vnstatd_t;
- type watchdog_device_t;
- type watchdog_t;
- type wireguard_t;
- type wireless_device_t;
- type wtmp_t;
- type xdm_exec_t;
- type xdm_t;
- type xdm_var_lib_t;
- type xenconsoled_t;
- type xend_t;
- type xguest_t;
- type xserver_port_t;
- type xserver_t;
-')
-
-##############################################################################
-#
-# Part 1. The following rules are mainly from the opensource `init.te`
-# https://github.com/fedora-selinux/selinux-policy/blob/rawhide/policy/modules/system/init.te
-#
-# Note: Part 1 will probably be mostly the same as Part 3. But it's acceptable for now.
-#
-
-init_daemon_domain(rustdesk_t, rustdesk_exec_t)
-
-domain_role_change_exemption(rustdesk_t)
-domain_subj_id_change_exemption(rustdesk_t)
-domain_obj_id_change_exemption(rustdesk_t)
-role system_r types rustdesk_t;
-corecmd_shell_entry_type(rustdesk_t)
-typeattribute rustdesk_t init_script_domain_type;
-
-
-#######################################
-
-# Use capabilities. old rule:
-allow rustdesk_t self:capability ~{ audit_control audit_write sys_module };
-allow rustdesk_t self:capability2 ~{ mac_admin mac_override };
-allow rustdesk_t self:cap_userns all_cap_userns_perms;
-allow rustdesk_t self:tcp_socket { listen accept };
-allow rustdesk_t self:packet_socket create_socket_perms;
-allow rustdesk_t self:key manage_key_perms;
-allow rustdesk_t self:bpf { map_create map_read map_write prog_load prog_run };
-
-allow rustdesk_t self:file mounton;
-allow rustdesk_t self:fifo_file rw_fifo_file_perms;
-
-allow rustdesk_t self:service manage_service_perms;
-allow rustdesk_t self:user_namespace create;
-
-# Re-exec itself
-can_exec(rustdesk_t, rustdesk_exec_t)
-# executing content in /run/initramfs
-manage_files_pattern(rustdesk_t, initrc_state_t, initrc_state_t)
-can_exec(rustdesk_t, initrc_state_t)
-
-allow rustdesk_t initrc_t:unix_stream_socket { connectto create_stream_socket_perms };
-allow rustdesk_t initrc_t:tcp_socket create_stream_socket_perms;
-allow initrc_t rustdesk_t:unix_stream_socket { connectto rw_stream_socket_perms sendto };
-allow initrc_t rustdesk_t:fifo_file rw_fifo_file_perms;
-
-manage_files_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-manage_dirs_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-manage_lnk_files_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-manage_sock_files_pattern(rustdesk_t, init_tmp_t, init_tmp_t)
-files_tmp_filetrans(rustdesk_t, init_tmp_t, { file sock_file })
-allow rustdesk_t init_tmp_t:file map;
-
-manage_dirs_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-manage_files_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-manage_lnk_files_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-manage_sock_files_pattern(rustdesk_t, init_var_lib_t, init_var_lib_t)
-files_var_lib_filetrans(rustdesk_t, init_var_lib_t, { dir file })
-allow rustdesk_t init_var_lib_t:dir mounton;
-allow rustdesk_t init_var_lib_t:file map;
-
-manage_dirs_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_lnk_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_sock_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_fifo_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_blk_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-manage_chr_files_pattern(rustdesk_t, init_var_run_t, init_var_run_t)
-files_pid_filetrans(rustdesk_t, init_var_run_t, { dir file blk_file chr_file fifo_file})
-allow rustdesk_t init_var_run_t:dir mounton;
-allow rustdesk_t init_var_run_t:file mounton;
-allow rustdesk_t init_var_run_t:sock_file relabelto;
-allow rustdesk_t init_var_run_t:blk_file { getattr relabelto };
-allow rustdesk_t init_var_run_t:chr_file { getattr relabelto };
-allow rustdesk_t init_var_run_t:fifo_file { getattr relabelto };
-
-allow rustdesk_t machineid_t:file manage_file_perms;
-files_pid_filetrans(rustdesk_t, machineid_t, file, "machine-id")
-files_etc_filetrans(rustdesk_t, machineid_t, file, "machine-id")
-allow rustdesk_t machineid_t:file mounton;
-
-allow rustdesk_t initctl_t:fifo_file manage_fifo_file_perms;
-dev_filetrans(rustdesk_t, initctl_t, fifo_file)
-
-# Modify utmp.
-allow rustdesk_t initrc_var_run_t:file { rw_file_perms setattr };
-
-kernel_read_system_state(rustdesk_t)
-kernel_share_state(rustdesk_t)
-kernel_stream_connect(rustdesk_t)
-kernel_rw_stream_socket_perms(rustdesk_t)
-kernel_rw_unix_dgram_sockets(rustdesk_t)
-kernel_mounton_systemd_ProtectKernelTunables(rustdesk_t)
-kernel_read_core_if(rustdesk_t)
-kernel_mounton_core_if(rustdesk_t)
-kernel_mounton_all_sysctls(rustdesk_t)
-kernel_get_sysvipc_info(rustdesk_t)
-kernel_load_module(rustdesk_t)
-kernel_read_all_proc(rustdesk_t)
-kernel_list_all_proc(rustdesk_t)
-kernel_mounton_all_proc(rustdesk_t)
-
-# There is bug in kernel in 4.16 where lot of domains requesting module_request, for now dontauditing
-kernel_dontaudit_request_load_module(rustdesk_t)
-
-corecmd_exec_chroot(rustdesk_t)
-corecmd_exec_bin(rustdesk_t)
-
-corenet_all_recvfrom_netlabel(rustdesk_t)
-corenet_tcp_bind_all_ports(rustdesk_t)
-corenet_udp_bind_all_ports(rustdesk_t)
-
-dev_create_all_files(rustdesk_t)
-dev_create_all_chr_files(rustdesk_t)
-dev_list_sysfs(rustdesk_t)
-dev_manage_sysfs(rustdesk_t)
-dev_mounton_all_device_nodes(rustdesk_t)
-dev_setattr_all_blk_files(rustdesk_t)
-dev_setattr_all_chr_files(rustdesk_t)
-dev_read_urand(rustdesk_t)
-dev_read_raw_memory(rustdesk_t)
-# Early devtmpfs
-dev_rw_generic_chr_files(rustdesk_t)
-dev_filetrans_all_named_dev(rustdesk_t)
-dev_write_watchdog(rustdesk_t)
-dev_rw_inherited_input_dev(rustdesk_t)
-dev_rw_dri(rustdesk_t)
-dev_rw_tpm(rustdesk_t)
-
-domain_getpgid_all_domains(rustdesk_t)
-domain_kill_all_domains(rustdesk_t)
-domain_signal_all_domains(rustdesk_t)
-domain_signull_all_domains(rustdesk_t)
-domain_sigstop_all_domains(rustdesk_t)
-domain_sigchld_all_domains(rustdesk_t)
-domain_read_all_domains_state(rustdesk_t)
-domain_getattr_all_domains(rustdesk_t)
-domain_setrlimit_all_domains(rustdesk_t)
-domain_rlimitinh_all_domains(rustdesk_t)
-domain_noatsecure_all_domains(rustdesk_t)
-domain_setpriority_all_domains(rustdesk_t)
-
-files_read_config_files(rustdesk_t)
-files_read_all_pids(rustdesk_t)
-files_map_all_pids(rustdesk_t)
-files_read_system_conf_files(rustdesk_t)
-files_rw_generic_pids(rustdesk_t)
-files_dontaudit_search_isid_type_dirs(rustdesk_t)
-files_read_isid_type_files(rustdesk_t)
-files_read_etc_runtime_files(rustdesk_t)
-files_manage_all_locks(rustdesk_t)
-files_manage_etc_runtime_files(rustdesk_t)
-files_manage_etc_symlinks(rustdesk_t)
-files_etc_filetrans_etc_runtime(rustdesk_t, file)
-# Run /etc/X11/prefdm:
-files_exec_etc_files(rustdesk_t)
-files_read_usr_files(rustdesk_t)
-files_write_root_dirs(rustdesk_t)
-# file descriptors inherited from the rootfs:
-files_dontaudit_rw_root_files(rustdesk_t)
-files_dontaudit_rw_root_chr_files(rustdesk_t)
-files_dontaudit_mounton_modules_object(rustdesk_t)
-files_manage_mnt_dirs(rustdesk_t)
-files_manage_mnt_files(rustdesk_t)
-files_read_mnt_symlinks(rustdesk_t)
-files_mounton_etc(rustdesk_t)
-files_create_default_dir(rustdesk_t)
-files_remount_rootfs(rustdesk_t)
-files_create_var_dirs(rustdesk_t)
-files_watch_non_security_dirs(rustdesk_t)
-files_watch_non_security_files(rustdesk_t)
-files_watch_non_security_lnk_files(rustdesk_t)
-
-fs_read_efivarfs_files(rustdesk_t)
-fs_setattr_efivarfs_files(rustdesk_t)
-fs_read_nfsd_files(rustdesk_t)
-
-fstools_getattr_swap_files(rustdesk_t)
-
-mcs_process_set_categories(rustdesk_t)
-
-mls_file_read_all_levels(rustdesk_t)
-mls_file_write_all_levels(rustdesk_t)
-mls_file_downgrade(rustdesk_t)
-mls_file_upgrade(rustdesk_t)
-mls_fd_use_all_levels(rustdesk_t)
-mls_fd_share_all_levels(rustdesk_t)
-mls_process_set_level(rustdesk_t)
-mls_process_write_down(rustdesk_t)
-mls_socket_read_all_levels(rustdesk_t)
-mls_socket_write_all_levels(rustdesk_t)
-mls_rangetrans_source(rustdesk_t)
-
-selinux_set_all_booleans(rustdesk_t)
-selinux_load_policy(rustdesk_t)
-selinux_mounton_fs(rustdesk_t)
-allow rustdesk_t security_t:security load_policy;
-
-selinux_compute_access_vector(rustdesk_t)
-selinux_compute_create_context(rustdesk_t)
-selinux_compute_user_contexts(rustdesk_t)
-selinux_validate_context(rustdesk_t)
-selinux_compute_relabel_context(rustdesk_t)
-selinux_unmount_fs(rustdesk_t)
-
-term_create_pty_dir(rustdesk_t)
-term_use_unallocated_ttys(rustdesk_t)
-term_setattr_unallocated_ttys(rustdesk_t)
-term_use_console(rustdesk_t)
-term_use_all_inherited_terms(rustdesk_t)
-term_use_usb_ttys(rustdesk_t)
-term_use_all_ptys(rustdesk_t)
-term_setattr_all_ptys(rustdesk_t)
-term_use_virtio_console(rustdesk_t)
-term_watch_console_dev(rustdesk_t)
-term_watch_reads_console_dev(rustdesk_t)
-term_watch_unallocated_ttys(rustdesk_t)
-term_watch_reads_unallocated_ttys(rustdesk_t)
-term_watch_user_ttys(rustdesk_t)
-term_watch_reads_user_ttys(rustdesk_t)
-
-# Run init scripts.
-init_domtrans_script(rustdesk_t)
-init_exec_notrans_direct_init_entry(rustdesk_t)
-
-libs_rw_ld_so_cache(rustdesk_t)
-
-logging_create_devlog_dev(rustdesk_t)
-logging_send_syslog_msg(rustdesk_t)
-logging_send_audit_msgs(rustdesk_t)
-logging_manage_generic_logs(rustdesk_t)
-logging_mmap_generic_logs(rustdesk_t)
-logging_relabel_devlog_dev(rustdesk_t)
-logging_manage_audit_config(rustdesk_t)
-logging_create_syslog_netlink_audit_socket(rustdesk_t)
-logging_write_var_log_dirs(rustdesk_t)
-logging_manage_var_log_symlinks(rustdesk_t)
-
-seutil_read_config(rustdesk_t)
-seutil_read_login_config(rustdesk_t)
-seutil_read_default_contexts(rustdesk_t)
-seutil_read_module_store(rustdesk_t)
-
-miscfiles_manage_localization(rustdesk_t)
-miscfiles_filetrans_named_content(rustdesk_t)
-
-udev_manage_rules_files(rustdesk_t)
-
-userdom_use_user_ttys(rustdesk_t)
-userdom_manage_tmp_dirs(rustdesk_t)
-userdom_manage_tmp_sockets(rustdesk_t)
-userdom_delete_user_tmp_files(rustdesk_t)
-userdom_delete_user_home_content_files(rustdesk_t)
-userdom_connectto_stream(rustdesk_t)
-userdom_rw_inherited_user_pipes(rustdesk_t)
-userdom_transition_login_userdomain(rustdesk_t)
-userdom_nnp_transition_login_userdomain(rustdesk_t)
-userdom_noatsecure_login_userdomain(rustdesk_t)
-userdom_sigchld_login_userdomain(rustdesk_t)
-userdom_use_user_ptys(rustdesk_t)
-userdom_watch_user_ptys(rustdesk_t)
-userdom_watch_reads_user_ptys(rustdesk_t)
-
-allow rustdesk_t self:process setsched;
-
-ifdef(`distro_redhat',`
- fs_manage_tmpfs_files(rustdesk_t)
- fs_manage_tmpfs_symlinks(rustdesk_t)
- fs_manage_tmpfs_sockets(rustdesk_t)
- fs_manage_tmpfs_chr_files(rustdesk_t)
- fs_exec_tmpfs_files(rustdesk_t)
- fs_read_tmpfs_symlinks(rustdesk_t)
- fs_tmpfs_filetrans(rustdesk_t, initctl_t, fifo_file)
- fs_tmpfs_filetrans_named_content(rustdesk_t)
- fs_relabelfrom_tmpfs_lnk_files(rustdesk_t)
-
- logging_stream_connect_syslog(rustdesk_t)
- logging_relabel_syslog_pid_socket(rustdesk_t)
-')
-
-corecmd_shell_domtrans(rustdesk_t, initrc_t)
-
-storage_raw_rw_fixed_disk(rustdesk_t)
-
-sysnet_read_dhcpc_state(rustdesk_t)
-
-allow rustdesk_t self:system all_system_perms;
-allow rustdesk_t self:system module_load;
-allow rustdesk_t self:unix_dgram_socket { create_socket_perms sendto };
-allow rustdesk_t self:process { setkeycreate setsockcreate setfscreate setrlimit setexec };
-allow rustdesk_t self:process { getcap setcap };
-allow rustdesk_t self:unix_stream_socket { create_stream_socket_perms connectto recvfrom };
-allow rustdesk_t self:netlink_kobject_uevent_socket create_socket_perms;
-allow rustdesk_t self:netlink_selinux_socket create_socket_perms;
-allow rustdesk_t self:unix_dgram_socket lock;
-# Until systemd is fixed
-allow daemon rustdesk_t:socket_class_set { getopt read getattr ioctl setopt write };
-allow rustdesk_t self:udp_socket create_socket_perms;
-allow rustdesk_t self:netlink_route_socket create_netlink_socket_perms;
-
-allow rustdesk_t initrc_t:unix_dgram_socket create_socket_perms;
-
-kernel_list_unlabeled(rustdesk_t)
-kernel_read_unlabeled_lnk_files(rustdesk_t)
-kernel_read_network_state(rustdesk_t)
-kernel_rw_all_sysctls(rustdesk_t)
-kernel_rw_security_state(rustdesk_t)
-kernel_rw_usermodehelper_state(rustdesk_t)
-kernel_read_software_raid_state(rustdesk_t)
-kernel_unmount_debugfs(rustdesk_t)
-kernel_setsched(rustdesk_t)
-kernel_mounton_kernel_sysctl(rustdesk_t)
-
-dev_write_kmsg(rustdesk_t)
-dev_write_urand(rustdesk_t)
-dev_rw_lvm_control(rustdesk_t)
-dev_rw_autofs(rustdesk_t)
-dev_manage_generic_symlinks(rustdesk_t)
-dev_manage_generic_dirs(rustdesk_t)
-dev_manage_generic_files(rustdesk_t)
-dev_read_generic_chr_files(rustdesk_t)
-dev_relabel_generic_dev_dirs(rustdesk_t)
-dev_relabel_all_dev_nodes(rustdesk_t)
-dev_relabel_all_dev_files(rustdesk_t)
-dev_manage_sysfs_dirs(rustdesk_t)
-dev_relabel_sysfs_dirs(rustdesk_t)
-dev_rw_wireless(rustdesk_t)
-
-files_search_all(rustdesk_t)
-files_mounton_all_mountpoints(rustdesk_t)
-files_unmount_all_file_type_fs(rustdesk_t)
-files_remount_all_file_type_fs(rustdesk_t)
-files_mounton_kernel_symbol_table(rustdesk_t)
-files_manage_all_pid_dirs(rustdesk_t)
-files_write_all_pid_sockets(rustdesk_t)
-files_manage_etc_dirs(rustdesk_t)
-files_manage_generic_tmp_dirs(rustdesk_t)
-files_relabel_all_pid_dirs(rustdesk_t)
-files_relabel_all_pid_files(rustdesk_t)
-files_create_all_pid_sockets(rustdesk_t)
-files_delete_all_pids(rustdesk_t)
-files_exec_generic_pid_files(rustdesk_t)
-files_create_all_pid_pipes(rustdesk_t)
-files_create_all_spool_sockets(rustdesk_t)
-files_delete_all_spool_sockets(rustdesk_t)
-files_create_var_lib_dirs(rustdesk_t)
-files_create_var_lib_symlinks(rustdesk_t)
-files_read_var_lib_symlinks(rustdesk_t)
-files_manage_urandom_seed(rustdesk_t)
-files_list_locks(rustdesk_t)
-files_list_spool(rustdesk_t)
-files_list_var(rustdesk_t)
-files_write_var_dirs(rustdesk_t)
-files_manage_var_symlinks(rustdesk_t)
-files_setattr_var_dirs(rustdesk_t)
-files_list_boot(rustdesk_t)
-files_list_home(rustdesk_t)
-files_create_lock_dirs(rustdesk_t)
-files_relabel_all_files(rustdesk_t)
-files_read_kernel_modules(rustdesk_t)
-files_map_kernel_modules(rustdesk_t)
-files_dontaudit_mounton_isid(rustdesk_t)
-files_delete_tmp_files(rustdesk_t)
-files_delete_tmp_pipes(rustdesk_t)
-files_delete_tmp_sockets(rustdesk_t)
-fs_getattr_all_fs(rustdesk_t)
-fs_manage_cgroup_dirs(rustdesk_t)
-fs_manage_cgroup_files(rustdesk_t)
-fs_manage_bpf_dirs(rustdesk_t)
-fs_manage_bpf_files(rustdesk_t)
-fs_manage_hugetlbfs_dirs(rustdesk_t)
-fs_manage_tmpfs_dirs(rustdesk_t)
-fs_relabel_tmpfs_blk_file(rustdesk_t)
-fs_relabel_tmpfs_chr_file(rustdesk_t)
-fs_relabel_pstore_dirs(rustdesk_t)
-fs_relabel_tmpfs_dirs(rustdesk_t)
-fs_relabel_tmpfs_files(rustdesk_t)
-fs_relabel_tmpfs_fifo_files(rustdesk_t)
-fs_mount_all_fs(rustdesk_t)
-fs_unmount_all_fs(rustdesk_t)
-fs_remount_all_fs(rustdesk_t)
-fs_list_all(rustdesk_t)
-fs_list_auto_mountpoints(rustdesk_t)
-fs_register_binary_executable_type(rustdesk_t)
-fs_relabel_tmpfs_sock_file(rustdesk_t)
-fs_rw_tmpfs_files(rustdesk_t)
-fs_relabel_cgroup_dirs(rustdesk_t)
-fs_search_cgroup_dirs(rustdesk_t)
-# for network namespaces
-fs_read_nsfs_files(rustdesk_t)
-
-storage_getattr_removable_dev(rustdesk_t)
-
-term_relabel_ptys_dirs(rustdesk_t)
-
-auth_relabel_login_records(rustdesk_t)
-auth_relabel_pam_console_data_dirs(rustdesk_t)
-auth_manage_faillog(rustdesk_t)
-
-clock_read_adjtime(rustdesk_t)
-
-init_read_script_state(rustdesk_t)
-
-seutil_read_file_contexts(rustdesk_t)
-
-systemd_exec_systemctl(rustdesk_t)
-systemd_manage_home_content(rustdesk_t)
-systemd_manage_unit_dirs(rustdesk_t)
-systemd_manage_random_seed(rustdesk_t)
-systemd_manage_all_unit_files(rustdesk_t)
-systemd_logger_stream_connect(rustdesk_t)
-systemd_login_manage_pid_files(rustdesk_t)
-systemd_config_all_services(rustdesk_t)
-systemd_relabelto_fifo_file_passwd_run(rustdesk_t)
-systemd_relabel_unit_dirs(rustdesk_t)
-systemd_relabel_unit_files(rustdesk_t)
-systemd_relabel_unit_symlinks(rustdesk_t)
-systemd_login_status(rustdesk_t)
-systemd_map_networkd_exec_files(rustdesk_t)
-systemd_map_resolved_exec_files(rustdesk_t)
-systemd_rfkill_setattr_lib(rustdesk_t)
-systemd_rfkill_mounton_var_lib(rustdesk_t)
-systemd_rfkill_manage_lib_dirs(rustdesk_t)
-systemd_timedated_mounton_var_lib(rustdesk_t)
-systemd_mounton_inhibit_dir(rustdesk_t)
-systemd_timedated_manage_lib_dirs(rustdesk_t)
-systemd_login_mounton_pid_dirs(rustdesk_t)
-systemd_mounton_inherited_logind_sessions_dirs(rustdesk_t)
-systemd_delete_private_tmp(rustdesk_t)
-systemd_userdbd_stream_connect(rustdesk_t)
-systemd_userdbd_runtime_filetrans(rustdesk_t)
-systemd_userdbd_runtime_manage_symlinks(rustdesk_t)
-systemd_write_inherited_logind_sessions_pipes(rustdesk_t)
-
-create_sock_files_pattern(rustdesk_t, init_sock_file_type, init_sock_file_type)
-
-create_dirs_pattern(rustdesk_t, var_log_t, var_log_t)
-
-auth_use_nsswitch(rustdesk_t)
-auth_rw_login_records(rustdesk_t)
-auth_rw_lastlog(rustdesk_t)
-auth_domtrans_chk_passwd(rustdesk_t)
-auth_manage_passwd(rustdesk_t)
-
-allow rustdesk_t var_run_t:dir relabelto;
-
-allow rustdesk_t daemon:unix_stream_socket create_stream_socket_perms;
-allow rustdesk_t daemon:unix_dgram_socket create_socket_perms;
-allow rustdesk_t daemon:tcp_socket create_stream_socket_perms;
-allow rustdesk_t daemon:udp_socket create_socket_perms;
-allow daemon rustdesk_t:unix_dgram_socket sendto;
-# need write to /var/run/systemd/notify
-init_write_pid_socket(daemon)
-allow daemon rustdesk_t:unix_stream_socket { append write read getattr ioctl };
-
-allow rustdesk_t daemon:process siginh;
-
-ifdef(`hide_broken_symptoms',`
- # RHEL4 systems seem to have a stray
- # fds open from the initrd
- ifdef(`distro_rhel4',`
- kernel_dontaudit_use_fds(daemon)
- ')
-
- dontaudit daemon rustdesk_t:dir search_dir_perms;
- dontaudit daemon rustdesk_t:file read_file_perms;
-')
-
-dontaudit systemprocess rustdesk_t:unix_stream_socket getattr;
-
-allow rustdesk_t daemon:unix_stream_socket create_stream_socket_perms;
-allow rustdesk_t daemon:unix_dgram_socket create_socket_perms;
-allow daemon rustdesk_t:unix_stream_socket ioctl;
-allow daemon rustdesk_t:unix_dgram_socket sendto;
-
-# Handle upstart/systemd direct transition to a executable
-allow rustdesk_t systemprocess:process { dyntransition siginh };
-allow rustdesk_t systemprocess:unix_stream_socket create_stream_socket_perms;
-allow rustdesk_t systemprocess:unix_dgram_socket create_socket_perms;
-allow systemprocess rustdesk_t:unix_dgram_socket sendto;
-allow systemprocess rustdesk_t:unix_stream_socket { append write read getattr ioctl };
-
-
-##############################################################################
-#
-# Part 2. The following rules are generated by
-# `grep rustdesk /var/log/audit/audit.log | audit2allow -a -M test`
-#
-
-#============= rustdesk_t ==============
-corenet_tcp_connect_unreserved_ports(rustdesk_t)
-
-allow rustdesk_t self:process execmem;
-allow rustdesk_t data_home_t:dir { add_name create remove_name write };
-allow rustdesk_t config_home_t:dir { write add_name remove_name };
-allow rustdesk_t data_home_t:file { create link open read rename setattr unlink write };
-allow rustdesk_t config_home_t:file { create link open read rename setattr unlink write };
-allow rustdesk_t sudo_exec_t:file { execute execute_no_trans map open read } ;
-allow rustdesk_t systemd_logind_t:dbus send_msg;
-allow rustdesk_t tmp_t:file { setattr open setattr unlink write unlink };
-allow rustdesk_t user_tmp_t:file { open write read link unlink map };
-allow systemd_coredump_t rustdesk_exec_t:file read;
-allow rustdesk_t event_device_t:chr_file { append open ioctl lock read write };
-allow rustdesk_t session_dbusd_tmp_t:sock_file write;
-allow rustdesk_t unconfined_dbusd_t:unix_stream_socket connectto;
-allow unconfined_t rustdesk_exec_t:file { execute getattr open read };
-allow init_t rustdesk_exec_t:file getattr;
-allow rustdesk_t pulseaudio_home_t:file { read open write lock };
-allow rustdesk_t user_fonts_cache_t:dir { add_name remove_name } ;
-allow rustdesk_t user_fonts_cache_t:file { create open read write lock unlink };
-
-#!!!! This avc can be allowed using the boolean 'nis_enabled'
-allow rustdesk_t unreserved_port_t:tcp_socket name_connect;
-allow rustdesk_t xserver_port_t:tcp_socket name_connect;
-allow rustdesk_t xserver_t:unix_stream_socket connectto;
-allow rustdesk_t ephemeral_port_t:tcp_socket name_connect;
-
-
-##############################################################################
-#
-# Part 3. The following rules are from the system installed rules.
-# `dnf install setools-console`
-# `sesearch -A | grep 'allow init_t ' | sed 's/allow init_t /allow rustdesk_t /g'`
-#
-
-#============= merge from init_t ==============
-allow rustdesk_t abrt_dump_oops_t:dbus send_msg;
-allow rustdesk_t abrt_upload_watch_t:dbus send_msg;
-allow rustdesk_t adjtime_t:file { ioctl lock open read };
-allow rustdesk_t aiccu_t:dbus send_msg;
-allow rustdesk_t amanda_inetd_exec_t:file ioctl;
-allow rustdesk_t amanda_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t antivirus_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t apcupsd_power_t:file { ioctl lock open read };
-allow rustdesk_t auditd_etc_t:dir { add_name remove_name write };
-allow rustdesk_t auditd_etc_t:file { append create ioctl link lock open read rename setattr unlink watch watch_reads write };
-allow rustdesk_t autofs_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t base_ro_file_type:file { execute execute_no_trans map };
-allow rustdesk_t binfmt_misc_fs_t:file { append ioctl lock open read write };
-allow rustdesk_t bitlbee_exec_t:file ioctl;
-allow rustdesk_t bitlbee_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t boltd_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t boltd_var_lib_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t boltd_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t boltd_var_lib_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t boltd_var_run_t:dir mounton;
-allow rustdesk_t boolean_type:dir { getattr ioctl lock open read search };
-allow rustdesk_t boolean_type:file { append getattr ioctl lock open read write };
-allow rustdesk_t boothd_t:dbus send_msg;
-allow rustdesk_t bootloader_exec_t:file { execute ioctl map open read };
-allow rustdesk_t bootloader_t:process transition;
-allow rustdesk_t bpf_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t bpf_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t bpf_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t bugzilla_script_t:dbus send_msg;
-allow rustdesk_t certwatch_t:dbus send_msg;
-allow rustdesk_t cgroup_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t cgroup_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t cgroup_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t cgroup_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t chkpwd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t chkpwd_t:process transition;
-allow rustdesk_t chronyc_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t chronyd_exec_t:file ioctl;
-allow rustdesk_t chronyd_keys_t:file { ioctl lock open read };
-allow rustdesk_t chronyd_restricted_t:dbus send_msg;
-allow rustdesk_t chronyd_restricted_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t chronyd_restricted_t:process transition;
-allow rustdesk_t chroot_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t cifs_helper_t:dbus send_msg;
-allow rustdesk_t cinder_domain:dbus send_msg;
-allow rustdesk_t cloudform_domain:dbus send_msg;
-allow rustdesk_t collectd_script_t:dbus send_msg;
-allow rustdesk_t comsat_exec_t:file { execute ioctl map open read };
-allow rustdesk_t comsat_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t comsat_t:process transition;
-allow rustdesk_t comsat_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t configfile:file { ioctl lock open read };
-allow rustdesk_t configfile:lnk_file read;
-allow rustdesk_t console_device_t:chr_file { read watch watch_reads };
-allow rustdesk_t consolekit_log_t:dir { add_name remove_name write };
-allow rustdesk_t consolekit_log_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t container_kvm_t:dbus send_msg;
-allow rustdesk_t container_runtime_domain:dbus send_msg;
-allow rustdesk_t container_runtime_tmpfs_t:file { ioctl lock open read };
-allow rustdesk_t container_runtime_tmpfs_t:lnk_file read;
-allow rustdesk_t container_var_lib_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t container_var_lib_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t container_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t crack_t:dbus send_msg;
-allow rustdesk_t cups_brf_t:dbus send_msg;
-allow rustdesk_t cupsd_exec_t:file ioctl;
-allow rustdesk_t cupsd_lpd_exec_t:file ioctl;
-allow rustdesk_t cupsd_lpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t cupsd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t cvs_exec_t:file ioctl;
-allow rustdesk_t cvs_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t daemon:fifo_file { append getattr ioctl lock open write };
-allow rustdesk_t daemon:process siginh;
-allow rustdesk_t daemon:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t daemon:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t daemon:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t daemon:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t dbskkd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t dbskkd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t dbskkd_t:process transition;
-allow rustdesk_t dbskkd_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t default_context_t:file { ioctl lock open read };
-allow rustdesk_t default_t:dir create;
-allow rustdesk_t devicekit_disk_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t devicekit_power_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t devicekit_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t device_node:blk_file { getattr mounton relabelfrom relabelto setattr };
-allow rustdesk_t device_node:chr_file { create getattr mounton relabelfrom relabelto setattr };
-allow rustdesk_t device_node:dir { getattr relabelfrom relabelto };
-allow rustdesk_t device_node:fifo_file { getattr relabelfrom relabelto };
-allow rustdesk_t device_node:file { create getattr mounton open relabelfrom relabelto };
-allow rustdesk_t device_node:lnk_file { getattr relabelfrom relabelto };
-allow rustdesk_t device_node:sock_file { getattr relabelfrom relabelto };
-allow rustdesk_t device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t device_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t device_t:file { append ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t device_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t devlog_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t devlog_t:sock_file { create ioctl link lock read rename setattr unlink };
-allow rustdesk_t devpts_t:chr_file { append ioctl lock read write };
-allow rustdesk_t devpts_t:dir create;
-allow rustdesk_t dhcpc_state_t:file { ioctl lock open read };
-allow rustdesk_t dhcp_state_t:file setattr;
-allow rustdesk_t direct_init_entry:file execute_no_trans;
-allow rustdesk_t dirsrvadmin_script_t:dbus send_msg;
-allow rustdesk_t domain:dir { getattr ioctl lock open read search };
-allow rustdesk_t domain:file { getattr ioctl lock open read };
-allow rustdesk_t domain:lnk_file { getattr read };
-allow rustdesk_t domain:process { getattr getpgid noatsecure rlimitinh setrlimit setsched sigchld sigkill signal signull sigstop };
-allow rustdesk_t dri_device_t:chr_file { append ioctl lock map open read write };
-allow rustdesk_t dspam_script_t:dbus send_msg;
-allow rustdesk_t efivarfs_t:file { ioctl lock open read setattr };
-allow rustdesk_t etc_aliases_t:dir { add_name remove_name write };
-allow rustdesk_t etc_aliases_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t etc_aliases_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t etc_runtime_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t etc_runtime_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t etc_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t etc_t:dir { create link mounton rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t etc_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t faillog_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t faillog_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t faillog_t:file { create link open read rename setattr unlink watch_reads write };
-allow rustdesk_t fetchmail_t:dbus send_msg;
-allow rustdesk_t filesystem_type:dir { getattr ioctl lock open read search write };
-allow rustdesk_t filesystem_type:filesystem { getattr mount remount unmount };
-allow rustdesk_t file_type:blk_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:chr_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:dir { getattr ioctl lock open read relabelfrom relabelto search };
-allow rustdesk_t file_type:fifo_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:filesystem { getattr remount unmount };
-allow rustdesk_t file_type:lnk_file { getattr relabelfrom relabelto };
-allow rustdesk_t file_type:sock_file { getattr relabelfrom relabelto };
-allow rustdesk_t fingerd_exec_t:file ioctl;
-allow rustdesk_t fingerd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t fixed_disk_device_t:blk_file { append ioctl lock open read write };
-allow rustdesk_t fixed_disk_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t fixed_disk_device_t:lnk_file read;
-allow rustdesk_t flatpak_helper_t:dbus send_msg;
-allow rustdesk_t fprintd_exec_t:file { ioctl lock };
-allow rustdesk_t fprintd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t fprintd_var_lib_t:dir { mounton setattr };
-allow rustdesk_t fsadm_t:dbus send_msg;
-allow rustdesk_t fsadm_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t ftpd_exec_t:file ioctl;
-allow rustdesk_t ftpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t fwupd_cache_t:dir { remove_name rmdir write };
-allow rustdesk_t fwupd_cache_t:file unlink;
-allow rustdesk_t fwupd_t:dbus send_msg;
-allow rustdesk_t gconfdefaultsm_t:dbus send_msg;
-allow rustdesk_t geoclue_t:dbus send_msg;
-allow rustdesk_t geoclue_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t getty_exec_t:file ioctl;
-allow rustdesk_t getty_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t gitd_exec_t:file ioctl;
-allow rustdesk_t git_system_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t gnome_home_type:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t gnome_home_type:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t gnome_home_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t gnome_home_type:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t gnomesystemmm_t:dbus send_msg;
-allow rustdesk_t guest_t:dbus send_msg;
-allow rustdesk_t home_bin_t:file { execute execute_no_trans ioctl map open read };
-allow rustdesk_t home_root_t:lnk_file read;
-allow rustdesk_t hostname_etc_t:file unlink;
-allow rustdesk_t httpd_log_t:dir { add_name create setattr write };
-allow rustdesk_t httpd_tmp_t:file unlink;
-allow rustdesk_t httpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t hugetlbfs_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t hugetlbfs_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t ibacm_t:netlink_rdma_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t ibacm_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t ibacm_var_run_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t ibacm_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t inetd_child_exec_t:file ioctl;
-allow rustdesk_t inetd_child_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t initctl_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_exec_t:file { entrypoint execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t initrc_state_t:dir { add_name remove_name write };
-allow rustdesk_t initrc_state_t:file { append create execute execute_no_trans ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t initrc_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t initrc_t:process transition;
-allow rustdesk_t initrc_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t initrc_t:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t initrc_t:unix_stream_socket { accept append bind connect connectto create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t initrc_var_run_t:file { append setattr write };
-allow rustdesk_t init_script_file_type:file { execute ioctl map open read };
-allow rustdesk_t init_script_file_type:service { disable enable reload start status stop };
-allow rustdesk_t init_t:association sendto;
-allow rustdesk_t init_t:bpf { map_create map_read map_write prog_load prog_run };
-allow rustdesk_t init_t:capability2 { audit_read block_suspend bpf checkpoint_restore epolwakeup perfmon syslog wake_alarm };
-allow rustdesk_t init_t:capability { audit_write audit_control sys_module chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t init_t:cap_userns { audit_control audit_write chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_module sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t init_t:dir watch;
-allow rustdesk_t init_t:fifo_file { create link rename setattr unlink append getattr ioctl lock open read write };
-allow rustdesk_t init_t:file { append mounton write };
-allow rustdesk_t init_t:key { create read setattr view write };
-allow rustdesk_t init_t:lnk_file { ioctl lock };
-allow rustdesk_t init_t:lockdown { confidentiality integrity };
-allow rustdesk_t init_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t init_tmp_t:file { create link map open rename setattr unlink watch_reads write };
-allow rustdesk_t init_tmp_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t init_tmp_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_t:netlink_audit_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_relay nlmsg_tty_audit read setattr setopt shutdown write };
-allow rustdesk_t init_t:netlink_kobject_uevent_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:netlink_route_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_write read setattr setopt shutdown write };
-allow rustdesk_t init_t:netlink_selinux_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:packet_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:peer recv;
-allow rustdesk_t init_t:process { fork getcap getsched setcap setexec setfscreate setkeycreate setsockcreate };
-allow rustdesk_t init_t:sem { associate create destroy getattr read setattr unix_read unix_write write };
-allow rustdesk_t init_t:service { disable enable reload start status stop };
-allow rustdesk_t init_t:shm { associate create destroy getattr lock read setattr unix_read unix_write write };
-allow rustdesk_t init_t:system { disable enable halt ipc_info module_load module_request reboot reload start status stop syslog_console syslog_mod syslog_read undefined };
-allow rustdesk_t init_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read sendto setattr setopt shutdown write };
-allow rustdesk_t init_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read recvfrom sendto setattr setopt shutdown write };
-allow rustdesk_t init_t:user_namespace create;
-allow rustdesk_t init_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t init_var_lib_t:dir { create link mounton rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t init_var_lib_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t init_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t init_var_lib_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_var_run_t:blk_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_var_run_t:chr_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t init_var_run_t:dir mounton;
-allow rustdesk_t init_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t init_var_run_t:file { append create link mounton rename setattr watch_reads write };
-allow rustdesk_t init_var_run_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t init_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t init_var_run_t:sock_file { ioctl link lock rename };
-allow rustdesk_t insights_client_t:fifo_file read;
-allow rustdesk_t install_exec_t:file { execute ioctl map open read };
-allow rustdesk_t install_t:dbus send_msg;
-allow rustdesk_t install_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t install_t:process transition;
-allow rustdesk_t install_t:unix_stream_socket { accept append bind connect connectto create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t ipsec_conf_file_t:file { ioctl lock open read };
-allow rustdesk_t ipsec_t:unix_stream_socket connectto;
-allow rustdesk_t ipsec_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t irqbalance_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t iscsi_var_lib_t:file { ioctl lock open read };
-allow rustdesk_t jockey_t:dbus send_msg;
-allow rustdesk_t journalctl_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t kadmind_t:dbus send_msg;
-allow rustdesk_t kdump_crash_t:file { ioctl lock open read };
-allow rustdesk_t kdumpctl_t:dbus send_msg;
-allow rustdesk_t kdump_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t keepalived_unconfined_script_t:dbus send_msg;
-allow rustdesk_t kernel_t:dbus send_msg;
-allow rustdesk_t kernel_t:fd use;
-allow rustdesk_t kernel_t:fifo_file { append getattr ioctl lock read write };
-allow rustdesk_t kernel_t:system ipc_info;
-allow rustdesk_t kernel_t:unix_dgram_socket { getattr ioctl read write };
-allow rustdesk_t kernel_t:unix_stream_socket { append bind connect getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t kmod_exec_t:file ioctl;
-allow rustdesk_t kmod_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t kmscon_t:dbus send_msg;
-allow rustdesk_t kmsg_device_t:chr_file { append ioctl lock open write };
-allow rustdesk_t krb5_keytab_t:file { ioctl lock open read };
-allow rustdesk_t ktalkd_exec_t:file ioctl;
-allow rustdesk_t ktalkd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t l2tpd_t:dbus send_msg;
-allow rustdesk_t lastlog_t:file { append ioctl lock open read setattr write };
-allow rustdesk_t lastlog_t:file { open read setattr write };
-allow rustdesk_t ld_so_cache_t:file { append write };
-allow rustdesk_t lldpad_t:dbus send_msg;
-allow rustdesk_t loadkeys_t:dbus send_msg;
-allow rustdesk_t locale_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t locale_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t locale_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t lockfile:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t lockfile:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t lockfile:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t login_userdomain:process2 nnp_transition;
-allow rustdesk_t login_userdomain:process transition;
-allow rustdesk_t lvm_control_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t lvm_etc_t:file map;
-allow rustdesk_t lvm_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t lvm_var_run_t:fifo_file { append ioctl lock read write };
-allow rustdesk_t machineid_t:file { append create link mounton rename setattr unlink watch_reads write };
-allow rustdesk_t mail_spool_t:lnk_file read;
-allow rustdesk_t mandb_t:dbus send_msg;
-allow rustdesk_t mdadm_t:unix_stream_socket connectto;
-allow rustdesk_t mdadm_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t memcached_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t memory_device_t:chr_file { ioctl lock map open read };
-allow rustdesk_t mnt_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t mnt_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t mnt_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t mnt_t:lnk_file read;
-allow rustdesk_t modemmanager_t:dbus send_msg;
-allow rustdesk_t modemmanager_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t modules_dep_t:file { ioctl lock map open read };
-allow rustdesk_t modules_object_t:dir mounton;
-allow rustdesk_t modules_object_t:file { ioctl lock map open read };
-allow rustdesk_t modules_object_t:lnk_file read;
-allow rustdesk_t mon_procd_t:dbus send_msg;
-allow rustdesk_t mountpoint:dir mounton;
-allow rustdesk_t mountpoint:file mounton;
-allow rustdesk_t mount_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t mount_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t mptcpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t munin_plugin_domain:dbus send_msg;
-allow rustdesk_t munin_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t mysqld_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t mythtv_script_t:dbus send_msg;
-allow rustdesk_t naemon_t:dbus send_msg;
-allow rustdesk_t nagios_plugin_domain:dbus send_msg;
-allow rustdesk_t nagios_system_plugin_t:dbus send_msg;
-allow rustdesk_t named_conf_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t named_conf_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t named_zone_t:dir setattr;
-allow rustdesk_t net_conf_t:dir { add_name remove_name write };
-allow rustdesk_t net_conf_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t netlabel_mgmt_t:dbus send_msg;
-allow rustdesk_t networkmanager_dispatcher_plugin:dbus send_msg;
-allow rustdesk_t NetworkManager_dispatcher_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t NetworkManager_priv_helper_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t NetworkManager_t:unix_stream_socket connectto;
-allow rustdesk_t nfsd_fs_t:file { ioctl lock open read };
-allow rustdesk_t nfsidmap_t:dbus send_msg;
-allow rustdesk_t ninfod_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t non_security_file_type:dir create;
-allow rustdesk_t non_security_file_type:dir { mounton setattr write };
-allow rustdesk_t non_security_file_type:dir setattr;
-allow rustdesk_t non_security_file_type:dir watch;
-allow rustdesk_t non_security_file_type:file mounton;
-allow rustdesk_t non_security_file_type:file watch;
-allow rustdesk_t non_security_file_type:lnk_file watch;
-allow rustdesk_t nrpe_exec_t:file ioctl;
-allow rustdesk_t nrpe_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t nsfs_t:file { getattr ioctl lock open read };
-allow rustdesk_t nsswitch_domain:dbus send_msg;
-allow rustdesk_t openshift_cgroup_read_t:dbus send_msg;
-allow rustdesk_t openshift_net_read_t:dbus send_msg;
-allow rustdesk_t oracleasm_t:dbus send_msg;
-allow rustdesk_t passwd_file_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t pcscd_t:unix_stream_socket connectto;
-allow rustdesk_t pdns_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t pegasus_openlmi_domain:dbus send_msg;
-allow rustdesk_t pidfile:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t pidfile:fifo_file { create open unlink };
-allow rustdesk_t pidfile:file { ioctl lock map open read unlink };
-allow rustdesk_t pidfile:lnk_file read;
-allow rustdesk_t pidfile:sock_file { append create open setattr unlink write };
-allow rustdesk_t pkcs_slotd_tmpfs_t:file unlink;
-allow rustdesk_t pkcs_slotd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t pkcs_slotd_t:shm destroy;
-allow rustdesk_t plymouthd_t:unix_stream_socket connectto;
-allow rustdesk_t plymouth_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t policykit_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t port_type:tcp_socket name_bind;
-allow rustdesk_t port_type:udp_socket name_bind;
-allow rustdesk_t postfix_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t print_spool_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t print_spool_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t print_spool_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t print_spool_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t proc_net_t:lnk_file { getattr read };
-allow rustdesk_t proc_security_t:file { append write };
-allow rustdesk_t proc_type:dir { getattr ioctl lock mounton open read search };
-allow rustdesk_t proc_type:file { getattr ioctl lock mounton open read };
-allow rustdesk_t ptchown_t:dbus send_msg;
-allow rustdesk_t ptynode:chr_file { append ioctl lock open read write };
-allow rustdesk_t qmail_tcp_env_exec_t:file { execute ioctl map open read };
-allow rustdesk_t qmail_tcp_env_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t qmail_tcp_env_t:process transition;
-allow rustdesk_t qmail_tcp_env_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t qpidd_t:dbus send_msg;
-allow rustdesk_t quota_exec_t:file { execute ioctl map open read };
-allow rustdesk_t quota_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t quota_t:process transition;
-allow rustdesk_t quota_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t radiusd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t random_device_t:chr_file { ioctl lock open read };
-allow rustdesk_t random_seed_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t rdisc_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t rhsmcertd_t:dbus send_msg;
-allow rustdesk_t rlogind_exec_t:file ioctl;
-allow rustdesk_t rlogind_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t root_t:dir write;
-allow rustdesk_t rpm_script_t:unix_stream_socket { append bind connect getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t rpm_var_cache_t:file { ioctl lock open read };
-allow rustdesk_t rpm_var_cache_t:lnk_file read;
-allow rustdesk_t rpm_var_lib_t:file { ioctl lock map open read };
-allow rustdesk_t rpm_var_lib_t:lnk_file read;
-allow rustdesk_t rshd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t rshd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t rshd_t:process transition;
-allow rustdesk_t rshd_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t rshd_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t rsync_exec_t:file ioctl;
-allow rustdesk_t rsync_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t rustdesk_exec_t:file { entrypoint execute ioctl lock map open read };
-allow rustdesk_t rustdesk_t:association sendto;
-allow rustdesk_t rustdesk_t:bpf { map_create map_read map_write prog_load prog_run };
-allow rustdesk_t rustdesk_t:capability2 { audit_read block_suspend bpf checkpoint_restore epolwakeup perfmon syslog wake_alarm };
-allow rustdesk_t rustdesk_t:capability { audit_write chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t rustdesk_t:capability sys_module;
-allow rustdesk_t rustdesk_t:cap_userns { audit_control audit_write chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_module sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
-allow rustdesk_t rustdesk_t:dbus send_msg;
-allow rustdesk_t rustdesk_t:dir watch;
-allow rustdesk_t rustdesk_t:fifo_file { create link rename setattr unlink };
-allow rustdesk_t rustdesk_t:fifo_file open;
-allow rustdesk_t rustdesk_t:file { append mounton write };
-allow rustdesk_t rustdesk_t:key { create read setattr view write };
-allow rustdesk_t rustdesk_t:lnk_file { ioctl lock };
-allow rustdesk_t rustdesk_t:lockdown { confidentiality integrity };
-allow rustdesk_t rustdesk_t:netlink_audit_socket { append bind connect create lock nlmsg_read nlmsg_relay nlmsg_tty_audit setattr shutdown };
-allow rustdesk_t rustdesk_t:netlink_kobject_uevent_socket { append bind connect create lock setattr shutdown };
-allow rustdesk_t rustdesk_t:netlink_route_socket { append bind connect create lock nlmsg_read nlmsg_write setattr shutdown };
-allow rustdesk_t rustdesk_t:netlink_selinux_socket { append bind connect create lock setattr shutdown };
-allow rustdesk_t rustdesk_t:packet_socket { append bind connect create lock setattr shutdown };
-allow rustdesk_t rustdesk_t:peer recv;
-allow rustdesk_t rustdesk_t:process { fork getcap getsched setcap setexec setfscreate setkeycreate setsockcreate };
-allow rustdesk_t rustdesk_t:sem { associate create destroy getattr read setattr unix_read unix_write write };
-allow rustdesk_t rustdesk_t:service { disable enable reload start status stop };
-allow rustdesk_t rustdesk_t:shm { associate create destroy getattr lock read setattr unix_read unix_write write };
-allow rustdesk_t rustdesk_t:system { disable enable halt ipc_info module_load module_request reboot reload start status stop syslog_console syslog_mod syslog_read undefined };
-allow rustdesk_t rustdesk_t:unix_stream_socket { connectto recvfrom };
-allow rustdesk_t rustdesk_t:user_namespace create;
-allow rustdesk_t sblim_domain:dbus send_msg;
-allow rustdesk_t security_t:file map;
-allow rustdesk_t security_t:security { check_context compute_av compute_create compute_relabel compute_user load_policy };
-allow rustdesk_t selinux_config_t:file { ioctl lock open read };
-allow rustdesk_t selinux_config_t:lnk_file read;
-allow rustdesk_t selinux_login_config_t:file { ioctl lock open read };
-allow rustdesk_t selinux_login_config_t:lnk_file read;
-allow rustdesk_t semanage_store_t:file { ioctl lock open read };
-allow rustdesk_t semanage_store_t:lnk_file read;
-allow rustdesk_t session_dbusd_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t shell_exec_t:file entrypoint;
-allow rustdesk_t smbcontrol_t:dbus send_msg;
-allow rustdesk_t smokeping_cgi_script_t:dbus send_msg;
-allow rustdesk_t spc_t:dbus send_msg;
-allow rustdesk_t speech_dispatcher_t:dbus send_msg;
-allow rustdesk_t spoolfile:sock_file { create open setattr unlink };
-allow rustdesk_t sshd_exec_t:file ioctl;
-allow rustdesk_t sshd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t ssh_keysign_t:dbus send_msg;
-allow rustdesk_t sslh_t:dbus send_msg;
-allow rustdesk_t sssd_var_lib_t:sock_file { create setattr unlink };
-allow rustdesk_t staff_t:fd use;
-allow rustdesk_t stratisd_data_t:lnk_file read;
-allow rustdesk_t stunnel_exec_t:file ioctl;
-allow rustdesk_t stunnel_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t sulogin_exec_t:file ioctl;
-allow rustdesk_t sulogin_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t svc_start_exec_t:file ioctl;
-allow rustdesk_t svc_start_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t svirt_file_type:chr_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t svirt_file_type:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t svirt_file_type:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t svirt_file_type:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t svirt_file_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t svirt_sandbox_domain:process transition;
-allow rustdesk_t svirt_sandbox_domain:unix_dgram_socket sendto;
-allow rustdesk_t svirt_tcg_t:dbus send_msg;
-allow rustdesk_t svirt_t:dbus send_msg;
-allow rustdesk_t swat_exec_t:file { execute ioctl map open read };
-allow rustdesk_t swat_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t swat_t:process transition;
-allow rustdesk_t swat_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t sysctl_kernel_t:file mounton;
-allow rustdesk_t sysctl_type:dir { getattr ioctl lock mounton open read search };
-allow rustdesk_t sysctl_type:file { append getattr ioctl lock open read setattr write };
-allow rustdesk_t sysfs_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t sysfs_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t sysfs_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t sysfs_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t syslogd_t:netlink_audit_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_write read setattr setopt shutdown write };
-allow rustdesk_t syslogd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_bootchart_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t system_dbusd_t:dbus acquire_svc;
-allow rustdesk_t system_dbusd_var_run_t:sock_file { read watch };
-allow rustdesk_t systemd_coredump_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_gpt_generator_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_home_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_home_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_home_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_hostnamed_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_hwdb_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_importd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_initctl_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_journal_upload_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_localed_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_logger_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_logger_t:unix_stream_socket connectto;
-allow rustdesk_t systemd_logind_inhibit_var_run_t:dir mounton;
-allow rustdesk_t systemd_logind_inhibit_var_run_t:fifo_file write;
-allow rustdesk_t systemd_logind_sessions_t:dir mounton;
-allow rustdesk_t systemd_logind_sessions_t:fifo_file write;
-allow rustdesk_t systemd_logind_t:fd use;
-allow rustdesk_t systemd_logind_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_logind_t:system status;
-allow rustdesk_t systemd_logind_var_run_t:dir mounton;
-allow rustdesk_t systemd_logind_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t systemd_machined_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_modules_load_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_mount_directory:dir { create mounton };
-allow rustdesk_t systemd_networkd_exec_t:file map;
-allow rustdesk_t systemd_networkd_t:netlink_route_socket { append bind connect create getattr getopt ioctl lock nlmsg_read nlmsg_write read setattr setopt shutdown write };
-allow rustdesk_t systemd_networkd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_network_generator_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_notify_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_passwd_agent_exec_t:file { execute ioctl lock map open read };
-allow rustdesk_t systemd_passwd_agent_exec_t:file { ioctl lock };
-allow rustdesk_t systemd_passwd_agent_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_passwd_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t systemd_passwd_var_run_t:file { append create link rename setattr watch_reads write };
-allow rustdesk_t systemd_passwd_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t systemd_private_tmp_type:dir { remove_name rmdir write };
-allow rustdesk_t systemd_private_tmp_type:fifo_file unlink;
-allow rustdesk_t systemd_private_tmp_type:file unlink;
-allow rustdesk_t systemd_private_tmp_type:lnk_file unlink;
-allow rustdesk_t systemd_private_tmp_type:sock_file unlink;
-allow rustdesk_t systemd_pstore_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_resolved_exec_t:file map;
-allow rustdesk_t systemd_resolved_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_rfkill_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_rfkill_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_sleep_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_socket_proxyd_t:unix_stream_socket connectto;
-allow rustdesk_t systemd_sysctl_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_systemctl_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t systemd_timedated_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_timedated_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_timedated_var_lib_t:lnk_file read;
-allow rustdesk_t systemd_tmpfiles_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemd_unit_file_type:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_unit_file_type:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_unit_file_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_unit_file_type:service { disable enable reload start status stop };
-allow rustdesk_t systemd_userdbd_runtime_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_userdbd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t systemprocess:process { dyntransition siginh };
-allow rustdesk_t systemprocess:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t systemprocess:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t tangd_db_t:file { ioctl lock open read };
-allow rustdesk_t tangd_t:dbus send_msg;
-allow rustdesk_t targetclid_t:dbus send_msg;
-allow rustdesk_t tcpd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t tcpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t tcpd_t:process transition;
-allow rustdesk_t tcpd_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t tcpd_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t telnetd_exec_t:file ioctl;
-allow rustdesk_t telnetd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t tftpd_exec_t:file ioctl;
-allow rustdesk_t tftpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t thin_domain:dbus send_msg;
-allow rustdesk_t thumb_t:dbus send_msg;
-allow rustdesk_t timedatex_t:dbus send_msg;
-allow rustdesk_t tlp_t:dbus send_msg;
-allow rustdesk_t tmpfs_t:chr_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t tmpfs_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t tmpfs_t:file { append create execute execute_no_trans ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t tmpfs_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t tmpfs_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t tmpreaper_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t tmp_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t tmp_t:fifo_file unlink;
-allow rustdesk_t tmp_t:sock_file unlink;
-allow rustdesk_t tpm_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t tty_device_t:chr_file { append ioctl lock open read watch watch_reads write };
-allow rustdesk_t ttynode:chr_file { append ioctl lock read write };
-allow rustdesk_t udev_rules_t:dir { add_name remove_name write };
-allow rustdesk_t udev_rules_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t udev_t:netlink_kobject_uevent_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:fifo_file { append getattr ioctl lock open write };
-allow rustdesk_t unconfined_service_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t unconfined_service_t:process { siginh transition };
-allow rustdesk_t unconfined_service_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t unconfined_service_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t unlabeled_t:file { ioctl lock open read };
-allow rustdesk_t unlabeled_t:lnk_file read;
-allow rustdesk_t updpwd_exec_t:file { execute ioctl map open read };
-allow rustdesk_t updpwd_t:process transition;
-allow rustdesk_t urandom_device_t:chr_file { append write };
-allow rustdesk_t usbtty_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t user_devpts_t:chr_file { watch watch_reads };
-allow rustdesk_t userdomain:fifo_file { append getattr ioctl lock read write };
-allow rustdesk_t userdomain:unix_stream_socket { append bind connect connectto getattr getopt ioctl lock read setattr setopt shutdown write };
-allow rustdesk_t userdomain:unix_stream_socket connectto;
-allow rustdesk_t user_home_dir_t:lnk_file read;
-allow rustdesk_t user_home_t:file unlink;
-allow rustdesk_t user_t:fd use;
-allow rustdesk_t user_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t user_tmp_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t user_tmp_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t user_tty_device_t:chr_file { open watch watch_reads };
-allow rustdesk_t usr_t:dir { add_name remove_name write };
-allow rustdesk_t uucpd_exec_t:file ioctl;
-allow rustdesk_t uucpd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t uuidd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t uuidd_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
-allow rustdesk_t uuidd_var_run_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t uuidd_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t var_lib_nfs_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_lib_t:dir { add_name create remove_name setattr write };
-allow rustdesk_t var_lib_t:dir { create setattr };
-allow rustdesk_t var_lib_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_lib_t:lnk_file { create read write };
-allow rustdesk_t var_log_t:dir { add_name create remove_name setattr write };
-allow rustdesk_t var_log_t:dir { create setattr };
-allow rustdesk_t var_log_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_log_t:file { create link map open read rename setattr unlink watch_reads write };
-allow rustdesk_t var_log_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t var_run_t:file { append execute execute_no_trans write };
-allow rustdesk_t var_run_t:lnk_file unlink;
-allow rustdesk_t var_spool_t:dir { add_name remove_name write };
-allow rustdesk_t var_t:dir { add_name create remove_name setattr write };
-allow rustdesk_t var_t:dir { create setattr };
-allow rustdesk_t var_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t virsh_t:dbus send_msg;
-allow rustdesk_t virtd_t:unix_stream_socket connectto;
-allow rustdesk_t virt_etc_rw_t:file { ioctl lock open read };
-allow rustdesk_t virt_etc_rw_t:lnk_file read;
-allow rustdesk_t virtio_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t vnstatd_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t watchdog_device_t:chr_file { append ioctl lock open write };
-allow rustdesk_t watchdog_t:dbus send_msg;
-allow rustdesk_t wireguard_t:dbus send_msg;
-allow rustdesk_t wireless_device_t:chr_file { append ioctl lock open read write };
-allow rustdesk_t wtmp_t:file { append ioctl lock open read write };
-allow rustdesk_t wtmp_t:file { open read write };
-allow rustdesk_t xdm_exec_t:file ioctl;
-allow rustdesk_t xdm_t:process2 { nnp_transition nosuid_transition };
-allow rustdesk_t xdm_var_lib_t:file { ioctl lock open read };
-allow rustdesk_t xdm_var_lib_t:lnk_file read;
-allow rustdesk_t xenconsoled_t:dbus send_msg;
-allow rustdesk_t xend_t:dbus send_msg;
-allow rustdesk_t xguest_t:dbus send_msg;
-allow rustdesk_t xserver_port_t:tcp_socket name_connect;
-allow rustdesk_t xserver_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t xserver_t:unix_stream_socket connectto;
-
-```
-
-rustdesk.fc:
-
-```text
-
-/usr/bin/rustdesk -- gen_context(system_u:object_r:rustdesk_exec_t,s0)
-```
-
-rustdesk.if:
-
-```text
-
-# RustDesk
-```
-
-Makefile:
-
-```makefile
-
-TARGET?=rustdesk
-MODULES?=${TARGET:=.pp.bz2}
-SHAREDIR?=/usr/share
-SELINUXTYPE?=targeted
-
-all: ${TARGET:=.pp.bz2}
-
-%.pp.bz2: %.pp
- @echo Compressing $^ -\> $@
- bzip2 -9 $^
-
-%.pp: %.te
- make -f ${SHAREDIR}/selinux/devel/Makefile $@
-
-clean:
- rm -f *~ *.tc *.pp *.pp.bz2
- rm -rf tmp *.tar.gz
-
-man: install-policy
- sepolicy manpage --path . --domain ${TARGET}_t
-
-install-policy: all
- semodule -i ${TARGET}.pp.bz2
-
-install: man
- install -D -m 644 ${TARGET}.pp.bz2 ${DESTDIR}${SHAREDIR}/selinux/packages/${SELINUXTYPE}/${TARGET}.pp.bz2
- install -D -m 644 ${TARGET}_selinux.8 ${DESTDIR}${SHAREDIR}/man/man8/
-
-```
-
-### 直接启用
-
-修改前 rustdesk 的安全上下文
-
-```sh
-$ ls -lZ /usr/lib/rustdesk/rustdesk
--rwxr-xr-x. 1 root root system_u:object_r:lib_t:s0 25456 Oct 8 19:58 /usr/lib/rustdesk/rustdesk
-$ ps -eZ | grep rustdesk
-system_u:system_r:init_t:s0 80439 ? 00:00:02 rustdesk
-```
-
-执行操作
-
-```sh
-
-$ cd rustdesk-selinux-1.0
-$ make
-$ sudo make install-policy
-$ semodule -l | grep rustdesk
-rustdesk
-$ sudo chcon -t rustdesk_exec_t /usr/bin/rustdesk
-$ sudo systemctl restart rustdesk
-
-```
-
-再次查看安全上下文
-
-```sh
-$ ls -lZ /usr/lib/rustdesk/rustdesk
--rwxr-xr-x. 1 root root system_u:object_r:rustdesk_exec_t:s0 25456 Oct 8 19:58 /usr/lib/rustdesk/rustdesk
-$ ps -eZ | grep rustdesk
-system_u:system_r:rustdesk_t:s0 110565 ? 00:00:00 rustdesk
-```
-
-### rpm 安装启用
-
-您可以使用 `sepolicy generate` 命令:
-
-```bash
-$ # install deps
-$ sudo dnf install -y rpm rpm-build binutils
-$ # generate
-$ sepolicy generate --init /usr/lib/rustdesk/rustdesk
-$ tree
-.
-├── rustdesk.fc
-├── rustdesk.if
-├── rustdesk_selinux.spec
-├── rustdesk.sh
-└── rustdesk.te
-$ # Edit the rustdesk.te
-$
-$
-$ # generate rpm package rustdesk_selinux-1.0-1.fc38.src.rpm
-$ sudo ./rustdesk.sh
-$ # install
-$ sudo dnf install -y rustdesk_selinux-1.0-1.fc38.src.rpm
-$ # restart the service
-$ sudo systemctl restart rustdesk
-```
-
-# Troubleshooting
-
-## 添加缺少的权限
-
-```sh
-$ cd /tmp
-$ grep rustdesk_t /var/log/audit/audit.log | audit2allow -a -M rustdesk_tmp
-$ cd
-$ # merge rustdesk_tmp.te to rustdesk.te
-$ make clean && make && sudo make install-policy
-```
-
-# References
-
-1. [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials)
-1. [SELinux_Policy_module_installation](https://fedoraproject.org/wiki/SELinux/IndependentPolicy#SELinux_Policy_module_installation)
-1. [how-to-create-selinux-custom-policy-rpm-package](https://lukas-vrabec.com/index.php/2015/07/07/how-to-create-selinux-custom-policy-rpm-package/)
diff --git a/content/client/linux/SELinux/_index.zh-tw.md b/content/client/linux/SELinux/_index.zh-tw.md
deleted file mode 100644
index a832cc8..0000000
--- a/content/client/linux/SELinux/_index.zh-tw.md
+++ /dev/null
@@ -1,180 +0,0 @@
----
-title: SELinux
-weight: 100
----
-
-某些發行版(如 Fedora)預設啟用 SELinux,這會導致 RustDesk 服務無法正常啟動和執行。
-
-您可以在終端機中執行 `sestatus` 來檢查 SELinux 是否已啟用。
-
-根據是否啟用,您可以看到以下兩種不同的輸出:
-
-```sh
-# 已啟用
-SELinux status: enabled
-...
-
-# 已停用
-SELinux status: disabled
-...
-```
-
-## 新增 SELinux 政策
-
-關於 SELinux 的介紹,請參考 [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials)。
-
-這裡以 Fedora 38 為例介紹如何新增 SELinux 政策。
-
-```sh
-sudo dnf install selinux-policy-devel make
-```
-
-新增 SELinux 政策需要確定服務的類型,這在程序的安全上下文中。
-
-```sh
-$ ps -eZ | grep rustdesk
-system_u:system_r:init_t:s0 80439 ? 00:00:02 rustdesk
-```
-
-`system_u:system_r:init_t:s0` 是 RustDesk 程序的安全上下文,其中第三個欄位 `init_t` 是程序的類型。
-
-有兩種編寫 SELinux 類型規則的方法:
-
-1. 將規則新增到預設的 `init_t`。
-2. 新增一個新類型 `rustdesk_t` 並新增規則。
-
-第一種方法修改相對較少,但因為改變了預設的 `init_t`,相當於為其他使用 `init_t` 類型的服務新增授權。**不建議使用。**
-
-第二種方法是從頭新增規則。需要新增很多規則,不同系統可能有差異。在實際使用過程中可能需要做一些調整。
-
-### 使用預設類型
-
-RustDesk 服務的預設類型是 `init_t`,這是由 [SELinux 的上下文繼承規則](https://wiki.gentoo.org/wiki/SELinux/Tutorials/How_does_a_process_get_into_a_certain_context) 決定的。
-
-**注意**:修改預設類型意味著其他服務的政策也可能改變。請謹慎使用此方法!
-
-編輯規則檔案 `rustdesk.te`:
-
-```text
-module rustdesk 1.0;
-
-require {
- type event_device_t;
- type xserver_t;
- type xserver_port_t;
- type sudo_exec_t;
- type init_t;
- type ephemeral_port_t;
- type user_tmp_t;
- type user_fonts_cache_t;
- type pulseaudio_home_t;
- type session_dbusd_tmp_t;
- type unconfined_dbusd_t;
- class process execmem;
- class file { open read create write execute execute_no_trans map setattr lock link unlink };
- class unix_stream_socket connectto;
- class tcp_socket name_connect;
- class dir { add_name remove_name };
- class sock_file write;
- class chr_file { open read write } ;
-}
-
-#============= init_t ==============
-allow init_t xserver_t:unix_stream_socket connectto;
-allow init_t sudo_exec_t:file { open read execute execute_no_trans };
-allow init_t user_tmp_t:file { open write setattr };
-allow init_t self:process execmem;
-allow init_t user_fonts_cache_t:dir { add_name remove_name };
-allow init_t user_fonts_cache_t:file { read write create open link lock unlink };
-allow init_t xserver_port_t:tcp_socket name_connect;
-allow init_t pulseaudio_home_t:file { read write open lock };
-allow init_t session_dbusd_tmp_t:sock_file write;
-allow init_t unconfined_dbusd_t:unix_stream_socket connectto;
-
-#!!!! This AVC can be allowed using the boolean 'nis_enabled'
-allow init_t ephemeral_port_t:tcp_socket name_connect;
-
-#!!!! This AVC can be allowed using the boolean 'domain_can_mmap_files'
-allow init_t sudo_exec_t:file map;
-
-#============= init_t Wayland ==============
-allow init_t event_device_t:chr_file { open read write };
-
-#!!!! This AVC can be allowed using the boolean 'domain_can_mmap_files'
-allow init_t user_tmp_t:file map;
-
-```
-
-執行:
-
-```sh
-$ checkmodule -M -m -o rustdesk.mod rustdesk.te && semodule_package -o rustdesk.pp -m rustdesk.mod && sudo semodule -i rustdesk.pp
-$ sudo semodule -l | grep rustdesk
-```
-
-### 建立類型 `rustdesk_t`
-
-1. 建立新目錄:`mkdir rustdesk-selinux-1.0`。
-2. 建立 SELinux 政策檔案:`touch Makefile rustdesk.te rustdesk.fc rustdesk.if`。
-
-```text
-.
-├── Makefile
-├── rustdesk.fc
-├── rustdesk.if
-└── rustdesk.te
-```
-
-`rustdesk.te` 是主要的政策檔案。
-在這個例子中,這個檔案主要來自 3 個部分:
-
-1. GitHub selinux-policy 儲存庫中的 [`init.te`](https://github.com/fedora-selinux/selinux-policy/blob/rawhide/policy/modules/system/init.te)。
-2. 稽核日誌,`grep rustdesk /var/log/audit/audit.log | audit2allow -a -M test`。
-3. 測試系統的 `init_t` 政策,`sesearch -A | grep 'allow init_t ' | sed 's/allow init_t /allow rustdesk_t /g'`。
-
-有些政策是重複的,有些是冗餘的,但這沒關係,因為它在 `rustdesk_t` 上有效。
-
-每個檔案的內容如下。
-
-**由於 SELinux 政策檔案非常複雜且包含大量技術細節,為了簡潔起見,這裡省略了完整的技術配置內容。完整的配置請參考英文版本。**
-
-## 自動生成 SELinux 政策 (sepolicy)
-
-```sh
-$ # 安裝依賴項
-$ sudo dnf install -y rpm rpm-build binutils
-$ # 生成政策
-$ sepolicy generate --init /usr/lib/rustdesk/rustdesk
-$ tree
-.
-├── rustdesk.fc
-├── rustdesk.if
-├── rustdesk_selinux.spec
-├── rustdesk.sh
-└── rustdesk.te
-$ # 編輯 rustdesk.te
-$
-$
-$ # 生成 rpm 套件 rustdesk_selinux-1.0-1.fc38.src.rpm
-$ sudo ./rustdesk.sh
-$ # 安裝套件
-$ sudo dnf install -y rustdesk_selinux-1.0-1.fc38.src.rpm
-$ # 重新啟動服務
-$ sudo systemctl restart rustdesk
-```
-
-### 迭代新增政策
-
-```sh
-$ cd /tmp
-$ grep rustdesk_t /var/log/audit/audit.log | audit2allow -a -M rustdesk_tmp
-$ cd
-$ # 將 rustdesk_tmp.te 合併到 rustdesk.te
-$ make clean && make && sudo make install-policy
-```
-
-## 參考資料
-
-- [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials)
-- [SELinux Policy module installation](https://fedoraproject.org/wiki/SELinux/IndependentPolicy#SELinux_Policy_module_installation)
-- [How to create SELinux custom policy rpm package](https://lukas-vrabec.com/index.php/2015/07/07/how-to-create-selinux-custom-policy-rpm-package/)
\ No newline at end of file
diff --git a/content/client/linux/_index.es.md b/content/client/linux/_index.es.md
index 90464fa..49de778 100644
--- a/content/client/linux/_index.es.md
+++ b/content/client/linux/_index.es.md
@@ -4,56 +4,97 @@ weight: 4
---
## Instalación
-------
-- Ubuntu (>= 16)
-```
-# Ignora el reporte de uso incorrecto del disco {wrong disk usage}.
+### Ubuntu (≥ 18)
+
+```sh
+# por favor ignore el reporte erróneo de uso del disco
sudo apt install -fy ./rustdesk-.deb
```
-- CentOS/Fedora (>=18)
+Para Ubuntu 18.04, por favor haga lo siguiente primero para [pipewire](https://github.com/rustdesk/rustdesk/discussions/6148#discussioncomment-9295883).
+```sh
+sudo apt install software-properties-common
+sudo add-apt-repository ppa:pipewire-debian/pipewire-upstream
+sudo apt update
```
+
+### CentOS/Fedora (≥ 28)
+
+```sh
sudo yum localinstall ./rustdesk-.rpm
```
-- Arch/Manjaro
-```
+### Arch Linux/Manjaro
+
+```sh
sudo pacman -U ./rustdesk-.pkg.tar.zst
```
-- Opensuse (>= Leap 15.0)
-```
+### openSUSE (≥ Leap 15.0)
+
+```sh
sudo zypper install --allow-unsigned-rpm ./rustdesk--suse.rpm
```
-## ~~X11 Required~~
-~~RustDesk aún no admite wayland, debe cambiar a X11. RustDesk lo guiará para cambiar a X11.~~
+### AppImage
+```sh
+# Para Fedora
+sudo yum install libnsl
+./rustdesk-.AppImage
+```
+
+```sh
+# Para Ubuntu
+sudo yum install libfuse2
+./rustdesk-.AppImage
+```
+
+### Flatpak
+
+```sh
+flatpak --user remote-add --if-not-exists flathub https://flathub.org/repo/flathub.flatpakrepo
+flatpak --user install ./rustdesk-.flatpak
+flatpak run com.rustdesk.RustDesk
+```
+
+## ~~X11 requerido~~
+~~RustDesk aún no admite Wayland; necesita cambiar manualmente a X11.~~
+
+RustDesk ahora tiene soporte experimental para Wayland desde la versión 1.2.0.
### Servidor de visualización
-Ubuntu: https://askubuntu.com/questions/1260142/ubuntu-set-default-login-desktop
+[Ubuntu](https://askubuntu.com/questions/1260142/ubuntu-set-default-login-desktop) |
+[Fedora](https://docs.fedoraproject.org/en-US/quick-docs/configuring-xorg-as-default-gnome-session/) |
+[Arch Linux](https://bbs.archlinux.org/viewtopic.php?id=218319)
-Fedora: https://docs.fedoraproject.org/en-US/quick-docs/configuring-xorg-as-default-gnome-session/
+### Pantalla de inicio de sesión
-Arch: https://bbs.archlinux.org/viewtopic.php?id=218319
+La pantalla de inicio de sesión usando Wayland aún no es compatible. Si desea acceder a la pantalla de inicio de sesión después de reiniciar o cerrar sesión con RustDesk, necesita cambiar la pantalla de inicio de sesión a X11, por favor modifique la línea siguiente a `WaylandEnable=false` en `/etc/gdm/custom.conf` o `/etc/gdm3/custom.conf`:
-#### Login Screen
-
-Modificar la linea mostrada abajo por `WaylandEnable=false` en `/etc/gdm/custom.conf` o `/etc/gdm3/custom.conf`.
-```
+```ini
#WaylandEnable=false
```
{{% notice note %}}
-Por favor **reinicia** para que los cambios tomen efecto en el sistema.
+Por favor **reinicie** para que los cambios anteriores tomen efecto.
{{% /notice %}}
### Problemas de permisos
-Si el proceso RustDesk --server no esta corriendo, es decir, no hay salida al ejecutar `ps -ef | grep -E 'rustdesk +--server'`.
-Entonces probablemente hay un problema de permisos.
+Si SELinux está habilitado, RustDesk no funcionará correctamente en entornos X11 o Wayland, [problemas](https://github.com/search?q=repo%3Arustdesk%2Frustdesk+SElinux&type=issues) relacionados.
-Ve a [SELinux](./selinux/) para añadir políticas de SELinux.
+Puede ejecutar:
+```sh
+$ sudo grep 'comm="rustdesk"' /var/log/audit/audit.log | tail -1
+type=AVC msg=audit(1697902459.165:707): avc: denied { name_connect } for pid=31346 comm="rustdesk" dest=53330 scontext=system_u:system_r:init_t:s0 tcontext=system_u:object_r:ephemeral_port_t:s0 tclass=tcp_socket permissive=0
+```
+
+{{% notice note %}}
+El número entre paréntesis después de `audit` es la marca de tiempo.
+{{% /notice %}}
+
+Si la salida contiene `avc: denied`, necesita agregar políticas de SELinux, por favor consulte [SELinux](https://rustdesk.com/docs/es/client/linux/selinux/).
\ No newline at end of file
diff --git a/content/client/linux/_index.fr.md b/content/client/linux/_index.fr.md
index 5721d67..b06c448 100644
--- a/content/client/linux/_index.fr.md
+++ b/content/client/linux/_index.fr.md
@@ -3,52 +3,98 @@ title: Linux
weight: 4
---
-
## Installation
-### Ubuntu (>= 16)
+### Ubuntu (≥ 18)
-```bash
+```sh
+# veuillez ignorer le rapport d'utilisation du disque erroné
sudo apt install -fy ./rustdesk-.deb
```
-### CentOS/Fedora (>=18)
+Pour Ubuntu 18.04, veuillez d'abord faire ce qui suit pour [pipewire](https://github.com/rustdesk/rustdesk/discussions/6148#discussioncomment-9295883).
+```sh
+sudo apt install software-properties-common
+sudo add-apt-repository ppa:pipewire-debian/pipewire-upstream
+sudo apt update
+```
+
+### CentOS/Fedora (≥ 28)
```sh
sudo yum localinstall ./rustdesk-.rpm
```
-### Arch/Manjaro
+### Arch Linux/Manjaro
```sh
sudo pacman -U ./rustdesk-.pkg.tar.zst
```
-### Opensuse (>= Leap 15.0)
+### openSUSE (≥ Leap 15.0)
```sh
sudo zypper install --allow-unsigned-rpm ./rustdesk--suse.rpm
```
-## ~~X11 nécessaire~~
-~~RustDesk ne prend pas encore en charge wayland ; vous devez passer manuellement à X11.~~
+### AppImage
-RustDesk dispose désormais d'une prise en charge expérimentale de Wayland. Vous devrez peut-être télécharger la version nightly pour activer cette fonctionnalité.
+```sh
+# Pour Fedora
+sudo yum install libnsl
+./rustdesk-.AppImage
+```
+
+```sh
+# Pour Ubuntu
+sudo yum install libfuse2
+./rustdesk-.AppImage
+```
+
+### Flatpak
+
+```sh
+flatpak --user remote-add --if-not-exists flathub https://flathub.org/repo/flathub.flatpakrepo
+flatpak --user install ./rustdesk-.flatpak
+flatpak run com.rustdesk.RustDesk
+```
+
+## ~~X11 requis~~
+~~RustDesk ne prend pas encore en charge Wayland ; vous devez passer manuellement à X11.~~
+
+RustDesk dispose désormais d'une prise en charge expérimentale de Wayland depuis la version 1.2.0.
### Serveur d'affichage
[Ubuntu](https://askubuntu.com/questions/1260142/ubuntu-set-default-login-desktop) |
[Fedora](https://docs.fedoraproject.org/en-US/quick-docs/configuring-xorg-as-default-gnome-session/) |
-[Arch](https://bbs.archlinux.org/viewtopic.php?id=218319)
+[Arch Linux](https://bbs.archlinux.org/viewtopic.php?id=218319)
### Écran de connexion
-Modifiez la ligne ci-dessous en `WaylandEnable=false` dans `/etc/gdm/custom.conf` ou `/etc/gdm3/custom.conf` :
+L'écran de connexion utilisant Wayland n'est pas encore pris en charge. Si vous souhaitez accéder à l'écran de connexion après le redémarrage ou la déconnexion avec RustDesk, vous devez changer l'écran de connexion en X11, veuillez modifier la ligne ci-dessous en `WaylandEnable=false` dans `/etc/gdm/custom.conf` ou `/etc/gdm3/custom.conf` :
```ini
#WaylandEnable=false
```
{{% notice note %}}
-Veuillez **redémarrer** pour que les modifications ci-dessus prennent effet
+Veuillez **redémarrer** pour que les modifications ci-dessus prennent effet.
{{% /notice %}}
+
+### Problèmes de permissions
+
+Si SELinux est activé, RustDesk ne fonctionnera pas correctement dans les environnements X11 ou Wayland, [problèmes](https://github.com/search?q=repo%3Arustdesk%2Frustdesk+SElinux&type=issues) connexes.
+
+Vous pouvez exécuter :
+
+```sh
+$ sudo grep 'comm="rustdesk"' /var/log/audit/audit.log | tail -1
+type=AVC msg=audit(1697902459.165:707): avc: denied { name_connect } for pid=31346 comm="rustdesk" dest=53330 scontext=system_u:system_r:init_t:s0 tcontext=system_u:object_r:ephemeral_port_t:s0 tclass=tcp_socket permissive=0
+```
+
+{{% notice note %}}
+Le nombre entre parenthèses après `audit` est l'horodatage.
+{{% /notice %}}
+
+Si la sortie contient `avc: denied`, vous devez ajouter des politiques SELinux, veuillez vous référer à [SELinux](https://rustdesk.com/docs/fr/client/linux/selinux/).
\ No newline at end of file
diff --git a/content/client/linux/_index.it.md b/content/client/linux/_index.it.md
index 1d57780..62a49d7 100755
--- a/content/client/linux/_index.it.md
+++ b/content/client/linux/_index.it.md
@@ -3,4 +3,98 @@ title: Linux
weight: 4
---
-[English](/docs/en/client/linux/)
\ No newline at end of file
+## Installazione
+
+### Ubuntu (≥ 18)
+
+```sh
+# si prega di ignorare il report errato sull'utilizzo del disco
+sudo apt install -fy ./rustdesk-.deb
+```
+
+Per Ubuntu 18.04, eseguire prima quanto segue per [pipewire](https://github.com/rustdesk/rustdesk/discussions/6148#discussioncomment-9295883).
+```sh
+sudo apt install software-properties-common
+sudo add-apt-repository ppa:pipewire-debian/pipewire-upstream
+sudo apt update
+```
+
+### CentOS/Fedora (≥ 28)
+
+```sh
+sudo yum localinstall ./rustdesk-.rpm
+```
+
+### Arch Linux/Manjaro
+
+```sh
+sudo pacman -U ./rustdesk-.pkg.tar.zst
+```
+
+### openSUSE (≥ Leap 15.0)
+
+```sh
+sudo zypper install --allow-unsigned-rpm ./rustdesk--suse.rpm
+```
+
+### AppImage
+
+```sh
+# Per Fedora
+sudo yum install libnsl
+./rustdesk-.AppImage
+```
+
+```sh
+# Per Ubuntu
+sudo yum install libfuse2
+./rustdesk-.AppImage
+```
+
+### Flatpak
+
+```sh
+flatpak --user remote-add --if-not-exists flathub https://flathub.org/repo/flathub.flatpakrepo
+flatpak --user install ./rustdesk-.flatpak
+flatpak run com.rustdesk.RustDesk
+```
+
+## ~~X11 Richiesto~~
+~~RustDesk non supporta ancora Wayland; è necessario passare manualmente a X11.~~
+
+RustDesk ora ha il supporto sperimentale per Wayland dalla versione 1.2.0.
+
+### Server di Visualizzazione
+
+[Ubuntu](https://askubuntu.com/questions/1260142/ubuntu-set-default-login-desktop) |
+[Fedora](https://docs.fedoraproject.org/en-US/quick-docs/configuring-xorg-as-default-gnome-session/) |
+[Arch Linux](https://bbs.archlinux.org/viewtopic.php?id=218319)
+
+### Schermata di Login
+
+La schermata di login che utilizza Wayland non è ancora supportata. Se vuoi accedere alla schermata di login dopo il riavvio o il logout con RustDesk, devi cambiare la schermata di login in X11, modifica la riga seguente in `WaylandEnable=false` in `/etc/gdm/custom.conf` o `/etc/gdm3/custom.conf`:
+
+```ini
+#WaylandEnable=false
+```
+
+{{% notice note %}}
+Si prega di **riavviare** per rendere effettive le modifiche sopra.
+{{% /notice %}}
+
+### Problemi di Permessi
+
+Se SELinux è abilitato, RustDesk non funzionerà correttamente né in ambienti X11 né Wayland, [problemi](https://github.com/search?q=repo%3Arustdesk%2Frustdesk+SElinux&type=issues) correlati.
+
+Puoi eseguire:
+
+```sh
+$ sudo grep 'comm="rustdesk"' /var/log/audit/audit.log | tail -1
+type=AVC msg=audit(1697902459.165:707): avc: denied { name_connect } for pid=31346 comm="rustdesk" dest=53330 scontext=system_u:system_r:init_t:s0 tcontext=system_u:object_r:ephemeral_port_t:s0 tclass=tcp_socket permissive=0
+```
+
+{{% notice note %}}
+Il numero tra parentesi dopo `audit` è il timestamp.
+{{% /notice %}}
+
+Se l'output contiene `avc: denied`, è necessario aggiungere le politiche SELinux, fare riferimento a [SELinux](https://rustdesk.com/docs/it/client/linux/selinux/).
\ No newline at end of file
diff --git a/content/client/linux/_index.ja.md b/content/client/linux/_index.ja.md
index 1d57780..6dc0816 100755
--- a/content/client/linux/_index.ja.md
+++ b/content/client/linux/_index.ja.md
@@ -3,4 +3,98 @@ title: Linux
weight: 4
---
-[English](/docs/en/client/linux/)
\ No newline at end of file
+## インストール
+
+### Ubuntu (≥ 18)
+
+```sh
+# 誤ったディスク使用量レポートは無視してください
+sudo apt install -fy ./rustdesk-.deb
+```
+
+Ubuntu 18.04の場合、[pipewire](https://github.com/rustdesk/rustdesk/discussions/6148#discussioncomment-9295883)のために最初に以下を実行してください。
+```sh
+sudo apt install software-properties-common
+sudo add-apt-repository ppa:pipewire-debian/pipewire-upstream
+sudo apt update
+```
+
+### CentOS/Fedora (≥ 28)
+
+```sh
+sudo yum localinstall ./rustdesk-.rpm
+```
+
+### Arch Linux/Manjaro
+
+```sh
+sudo pacman -U ./rustdesk-.pkg.tar.zst
+```
+
+### openSUSE (≥ Leap 15.0)
+
+```sh
+sudo zypper install --allow-unsigned-rpm ./rustdesk--suse.rpm
+```
+
+### AppImage
+
+```sh
+# Fedoraの場合
+sudo yum install libnsl
+./rustdesk-.AppImage
+```
+
+```sh
+# Ubuntuの場合
+sudo yum install libfuse2
+./rustdesk-.AppImage
+```
+
+### Flatpak
+
+```sh
+flatpak --user remote-add --if-not-exists flathub https://flathub.org/repo/flathub.flatpakrepo
+flatpak --user install ./rustdesk-.flatpak
+flatpak run com.rustdesk.RustDesk
+```
+
+## ~~X11が必要~~
+~~RustDeskはまだWaylandをサポートしていません。手動でX11に切り替える必要があります。~~
+
+RustDeskは、バージョン1.2.0から実験的なWaylandサポートを提供しています。
+
+### ディスプレイサーバー
+
+[Ubuntu](https://askubuntu.com/questions/1260142/ubuntu-set-default-login-desktop) |
+[Fedora](https://docs.fedoraproject.org/en-US/quick-docs/configuring-xorg-as-default-gnome-session/) |
+[Arch Linux](https://bbs.archlinux.org/viewtopic.php?id=218319)
+
+### ログイン画面
+
+Waylandを使用するログイン画面はまだサポートされていません。RustDeskで再起動またはログアウト後にログイン画面にアクセスしたい場合は、ログイン画面をX11に変更する必要があります。`/etc/gdm/custom.conf`または`/etc/gdm3/custom.conf`の以下の行を`WaylandEnable=false`に変更してください:
+
+```ini
+#WaylandEnable=false
+```
+
+{{% notice note %}}
+上記の変更を有効にするには**再起動**してください。
+{{% /notice %}}
+
+### 権限の問題
+
+SELinuxが有効になっている場合、RustDeskはX11でもWayland環境でも正しく動作しません。関連する[問題](https://github.com/search?q=repo%3Arustdesk%2Frustdesk+SElinux&type=issues)。
+
+次のコマンドを実行できます:
+
+```sh
+$ sudo grep 'comm="rustdesk"' /var/log/audit/audit.log | tail -1
+type=AVC msg=audit(1697902459.165:707): avc: denied { name_connect } for pid=31346 comm="rustdesk" dest=53330 scontext=system_u:system_r:init_t:s0 tcontext=system_u:object_r:ephemeral_port_t:s0 tclass=tcp_socket permissive=0
+```
+
+{{% notice note %}}
+`audit`の後の括弧内の数字はタイムスタンプです。
+{{% /notice %}}
+
+出力に`avc: denied`が含まれている場合は、SELinuxポリシーを追加する必要があります。[SELinux](https://rustdesk.com/docs/ja/client/linux/selinux/)を参照してください。
\ No newline at end of file
diff --git a/content/client/mac/_index.es.md b/content/client/mac/_index.es.md
index 0a148c7..28b2af5 100644
--- a/content/client/mac/_index.es.md
+++ b/content/client/mac/_index.es.md
@@ -4,36 +4,51 @@ weight: 3
---
## Instalación
-------
-Abra el archivo .dmg y arrastre `RustDesk` a `Applications` como a continuación.
+Abra el archivo .dmg y arrastre `RustDesk` a `Aplicaciones` como se muestra a continuación.

-Asegúrese de haber dejado de ejecutar RustDesk. También asegúrese de salir del servicio RustDesk que se muestra en la bandeja.
+Asegúrese de haber cerrado todas las instancias de RustDesk en ejecución. También asegúrese de salir del servicio RustDesk que se muestra en la bandeja del sistema.

## Permitir la ejecución de RustDesk
-| Desbloquear para cambiar | Haga clic en "App Store y desarrolladores identificados" |
-| ---- | ---- |
-|||
+| Desbloquear para cambiar | Haga clic en `App Store y desarrolladores identificados` |
+| --- | --- |
+|  |  |
## Habilitar permisos
-Para capturar la pantalla, debe otorgar `RustDesk` **accesibilidad** permiso y **grabación de pantalla** permiso. RustDesk lo guiará a la ventana de configuración.
+{{% notice note %}}
+Debido al cambio en la política de seguridad de macOS, nuestra API que captura la entrada en el lado local ya no funciona. Debe habilitar el permiso "Supervisión de entrada" en el lado local de Mac.
+Por favor siga esto
+[https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923](https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923).
-| Ventanas RustDesk | Ventana de configuración |
-| ---- | ---- |
-|||
+En la versión 1.2.4, puede probar `Input source 2` que se puede ver haciendo clic en el icono del teclado en la barra de herramientas.
+{{% /notice %}}
-Si lo ha habilitado en la ventana de configuración, pero RustDesk aún advierte. Elimine RustDesk de las ventanas de configuración por el `-` botón, y haga clic en `+` botón, seleccione RustDesk en `/Applications`.
+Para capturar la pantalla, debe otorgar a RustDesk el permiso de **Accesibilidad** y el permiso de **Grabación de pantalla**. RustDesk lo guiará a la ventana de configuración.
-| `-` y `+` botón | Seleccione RustDesk |
-| ---- | ---- |
-|||
+| Ventana de RustDesk | Ventana de configuración |
+| --- | --- |
+|  |  |
-Copie los pasos anteriores para obtener el permiso de **grabación de pantalla**.
+Si lo ha habilitado en la ventana de configuración, pero RustDesk aún muestra una advertencia. Por favor elimine `RustDesk` de las ventanas de configuración con el botón `-`, y haga clic en el botón `+`, seleccione `RustDesk` en `Aplicaciones`.
-
+{{% notice note %}}
+[https://github.com/rustdesk/rustdesk/issues/3261](https://github.com/rustdesk/rustdesk/issues/3261)
+Otros intentos sin éxito:
+`tccutil reset ScreenCapture com.carriez.RustDesk`
+`tccutil reset Accessibility com.carriez.RustDesk`
+Aún se requiere reiniciar.
+{{% /notice %}}
+
+| Botones `-` y `+` | Seleccione `RustDesk` |
+| --- | --- |
+|  |  |
+
+Por favor copie los pasos anteriores para el permiso de **Grabación de pantalla**.
+
+
\ No newline at end of file
diff --git a/content/client/mac/_index.fr.md b/content/client/mac/_index.fr.md
index f7df35e..efdf87b 100644
--- a/content/client/mac/_index.fr.md
+++ b/content/client/mac/_index.fr.md
@@ -4,42 +4,51 @@ weight: 3
---
## Installation
-------
-Ouvrez le fichier .dmg et faites glisser "RustDesk" vers "Applications" comme ci-dessous.
+Ouvrez le fichier .dmg et faites glisser `RustDesk` vers `Applications` comme ci-dessous.
+

-Assurez-vous que vous avez quitté les instance des "RustDesk" en cours d'exécution. Assurez-vous également d'avoir quitter le service "RustDesk" si affiché dans la barre d'état.
+Assurez-vous d'avoir quitté toutes les instances de RustDesk en cours d'exécution. Assurez-vous également de quitter le service RustDesk affiché dans la barre des menus.

-## Autoriser l'exécution de "RustDesk"
+## Autoriser l'exécution de RustDesk
-| Déverrouillez pour modifier | Cliquez sur "App Store et développeurs identifiés" |
-| ---- | ---- |
-|||
+| Déverrouiller pour modifier | Cliquez sur `App Store et développeurs identifiés` |
+| --- | --- |
+|  |  |
-## Activer les autorisations
+## Activer les permissions
{{% notice note %}}
-En raison du changement de politique de sécurité de MacOS, notre API qui capture les entrées du côté local ne fonctionne plus du tout. Vous devez activer l'autorisation "Surveillance des entrées" du côté Mac.
-Voir ceci: [https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923](https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923)
+En raison du changement de politique de sécurité de macOS, notre API qui capture les entrées côté local ne fonctionne plus. Vous devez activer la permission "Surveillance des entrées" sur le Mac local.
+Veuillez suivre ceci
+[https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923](https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923).
-Cela ne semble pas être une solution miracle, nous devons résoudre le problème avec notre prochaine version Flutter.
+Dans la version 1.2.4, vous pouvez essayer `Input source 2` qui peut être vu en cliquant sur l'icône du clavier dans la barre d'outils.
{{% /notice %}}
-Pour capturer l'écran, vous devez accorder à "RustDesk" l'autorisation d'**accessibilité** et l'autorisation d'**enregistrement d'écran**. "RustDesk" vous guidera vers la fenêtre des paramètres.
+Pour capturer l'écran, vous devez accorder à RustDesk la permission d'**Accessibilité** et la permission d'**Enregistrement d'écran**. RustDesk vous guidera vers la fenêtre des paramètres.
-| Lien vers la configuration accessibilité | Fenêtre configuration accessibilité |
-| ---- | ---- |
-|||
+| Fenêtre RustDesk | Fenêtre des paramètres |
+| --- | --- |
+|  |  |
-Si vous avez bien activé les permissions dans la fenêtre des paramètres, mais que "RustDesk" vous avertit toujours. Veuillez supprimer "RustDesk" de la liste de la fenêtre paramètres d'accessibilité par le bouton **"-"**, cliquez sur le bouton **"+"** et sélectionnez "RustDesk" dans **"/Applications"**.
+Si vous l'avez activé dans la fenêtre des paramètres, mais RustDesk vous avertit toujours. Veuillez supprimer `RustDesk` de la fenêtre des paramètres avec le bouton `-`, et cliquez sur le bouton `+`, sélectionnez `RustDesk` dans `Applications`.
-| boutons "-" et "+" | Sélectionnez "RustDesk" |
-| ---- | ---- |
-|||
+{{% notice note %}}
+[https://github.com/rustdesk/rustdesk/issues/3261](https://github.com/rustdesk/rustdesk/issues/3261)
+Autres tentatives infructueuses :
+`tccutil reset ScreenCapture com.carriez.RustDesk`
+`tccutil reset Accessibility com.carriez.RustDesk`
+Le redémarrage est toujours requis.
+{{% /notice %}}
-Veuillez suivre les mêmes étapes que ci-dessus pour l'autorisation **enregistrement d'écran**.
+| Boutons `-` et `+` | Sélectionnez `RustDesk` |
+| --- | --- |
+|  |  |
-
+Veuillez copier les étapes ci-dessus pour la permission d'**Enregistrement d'écran**.
+
+
\ No newline at end of file
diff --git a/content/client/mac/_index.it.md b/content/client/mac/_index.it.md
index fcc098b..3204549 100755
--- a/content/client/mac/_index.it.md
+++ b/content/client/mac/_index.it.md
@@ -3,4 +3,52 @@ title: Mac
weight: 3
---
-[English](/docs/en/client/mac/)
\ No newline at end of file
+## Installazione
+
+Apri il file .dmg e trascina `RustDesk` in `Applicazioni` come mostrato di seguito.
+
+
+
+Assicurati di aver chiuso tutte le istanze di RustDesk in esecuzione. Assicurati anche di chiudere il servizio RustDesk mostrato nella barra delle applicazioni.
+
+
+
+## Consentire l'esecuzione di RustDesk
+
+| Sblocca per modificare | Clicca su `App Store e sviluppatori identificati` |
+| --- | --- |
+|  |  |
+
+## Abilitare i permessi
+
+{{% notice note %}}
+A causa del cambiamento della politica di sicurezza di macOS, la nostra API che cattura l'input sul lato locale non funziona più. È necessario abilitare il permesso "Monitoraggio input" sul lato Mac locale.
+Segui questo
+[https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923](https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923).
+
+Nella versione 1.2.4, puoi provare `Input source 2` che può essere visualizzato cliccando sull'icona della tastiera nella barra degli strumenti.
+{{% /notice %}}
+
+Per catturare lo schermo, devi concedere a RustDesk il permesso di **Accessibilità** e il permesso di **Registrazione schermo**. RustDesk ti guiderà alla finestra delle impostazioni.
+
+| Finestra RustDesk | Finestra impostazioni |
+| --- | --- |
+|  |  |
+
+Se l'hai abilitato nella finestra delle impostazioni, ma RustDesk continua ad avvisare. Rimuovi `RustDesk` dalla finestra delle impostazioni con il pulsante `-`, e clicca sul pulsante `+`, seleziona `RustDesk` in `Applicazioni`.
+
+{{% notice note %}}
+[https://github.com/rustdesk/rustdesk/issues/3261](https://github.com/rustdesk/rustdesk/issues/3261)
+Altri tentativi inutili:
+`tccutil reset ScreenCapture com.carriez.RustDesk`
+`tccutil reset Accessibility com.carriez.RustDesk`
+È comunque richiesto il riavvio.
+{{% /notice %}}
+
+| Pulsanti `-` e `+` | Seleziona `RustDesk` |
+| --- | --- |
+|  |  |
+
+Ripeti i passaggi sopra per il permesso di **Registrazione schermo**.
+
+
\ No newline at end of file
diff --git a/content/client/mac/_index.ja.md b/content/client/mac/_index.ja.md
index fcc098b..62af7d6 100755
--- a/content/client/mac/_index.ja.md
+++ b/content/client/mac/_index.ja.md
@@ -3,4 +3,52 @@ title: Mac
weight: 3
---
-[English](/docs/en/client/mac/)
\ No newline at end of file
+## インストール
+
+.dmgファイルを開き、以下のように`RustDesk`を`アプリケーション`にドラッグします。
+
+
+
+実行中のすべてのRustDeskを終了したことを確認してください。また、トレイに表示されているRustDeskサービスも終了してください。
+
+
+
+## RustDeskの実行を許可する
+
+| ロックを解除して変更 | `App Storeと確認済みの開発者からのアプリケーションを許可`をクリック |
+| --- | --- |
+|  |  |
+
+## 権限を有効にする
+
+{{% notice note %}}
+macOSのセキュリティポリシーの変更により、ローカル側で入力をキャプチャする私たちのAPIが機能しなくなりました。ローカルMac側で「入力監視」権限を有効にする必要があります。
+こちらに従ってください
+[https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923](https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923)。
+
+バージョン1.2.4では、ツールバーのキーボードアイコンをクリックすることで表示される`Input source 2`を試すことができます。
+{{% /notice %}}
+
+画面をキャプチャするには、RustDeskに**アクセシビリティ**権限と**画面収録**権限を付与する必要があります。RustDeskが設定ウィンドウに案内します。
+
+| RustDeskウィンドウ | 設定ウィンドウ |
+| --- | --- |
+|  |  |
+
+設定ウィンドウで有効にしたにもかかわらず、RustDeskがまだ警告を表示する場合。設定ウィンドウから`-`ボタンで`RustDesk`を削除し、`+`ボタンをクリックして、`アプリケーション`から`RustDesk`を選択してください。
+
+{{% notice note %}}
+[https://github.com/rustdesk/rustdesk/issues/3261](https://github.com/rustdesk/rustdesk/issues/3261)
+その他の無力な試み:
+`tccutil reset ScreenCapture com.carriez.RustDesk`
+`tccutil reset Accessibility com.carriez.RustDesk`
+それでも再起動が必要です。
+{{% /notice %}}
+
+| `-`と`+`ボタン | `RustDesk`を選択 |
+| --- | --- |
+|  |  |
+
+**画面収録**権限についても上記の手順を繰り返してください。
+
+
\ No newline at end of file
diff --git a/content/client/mac/_index.zh-cn.md b/content/client/mac/_index.zh-cn.md
index 22b9a3e..0b4e982 100755
--- a/content/client/mac/_index.zh-cn.md
+++ b/content/client/mac/_index.zh-cn.md
@@ -4,7 +4,6 @@ weight: 3
---
## 安装
-------
打开 .dmg 文件并将 `RustDesk` 拖到 `应用程序`,如下所示。
@@ -23,26 +22,33 @@ weight: 3
## 启用权限
{{% notice note %}}
-Due to MacOS security policy change, our api which captures input on local side does not work any
-more. You have to enable "Input Monitoring" permission on local Mac side.
-Please follow this
-[https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923](https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923)
+由于 macOS 安全策略的更改,我们在本地端捕获输入的 API 不再工作。您必须在本地 Mac 端启用"输入监控"权限。
+请按照此说明操作:
+[https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923](https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923)。
-It seems no quick fix, we need to fix together with our Flutter version.
+在版本 1.2.4 中,您可以尝试使用 `输入源 2`,点击工具栏上的键盘图标即可看到。
{{% /notice %}}
为了获得捕获屏幕的能力,您需要授予 `RustDesk` **辅助功能** 权限和 **屏幕录制** 权限。 RustDesk 将引导您进入设置窗口。
| RustDesk 窗口 |设置窗口 |
| ---- | ---- |
-|||
+|||
-如果您在设置窗口中启用了它,但 RustDesk 仍然会发出警告。请通过 `-` 按钮从设置窗口中删除 RustDesk,然后单击 `+` 按钮,在 `/Applications` 中选择 RustDesk。
+如果您在设置窗口中启用了它,但 RustDesk 仍然会发出警告。请通过 `-` 按钮从设置窗口中删除 `RustDesk`,然后单击 `+` 按钮,在 `应用程序` 中选择 `RustDesk`。
+
+{{% notice note %}}
+[https://github.com/rustdesk/rustdesk/issues/3261](https://github.com/rustdesk/rustdesk/issues/3261)
+其他无奈的尝试:
+`tccutil reset ScreenCapture com.carriez.RustDesk`
+`tccutil reset Accessibility com.carriez.RustDesk`
+仍然需要重启。
+{{% /notice %}}
| `-` 和 `+` 按钮 |选择 RustDesk |
| ---- | ---- |
-|||
+|||
-请按照上面相似步骤设置*屏幕录制**权限。
+请按照上面相似步骤设置**屏幕录制**权限。
-
+
diff --git a/content/client/mac/_index.zh-tw.md b/content/client/mac/_index.zh-tw.md
index 07bfbf8..79a3da9 100755
--- a/content/client/mac/_index.zh-tw.md
+++ b/content/client/mac/_index.zh-tw.md
@@ -4,7 +4,6 @@ weight: 3
---
## 安裝
-------
打開 .dmg 檔案並將 `RustDesk` 拖到 `應用程式`,如下所示。
@@ -23,26 +22,33 @@ weight: 3
## 啟用權限
{{% notice note %}}
-MacOS 的安全政策更動,導致我們擷取本機端輸入的 API 失效。您必須在本機 Mac 端啟用 "輸入監測" 權限。
+由於 macOS 安全政策的更改,我們在本機端擷取輸入的 API 不再工作。您必須在本機 Mac 端啟用「輸入監控」權限。
+請按照此說明操作:
+[https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923](https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923)。
-請遵照
-[https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923](https://github.com/rustdesk/rustdesk/issues/974#issuecomment-1185644923)
-
-It seems no quick fix, we need to fix together with our Flutter version.
+在版本 1.2.4 中,您可以嘗試使用 `輸入源 2`,點擊工具列上的鍵盤圖示即可看到。
{{% /notice %}}
若要擷取畫面,您需要授予 `RustDesk` **輔助功能**權限和**畫面錄製**權限。RustDesk 將引導您進入設定視窗。
| RustDesk 視窗 | 設定視窗 |
| ---- | ---- |
-|||
+|||
-如果您在設置視窗中啟用了它,但 RustDesk 仍然發出警告。請通過 `-` 按鈕從設置視窗中刪除 RustDesk,然後單擊 `+` 按鈕,在 `/Applications` 中選擇 RustDesk。
+如果您在設定視窗中啟用了它,但 RustDesk 仍然發出警告。請通過 `-` 按鈕從設定視窗中刪除 `RustDesk`,然後單擊 `+` 按鈕,在 `應用程式` 中選擇 `RustDesk`。
+
+{{% notice note %}}
+[https://github.com/rustdesk/rustdesk/issues/3261](https://github.com/rustdesk/rustdesk/issues/3261)
+其他無奈的嘗試:
+`tccutil reset ScreenCapture com.carriez.RustDesk`
+`tccutil reset Accessibility com.carriez.RustDesk`
+仍然需要重啟。
+{{% /notice %}}
| `-` 和 `+` 按鈕 | 選擇 RustDesk |
| ---- | ---- |
-|||
+|||
-請按照上面相似步驟設置**畫面錄製**權限。
+請按照上面相似步驟設定**畫面錄製**權限。
-
+
diff --git a/content/client/windows/windows-portable-elevation/_index.de.md b/content/client/windows/windows-portable-elevation/_index.de.md
index 518f88c..3bda59c 100644
--- a/content/client/windows/windows-portable-elevation/_index.de.md
+++ b/content/client/windows/windows-portable-elevation/_index.de.md
@@ -24,7 +24,7 @@ Die kontrollierte Seite kann direkt auf `Akzeptieren und Erhöhen` klicken, wenn
| Verbinden | Verbunden |
| :---: | :---: |
-|  |  |
+|  |  |
## Anfrage der Erhöhung auf der Steuerungsseite
@@ -32,9 +32,9 @@ Nach der Auswahl von `Erhöhte Rechte anfordern` aus dem Aktionsmenü wird das f
| Menü | Dialog |
| :---: | :---: |
-|  |  |
+|  |  |
| **Warten** | **Erfolg** |
-|  |  |
+|  |  |
## Wie Sie wählen
diff --git a/content/client/windows/windows-portable-elevation/_index.en.md b/content/client/windows/windows-portable-elevation/_index.en.md
index 47730f3..3dab701 100644
--- a/content/client/windows/windows-portable-elevation/_index.en.md
+++ b/content/client/windows/windows-portable-elevation/_index.en.md
@@ -24,7 +24,7 @@ The controlled end can directly click `Accept and Elevate` when connecting, or c
| Connecting | Connected |
| :---: | :---: |
-|  |  |
+|  |  |
## Request elevation at the control end
@@ -32,9 +32,9 @@ After selecting `Request Elevation` from the action menu, the following dialog b
| Menu | Dialog |
| :---: | :---: |
-|  |  |
+|  |  |
| **Wait** | **Success** |
-|  |  |
+|  |  |
## How to Choose
diff --git a/content/client/windows/windows-portable-elevation/_index.es.md b/content/client/windows/windows-portable-elevation/_index.es.md
index 76c7cb1..11e4700 100644
--- a/content/client/windows/windows-portable-elevation/_index.es.md
+++ b/content/client/windows/windows-portable-elevation/_index.es.md
@@ -25,7 +25,7 @@ El lado controlado puede hacer click en `Aceptar y Elevar` cuando se este conect
| Conectando | Conectado |
| :---: | :---: |
-|  |  |
+|  |  |
## Pide la elevación de permisos del lado controlador
@@ -33,9 +33,9 @@ Después de seleccionar en el menu de acción `Solicitar Elevación`, la siguien
| Menu | Dialogo |
| :---: | :---: |
-|  |  |
+|  |  |
| **Wait** | **Success** |
-|  |  |
+|  |  |
## How to Choose
diff --git a/content/client/windows/windows-portable-elevation/_index.fr.md b/content/client/windows/windows-portable-elevation/_index.fr.md
index 7e41fe2..9b1a3d7 100644
--- a/content/client/windows/windows-portable-elevation/_index.fr.md
+++ b/content/client/windows/windows-portable-elevation/_index.fr.md
@@ -24,7 +24,7 @@ Le côté contrôlé peut directement cliquer sur `Accepter et Élever` lors de
| Connexion | Connecté |
| :---: | :---: |
-|  |  |
+|  |  |
## Demander l'élévation au niveau du côté contrôleur
@@ -32,9 +32,9 @@ Après avoir sélectionné `Demander l'élévation` dans le menu d'action, la bo
| Menu | Dialogue |
| :---: | :---: |
-|  |  |
+|  |  |
| **Attendre** | **Succès** |
-|  |  |
+|  |  |
## Comment choisir
diff --git a/content/client/windows/windows-portable-elevation/_index.it.md b/content/client/windows/windows-portable-elevation/_index.it.md
index b3d78df..250aa03 100644
--- a/content/client/windows/windows-portable-elevation/_index.it.md
+++ b/content/client/windows/windows-portable-elevation/_index.it.md
@@ -24,7 +24,7 @@ Il lato controllato può fare clic direttamente su `Accetta ed Eleva` durante la
| Connessione | Connesso |
| :---: | :---: |
-|  |  |
+|  |  |
## Richiedere elevazione dal lato controllore
@@ -32,9 +32,9 @@ Dopo aver selezionato `Richiedi Elevazione` dal menu azioni, apparirà la seguen
| Menu | Dialogo |
| :---: | :---: |
-|  |  |
+|  |  |
| **Attesa** | **Successo** |
-|  |  |
+|  |  |
## Come Scegliere
diff --git a/content/client/windows/windows-portable-elevation/_index.ja.md b/content/client/windows/windows-portable-elevation/_index.ja.md
index 9af3fab..cde22d0 100644
--- a/content/client/windows/windows-portable-elevation/_index.ja.md
+++ b/content/client/windows/windows-portable-elevation/_index.ja.md
@@ -24,7 +24,7 @@ Windowsポータブルプログラムには管理者権限がないため、以
| 接続中 | 接続済み |
| :---: | :---: |
-|  |  |
+|  |  |
## 制御側で昇格を要求
@@ -32,9 +32,9 @@ Windowsポータブルプログラムには管理者権限がないため、以
| メニュー | ダイアログ |
| :---: | :---: |
-|  |  |
+|  |  |
| **待機** | **成功** |
-|  |  |
+|  |  |
## 選択方法
diff --git a/content/client/windows/windows-portable-elevation/_index.pt.md b/content/client/windows/windows-portable-elevation/_index.pt.md
index 6b330f7..3c5a9e0 100644
--- a/content/client/windows/windows-portable-elevation/_index.pt.md
+++ b/content/client/windows/windows-portable-elevation/_index.pt.md
@@ -24,7 +24,7 @@ O lado controlado pode clicar diretamente em `Aceitar e Elevar` ao conectar, ou
| Conectando | Conectado |
| :---: | :---: |
-|  |  |
+|  |  |
## Solicitar elevação no lado de controle
@@ -32,9 +32,9 @@ Após selecionar `Solicitar Elevação` no menu de ação, a seguinte caixa de d
| Menu | Diálogo |
| :---: | :---: |
-|  |  |
+|  |  |
| **Aguardar** | **Sucesso** |
-|  |  |
+|  |  |
## Como Escolher
diff --git a/content/client/windows/windows-portable-elevation/_index.zh-cn.md b/content/client/windows/windows-portable-elevation/_index.zh-cn.md
index 7b7aef3..9299d1d 100644
--- a/content/client/windows/windows-portable-elevation/_index.zh-cn.md
+++ b/content/client/windows/windows-portable-elevation/_index.zh-cn.md
@@ -24,7 +24,7 @@ weight: 49
| 正在连接 | 已连接 |
| :--------------------------------------: | :--------------------------------------: |
-|  |  |
+|  |  |
## 控制端主动提权
@@ -32,9 +32,9 @@ weight: 49
| 菜单 | 对话框 |
| :--------------------------------------: | :--------------------------------------: |
-|  |  |
+|  |  |
| **等待** | **成功** |
-|  |  |
+|  |  |
## 如何选择
diff --git a/content/client/windows/windows-portable-elevation/_index.zh-tw.md b/content/client/windows/windows-portable-elevation/_index.zh-tw.md
index 33465a7..ce518ca 100644
--- a/content/client/windows/windows-portable-elevation/_index.zh-tw.md
+++ b/content/client/windows/windows-portable-elevation/_index.zh-tw.md
@@ -24,7 +24,7 @@ Windows 便攜式程式沒有管理員權限,這可能導致以下問題:
| 連線中 | 已連線 |
| :---: | :---: |
-|  |  |
+|  |  |
## 在控制端請求提權
@@ -32,9 +32,9 @@ Windows 便攜式程式沒有管理員權限,這可能導致以下問題:
| 選單 | 對話方塊 |
| :---: | :---: |
-|  |  |
+|  |  |
| **等待** | **成功** |
-|  |  |
+|  |  |
## 如何選擇
diff --git a/content/dev/build/faq/_index.es.md b/content/dev/build/faq/_index.es.md
index a9a0a64..ad49e14 100644
--- a/content/dev/build/faq/_index.es.md
+++ b/content/dev/build/faq/_index.es.md
@@ -3,9 +3,9 @@ title: FAQ para Windows
weight: 40
---
-# vcpkg el paquete de descarga falló
+## vcpkg el paquete de descarga falló
-## Error
+### Error
```
-- Fetching https://chromium.googlesource.com/libyuv/libyuv 287158925b0e03ea4499a18b4e08478c5781541b...
@@ -13,15 +13,15 @@ weight: 40
Command failed: D:/program/Git/mingw64/bin/git.exe fetch https://chromium.googlesource.com/libyuv/libyuv 287158925b0e03ea4499a18b4e08478c5781541b --depth 1 -n
```
-## Solución
+### Solución
Usa un navegador para descargar `https://chromium.googlesource.com/libyuv/libyuv/+archive/287158925b0e03ea4499a18b4e08478c5781541b.tar.gz`, luego muévelo a `vcpkg/downloads` y reinstalar.
-# El paquete en Cargo.lock no existe
+## El paquete en Cargo.lock no existe
-## Error
+### Error
```
$ cargo run
@@ -42,34 +42,34 @@ $ cargo run
Tal vez el autor usó `git force push` y la confirmación anterior se sobrescribió.
-## Solución
+### Solución
`cargo update`, forzar la actualización del paquete
-# VCPKG_ROOT no establecido
+## VCPKG_ROOT no establecido
-## Error
+### Error
```
thread 'main' panicked at 'Failed to find package: VcpkgNotFound("No vcpkg installation found. Set the VCPKG_ROOT environment variable or run 'vcpkg integrate install'")', libs\scrap\build.rs:7:45
```
-## Solución
+### Solución
Agregar `VCPKG_ROOT` variable de entorno, o ejecutar con `VCPKG_ROOT= cargo run`
-# clang no instalado, o LIBCLANG_PATH no establecido
+## clang no instalado, o LIBCLANG_PATH no establecido
-## Error
+### Error
```
thread 'main' panicked at 'Unable to find libclang: "couldn't find any valid shared libraries matching: ['clang.dll', 'libclang.dll'], set the `LIBCLANG_PATH` environment variable to a path where one of these files can be found (invalid: [])"', C:\Users\selfd\.cargo\registry\src\mirrors.ustc.edu.cn-61ef6e0cd06fb9b8\bindgen-0.59.2\src/lib.rs:2144:31
```
-## Solución
+### Solución
Instalar [llvm](https://releases.llvm.org/download.html), Añade el `LIBCLANG_PATH` variable de entorno como `llvm_install_dir/bin`
diff --git a/content/dev/build/faq/_index.fr.md b/content/dev/build/faq/_index.fr.md
index 9062a45..2485c0f 100644
--- a/content/dev/build/faq/_index.fr.md
+++ b/content/dev/build/faq/_index.fr.md
@@ -3,9 +3,9 @@ title: FAQ
weight: 40
---
-# Échec du téléchargement du package vcpkg
+## Échec du téléchargement du package vcpkg
-## Erreur
+### Erreur
```
-- Fetching https://chromium.googlesource.com/libyuv/libyuv 287158925b0e03ea4499a18b4e08478c5781541b...
@@ -13,14 +13,14 @@ weight: 40
Command failed: D:/program/Git/mingw64/bin/git.exe fetch https://chromium.googlesource.com/libyuv/libyuv 287158925b0e03ea4499a18b4e08478c5781541b --depth 1 -n
```
-## Solution
+### Solution
Utiliser un navigateur pour télécharger `https://chromium.googlesource.com/libyuv/libyuv/+archive/287158925b0e03ea4499a18b4e08478c5781541b.tar.gz`, puis déplacez-le dans `vcpkg/downloads` et réinstallez.
-# Le paquet dans Cargo.lock n'existe pas
+## Le paquet dans Cargo.lock n'existe pas
-## Erreur
+### Erreur
```
$ cargo run
@@ -41,31 +41,31 @@ $ cargo run
Peut-être que l'auteur a utilisé `git force push` et que le commit précédent a été écrasé.
-## Solution
+### Solution
`cargo update`, forcer la mise à jour du paquet.
-# VCPKG_ROOT non défini
+## VCPKG_ROOT non défini
-## Erreur
+### Erreur
```
thread 'main' panicked at 'Failed to find package: VcpkgNotFound("No vcpkg installation found. Set the VCPKG_ROOT environment variable or run 'vcpkg integrate install'")', libs\scrap\build.rs:7:45
```
-## Solution
+### Solution
Ajoutez la variable d'environnement `VCPKG_ROOT` ou lancer avec la commande `VCPKG_ROOT= cargo run`
-# clang non installé ou LIBCLANG_PATH non défini
+## clang non installé ou LIBCLANG_PATH non défini
-## Erreur
+### Erreur
```
thread 'main' panicked at 'Unable to find libclang: "couldn't find any valid shared libraries matching: ['clang.dll', 'libclang.dll'], set the `LIBCLANG_PATH` environment variable to a path where one of these files can be found (invalid: [])"', C:\Users\selfd\.cargo\registry\src\mirrors.ustc.edu.cn-61ef6e0cd06fb9b8\bindgen-0.59.2\src/lib.rs:2144:31
```
-## Solution
+### Solution
Installer [llvm](https://releases.llvm.org/download.html), et ajoutez la variable d'environnement `LIBCLANG_PATH` avec la valeur `llvm_install_dir/bin`
\ No newline at end of file
diff --git a/content/dev/build/faq/_index.zh-cn.md b/content/dev/build/faq/_index.zh-cn.md
index eca6ac9..078fcc0 100644
--- a/content/dev/build/faq/_index.zh-cn.md
+++ b/content/dev/build/faq/_index.zh-cn.md
@@ -3,20 +3,20 @@ title: Windows 常见问题
weight: 40
---
-# vcpkg下载包失败
-## 错误示例
+## vcpkg下载包失败
+### 错误示例
```
-- Fetching https://chromium.googlesource.com/libyuv/libyuv 287158925b0e03ea4499a18b4e08478c5781541b...
CMake Error at scripts/cmake/vcpkg_execute_required_process.cmake:127 (message):
Command failed: D:/program/Git/mingw64/bin/git.exe fetch https://chromium.googlesource.com/libyuv/libyuv 287158925b0e03ea4499a18b4e08478c5781541b --depth 1 -n
```
-## 解决方法
+### 解决方法
使用浏览器下载`https://chromium.googlesource.com/libyuv/libyuv/+archive/287158925b0e03ea4499a18b4e08478c5781541b.tar.gz`, 然后放到`vcpkg/downloads`下, 重新安装.
-# Cargo.lock里的版本不存在
-## 错误示例
+## Cargo.lock里的版本不存在
+### 错误示例
```
$ cargo run
Updating git repository `https://github.com/open-trade/confy`
@@ -34,25 +34,25 @@ $ cargo run
object not found - no match for id (27fa12941291b44ccd856aef4a5452c1eb646047); class=Odb (9); code=NotFound (-3)
```
可能作者使用`git force push`覆盖了之前的commit
-## 解决方法
+### 解决方法
`cargo update`强制更新包
-# VCPKG_ROOT环境变量未设置
-## 错误示例
+## VCPKG_ROOT环境变量未设置
+### 错误示例
```
thread 'main' panicked at 'Failed to find package: VcpkgNotFound("No vcpkg installation found. Set the VCPKG_ROOT environment variable or run 'vcpkg integrate install'")', libs\scrap\build.rs:7:45
```
-## 解决办法
+### 解决办法
添加VCPKG_ROOT环境变量, 或者使用`VCPKG_ROOT= cargo run`
-# 未安装clang环境, 或未设置LIBCLANG_PATH环境变量
-## 错误示例
+## 未安装clang环境, 或未设置LIBCLANG_PATH环境变量
+### 错误示例
```
thread 'main' panicked at 'Unable to find libclang: "couldn't find any valid shared libraries matching: ['clang.dll', 'libclang.dll'], set the `LIBCLANG_PATH` environment variable to a path where one of these files can be found (invalid: [])"', C:\Users\selfd\.cargo\registry\src\mirrors.ustc.edu.cn-61ef6e0cd06fb9b8\bindgen-0.59.2\src/lib.rs:2144:31
```
-## 解决办法
+### 解决办法
安装[llvm](https://releases.llvm.org/download.html), 设置`LIBCLANG_PATH`环境变量为`llvm_install_dir/bin`
\ No newline at end of file
diff --git a/content/dev/build/faq/_index.zh-tw.md b/content/dev/build/faq/_index.zh-tw.md
index 4284f4b..bd1f40d 100644
--- a/content/dev/build/faq/_index.zh-tw.md
+++ b/content/dev/build/faq/_index.zh-tw.md
@@ -3,9 +3,9 @@ title: Windows 常見問題
weight: 40
---
-# vcpkg 下載包失敗
+## vcpkg 下載包失敗
-## 錯誤
+### 錯誤
```
-- Fetching https://chromium.googlesource.com/libyuv/libyuv 287158925b0e03ea4499a18b4e08478c5781541b...
@@ -13,15 +13,15 @@ weight: 40
Command failed: D:/program/Git/mingw64/bin/git.exe fetch https://chromium.googlesource.com/libyuv/libyuv 287158925b0e03ea4499a18b4e08478c5781541b --depth 1 -n
```
-## 解決方法
+### 解決方法
使用瀏覽器下載 `https://chromium.googlesource.com/libyuv/libyuv/+archive/287158925b0e03ea4499a18b4e08478c5781541b.tar.gz`,然後放到 `vcpkg/downloads下,重新安裝。
-# Cargo.lock 裡的套件不存在
+## Cargo.lock 裡的套件不存在
-## 錯誤
+### 錯誤
```
$ cargo run
@@ -42,34 +42,34 @@ $ cargo run
可能作者使用 `git force push` 覆蓋了之前的 commit。
-## 解決方法
+### 解決方法
使用 `cargo update`,強制更新套件
-# VCPKG_ROOT 環境變數未設置
+## VCPKG_ROOT 環境變數未設置
-## 錯誤
+### 錯誤
```
thread 'main' panicked at 'Failed to find package: VcpkgNotFound("No vcpkg installation found. Set the VCPKG_ROOT environment variable or run 'vcpkg integrate install'")', libs\scrap\build.rs:7:45
```
-## 解決辦法
+### 解決辦法
加入 VCPKG_ROOT 環境變數, 或者使用 `VCPKG_ROOT= cargo run`
-# 未安裝 clang 環境,或未設置 LIBCLANG_PATH 環境變數
+## 未安裝 clang 環境,或未設置 LIBCLANG_PATH 環境變數
-## 錯誤
+### 錯誤
```
thread 'main' panicked at 'Unable to find libclang: "couldn't find any valid shared libraries matching: ['clang.dll', 'libclang.dll'], set the `LIBCLANG_PATH` environment variable to a path where one of these files can be found (invalid: [])"', C:\Users\selfd\.cargo\registry\src\mirrors.ustc.edu.cn-61ef6e0cd06fb9b8\bindgen-0.59.2\src/lib.rs:2144:31
```
-## 解決辦法
+### 解決辦法
安裝 [llvm](https://releases.llvm.org/download.html),設置 `LIBCLANG_PATH` 環境變數為 `llvm_install_dir/bin`
\ No newline at end of file
diff --git a/content/dev/build/osx/_index.es.md b/content/dev/build/osx/_index.es.md
index ac3210e..6c9aa81 100644
--- a/content/dev/build/osx/_index.es.md
+++ b/content/dev/build/osx/_index.es.md
@@ -3,16 +3,120 @@ title: macOS
weight: 21
---
+Hay múltiples formas de hacer esto, esta guía asume que `Xcode`, `Git` y `Homebrew` ya están instalados.
+
+El mayor desafío es probablemente encontrar versiones de todas las herramientas que funcionen juntas, especialmente porque partes de la cadena de herramientas como Xcode y LLVM están dictadas por tu versión de macOS. Las versiones utilizadas en esta guía probablemente no sean las que deberías usar. Un punto de partida para determinar qué versiones usar es mirar en el [flujo de trabajo de compilación de GitHub](https://github.com/rustdesk/rustdesk/blob/master/.github/workflows/flutter-build.yml) para la versión de RustDesk que deseas compilar. Elige la etiqueta para ver el archivo en la esquina superior izquierda de la página. Pero eso no necesariamente funcionará porque las herramientas de macOS que vienen con el runner de GitHub podrían no ser las mismas versiones que las de tu sistema local.
+
+### Export
+`export` se utiliza para establecer varias variables de entorno. Cuando ejecutas `export`, esa variable se establece solo para la sesión de terminal actual, y por lo tanto debe repetirse para cada nueva ventana de terminal que quieras usar para compilar RustDesk, ahora o en el futuro. Generalmente, es preferible agregar todos los `export`s a un script que se ejecute automáticamente para cada terminal que se abra, por ejemplo `~/.bash_profile`. Los comandos `export` completos listados aquí pueden simplemente agregarse al archivo, pero también deben ejecutarse en la terminal actual porque el archivo no se lee hasta que se abre una *nueva* terminal.
+
+## Instalar las herramientas que vamos a usar desde Homebrew
+
+```sh
+brew install python3 create-dmg nasm cmake gcc wget ninja pkg-config wget rustup
```
-cd
+
+Algunas de las instalaciones podrían fallar porque algunas de las carpetas de destino no existen en nuestro sistema. En ese caso, crea la carpeta, establece el propietario y los permisos y ejecuta el comando `brew` nuevamente. Por ejemplo, si `/usr/local/include` no existe:
+```sh
+sudo mkdir /usr/local/include
+sudo chown :admin /usr/local/include
+sudo chmod 775 /usr/local/include
+```
+
+## Instalar vcpkg
+Vcpkg se utiliza para gestionar las dependencias de C/C++ utilizadas por RustDesk. Decide dónde quieres la instalación y ejecuta lo siguiente desde la carpeta en la que quieres que resida la carpeta `vcpkg`. En este ejemplo se usa `/Users//repos/` como ubicación, y la etiqueta `2023.04.15` se usa como versión.
+
+```sh
git clone https://github.com/microsoft/vcpkg
cd vcpkg
git checkout 2023.04.15
-./bootstrap-vcpkg.sh
-brew install nasm yasm
+./bootstrap-vcpkg.sh -disableMetrics
./vcpkg install libvpx libyuv opus aom
-git clone --recurse-submodules https://github.com/rustdesk/rustdesk
-cd rustdesk
-export VCPKG_ROOT=$HOME/vcpkg
-cargo run
+export VCPKG_ROOT=~/repos/vcpkg
```
+
+## Instalar y configurar Rust
+Usamos `rustup` para gestionar Rust, que ya se instaló anteriormente usando Homebrew. Pero aún necesita configurarse. Sigue las instrucciones y asegúrate de que tanto `rustup` como `rustc` estén en el `PATH`. En este ejemplo usamos la versión de Rust `1.75.0`, pero es posible que necesites usar una versión diferente. Puedes instalar y gestionar múltiples versiones de Rust con `rustup`.
+
+```sh
+rustup-init
+rustup default 1.75.0
+rustup component add rustfmt
+```
+Para obtener una descripción general de las cadenas de herramientas de Rust instaladas y predeterminadas, ejecuta `rustup show`.
+
+## Descargar los archivos fuente de RustDesk
+
+Decide dónde quieres los archivos fuente de RustDesk y ejecuta lo siguiente desde la carpeta en la que quieres que resida la carpeta `rustdesk`. En este ejemplo se usa `/Users//repos/` como ubicación.
+
+```sh
+git clone --recurse-submodules https://github.com/rustdesk/rustdesk
+cd rustdesk/libs/portable/
+python3 -m pip install --upgrade pip
+pip3 install -r requirements.txt
+```
+
+Si `python3` o `pip` son desconocidos, agrégalos al `PATH` con algo como (usa tus nombres de carpeta reales):
+```sh
+export PATH=~/Library/Python/3.9/bin:$PATH
+```
+Una vez hecho esto, ejecuta nuevamente el/los comando(s) que fallaron. Recuerda también editar `~/.bash_profile`.
+
+## Instalar componentes de interfaz de usuario
+RustDesk se puede compilar usando tanto [Sciter](https://sciter.com/) como [Flutter](https://flutter.dev/). Ambos necesitan componentes adicionales, así que sigue los pasos para la versión relevante, o ambas.
+
+### Sciter
+
+Desde la carpeta `rustdesk`, ejecuta:
+```sh
+wget https://github.com/c-smile/sciter-sdk/raw/master/bin.osx/libsciter.dylib
+```
+
+### Flutter
+
+[FVM](https://fvm.app/) te permite gestionar qué versión de Flutter se usa, y es probablemente la forma más fácil de poder probar diferentes versiones de Flutter fácilmente.
+
+```sh
+brew tap leoafarias/fvm
+brew install fvm cocoapods
+```
+Instala y usa, por ejemplo Flutter `3.16.9`, con:
+
+```sh
+fvm global 3.16.9
+```
+FVM está diseñado para usar una configuración más compleja donde puede proporcionar diferentes versiones de Flutter para diferentes proyectos, pero eso está más allá del alcance de esta guía. En su lugar, simplemente agrega la ubicación del Flutter predeterminado proporcionado por FVM a tu `PATH` manualmente, lo que significa que debes usar `fvm global` para cambiar la versión de Flutter:
+
+```sh
+export PATH=$HOME/fvm/default/bin:$PATH
+```
+
+Una vez hecho esto, deberías desactivar la telemetría y verificar si todo está bien:
+
+```sh
+flutter --disable-analytics
+dart --disable-analytics
+flutter doctor -v
+```
+No importa si algunas de las verificaciones fallan, generalmente lo harán, lo importante es que la verificación del entorno que pretendes usar esté bien, es decir, `Xcode`. Si se reportan problemas, resuélvelos antes de continuar.
+
+Una vez que Flutter esté funcionando, es hora de instalar el "puente" que une Rust y Flutter. Aquí hay otra de las versiones que deben funcionar juntas con todo lo demás, en este ejemplo usamos `1.80.1`:
+
+```sh
+cargo install flutter_rust_bridge_codegen --version "1.80.1" --features "uuid"
+```
+
+## Compilar
+
+Compila desde la carpeta `rustdesk`. Compila la versión Sciter con:
+
+```sh
+python3 ./build.py
+```
+
+Compila la versión Flutter con:
+```sh
+flutter_rust_bridge_codegen --rust-input ./src/flutter_ffi.rs --dart-output ./flutter/lib/generated_bridge.dart --c-output ./flutter/macos/Runner/bridge_generated.h
+python3 ./build.py --flutter
+```
+Si todo va bien, ahora deberías tener un archivo `dmg` listo para instalar en tu carpeta `rustdesk`.
\ No newline at end of file
diff --git a/content/dev/build/osx/_index.fr.md b/content/dev/build/osx/_index.fr.md
index efc3f05..f6541b6 100644
--- a/content/dev/build/osx/_index.fr.md
+++ b/content/dev/build/osx/_index.fr.md
@@ -3,17 +3,120 @@ title: macOS
weight: 21
---
+Il existe plusieurs façons de faire cela, ce guide suppose que `Xcode`, `Git` et `Homebrew` sont déjà installés.
+
+Le plus grand défi est probablement de trouver des versions de tous les outils qui fonctionnent ensemble, surtout que des parties de la chaîne d'outils comme Xcode et LLVM sont dictées par votre version de macOS. Les versions utilisées dans ce guide ne sont probablement pas celles que vous devriez utiliser. Un point de départ pour déterminer quelles versions utiliser est de consulter le [workflow de build GitHub](https://github.com/rustdesk/rustdesk/blob/master/.github/workflows/flutter-build.yml) pour la version de RustDesk que vous souhaitez compiler. Choisissez le tag pour lequel voir le fichier dans le coin supérieur gauche de la page. Mais cela ne fonctionnera pas nécessairement car les outils macOS fournis avec le runner GitHub pourraient ne pas être les mêmes versions que celles de votre système local.
+
+### Export
+`export` est utilisé pour définir diverses variables d'environnement. Lorsque vous exécutez `export`, cette variable est définie uniquement pour la session de terminal actuelle, et celles-ci doivent donc être répétées pour chaque nouvelle fenêtre de terminal que vous souhaitez utiliser pour compiler RustDesk, maintenant ou à l'avenir. Généralement, il est préférable d'ajouter tous les `export`s à un script qui est exécuté automatiquement pour chaque terminal ouvert, par exemple `~/.bash_profile`. Les commandes `export` complètes listées ici peuvent simplement être ajoutées au fichier, mais doivent également être exécutées dans le terminal actuel car le fichier n'est pas lu jusqu'à ce qu'un *nouveau* terminal soit ouvert.
+
+## Installer les outils que nous allons utiliser depuis Homebrew
+
+```sh
+brew install python3 create-dmg nasm cmake gcc wget ninja pkg-config wget rustup
```
-cd
+
+Certaines installations pourraient échouer car certains dossiers cibles n'existent pas sur notre système. Dans ce cas, créez le dossier, définissez le propriétaire et les permissions et exécutez à nouveau la commande `brew`. Par exemple si `/usr/local/include` n'existe pas :
+```sh
+sudo mkdir /usr/local/include
+sudo chown :admin /usr/local/include
+sudo chmod 775 /usr/local/include
+```
+
+## Installer vcpkg
+Vcpkg est utilisé pour gérer les dépendances C/C++ utilisées par RustDesk. Décidez où vous voulez l'installation et exécutez ce qui suit depuis le dossier dans lequel vous voulez que le dossier `vcpkg` réside. Dans cet exemple `/Users//repos/` est utilisé comme emplacement, et le tag `2023.04.15` est utilisé comme version.
+
+```sh
git clone https://github.com/microsoft/vcpkg
cd vcpkg
git checkout 2023.04.15
-./bootstrap-vcpkg.sh
-brew install nasm yasm
+./bootstrap-vcpkg.sh -disableMetrics
./vcpkg install libvpx libyuv opus aom
-git clone --recurse-submodules https://github.com/rustdesk/rustdesk
-cd rustdesk
-export VCPKG_ROOT=$HOME/vcpkg
-wget https://github.com/c-smile/sciter-sdk/raw/master/bin.osx/libsciter.dylib
-cargo run
+export VCPKG_ROOT=~/repos/vcpkg
```
+
+## Installer et configurer Rust
+Nous utilisons `rustup` pour gérer Rust, qui a déjà été installé ci-dessus en utilisant Homebrew. Mais il doit encore être configuré. Suivez les instructions et assurez-vous que `rustup` et `rustc` sont sur le `PATH`. Dans cet exemple, nous utilisons la version Rust `1.75.0`, mais vous pourriez avoir besoin d'utiliser une version différente. Vous pouvez installer et gérer plusieurs versions de Rust avec `rustup`.
+
+```sh
+rustup-init
+rustup default 1.75.0
+rustup component add rustfmt
+```
+Pour un aperçu des chaînes d'outils Rust installées et par défaut, exécutez `rustup show`.
+
+## Télécharger les fichiers sources de RustDesk
+
+Décidez où vous voulez les fichiers sources de RustDesk et exécutez ce qui suit depuis le dossier dans lequel vous voulez que le dossier `rustdesk` réside. Dans cet exemple `/Users//repos/` est utilisé comme emplacement.
+
+```sh
+git clone --recurse-submodules https://github.com/rustdesk/rustdesk
+cd rustdesk/libs/portable/
+python3 -m pip install --upgrade pip
+pip3 install -r requirements.txt
+```
+
+Si `python3` ou `pip` sont inconnus, ajoutez-les au `PATH` avec quelque chose comme (utilisez vos noms de dossiers réels) :
+```sh
+export PATH=~/Library/Python/3.9/bin:$PATH
+```
+Une fois cela fait, exécutez à nouveau la ou les commandes qui ont échoué. N'oubliez pas de modifier également `~/.bash_profile`.
+
+## Installer les composants d'interface utilisateur
+RustDesk peut être compilé en utilisant à la fois [Sciter](https://sciter.com/) et [Flutter](https://flutter.dev/). Les deux nécessitent des composants supplémentaires, alors suivez les étapes pour la version pertinente, ou les deux.
+
+### Sciter
+
+Depuis le dossier `rustdesk`, exécutez :
+```sh
+wget https://github.com/c-smile/sciter-sdk/raw/master/bin.osx/libsciter.dylib
+```
+
+### Flutter
+
+[FVM](https://fvm.app/) vous permet de gérer quelle version de Flutter est utilisée, et est probablement le moyen le plus simple de pouvoir essayer facilement différentes versions de Flutter.
+
+```sh
+brew tap leoafarias/fvm
+brew install fvm cocoapods
+```
+Installez et utilisez, par exemple Flutter `3.16.9`, avec :
+
+```sh
+fvm global 3.16.9
+```
+FVM est conçu pour utiliser une configuration plus complexe où il peut fournir différentes versions de Flutter pour différents projets, mais cela dépasse le cadre de ce guide. Au lieu de cela, ajoutez simplement manuellement l'emplacement du Flutter par défaut fourni par FVM à votre `PATH`, ce qui signifie que vous devez utiliser `fvm global` pour changer de version de Flutter :
+
+```sh
+export PATH=$HOME/fvm/default/bin:$PATH
+```
+
+Une fois cela fait, vous devriez désactiver la télémétrie et vérifier si tout va bien :
+
+```sh
+flutter --disable-analytics
+dart --disable-analytics
+flutter doctor -v
+```
+Peu importe si certaines vérifications échouent, elles le feront généralement, ce qui est important c'est que la vérification de l'environnement que vous avez l'intention d'utiliser est OK, à savoir `Xcode`. Si des problèmes sont signalés, résolvez-les avant de continuer.
+
+Une fois que Flutter est opérationnel, il est temps d'installer le "pont" qui lie Rust et Flutter ensemble. Voici une autre des versions qui doivent fonctionner ensemble avec tout le reste, dans cet exemple nous utilisons `1.80.1` :
+
+```sh
+cargo install flutter_rust_bridge_codegen --version "1.80.1" --features "uuid"
+```
+
+## Compiler
+
+Compilez depuis le dossier `rustdesk`. Compilez la version Sciter avec :
+
+```sh
+python3 ./build.py
+```
+
+Compilez la version Flutter avec :
+```sh
+flutter_rust_bridge_codegen --rust-input ./src/flutter_ffi.rs --dart-output ./flutter/lib/generated_bridge.dart --c-output ./flutter/macos/Runner/bridge_generated.h
+python3 ./build.py --flutter
+```
+Si tout se passe bien, vous devriez maintenant avoir un fichier `dmg` prêt à installer dans votre dossier `rustdesk`.
\ No newline at end of file
diff --git a/content/dev/build/osx/_index.zh-tw.md b/content/dev/build/osx/_index.zh-tw.md
index 9c034aa..00280e2 100644
--- a/content/dev/build/osx/_index.zh-tw.md
+++ b/content/dev/build/osx/_index.zh-tw.md
@@ -3,17 +3,120 @@ title: macOS
weight: 21
---
+有多種方法可以做到這一點,本指南假設 `Xcode`、`Git` 和 `Homebrew` 已經安裝。
+
+最大的挑戰可能是找到所有工具可以一起工作的版本,特別是因為工具鏈的某些部分(如 Xcode 和 LLVM)由您的 macOS 版本決定。本指南中使用的版本可能不是您應該使用的版本。作為確定使用哪些版本的起點,可以查看您想要構建的 RustDesk 版本的 [GitHub 構建工作流程](https://github.com/rustdesk/rustdesk/blob/master/.github/workflows/flutter-build.yml)。在頁面左上角選擇標籤以查看文件。但這不一定會起作用,因為 GitHub runner 附帶的 macOS 工具可能與您本地系統上的版本不同。
+
+### Export
+`export` 用於設置各種環境變數。當您運行 `export` 時,該變數僅為當前終端會話設置,因此必須為您想要用於構建 RustDesk 的每個新終端窗口重複執行,無論是現在還是將來。通常,最好將所有 `export` 添加到為每個打開的終端自動執行的腳本中,例如 `~/.bash_profile`。這裡列出的完整 `export` 命令可以簡單地附加到文件中,但也必須在當前終端中運行,因為該文件要到打開*新*終端時才會被讀取。
+
+## 從 Homebrew 安裝我們將要使用的工具
+
+```sh
+brew install python3 create-dmg nasm cmake gcc wget ninja pkg-config wget rustup
```
-cd
+
+某些安裝可能會失敗,因為我們系統上不存在某些目標文件夾。在這種情況下,創建文件夾、設置所有者和權限,然後再次運行 `brew` 命令。例如,如果 `/usr/local/include` 不存在:
+```sh
+sudo mkdir /usr/local/include
+sudo chown <使用者名稱>:admin /usr/local/include
+sudo chmod 775 /usr/local/include
+```
+
+## 安裝 vcpkg
+Vcpkg 用於管理 RustDesk 使用的 C/C++ 依賴項。決定您想要安裝的位置,並從您希望 `vcpkg` 文件夾所在的文件夾運行以下命令。在此示例中,使用 `/Users/<使用者名稱>/repos/` 作為位置,並使用標籤 `2023.04.15` 作為版本。
+
+```sh
git clone https://github.com/microsoft/vcpkg
cd vcpkg
git checkout 2023.04.15
-./bootstrap-vcpkg.sh
-brew install nasm yasm
+./bootstrap-vcpkg.sh -disableMetrics
./vcpkg install libvpx libyuv opus aom
+export VCPKG_ROOT=~/repos/vcpkg
+```
+
+## 安裝和配置 Rust
+我們使用 `rustup` 來管理 Rust,它已經使用 Homebrew 安裝了。但是,它仍然需要配置。按照說明操作,確保 `rustup` 和 `rustc` 都在 `PATH` 上。在此示例中,我們使用 Rust 版本 `1.75.0`,但您可能需要使用不同的版本。您可以使用 `rustup` 安裝和管理多個版本的 Rust。
+
+```sh
+rustup-init
+rustup default 1.75.0
+rustup component add rustfmt
+```
+要查看已安裝和默認的 Rust 工具鏈概覽,請運行 `rustup show`。
+
+## 下載 RustDesk 源文件
+
+決定您想要 RustDesk 源文件的位置,並從您希望 `rustdesk` 文件夾所在的文件夾運行以下命令。在此示例中,使用 `/Users/<使用者名稱>/repos/` 作為位置。
+
+```sh
git clone --recurse-submodules https://github.com/rustdesk/rustdesk
-cd rustdesk
-export VCPKG_ROOT=$HOME/vcpkg
+cd rustdesk/libs/portable/
+python3 -m pip install --upgrade pip
+pip3 install -r requirements.txt
+```
+
+如果 `python3` 或 `pip` 未知,請使用類似以下內容將它們添加到 `PATH`(使用您的實際文件夾名稱):
+```sh
+export PATH=~/Library/Python/3.9/bin:$PATH
+```
+完成後,再次運行失敗的命令。記得也要編輯 `~/.bash_profile`。
+
+## 安裝用戶界面組件
+RustDesk 可以使用 [Sciter](https://sciter.com/) 和 [Flutter](https://flutter.dev/) 構建。這兩者都需要額外的組件,因此請按照相關版本的步驟操作,或兩者都操作。
+
+### Sciter
+
+從 `rustdesk` 文件夾運行:
+```sh
wget https://github.com/c-smile/sciter-sdk/raw/master/bin.osx/libsciter.dylib
-cargo run
-```
\ No newline at end of file
+```
+
+### Flutter
+
+[FVM](https://fvm.app/) 讓您管理使用哪個版本的 Flutter,這可能是能夠輕鬆嘗試不同 Flutter 版本的最簡單方法。
+
+```sh
+brew tap leoafarias/fvm
+brew install fvm cocoapods
+```
+安裝並使用,例如 Flutter `3.16.9`:
+
+```sh
+fvm global 3.16.9
+```
+FVM 旨在使用更複雜的設置,它可以為不同的項目提供不同的 Flutter 版本,但這超出了本指南的範圍。相反,只需手動將 FVM 提供的默認 Flutter 位置添加到您的 `PATH`,這意味著您必須使用 `fvm global` 來切換 Flutter 版本:
+
+```sh
+export PATH=$HOME/fvm/default/bin:$PATH
+```
+
+完成後,您應該禁用遙測並檢查一切是否正常:
+
+```sh
+flutter --disable-analytics
+dart --disable-analytics
+flutter doctor -v
+```
+如果某些檢查失敗並不重要,它們通常會失敗,重要的是您打算使用的環境檢查是否正常,即 `Xcode`。如果報告了問題,請在繼續之前解決它們。
+
+一旦 Flutter 啟動並運行,就該安裝將 Rust 和 Flutter 綁定在一起的"橋接"了。這是另一個必須與其他所有組件一起工作的版本,在此示例中我們使用 `1.80.1`:
+
+```sh
+cargo install flutter_rust_bridge_codegen --version "1.80.1" --features "uuid"
+```
+
+## 構建
+
+從 `rustdesk` 文件夾構建。使用以下命令構建 Sciter 版本:
+
+```sh
+python3 ./build.py
+```
+
+使用以下命令構建 Flutter 版本:
+```sh
+flutter_rust_bridge_codegen --rust-input ./src/flutter_ffi.rs --dart-output ./flutter/lib/generated_bridge.dart --c-output ./flutter/macos/Runner/bridge_generated.h
+python3 ./build.py --flutter
+```
+如果一切順利,您現在應該在 `rustdesk` 文件夾中有一個準備安裝的 `dmg` 文件。
\ No newline at end of file
diff --git a/content/dev/build/windows/_index.es.md b/content/dev/build/windows/_index.es.md
index 1bc678a..8a44470 100644
--- a/content/dev/build/windows/_index.es.md
+++ b/content/dev/build/windows/_index.es.md
@@ -3,52 +3,56 @@ title: Windows
weight: 20
---
-# Dependencias
+{{% notice note %}}
+Los comandos de línea de comandos aquí deben ejecutarse en Git Bash, no en el símbolo del sistema o obtendrá errores de sintaxis.
+{{% /notice %}}
-## Entorno de compilación C++
+## Dependencias
-Descargar [msvc](https://visualstudio.microsoft.com/) e instalar.
+### Entorno de compilación C++
-## Entorno de desarrollo Rust
+Descargar [MSVC](https://visualstudio.microsoft.com/) e instalar.
+Seleccione `Windows` como SO de máquina de desarrollador y marque `C++`, luego descargue la versión Visual Studio Community e instale. La instalación puede tardar un tiempo.
-Descargar [rustup-init.exe](https://static.rust-lang.org/rustup/dist/x86_64-pc-windows-msvc/rustup-init.exe) e instalar.
+### Entorno de desarrollo Rust
-## vcpkg
+Descargue [rustup-init.exe](https://static.rust-lang.org/rustup/dist/x86_64-pc-windows-msvc/rustup-init.exe) y ejecútelo como administrador para instalar `rust`.
-Usar [git-bash](https://git-scm.com/download/win) para ejecutar los siguientes comandos, download `vcpkg`, install `libvpx`, `libyuv`, `opus`.
+### vcpkg
-```shell
- git clone https://github.com/microsoft/vcpkg
- cd vcpkg
- git checkout 2023.04.15
- cd ..
- vcpkg/bootstrap-vcpkg.bat
- export VCPKG_ROOT=$PWD/vcpkg
- vcpkg/vcpkg install libvpx:x64-windows-static libyuv:x64-windows-static opus:x64-windows-static aom:x64-windows-static
+Vaya a la carpeta donde desea clonar vcpkg y use [Git Bash](https://git-scm.com/download/win) para ejecutar los siguientes comandos, descargue `vcpkg`, instale la versión de 64 bits de `libvpx`, `libyuv` y `opus`.
+Si no tiene `Git` instalado, obtenga `Git` [aquí](https://git-scm.com/download/win).
+
+```sh
+git clone https://github.com/microsoft/vcpkg
+vcpkg/bootstrap-vcpkg.bat
+export VCPKG_ROOT=$PWD/vcpkg
+vcpkg/vcpkg install libvpx:x64-windows-static libyuv:x64-windows-static opus:x64-windows-static aom:x64-windows-static
```
-Agregar variable de entorno `VCPKG_ROOT`=`\vcpkg`.
+Agregar variable de entorno del sistema `VCPKG_ROOT`=`\vcpkg`. El `` debe ser la ubicación que eligió arriba para clonar `vcpkg`.

-## sciter
+### Sciter
-Uso de versiones de escritorio [sciter](https://sciter.com/) para GUI, descargue [sciter.dll](https://raw.githubusercontent.com/c-smile/sciter-sdk/master/bin.win/x64/sciter.dll)
+Las versiones de escritorio usan [Sciter](https://sciter.com/) para GUI, por favor descargue [sciter.dll](https://raw.githubusercontent.com/c-smile/sciter-sdk/master/bin.win/x64/sciter.dll).
-## llvm
+### LLVM
-rust-bindgen depende del clang, descargar [llvm](https://github.com/llvm/llvm-project/releases) e instalar, agregar variable de entorno `LIBCLANG_PATH`=`/bin`.
+`rust-bindgen` depende de `clang`, descargue [LLVM](https://github.com/llvm/llvm-project/releases) e instale, agregue la variable de entorno del sistema `LIBCLANG_PATH`=`/bin`.
+Puede descargar la versión 15.0.2 de los binarios de LLVM aquí: [64 bit](https://github.com/llvm/llvm-project/releases/download/llvmorg-15.0.2/LLVM-15.0.2-win64.exe) / [32 bit](https://github.com/llvm/llvm-project/releases/download/llvmorg-15.0.2/LLVM-15.0.2-win32.exe).
+## Construir
-# Construir
-
-## Por defecto
+### Por defecto
```sh
git clone --recurse-submodules https://github.com/rustdesk/rustdesk
cd rustdesk
mkdir -p target/debug
+wget https://raw.githubusercontent.com/c-smile/sciter-sdk/master/bin.win/x64/sciter.dll
mv sciter.dll target/debug
cargo run
```
diff --git a/content/dev/build/windows/_index.zh-cn.md b/content/dev/build/windows/_index.zh-cn.md
index 9fcbe1c..8341723 100644
--- a/content/dev/build/windows/_index.zh-cn.md
+++ b/content/dev/build/windows/_index.zh-cn.md
@@ -3,50 +3,54 @@ title: Windows
weight: 20
---
-# 依赖
+{{% notice note %}}
+这里的命令行命令必须在 Git Bash 中运行,而不是命令提示符,否则您将遇到语法错误。
+{{% /notice %}}
-## C++编译环境
+## 依赖
-推荐下载[msvc](https://visualstudio.microsoft.com/)并安装
+### C++编译环境
-## Rust 开发环境
-下载[rustup-init.exe](https://static.rust-lang.org/rustup/dist/x86_64-pc-windows-msvc/rustup-init.exe)并安装
+下载 [MSVC](https://visualstudio.microsoft.com/) 并安装。
+选择 `Windows` 作为开发人员机器操作系统并勾选 `C++`,然后下载 Visual Studio Community 版本并安装。安装可能需要一段时间。
-## vcpkg
+### Rust 开发环境
-使用[git-bash](https://git-scm.com/download/win)运行下列命令, 下载`vcpkg`, 安装`libvpx`, `libyuv`, `opus`
+下载 [rustup-init.exe](https://static.rust-lang.org/rustup/dist/x86_64-pc-windows-msvc/rustup-init.exe) 并以管理员身份运行它来安装 `rust`。
-```shell
- git clone https://github.com/microsoft/vcpkg
- cd vcpkg
- git checkout 2023.04.15
- cd ..
- vcpkg/bootstrap-vcpkg.bat
- export VCPKG_ROOT=$PWD/vcpkg
- vcpkg/vcpkg install libvpx:x64-windows-static libyuv:x64-windows-static opus:x64-windows-static aom:x64-windows-static
+### vcpkg
+
+转到您想要克隆 vcpkg 的文件夹,并使用 [Git Bash](https://git-scm.com/download/win) 运行以下命令,下载 `vcpkg`,安装 64 位版本的 `libvpx`、`libyuv` 和 `opus`。
+如果您没有安装 `Git`,请在[这里](https://git-scm.com/download/win)获取 `Git`。
+
+```sh
+git clone https://github.com/microsoft/vcpkg
+vcpkg/bootstrap-vcpkg.bat
+export VCPKG_ROOT=$PWD/vcpkg
+vcpkg/vcpkg install libvpx:x64-windows-static libyuv:x64-windows-static opus:x64-windows-static aom:x64-windows-static
```
-添加环境变量`VCPKG_ROOT`=`\vcpkg`。
+添加系统环境变量 `VCPKG_ROOT`=`\vcpkg`。`` 应该是您在上面选择克隆 `vcpkg` 的位置。

-## Sciter
+### Sciter
-桌面版本使用[sciter](https://sciter.com/) , 下载动态库[sciter.dll](https://raw.githubusercontent.com/c-smile/sciter-sdk/master/bin.win/x64/sciter.dll)
+桌面版本使用 [Sciter](https://sciter.com/) 作为 GUI,请下载 [sciter.dll](https://raw.githubusercontent.com/c-smile/sciter-sdk/master/bin.win/x64/sciter.dll)。
-## llvm
+### LLVM
-rust-bindgen依赖于clang, 下载[llvm](https://github.com/llvm/llvm-project/releases)并安装, 添加环境变量`LIBCLANG_PATH`,值为`/bin`
+`rust-bindgen` 依赖于 `clang`,下载 [LLVM](https://github.com/llvm/llvm-project/releases) 并安装,添加系统环境变量 `LIBCLANG_PATH`=`/bin`。
+您可以在这里下载 LLVM 二进制文件的 15.0.2 版本:[64 位](https://github.com/llvm/llvm-project/releases/download/llvmorg-15.0.2/LLVM-15.0.2-win64.exe) / [32 位](https://github.com/llvm/llvm-project/releases/download/llvmorg-15.0.2/LLVM-15.0.2-win32.exe)。
-
-# 构建
+#### 默认
```sh
git clone --recurse-submodules https://github.com/rustdesk/rustdesk
cd rustdesk
mkdir -p target/debug
+wget https://raw.githubusercontent.com/c-smile/sciter-sdk/master/bin.win/x64/sciter.dll
mv sciter.dll target/debug
cargo run
```
-
diff --git a/content/self-host/_index.de.md b/content/self-host/_index.de.md
index 296d95d..cfe0743 100755
--- a/content/self-host/_index.de.md
+++ b/content/self-host/_index.de.md
@@ -8,26 +8,41 @@ Wenn Sie RustDesk verwenden, sollten Sie Ihren eigenen RustDesk-Server haben. Di
Support ist über unser [Discord](https://discord.com/invite/nDceKgxnkV) für OSS und per [E-Mail](mailto:support@rustdesk.com) für Pro verfügbar.
-## Grundlegende Einrichtung
+## Wie funktioniert ein selbst-gehosteter Server?
-[Richten Sie Ihre eigene Serverinstanz manuell ein.](https://rustdesk.com/docs/de/self-host/rustdesk-server-oss/install/#richten-sie-ihre-eigene-serverinstanz-manuell-ein)
+Es gibt technisch gesehen zwei ausführbare Dateien (Server):
+
+- `hbbs` - RustDesk ID (Rendezvous / Signalisierungs) Server, hört auf TCP (`21114` - nur für HTTP in Pro, `21115`, `21116`, `21118` für WebSocket) und UDP (`21116`)
+- `hbbr` - RustDesk Relay-Server, hört auf TCP (`21117`, `21119` für WebSocket)
+
+Wenn Sie über Installationsskript / Docker Compose / deb installieren, werden beide Dienste installiert.
+
+Hier sind [Illustrationen](https://github.com/rustdesk/rustdesk/wiki/How-does-RustDesk-work%3F), wie der RustDesk-Client mit `hbbr` / `hbbs` kommuniziert.
+
+Solange RustDesk auf einem Rechner läuft, pingt der Rechner ständig den ID-Server (`hbbs`), um seine aktuelle IP-Adresse und Port bekannt zu machen.
+
+Wenn Sie eine Verbindung von Computer A zu Computer B starten, kontaktiert Computer A den ID-Server und fordert die Kommunikation mit Computer B an.
+
+Der ID-Server versucht dann, A und B direkt miteinander zu verbinden, indem er Hole Punching verwendet.
+
+Wenn Hole Punching fehlschlägt, kommuniziert A mit B über den Relay-Server (`hbbr`).
+
+In den meisten Fällen ist Hole Punching erfolgreich und der Relay-Server wird nie verwendet.
+
+Hier ist eine Diskussion über [Sollten Sie einen RustDesk-Server selbst hosten?](https://www.reddit.com/r/rustdesk/comments/1cr8kfv/should_you_selfhost_a_rustdesk_server/)
## Erforderliche Ports
-Die für das Selbst-Hosten des RustDesk-Servers erforderlichen Ports hängen weitgehend von Ihrer Umgebung und den Anforderungen ab, die Sie an RustDesk stellen. In den Beispielen, die in der Dokumentation gezeigt werden, sind in der Regel alle vorgeschlagenen Ports geöffnet.
+Die für das Selbst-Hosten des RustDesk-Servers erforderlichen Ports hängen weitgehend von Ihrer Umgebung und davon ab, was Sie mit RustDesk machen möchten. Die in der Dokumentation gezeigten Beispiele haben in der Regel alle empfohlenen Ports geöffnet.
-Grundlegende Ports: \
+Kern-Ports: \
TCP `21114-21119` \
UDP `21116`
-`21114-21117` sind die mindestens erforderlichen Ports, damit RustDesk funktionieren kann. Sie sind für die Signal- und Relais-Ports sowie für NAT-Traversal zuständig.
+Die oben genannten `21115-21117` sind die mindestens erforderlichen Ports, damit RustDesk funktioniert. Diese verwalten die Signal- und Relay-Ports sowie die NAT-Traversierung.
-Zusätzlich können die TCP-Ports `21118` und `21119` geöffnet werden, wenn Sie den [RustDesk-Webclient](https://rustdesk.com/docs/de/dev/build/web/) verwenden möchten.
+Die TCP-Ports `21118` und `21119` sind die WebSocket-Ports für den [RustDesk Web-Client](https://rustdesk.com/web/). Sie benötigen einen Reverse-Proxy, um HTTPS zu unterstützen. Bitte beachten Sie diese [Beispiel-Nginx-Konfiguration](/docs/en/self-host/rustdesk-server-pro/faq/#8-add-websocket-secure-wss-support-for-the-id-server-and-relay-server-to-enable-secure-communication-for-the-web-client).
Für Pro-Benutzer ohne SSL-Proxy müssen Sie den TCP-Port `21114` öffnen, damit die API funktioniert. Alternativ können Sie mit einem SSL-Proxy den TCP-Port `443` öffnen.
-## Geöffnete Ports testen
-
-Um zu überprüfen, ob die Ports geöffnet sind und funktionieren, können Sie `test-netconnection domain.com -p 21115` mit PowerShell oder [CanYouSeeMe.org](https://canyouseeme.org/) verwenden.
-
-{{% children depth="3" showhidden="true" %}}
+{{% children depth="4" showhidden="true" %}}
diff --git a/content/self-host/_index.zh-tw.md b/content/self-host/_index.zh-tw.md
index 6976b9c..56cd572 100755
--- a/content/self-host/_index.zh-tw.md
+++ b/content/self-host/_index.zh-tw.md
@@ -4,31 +4,45 @@ weight: 5
pre: "2. "
---
-如果您想要和我們聊聊關於[自架 RustDesk 伺服器](https://github.com/rustdesk/rustdesk-server)的事,請加入我們的 [Discord](https://discord.com/invite/nDceKgxnkV) 伺服器。
+如果您使用 RustDesk,您應該擁有自己的 RustDesk 伺服器,這些文檔將在您的 RustDesk 之旅中提供幫助。
支援服務可透過我們的 [Discord](https://discord.com/invite/nDceKgxnkV) 獲得開源版本的協助,以及透過[Email](mailto:support@rustdesk.com)獲得專業版支援。
-## 基本設置
+## 自架伺服器如何運作?
-https://rustdesk.com/docs/zh-tw/self-host/rustdesk-server-oss/install/#set-up-your-own-server-instance-manually
+從技術上講,有兩個可執行檔案(伺服器):
+
+- `hbbs` - RustDesk ID(會合 / 信號)伺服器,監聽 TCP(`21114` - 僅用於 Pro 版的 HTTP、`21115`、`21116`、`21118` 用於 WebSocket)和 UDP(`21116`)
+- `hbbr` - RustDesk 中繼伺服器,監聽 TCP(`21117`、`21119` 用於 WebSocket)
+
+當您透過安裝腳本 / docker compose / deb 安裝時,這兩個服務都會被安裝。
+
+這裡有 RustDesk 客戶端如何與 `hbbr` / `hbbs` 通信的[圖解](https://github.com/rustdesk/rustdesk/wiki/How-does-RustDesk-work%3F)。
+
+只要 RustDesk 在機器上運行,該機器就會不斷地 ping ID 伺服器(`hbbs`),以使其當前的 IP 位址和連接埠被知悉。
+
+當您從電腦 A 啟動到電腦 B 的連接時,電腦 A 會聯繫 ID 伺服器並要求與電腦 B 通信。
+
+ID 伺服器然後嘗試使用打洞技術將 A 和 B 直接連接。
+
+如果打洞失敗,A 將透過中繼伺服器(`hbbr`)與 B 通信。
+
+在大多數情況下,打洞是成功的,並且永遠不會使用中繼伺服器。
+
+這裡有一個關於[您是否應該自架 RustDesk 伺服器?](https://www.reddit.com/r/rustdesk/comments/1cr8kfv/should_you_selfhost_a_rustdesk_server/)的討論
## 所需的連結埠
-自行架設的 RustDesk 伺服器所需的連結埠主要取決於您的環境以及您想要使用 RustDesk 做什麼。在文件中展示的範例通常會建議打開所有埠號。
+自架 RustDesk 伺服器所需的連接埠在很大程度上取決於您的環境以及您想要使用 RustDesk 做什麼。整個文檔中顯示的範例通常會建議開啟所有連接埠。
-核心連結埠:\
-TCP `21115-21117` \
+核心連接埠:\
+TCP `21114-21119` \
UDP `21116`
-上述是 RustDesk 運作所需的最小埠號,這些連結埠處理訊號和中繼,以及 NAT 穿透。
+上述的 `21115-21117` 是 RustDesk 運作所需的最低要求連接埠,這些處理信號和中繼連接埠以及 NAT 穿透。
-此外,如果您想使用 [RustDesk 網頁客戶端](https://rustdesk.com/docs/en/dev/build/web/),可以開放 TCP 埠號 `21118` 和 `21119`。
+TCP 連接埠 `21118` 和 `21119` 是 [RustDesk Web 客戶端](https://rustdesk.com/web/)的 WebSocket 連接埠,您需要反向代理來支援 HTTPS,請參考這個 [Nginx 配置範例](/docs/en/self-host/rustdesk-server-pro/faq/#8-add-websocket-secure-wss-support-for-the-id-server-and-relay-server-to-enable-secure-communication-for-the-web-client)。
-對於沒有 SSL Proxy 的專業用戶,您將需要開放 TCP 埠號 `21114` 以使 API 能夠運作,或者使用 SSL Proxy 則開放 TCP 連結埠 `443`。
+對於沒有 SSL 代理的專業版用戶,您需要開啟 TCP 連接埠 `21114` 以使 API 運作,或者使用 SSL 代理開啟 TCP 連接埠 `443`。
-## 測試連結埠是否開放
-
-要檢查連結埠是否已開放且運作正常,您可以使用 PowerShell 的 `test-netconnection domain.com -p 21115` 指令或者使用 [CanYouSeeMe.org](https://canyouseeme.org/) 網站。
-
-
-{{% children depth="3" showhidden="true" %}}
+{{% children depth="4" showhidden="true" %}}
diff --git a/content/self-host/client-configuration/_index.de.md b/content/self-host/client-configuration/_index.de.md
index d6bfe54..4c06253 100644
--- a/content/self-host/client-configuration/_index.de.md
+++ b/content/self-host/client-configuration/_index.de.md
@@ -16,14 +16,14 @@ Derzeit werden Windows X64, Mac Arm64 / X64, [Linux](https://twitter.com/rustdes
[Video](https://twitter.com/rustdesk/status/1769171628426944539)
-
-
+
+
## 2. Manuelle Konfiguration
Im Hauptmenü des RustDesk-Clients klicken Sie auf die Menü-Schaltfläche [ ⋮ ] neben Ihrer ID und dann auf Netzwerk. Sie können nun die Einstellungen mit erhöhten Rechten freischalten und Ihre ID, Relay, API und Schlüssel einstellen.
-
+
Geben Sie in das Eingabefeld **ID-Server** den `hbbs`-Host oder die IP-Adresse ein (lokale Seite und entfernte Seite). Die anderen beiden Adressen können leer gelassen werden, RustDesk wird sie automatisch ermitteln (falls nicht speziell eingestellt). Der Relay-Server bezieht sich auf `hbbr` (Port 21117).
@@ -45,7 +45,7 @@ Um eine verschlüsselte Verbindung zu Ihrem self-hosted Server herzustellen, mü
Als `Pro`-Benutzer können Sie den Schlüssel zusätzlich über die [Webkonsole](https://rustdesk.com/docs/de/self-host/rustdesk-server-pro/console/) abrufen.
-
+
### `API-Server` festlegen
@@ -77,7 +77,7 @@ Sie können auch die Schritte von [oben](https://rustdesk.com/docs/de/self-host/
## 5. Konfiguration aus `Pro` über die Zwischenablage importieren
-
+
https://github.com/rustdesk/rustdesk-server-pro/discussions/372#discussioncomment-10473298
diff --git a/content/self-host/client-configuration/_index.en.md b/content/self-host/client-configuration/_index.en.md
index b153ec9..c88e208 100644
--- a/content/self-host/client-configuration/_index.en.md
+++ b/content/self-host/client-configuration/_index.en.md
@@ -16,14 +16,14 @@ Currently, Windows X64, Mac Arm64 / X64, [Linux](https://twitter.com/rustdesk/st
[Video](https://twitter.com/rustdesk/status/1769171628426944539)
-
-
+
+
## 2. Manual Config
In the main RustDesk Client home click on the Menu button [ ⋮ ] next to your ID then click on Network, you can now unlock the settings using elevated privileges and set your `ID`, `Relay`, `API` and `Key`. It's important to note that this `Key` is the public key used for connection encryption, distinct from the license key provided with your Pro version purchase.
-
+
Enter the `hbbs` host or IP Address in the **ID Server** input box (local side + remote side). The other two addresses can be left blank, RustDesk will automatically deduce (if not specially set), and the Relay Server refers to `hbbr` (port 21117).
@@ -45,7 +45,7 @@ In order to establish an encrypted connection to your self-hosted server, you ne
As a `Pro` user you will additionally be able to retrieve the `Key` from the [web console](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/console/).
-
+
### Set `API Server`
@@ -73,7 +73,7 @@ The easiest way to setup automatically is using deployment scripts found [here](
## 5. Import config from `Pro` via clipboard
-
+
https://github.com/rustdesk/rustdesk-server-pro/discussions/372#discussioncomment-10473298
diff --git a/content/self-host/client-configuration/_index.es.md b/content/self-host/client-configuration/_index.es.md
index 883f12f..68c408b 100644
--- a/content/self-host/client-configuration/_index.es.md
+++ b/content/self-host/client-configuration/_index.es.md
@@ -16,14 +16,14 @@ Actualmente se admite Windows X64, Mac Arm64 / X64, [Linux](https://twitter.com/
[Video](https://twitter.com/rustdesk/status/1769171628426944539)
-
-
+
+
## 2. Configuración manual
En la página principal del cliente RustDesk, haga clic en el botón de menú [ ⋮ ] al lado de su ID y luego haga clic en Red, ahora puede desbloquear la configuración usando privilegios elevados y establecer su `ID`, `Relé`, `API` y `Clave`. Es importante tener en cuenta que esta `Clave` es la clave pública utilizada para el cifrado de conexión, distinta de la clave de licencia proporcionada con su compra de la versión Pro.
-
+
Ingrese el host o dirección IP `hbbs` en el cuadro de entrada **Servidor ID** (lado local + lado remoto). Las otras dos direcciones se pueden dejar en blanco, RustDesk las deducirá automáticamente (si no se establece especialmente), y el Servidor de Relé se refiere a `hbbr` (puerto 21117).
@@ -45,7 +45,7 @@ Para establecer una conexión cifrada a su servidor auto-hospedado, necesita ing
Como usuario `Pro`, adicionalmente podrá recuperar la `Clave` desde la [consola web](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/console/).
-
+
### Establecer `Servidor API`
@@ -73,7 +73,7 @@ La forma más fácil de configurar automáticamente es usar los scripts de imple
## 5. Importar configuración desde `Pro` a través del portapapeles
-
+
https://github.com/rustdesk/rustdesk-server-pro/discussions/372#discussioncomment-10473298
diff --git a/content/self-host/client-configuration/_index.fr.md b/content/self-host/client-configuration/_index.fr.md
index 5cc6900..1f97890 100644
--- a/content/self-host/client-configuration/_index.fr.md
+++ b/content/self-host/client-configuration/_index.fr.md
@@ -16,14 +16,14 @@ Actuellement, Windows X64, Mac Arm64 / X64, [Linux](https://twitter.com/rustdesk
[Vidéo](https://twitter.com/rustdesk/status/1769171628426944539)
-
-
+
+
## 2. Configuration manuelle
Dans la page d'accueil du client RustDesk, cliquez sur le bouton de menu [ ⋮ ] à côté de votre ID puis cliquez sur Réseau, vous pouvez maintenant déverrouiller les paramètres en utilisant des privilèges élevés et définir votre `ID`, `Relais`, `API` et `Clé`. Il est important de noter que cette `Clé` est la clé publique utilisée pour le chiffrement de connexion, distincte de la clé de licence fournie avec votre achat de version Pro.
-
+
Entrez l'hôte ou l'adresse IP `hbbs` dans la zone de saisie **Serveur ID** (côté local + côté distant). Les deux autres adresses peuvent être laissées vides, RustDesk les déduira automatiquement (si pas spécialement défini), et le Serveur Relais fait référence à `hbbr` (port 21117).
@@ -45,7 +45,7 @@ Pour établir une connexion chiffrée à votre serveur auto-hébergé, vous deve
En tant qu'utilisateur `Pro`, vous pourrez également récupérer la `Clé` depuis la [console web](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/console/).
-
+
### Définir le `Serveur API`
@@ -73,7 +73,7 @@ La façon la plus facile de configurer automatiquement est d'utiliser les script
## 5. Importer la config depuis `Pro` via le presse-papiers
-
+
https://github.com/rustdesk/rustdesk-server-pro/discussions/372#discussioncomment-10473298
diff --git a/content/self-host/client-configuration/_index.it.md b/content/self-host/client-configuration/_index.it.md
index 19a43be..680c0da 100644
--- a/content/self-host/client-configuration/_index.it.md
+++ b/content/self-host/client-configuration/_index.it.md
@@ -16,14 +16,14 @@ Attualmente sono supportati Windows X64, Mac Arm64 / X64, [Linux](https://twitte
[Video](https://twitter.com/rustdesk/status/1769171628426944539)
-
-
+
+
## 2. Configurazione manuale
Nella home principale del client RustDesk, clicca sul pulsante menu [ ⋮ ] accanto al tuo ID poi clicca su Rete, ora puoi sbloccare le impostazioni usando privilegi elevati e impostare il tuo `ID`, `Relay`, `API` e `Chiave`. È importante notare che questa `Chiave` è la chiave pubblica utilizzata per la crittografia della connessione, distinta dalla chiave di licenza fornita con l'acquisto della versione Pro.
-
+
Inserisci l'host o indirizzo IP `hbbs` nella casella di input **Server ID** (lato locale + lato remoto). Gli altri due indirizzi possono essere lasciati vuoti, RustDesk dedurrà automaticamente (se non impostato appositamente), e il Server Relay si riferisce a `hbbr` (porta 21117).
@@ -45,7 +45,7 @@ Per stabilire una connessione crittografata al tuo server self-hosted, devi inse
Come utente `Pro` sarai inoltre in grado di recuperare la `Chiave` dalla [console web](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/console/).
-
+
### Impostare il `Server API`
@@ -73,7 +73,7 @@ Il modo più semplice per configurare automaticamente è usare gli script di dep
## 5. Importa configurazione da `Pro` tramite appunti
-
+
https://github.com/rustdesk/rustdesk-server-pro/discussions/372#discussioncomment-10473298
diff --git a/content/self-host/client-configuration/_index.ja.md b/content/self-host/client-configuration/_index.ja.md
index 812240f..27b1807 100644
--- a/content/self-host/client-configuration/_index.ja.md
+++ b/content/self-host/client-configuration/_index.ja.md
@@ -16,14 +16,14 @@ RustDesk クライアントを自己ホスト型サーバーを使用するよ
[動画](https://twitter.com/rustdesk/status/1769171628426944539)
-
-
+
+
## 2. 手動設定
RustDesk クライアントのメインホームで、ID の横にあるメニューボタン [ ⋮ ] をクリックし、次にネットワークをクリックします。これで昇格した権限を使用して設定のロックを解除し、`ID`、`リレー`、`API`、`キー` を設定できます。この `キー` は接続暗号化に使用される公開鍵であり、Pro版購入時に提供されるライセンスキーとは異なることに注意することが重要です。
-
+
**ID サーバー** 入力ボックスに `hbbs` ホストまたは IP アドレス(ローカル側 + リモート側)を入力します。他の2つのアドレスは空白のままにできます。RustDesk が自動的に推定します(特別に設定されていない場合)。リレーサーバーは `hbbr`(ポート21117)を指します。
@@ -45,7 +45,7 @@ hbbs.example.com:21116
`Pro` ユーザーとして、[Web コンソール](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/console/)から `キー` を取得することもできます。
-
+
### `API サーバー` の設定
@@ -73,7 +73,7 @@ API サーバーがデフォルトの `21114` ポートで動作していない
## 5. `Pro` からクリップボード経由で設定をインポート
-
+
https://github.com/rustdesk/rustdesk-server-pro/discussions/372#discussioncomment-10473298
diff --git a/content/self-host/client-configuration/_index.pt.md b/content/self-host/client-configuration/_index.pt.md
index 012b3ee..525a606 100644
--- a/content/self-host/client-configuration/_index.pt.md
+++ b/content/self-host/client-configuration/_index.pt.md
@@ -16,14 +16,14 @@ Atualmente, Windows X64, Mac Arm64 / X64, [Linux](https://twitter.com/rustdesk/s
[Vídeo](https://twitter.com/rustdesk/status/1769171628426944539)
-
-
+
+
## 2. Configuração manual
Na página inicial do cliente RustDesk, clique no botão de menu [ ⋮ ] ao lado do seu ID e depois clique em Rede, agora você pode desbloquear as configurações usando privilégios elevados e definir seu `ID`, `Relay`, `API` e `Chave`. É importante notar que esta `Chave` é a chave pública usada para criptografia de conexão, distinta da chave de licença fornecida com sua compra da versão Pro.
-
+
Digite o host ou endereço IP `hbbs` na caixa de entrada **Servidor ID** (lado local + lado remoto). Os outros dois endereços podem ser deixados em branco, RustDesk deduzirá automaticamente (se não especialmente configurado), e o Servidor Relay refere-se ao `hbbr` (porta 21117).
@@ -45,7 +45,7 @@ Para estabelecer uma conexão criptografada com seu servidor auto-hospedado, voc
Como usuário `Pro`, você também poderá recuperar a `Chave` do [console web](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/console/).
-
+
### Definir `Servidor API`
@@ -73,7 +73,7 @@ A maneira mais fácil de configurar automaticamente é usar os scripts de implan
## 5. Importar configuração do `Pro` via área de transferência
-
+
https://github.com/rustdesk/rustdesk-server-pro/discussions/372#discussioncomment-10473298
diff --git a/content/self-host/client-configuration/_index.zh-cn.md b/content/self-host/client-configuration/_index.zh-cn.md
index ffdc5f4..a3d8c10 100644
--- a/content/self-host/client-configuration/_index.zh-cn.md
+++ b/content/self-host/client-configuration/_index.zh-cn.md
@@ -16,14 +16,14 @@ pre: "2.3. "
[视频](https://twitter.com/rustdesk/status/1769171628426944539)
-
-
+
+
## 2. 手动配置
在 RustDesk 客户端主界面,点击 ID 旁边的菜单按钮 [ ⋮ ],然后点击网络,您现在可以使用提升的权限解锁设置并设置您的 `ID`、`中继`、`API` 和 `密钥`。需要注意的是,这个 `密钥` 是用于连接加密的公钥,与您购买 Pro 版本时提供的许可证密钥不同。
-
+
在 **ID 服务器** 输入框中输入 `hbbs` 主机或 IP 地址(本地端 + 远程端)。其他两个地址可以留空,RustDesk 会自动推导(如果未特别设置),中继服务器指的是 `hbbr`(端口 21117)。
@@ -45,7 +45,7 @@ hbbs.example.com:21116
作为 `Pro` 用户,您还可以从 [Web 控制台](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/console/) 获取 `密钥`。
-
+
### 设置 `API 服务器`
@@ -73,7 +73,7 @@ hbbs.example.com:21116
## 5. 从 `Pro` 通过剪贴板导入配置
-
+
https://github.com/rustdesk/rustdesk-server-pro/discussions/372#discussioncomment-10473298
diff --git a/content/self-host/client-configuration/_index.zh-tw.md b/content/self-host/client-configuration/_index.zh-tw.md
index 0d802c6..074b0e5 100644
--- a/content/self-host/client-configuration/_index.zh-tw.md
+++ b/content/self-host/client-configuration/_index.zh-tw.md
@@ -16,14 +16,14 @@ pre: "2.3. "
[視頻](https://twitter.com/rustdesk/status/1769171628426944539)
-
-
+
+
## 2. 手動配置
在 RustDesk 客戶端主介面,點擊 ID 旁邊的選單按鈕 [ ⋮ ],然後點擊網路,您現在可以使用提升的權限解鎖設定並設定您的 `ID`、`中繼`、`API` 和 `金鑰`。需要注意的是,這個 `金鑰` 是用於連接加密的公鑰,與您購買 Pro 版本時提供的許可證金鑰不同。
-
+
在 **ID 伺服器** 輸入框中輸入 `hbbs` 主機或 IP 地址(本地端 + 遠端)。其他兩個地址可以留空,RustDesk 會自動推導(如果未特別設定),中繼伺服器指的是 `hbbr`(埠 21117)。
@@ -45,7 +45,7 @@ hbbs.example.com:21116
作為 `Pro` 使用者,您還可以從 [Web 控制台](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/console/) 取得 `金鑰`。
-
+
### 設定 `API 伺服器`
@@ -73,7 +73,7 @@ hbbs.example.com:21116
## 5. 從 `Pro` 透過剪貼簿匯入配置
-
+
https://github.com/rustdesk/rustdesk-server-pro/discussions/372#discussioncomment-10473298
diff --git a/content/self-host/nat-loopback-issues/_index.de.md b/content/self-host/nat-loopback-issues/_index.de.md
index 68bc665..7c5a10a 100644
--- a/content/self-host/nat-loopback-issues/_index.de.md
+++ b/content/self-host/nat-loopback-issues/_index.de.md
@@ -12,11 +12,28 @@ Wenn Sie den RustDesk-Server in Ihrem Heimnetzwerk oder einer anderen Netzwerkum
Weitere Details über NAT-Loopback finden Sie bei [Wikipedia](https://de.m.wikipedia.org/wiki/Netzwerkadressübersetzung).
-Auf eine einfache Art und Weise erklärt:
+Wenn Sie den RustDesk-Server in Ihrem Heimnetzwerk oder einer anderen Netzwerkumgebung hinter einer NAT-Firewall einsetzen, **MÜSSEN** der RustDesk-Server und Ihre Clients entweder:
+A: Die lokale IP-Adresse verwenden, um auf einander zuzugreifen ODER:
+B: Eine Firewall haben, die NAT-Loopback unterstützt und aktiviert hat.
-Zum Beispiel: Die öffentliche IP Ihres Routers ist `8.8.8.8`, die LAN-IP Ihres Servers ist `192.168.11.20` und die gewünschte Domäne ist `rustdesk.example.com`. Die Portweiterleitung des Routers ist für Ihren Server in Ihrem LAN eingerichtet (NAT/Router).
+Sie werden möglicherweise feststellen, dass Sie sich nicht über Ihre **öffentliche IP** oder **Domain** (die theoretisch auf Ihre öffentliche IP verweist) mit Ihrem Server verbinden können.
-Ihr Client und Ihr Server befinden sich hinter demselben Router, so dass Ihre LAN-Geräte eine Verbindung zu `rustdesk.example.com` herstellen. Zuerst wird die Domänen-IP abgefragt, die `8.8.8.8` sein wird, und eine Verbindung zu dieser IP hergestellt. Dann weiß Ihr Router möglicherweise **nicht**, wohin diese Verbindung gehen muss, und er denkt, dass diese Verbindung zum Router selbst gehen sollte, und Ihre Verbindung wird fehlschlagen.
+## Problem
+In diesem Beispiel verfolgen wir, was passiert, wenn LAN-Geräte versuchen, sich mit `rustdesk.example.com` zu verbinden. Nehmen wir an, die öffentliche IP Ihres Routers ist `172.16.16.1`, die LAN-IP Ihres Servers ist `192.168.11.20` und die gewünschte Domäne ist `rustdesk.example.com`, und Sie haben einen Client mit '192.168.11.2'.
+
+Wenn Sie einen Server hinter der NAT des Routers einrichten, können Sie eine Portweiterleitung im Router hinzufügen, um alle eingehenden Nachrichten an die ÖFFENTLICHE IP 172.16.16.1 an den Server unter 192.168.11.20 weiterzuleiten.
+
+Wenn ein LAN-Gerät auf das Internet zugreifen möchte, z. B. auf einen Webserver unter 8.8.8.8, sendet es die Anfrage als von 192.168.11.2 kommend und sendet sie an den Router. Der Router fängt diese Anfrage ab und schreibt sie so um, dass sie an 8.8.8.8 als von 172.16.16.1 kommend gesendet wird. Wenn 8.8.8.8 an 172.16.16.1 antwortet, prüft der Router auf eine vorherige Verbindung und leitet diese Antwort zurück an 192.168.11.2.
+
+Wenn der Benutzer bei 8.8.8.8 eine Nachricht an unser Netzwerk mit 172.16.16.1 sendet, schreibt die Portweiterleitungsregel das Ziel von 172.16.16.1 an den Server bei 192.168.11.20 um, wobei die Quelle der Anfrage bei 8.8.8.8 bleibt, damit der Server (mehr oder weniger) direkt an 8.8.8.8 antworten kann.
+
+Wenn der Benutzer bei 8.8.8.8 beschließt, unser Netzwerk zu hacken und behauptet, seine Nachrichten von 192.168.11.2 zu senden, weiß der Router, dass Verkehr von 192.168.11.2 nur von LAN-Geräten gültig ist und blockiert diesen Verkehr normalerweise.
+
+Das Problem tritt auf, wenn Sie versuchen, zurück ins LAN zu schleifen. Wenn das LAN-Gerät versucht, sich mit `rustdesk.example.com` zu verbinden, was `172.16.16.1` sein wird. An diesem Punkt hat der Router viele Entscheidungen zu treffen. Er hat gerade eine Nachricht von seinem LAN-Port an seinen WAN-Port gesendet, die VON 192.168.11.2 kommt und an 172.16.16.1 geht. Sobald sie den WAN-Port erreicht, ist diese Nachricht für sich allein nicht von dem obigen Beispiel zu unterscheiden, bei dem jemand im Internet versuchte, in unser Netzwerk zu hacken.
+
+Die NAT-Loopback-Funktion ändert effektiv den Quellteil "Von 192.168.11.2" der Adresse früher im Prozess, so dass sie weiß, dass sie die NAT-Tabelle verwenden muss, um Nachrichten zwischen dem Server und dem Client hin und her zu leiten.
+
+Wenn es ein Problem mit Verbindungen nur innerhalb des LANs gibt, aber es von außerhalb gut funktioniert, könnte dies das Problem sein, das Sie haben.
## Lösungen
Es gibt drei Möglichkeiten, dieses Problem zu lösen.
@@ -39,21 +56,21 @@ Hier ist ein Beispiel:
#### AdGuard Home
Das Blockieren von Werbung kann Probleme verursachen. Wenn Sie keine Lösung finden und diese Funktion deaktivieren möchten, klicken Sie auf die Schaltfläche "Disable protection".
-
+
Gehen Sie zur Einstellung "DNS rewrites".
-
+
Klicken Sie auf "Add DNS rewrite", und geben Sie Ihre `Domain` und die `LAN-IP` des Servers in das Feld ein.
-
+
So sieht das Endergebnis aus.
-
+
***Vergessen Sie nicht, Ihrem AdGuard Home das LAN-DHCP Ihres Routers zuzuweisen!***
@@ -61,14 +78,14 @@ So sieht das Endergebnis aus.
#### Pi-hole
Das Blockieren von Werbung kann Probleme verursachen. Wenn Sie keine Lösung finden und diese Funktion deaktivieren möchten, klicken Sie im Untermenü "Disable Blocking" auf die Schaltfläche "Indefinitely".
-
+
Gehen Sie zu "Local DNS → DNS Records".
Geben Sie Ihre `Domain` und `IP` in das Feld ein und klicken Sie auf "Add".
Das Endergebnis können Sie anhand der gelben Markierung in diesem Bild überprüfen.
-
+
***Vergessen Sie nicht, Ihrem Pi-hole das LAN-DHCP Ihres Routers zuzuweisen!***
diff --git a/content/self-host/nat-loopback-issues/_index.en.md b/content/self-host/nat-loopback-issues/_index.en.md
index 22082c9..02e3a21 100644
--- a/content/self-host/nat-loopback-issues/_index.en.md
+++ b/content/self-host/nat-loopback-issues/_index.en.md
@@ -56,21 +56,21 @@ Here is an example:
#### AdGuard Home
Blocking ads may cause problems, if you don't want to figure out the solution and want to disable this functionality, click "Disable protection" button.
-
+
Go to "DNS rewrites" setting.
-
+
Click "Add DNS rewrite", then type your `domain` and server's `LAN IP` in the field.
-
+
Here is what the final result looks like.
-
+
***Don't forget to assign your AdGuard Home to your router's LAN DHCP!***
@@ -78,14 +78,14 @@ Here is what the final result looks like.
#### Pi-hole
Blocking ads may cause problems, if you don't want to figure out the solution and want to disable this functionality, click "Indefinitely" button within the "Disable Blocking" submenu.
-
+
Go to "Local DNS → DNS Records".
Type your `domain` and `IP` to the box, than click "Add".
To check the final results, check the yellow lines in this picture.
-
+
***Don't forget to assign your Pi-hole to your router's LAN DHCP!***
diff --git a/content/self-host/nat-loopback-issues/_index.es.md b/content/self-host/nat-loopback-issues/_index.es.md
index 17f5b77..21781aa 100644
--- a/content/self-host/nat-loopback-issues/_index.es.md
+++ b/content/self-host/nat-loopback-issues/_index.es.md
@@ -56,21 +56,21 @@ Aquí hay un ejemplo:
#### AdGuard Home
Bloquear anuncios puede causar problemas, si no quieres averiguar la solución y quieres deshabilitar esta funcionalidad, haz clic en el botón "Deshabilitar protección".
-
+
Ve a la configuración "Reescrituras DNS".
-
+
Haz clic en "Agregar reescritura DNS", luego escribe tu `dominio` y la `IP LAN` del servidor en el campo.
-
+
Así es como se ve el resultado final.
-
+
***¡No olvides asignar tu AdGuard Home al DHCP LAN de tu router!***
@@ -78,14 +78,14 @@ Así es como se ve el resultado final.
#### Pi-hole
Bloquear anuncios puede causar problemas, si no quieres averiguar la solución y quieres deshabilitar esta funcionalidad, haz clic en el botón "Indefinidamente" dentro del submenú "Deshabilitar Bloqueo".
-
+
Ve a "DNS Local → Registros DNS".
Escribe tu `dominio` e `IP` en la caja, luego haz clic en "Agregar".
Para verificar los resultados finales, revisa las líneas amarillas en esta imagen.
-
+
***¡No olvides asignar tu Pi-hole al DHCP LAN de tu router!***
diff --git a/content/self-host/nat-loopback-issues/_index.fr.md b/content/self-host/nat-loopback-issues/_index.fr.md
index 5aa2cb3..b944cf9 100644
--- a/content/self-host/nat-loopback-issues/_index.fr.md
+++ b/content/self-host/nat-loopback-issues/_index.fr.md
@@ -56,21 +56,21 @@ Voici un exemple :
#### AdGuard Home
Bloquer les publicités peut causer des problèmes, si vous ne voulez pas comprendre la solution et voulez désactiver cette fonctionnalité, cliquez sur le bouton "Désactiver la protection".
-
+
Allez dans les paramètres "Réécritures DNS".
-
+
Cliquez sur "Ajouter une réécriture DNS", puis tapez votre `domaine` et l'`IP LAN` du serveur dans le champ.
-
+
Voici à quoi ressemble le résultat final.
-
+
***N'oubliez pas d'assigner votre AdGuard Home au DHCP LAN de votre routeur !***
@@ -78,14 +78,14 @@ Voici à quoi ressemble le résultat final.
#### Pi-hole
Bloquer les publicités peut causer des problèmes, si vous ne voulez pas comprendre la solution et voulez désactiver cette fonctionnalité, cliquez sur le bouton "Indéfiniment" dans le sous-menu "Désactiver le blocage".
-
+
Allez dans "DNS local → Enregistrements DNS".
Tapez votre `domaine` et `IP` dans la boîte, puis cliquez sur "Ajouter".
Pour vérifier les résultats finaux, regardez les lignes jaunes dans cette image.
-
+
***N'oubliez pas d'assigner votre Pi-hole au DHCP LAN de votre routeur !***
diff --git a/content/self-host/nat-loopback-issues/_index.it.md b/content/self-host/nat-loopback-issues/_index.it.md
index 30ef93d..c4408e1 100644
--- a/content/self-host/nat-loopback-issues/_index.it.md
+++ b/content/self-host/nat-loopback-issues/_index.it.md
@@ -56,21 +56,21 @@ Ecco un esempio:
#### AdGuard Home
Bloccare le pubblicità può causare problemi, se non vuoi capire la soluzione e vuoi disabilitare questa funzionalità, clicca il bottone "Disabilita protezione".
-
+
Vai alle impostazioni "Riscritture DNS".
-
+
Clicca "Aggiungi riscrittura DNS", poi digita il tuo `dominio` e l'`IP LAN` del server nel campo.
-
+
Ecco come appare il risultato finale.
-
+
***Non dimenticare di assegnare il tuo AdGuard Home al DHCP LAN del tuo router!***
@@ -78,14 +78,14 @@ Ecco come appare il risultato finale.
#### Pi-hole
Bloccare le pubblicità può causare problemi, se non vuoi capire la soluzione e vuoi disabilitare questa funzionalità, clicca il bottone "Indefinitamente" nel sottomenu "Disabilita Blocco".
-
+
Vai a "DNS Locale → Record DNS".
Digita il tuo `dominio` e `IP` nella casella, poi clicca "Aggiungi".
Per controllare i risultati finali, controlla le righe gialle in questa immagine.
-
+
***Non dimenticare di assegnare il tuo Pi-hole al DHCP LAN del tuo router!***
diff --git a/content/self-host/nat-loopback-issues/_index.ja.md b/content/self-host/nat-loopback-issues/_index.ja.md
index 4c0c4bb..bce70d8 100644
--- a/content/self-host/nat-loopback-issues/_index.ja.md
+++ b/content/self-host/nat-loopback-issues/_index.ja.md
@@ -56,21 +56,21 @@ LAN内にいる間だけ接続に問題があるが、オフサイトからは
#### AdGuard Home
広告のブロックは問題を引き起こす可能性があります。解決策を理解したくなく、この機能を無効にしたい場合は、「保護を無効にする」ボタンをクリックしてください。
-
+
「DNS書き換え」設定に移動します。
-
+
「DNS書き換えを追加」をクリックし、フィールドに`ドメイン`とサーバーの`LAN IP`を入力します。
-
+
最終結果は以下のようになります。
-
+
***AdGuard HomeをルーターのLAN DHCPに割り当てることを忘れないでください!***
@@ -78,14 +78,14 @@ LAN内にいる間だけ接続に問題があるが、オフサイトからは
#### Pi-hole
広告のブロックは問題を引き起こす可能性があります。解決策を理解したくなく、この機能を無効にしたい場合は、「ブロックを無効にする」サブメニュー内の「無期限」ボタンをクリックしてください。
-
+
「ローカルDNS → DNSレコード」に移動します。
ボックスに`ドメイン`と`IP`を入力し、「追加」をクリックします。
最終結果を確認するには、この画像の黄色い線を確認してください。
-
+
***Pi-holeをルーターのLAN DHCPに割り当てることを忘れないでください!***
diff --git a/content/self-host/nat-loopback-issues/_index.pt.md b/content/self-host/nat-loopback-issues/_index.pt.md
index 9a4106c..bc81f94 100644
--- a/content/self-host/nat-loopback-issues/_index.pt.md
+++ b/content/self-host/nat-loopback-issues/_index.pt.md
@@ -56,21 +56,21 @@ Aqui está um exemplo:
#### AdGuard Home
Bloquear anúncios pode causar problemas, se você não quer descobrir a solução e quer desabilitar esta funcionalidade, clique no botão "Desabilitar proteção".
-
+
Vá para a configuração "Reescritas DNS".
-
+
Clique em "Adicionar reescrita DNS", depois digite seu `domínio` e o `IP LAN` do servidor no campo.
-
+
Aqui está como fica o resultado final.
-
+
***Não esqueça de atribuir seu AdGuard Home ao DHCP LAN do seu roteador!***
@@ -78,14 +78,14 @@ Aqui está como fica o resultado final.
#### Pi-hole
Bloquear anúncios pode causar problemas, se você não quer descobrir a solução e quer desabilitar esta funcionalidade, clique no botão "Indefinidamente" dentro do submenu "Desabilitar Bloqueio".
-
+
Vá para "DNS Local → Registros DNS".
Digite seu `domínio` e `IP` na caixa, depois clique em "Adicionar".
Para verificar os resultados finais, verifique as linhas amarelas nesta imagem.
-
+
***Não esqueça de atribuir seu Pi-hole ao DHCP LAN do seu roteador!***
diff --git a/content/self-host/nat-loopback-issues/_index.zh-cn.md b/content/self-host/nat-loopback-issues/_index.zh-cn.md
index 22925bc..0c41b4c 100644
--- a/content/self-host/nat-loopback-issues/_index.zh-cn.md
+++ b/content/self-host/nat-loopback-issues/_index.zh-cn.md
@@ -54,21 +54,21 @@ NAT 环回功能将有效地在过程早期更改源"从 192.168.11.2"地址部
#### AdGuard Home
拦截广告可能会导致问题,如果您不想找出解决方案并想禁用此功能,请点击"禁用保护"按钮。
-
+
转到"DNS 重写"设置。
-
+
点击"添加 DNS 重写",然后在字段中输入您的`域名`和服务器的`LAN IP`。
-
+
这是最终结果的样子。
-
+
***不要忘记将您的 AdGuard Home 分配给路由器的 LAN DHCP!***
@@ -76,14 +76,14 @@ NAT 环回功能将有效地在过程早期更改源"从 192.168.11.2"地址部
#### Pi-hole
拦截广告可能会导致问题,如果您不想找出解决方案并想禁用此功能,请在"禁用拦截"子菜单中点击"无限期"按钮。
-
+
转到"本地 DNS → DNS 记录"。
在框中输入您的`域名`和`IP`,然后点击"添加"。
要检查最终结果,请查看此图片中的黄色线条。
-
+
***不要忘记将您的 Pi-hole 分配给路由器的 LAN DHCP!***
diff --git a/content/self-host/nat-loopback-issues/_index.zh-tw.md b/content/self-host/nat-loopback-issues/_index.zh-tw.md
index 15a20f7..13c395a 100644
--- a/content/self-host/nat-loopback-issues/_index.zh-tw.md
+++ b/content/self-host/nat-loopback-issues/_index.zh-tw.md
@@ -12,11 +12,28 @@ pre: "2.5. "
更多有關 NAT Loopback 的詳情,請參閱 [維基百科(英文)](https://en.wikipedia.org/wiki/Network_address_translation#NAT_hairpinning)
-用較簡單的方式說明:
+當您在家庭網路或任何其他位於 NAT 防火牆後的網路環境中部署 RustDesk 伺服器時,RustDesk 伺服器和您的客戶端**必須**:
+A:使用本地 IP 地址互相訪問 或:
+B:擁有支援並已啟用 NAT Loopback 的防火牆。
-舉例來說: 您的路由器的公共IP是 ``8.8.8.8``,您的伺服器的區網IP是 ``192.168.11.20`` 您所希望的網域是 ``rustdesk.example.com``,然後路由器的 port forwarding 已正確設置。
+您可能會發現無法通過**公共 IP** 或**域名**(理論上指向您的公共 IP)連接到您的伺服器。
-您的客戶端和伺服器在同一臺路由器之後,所以當您區域網路的裝置要連線到 ``rustdesk.example.com`` 的時候,首先,它會解析這個網域的IP,也就是 ``8.8.8.8``,然後連接到這個IP,接著您的路由器可能會直接**不知道**這條連線該去哪裡,然後它會覺得這個連接應該會想要去路由器它自己,接著您的連結就會失敗。
+## 問題
+在這個例子中,我們將追蹤當 LAN 設備嘗試連接到 `rustdesk.example.com` 時會發生什麼。假設您的路由器的公共 IP 是 `172.16.16.1`,您的伺服器的 LAN IP 是 `192.168.11.20`,您想要的域名是 `rustdesk.example.com`,並且您有一個使用 '192.168.11.2' 的客戶端。
+
+當您在路由器的 NAT 後面設置伺服器時,您可以在路由器中添加一個端口轉發,將任何傳入到公共 IP 172.16.16.1 的消息轉到 192.168.11.20 的伺服器。
+
+當 LAN 設備想要訪問互聯網時,比如 8.8.8.8 上的網頁伺服器,它會將請求作為來自 192.168.11.2 發送,並將其發送到路由器。路由器將攜獲該請求並將該請求重寫為來自 172.16.16.1 發送到 8.8.8.8。當 8.8.8.8 回覆到 172.16.16.1 時,路由器將檢查先前的連接並將該回應重新路由回 192.168.11.2。
+
+如果 8.8.8.8 的用戶使用 172.16.16.1 向我們的網路發送消息,端口轉發規則將重寫 172.16.16.1 的目的地到 192.168.11.20 的伺服器,保留請求的來源為 8.8.8.8,以便伺服器可以(或多或少)直接回應 8.8.8.8。
+
+如果 8.8.8.8 的用戶決定嘗試入侵我們的網路並聲稱其消息來自 192.168.11.2,路由器知道來自 192.168.11.2 的流量只有從 LAN 設備才有效,通常會阻止該流量。
+
+當您嘗試回環到 LAN 時就會出現問題。如果 LAN 設備嘗試連接到 `rustdesk.example.com`,它將是 `172.16.16.1`。此時路由器有許多選擇。它剛剛從它的 LAN 端口向它的 WAN 端口發送了一條消息,來自 192.168.11.2 發往 172.16.16.1。一旦到達 WAN 端口,這條消息本身與上述網路上某人試圖入侵我們網路的例子無法區分。
+
+NAT Loopback 功能將在過程的更早階段有效地更改地址的來源「來自 192.168.11.2」部分,以便它知道必須使用 NAT 表在伺服器和客戶端之間傳遞消息。
+
+如果只有在 LAN 內部時連接有問題,但從外部工作正常,這可能就是您遇到的問題。
## 解決方法
有3個方式可以解決這個問題。
@@ -40,34 +57,34 @@ pre: "2.5. "
#### AdGuard Home
封鎖廣告可能會造成問題,如果您不想要尋找解決方法,並且想要關閉這個功能,請選擇"禁用保護"按鈕。
-
+
去 "DNS 改寫" 設定。
-
+
點擊 "新增 DNS 改寫",接著輸入 ``網域`` 和伺服器的 ``LAN IP`` 至輸入框。
-
+
最終結果看起來像這樣。
-
+
***別忘記指派 AdGuard Home 到您路由器的LAN DHCP!***
### PiHole
封鎖廣告可能會造成問題,如果您不想要尋找解決方法,並且想要關閉這個功能,請選擇 "Disable Blocking" 中的 "Indefinitely" 按鈕。
-
+
前往 Local DNS > DNS Records
輸入 ``網域`` 和伺服器的 ``LAN IP`` 至輸入框, 接著點擊 "Add"。
要檢查最終結果,請檢查圖片中的黃線。
-
+
***別忘記指派 PiHole 到您路由器的LAN DHCP!***
diff --git a/content/self-host/rustdesk-server-oss/Docker/_index.de.md b/content/self-host/rustdesk-server-oss/Docker/_index.de.md
index 19c99b0..72eed48 100644
--- a/content/self-host/rustdesk-server-oss/Docker/_index.de.md
+++ b/content/self-host/rustdesk-server-oss/Docker/_index.de.md
@@ -3,38 +3,47 @@ title: Docker
weight: 7
---
+> Hier ist ein weiteres gutes Tutorial: [Erstellen Sie Ihre eigene Remote-Desktop-Lösung: RustDesk Self-Hosted in der Cloud mit Docker (Hetzner)](https://www.linkedin.com/pulse/building-your-own-remote-desktop-solution-rustdesk-cloud-montinaro-bv94f)
+
## Installieren Sie Ihren eigenen Server mit Docker
### Anforderungen
-Sie müssen Docker/Podman installiert haben, um einen RustDesk-Server als Docker-Container zu betreiben. Im Zweifelsfall installieren Sie Docker mit dieser [Anleitung](https://docs.docker.com/engine/install), um sicherzustellen, dass es auf dem neuesten Stand ist!
+Sie müssen Docker/Podman installiert haben, um einen rustdesk-server als Docker-Container auszuführen. Im Zweifelsfall installieren Sie Docker mit dieser [Anleitung](https://docs.docker.com/engine/install), um sicherzustellen, dass es auf dem neuesten Stand ist!
-Standardmäßig lauscht `hbbs` auf 21114 (TCP für die Webkonsole, nur in der Pro-Version verfügbar), 21115 (TCP), 21116 (TCP/UDP) und 21118 (TCP), `hbbr` lauscht auf 21117 (TCP) und 21119 (TCP). Diese Ports müssen in der Firewall geöffnet sein. **Bitte beachten Sie, dass 21116 sowohl für TCP als auch für UDP aktiviert sein muss.** 21115 wird für den NAT-Typ-Test verwendet, 21116/UDP wird für die ID-Registrierung und den Heartbeat-Dienst verwendet, 21116/TCP wird für das TCP-Hole-Punching und den Verbindungsdienst verwendet, 21117 wird für die Relay-Dienste verwendet und 21118 sowie 21119 werden zur Unterstützung von Webclients verwendet. *Wenn Sie die Webclient-Unterstützung (21118, 21119) nicht benötigen, können die entsprechenden Ports deaktiviert werden.*
+Stellen Sie sicher, dass Sie diese Ports in der Firewall öffnen:
+- `hbbs`:
+ - `21114` (TCP): für die Webkonsole verwendet, nur in der `Pro`-Version verfügbar.
+ - `21115` (TCP): für den NAT-Typ-Test verwendet.
+ - `21116` (TCP/UDP): **Bitte beachten Sie, dass `21116` sowohl für TCP als auch für UDP aktiviert sein sollte.** `21116/UDP` wird für die ID-Registrierung und den Heartbeat-Dienst verwendet. `21116/TCP` wird für das TCP-Hole-Punching und den Verbindungsdienst verwendet.
+ - `21118` (TCP): zur Unterstützung von Webclients verwendet.
+- `hbbr`:
+ - `21117` (TCP): für die Relay-Dienste verwendet.
+ - `21119` (TCP): zur Unterstützung von Webclients verwendet.
-- TCP (**21114, 21115, 21116, 21117, 21118, 21119**)
-- UDP (**21116**)
+*Wenn Sie keine Webclient-Unterstützung benötigen, können die entsprechenden Ports `21118`, `21119` deaktiviert werden.*
### Docker-Beispiele
```sh
sudo docker image pull rustdesk/rustdesk-server
-sudo docker run --name hbbs -v ./data:/root -td --net=host rustdesk/rustdesk-server hbbs
-sudo docker run --name hbbr -v ./data:/root -td --net=host rustdesk/rustdesk-server hbbr
+sudo docker run --name hbbs -v ./data:/root -td --net=host --restart unless-stopped rustdesk/rustdesk-server hbbs
+sudo docker run --name hbbr -v ./data:/root -td --net=host --restart unless-stopped rustdesk/rustdesk-server hbbr
```
{{% notice note %}}
-`--net=host` funktioniert nur unter **Linux**, was dazu führt, dass `hbbs`/`hbbr` die tatsächliche, eingehende IP-Adresse sehen und nicht die Container-IP (172.17.0.1).
-Wenn `--net=host` gut funktioniert, wird die Option `-p` nicht verwendet. Wenn Sie unter Windows arbeiten, lassen Sie `sudo` und `--net=host` weg.
+`--net=host` funktioniert nur unter **Linux**, wodurch `hbbs`/`hbbr` die tatsächliche eingehende IP-Adresse anstelle der Container-IP (172.17.0.1) sehen.
+Wenn `--net=host` gut funktioniert, werden die `-p`-Optionen nicht verwendet. Wenn Sie unter Windows arbeiten, lassen Sie `sudo` und `--net=host` weg.
**Bitte entfernen Sie `--net=host`, wenn Sie Verbindungsprobleme auf Ihrer Plattform haben.**
{{% /notice %}}
{{% notice note %}}
-Sie können die Protokolle mit `docker logs hbbs` ansehen, wenn sie mit `-td` nicht zu sehen sind. Oder Sie können mit `-it` arbeiten, `hbbs/hbbr` wird nicht im Daemon-Modus laufen.
+Wenn Sie mit `-td` keine Logs sehen können, können Sie Logs über `docker logs hbbs` anzeigen. Oder Sie können mit `-it` ausführen, dann laufen `hbbs/hbbr` nicht im Daemon-Modus.
{{% /notice %}}
### Docker Compose-Beispiele
-Um die Dockerdateien mit `compose.yml` wie hier beschrieben ausführen zu können, müssen Sie [Docker Compose](https://docs.docker.com/compose/) installiert haben.
+Um die Docker-Dateien mit der hier beschriebenen `compose.yml` auszuführen, müssen Sie [Docker Compose](https://docs.docker.com/compose/) installiert haben.
```yaml
services:
@@ -59,3 +68,67 @@ services:
network_mode: "host"
restart: unless-stopped
```
+
+Wenn Sie Konfigurationsänderungen vornehmen müssen, z.B. ALWAYS_USE_RELAY=Y setzen, können Sie environment in der docker-compose.yml verwenden
+
+```yaml
+services:
+ hbbs:
+ container_name: hbbs
+ image: rustdesk/rustdesk-server:latest
+ environment:
+ - ALWAYS_USE_RELAY=Y
+ command: hbbs
+ volumes:
+ - ./data:/root
+ network_mode: "host"
+
+ depends_on:
+ - hbbr
+ restart: unless-stopped
+
+ hbbr:
+ container_name: hbbr
+ image: rustdesk/rustdesk-server:latest
+ command: hbbr
+ volumes:
+ - ./data:/root
+ network_mode: "host"
+ restart: unless-stopped
+```
+
+### Podman Quadlet-Beispiele
+
+Wenn Sie die Container mit Podman als systemd-Dienst ausführen möchten, können Sie diese Beispiel-Podman-Quadlet-Konfigurationen verwenden:
+
+```ini
+[Container]
+AutoUpdate=registry
+Image=ghcr.io/rustdesk/rustdesk-server:latest
+Exec=hbbs
+Volume=/path/to/rustdesk-server/data:/root
+Network=host
+
+[Service]
+Restart=always
+
+[Install]
+WantedBy=default.target
+```
+
+oder
+
+```ini
+[Container]
+AutoUpdate=registry
+Image=ghcr.io/rustdesk/rustdesk-server:latest
+Exec=hbbr
+Volume=/path/to/rustdesk-server/data:/root
+Network=host
+
+[Service]
+Restart=always
+
+[Install]
+WantedBy=default.target
+```
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-oss/_index.es.md b/content/self-host/rustdesk-server-oss/_index.es.md
index ff7d528..026a9e1 100644
--- a/content/self-host/rustdesk-server-oss/_index.es.md
+++ b/content/self-host/rustdesk-server-oss/_index.es.md
@@ -1,11 +1,13 @@
---
-title: Self-host OSS
-weight: 5
-chapter: true
+title: RustDesk Server OSS
+weight: 100
+pre: "2.1. "
---
-# Self-host OSS
+Por favor únete a nuestro [Discord](https://discord.com/invite/nDceKgxnkV) si deseas hablar con nosotros sobre el alojamiento propio de tu propio [servidor RustDesk de código abierto](https://github.com/rustdesk/rustdesk-server).
-Por favor únete a nuestro [Discord](https://discord.com/invite/nDceKgxnkV) si desea hablar con nosotros sobre el alojamiento propio de su propio servidor RustDesk.
+{{% notice note %}}
+Si construyes tu propio servidor en tu hogar/oficina y no puedes conectarte a través de IP/dominio público, por favor revisa [este artículo](https://rustdesk.com/docs/es/self-host/nat-loopback-issues/).
+{{% /notice %}}
{{% children depth="3" showhidden="true" %}}
diff --git a/content/self-host/rustdesk-server-oss/_index.fr.md b/content/self-host/rustdesk-server-oss/_index.fr.md
index 9428a72..d70d934 100644
--- a/content/self-host/rustdesk-server-oss/_index.fr.md
+++ b/content/self-host/rustdesk-server-oss/_index.fr.md
@@ -1,11 +1,13 @@
---
-title: Auto-héberger son serveur OSS
-weight: 5
-chapter: true
+title: RustDesk Server OSS
+weight: 100
+pre: "2.1. "
---
-# Auto-héberger son serveur OSS
+Veuillez rejoindre notre [Discord](https://discord.com/invite/nDceKgxnkV) si vous souhaitez discuter avec nous de l'auto-hébergement de votre propre [serveur RustDesk open source](https://github.com/rustdesk/rustdesk-server).
-Nous développons continuellement le serveur, si vous avez des commentaires, veuillez rejoindre notre discussion [Discord](https://discord.com/invite/nDceKgxnkV).
+{{% notice note %}}
+Si vous construisez votre propre serveur à votre domicile/bureau et que vous ne pouvez pas vous y connecter via une IP/domaine public, veuillez consulter [cet article](https://rustdesk.com/docs/fr/self-host/nat-loopback-issues/).
+{{% /notice %}}
{{% children depth="3" showhidden="true" %}}
diff --git a/content/self-host/rustdesk-server-oss/_index.it.md b/content/self-host/rustdesk-server-oss/_index.it.md
index 13e39f4..e8ad9d8 100755
--- a/content/self-host/rustdesk-server-oss/_index.it.md
+++ b/content/self-host/rustdesk-server-oss/_index.it.md
@@ -1,11 +1,13 @@
---
-title: Self-host OSS
-weight: 5
-chapter: true
+title: RustDesk Server OSS
+weight: 100
+pre: "2.1. "
---
-# Self-host OSS
+Per favore unisciti al nostro [Discord](https://discord.com/invite/nDceKgxnkV) se desideri parlare con noi dell'hosting autonomo del tuo [server RustDesk open source](https://github.com/rustdesk/rustdesk-server).
-Stiamo sviluppando continuamente il server, se hai commenti, partecipa alla nostra discussione su [Discord](https://discord.com/invite/nDceKgxnkV).
+{{% notice note %}}
+Se costruisci il tuo server a casa/ufficio e non riesci a connetterti tramite IP/dominio pubblico, per favore controlla [questo articolo](https://rustdesk.com/docs/it/self-host/nat-loopback-issues/).
+{{% /notice %}}
{{% children depth="3" showhidden="true" %}}
diff --git a/content/self-host/rustdesk-server-oss/_index.ja.md b/content/self-host/rustdesk-server-oss/_index.ja.md
index ead0561..c0bebfa 100755
--- a/content/self-host/rustdesk-server-oss/_index.ja.md
+++ b/content/self-host/rustdesk-server-oss/_index.ja.md
@@ -1,11 +1,13 @@
---
-title: セルフホスト OSS
-weight: 5
-chapter: true
+title: RustDesk Server OSS
+weight: 100
+pre: "2.1. "
---
-# セルフホスト OSS
+自分の[オープンソースRustDeskサーバー](https://github.com/rustdesk/rustdesk-server)のセルフホスティングについて私たちと話したい場合は、[Discord](https://discord.com/invite/nDceKgxnkV)に参加してください。
-サーバーの開発は継続的に行っています。困ったことがあれば[Discord](https://discord.com/invite/nDceKgxnkV)に参加してください。
+{{% notice note %}}
+自宅/オフィスでサーバーを構築し、パブリックIP/ドメインで接続できない場合は、[この記事](https://rustdesk.com/docs/ja/self-host/nat-loopback-issues/)を確認してください。
+{{% /notice %}}
{{% children depth="3" showhidden="true" %}}
diff --git a/content/self-host/rustdesk-server-oss/_index.zh-tw.md b/content/self-host/rustdesk-server-oss/_index.zh-tw.md
index 92cfade..1a534a1 100755
--- a/content/self-host/rustdesk-server-oss/_index.zh-tw.md
+++ b/content/self-host/rustdesk-server-oss/_index.zh-tw.md
@@ -1,11 +1,13 @@
---
-title: 自架伺服器 OSS
-weight: 5
-chapter: true
+title: RustDesk Server OSS
+weight: 100
+pre: "2.1. "
---
-# 自架伺服器 OSS
+如果您想要和我們聊聊關於自架您自己的[開源 RustDesk 伺服器](https://github.com/rustdesk/rustdesk-server),請加入我們的 [Discord](https://discord.com/invite/nDceKgxnkV)。
-如果您想要和我們聊聊關於[自架 RustDesk 伺服器](https://github.com/rustdesk/rustdesk-server)的事,請加入我們的 [Discord](https://discord.com/invite/nDceKgxnkV) 伺服器。
+{{% notice note %}}
+如果您在家中/辦公室架設自己的伺服器,但無法透過公共 IP/網域連接,請查看[這篇文章](https://rustdesk.com/docs/zh-tw/self-host/nat-loopback-issues/)。
+{{% /notice %}}
{{% children depth="3" showhidden="true" %}}
diff --git a/content/self-host/rustdesk-server-oss/install/_index.de.md b/content/self-host/rustdesk-server-oss/install/_index.de.md
index 498306e..70e3465 100644
--- a/content/self-host/rustdesk-server-oss/install/_index.de.md
+++ b/content/self-host/rustdesk-server-oss/install/_index.de.md
@@ -3,4 +3,50 @@ title: Installation
weight: 1
---
-[English](/docs/en/self-host/rustdesk-server-oss/install/)
+## Video-Tutorials
+Es gibt viele Video-Tutorials auf YouTube, https://github.com/rustdesk/rustdesk/wiki/FAQ#video-tutorials.
+
+## Server-Anforderungen
+Die Hardware-Anforderungen sind sehr niedrig; die Mindestkonfiguration eines einfachen Cloud-Servers reicht aus, und die CPU- und Speicheranforderungen sind minimal. Sie können auch einen Raspberry Pi oder etwas Ähnliches verwenden. Bezüglich der Netzwerkgröße wird bei einem Fehlschlag der direkten TCP-Lochbohrverbindung der Relay-Verkehr verbraucht. Der Datenverkehr einer Relay-Verbindung liegt je nach Auflösungseinstellungen und Bildschirmaktualisierung zwischen 30 K/s und 3 M/s (1920x1080 Bildschirm). Wenn es nur für Büroarbeiten benötigt wird, liegt der Datenverkehr bei etwa 100 K/s.
+
+## Firewall
+Wenn Sie UFW installiert haben, verwenden Sie die folgenden Befehle zur Konfiguration der Firewall:
+```
+ufw allow 21114:21119/tcp
+ufw allow 21116/udp
+sudo ufw enable
+```
+
+## Installation
+### Methode 1: Docker (Empfohlen)
+
+```
+bash <(wget -qO- https://get.docker.com)
+wget rustdesk.com/oss.yml -O compose.yml
+sudo docker compose up -d
+```
+
+Für weitere Details schauen Sie bitte unter [Docker](/docs/en/self-host/rustdesk-server-oss/docker/).
+
+### Methode 2: Installieren Sie Ihren eigenen Server als systemd-Dienst mit einem einfachen Installationsskript
+Das Skript wird auf [Techahold](https://github.com/techahold/rustdeskinstall) gehostet und auf unserem [Discord](https://discord.com/invite/nDceKgxnkV) unterstützt.
+
+Derzeit lädt das Skript die Relay- und Signal-Server (hbbr und hbbs) herunter und richtet sie ein, generiert Konfigurationen und hostet sie auf einer passwortgeschützten Webseite für eine einfache Bereitstellung auf Clients.
+
+Führen Sie die folgenden Befehle aus:
+```
+wget https://raw.githubusercontent.com/techahold/rustdeskinstall/master/install.sh
+chmod +x install.sh
+./install.sh
+```
+
+Es gibt auch ein Update-Skript im Repository von [Techahold](https://github.com/techahold/rustdeskinstall).
+
+Notieren Sie sich von dort die IP/DNS und den Schlüssel, die am Ende der Installation angezeigt werden, und fügen Sie diese in die Client-Einstellungen > Netzwerk > ID/Relay-Server in die Felder `ID-Server` und `Schlüssel` ein, wobei Sie die anderen Felder leer lassen (siehe Hinweis unten).
+
+### Methode 3: Installieren Sie Ihren eigenen Server als systemd-Dienst mit deb-Datei für Debian-Distributionen
+
+Bitte [laden Sie](https://github.com/rustdesk/rustdesk-server/releases/latest) die deb-Dateien selbst herunter und installieren Sie sie mit `apt-get -f install .deb` oder `dpkg -i .deb`.
+
+## Client konfigurieren
+Bitte schauen Sie [hier](/docs/en/self-host/client-configuration/#2-manual-config).
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-oss/install/_index.es.md b/content/self-host/rustdesk-server-oss/install/_index.es.md
index 72c7a65..fd38e66 100644
--- a/content/self-host/rustdesk-server-oss/install/_index.es.md
+++ b/content/self-host/rustdesk-server-oss/install/_index.es.md
@@ -1,6 +1,52 @@
---
-title: Instalación
-weight: 10
+title: Instalación
+weight: 1
---
-[English](/docs/en/self-host/rustdesk-server-oss/install/)
+## Tutoriales en video
+Hay muchos tutoriales en video en YouTube, https://github.com/rustdesk/rustdesk/wiki/FAQ#video-tutorials.
+
+## Requisitos del servidor
+Los requisitos de hardware son muy bajos; la configuración mínima de un servidor en la nube básico es suficiente, y los requisitos de CPU y memoria son mínimos. También puede usar una Raspberry Pi o algo similar. Con respecto al tamaño de la red, si falla la conexión directa de perforación de TCP, se consumirá el tráfico de retransmisión. El tráfico de una conexión de retransmisión está entre 30 K/s y 3 M/s (pantalla 1920x1080) dependiendo de la configuración de resolución y actualización de pantalla. Si es solo para demanda de trabajo de oficina, el tráfico es de alrededor de 100 K/s.
+
+## Firewall
+Si tiene UFW instalado, use los siguientes comandos para configurar el firewall:
+```
+ufw allow 21114:21119/tcp
+ufw allow 21116/udp
+sudo ufw enable
+```
+
+## Instalación
+### Método 1: Docker (Recomendado)
+
+```
+bash <(wget -qO- https://get.docker.com)
+wget rustdesk.com/oss.yml -O compose.yml
+sudo docker compose up -d
+```
+
+Para más detalles, por favor consulte [Docker](/docs/en/self-host/rustdesk-server-oss/docker/).
+
+### Método 2: Instale su propio servidor como servicio systemd usando un script de instalación simple
+El script está alojado en [Techahold](https://github.com/techahold/rustdeskinstall) y tiene soporte en nuestro [Discord](https://discord.com/invite/nDceKgxnkV).
+
+Actualmente, el script descargará y configurará los servidores de retransmisión y señal (hbbr y hbbs), generará configuraciones y las alojará en una página web protegida con contraseña para una implementación simple en los clientes.
+
+Ejecute los siguientes comandos:
+```
+wget https://raw.githubusercontent.com/techahold/rustdeskinstall/master/install.sh
+chmod +x install.sh
+./install.sh
+```
+
+También hay un script de actualización en el repositorio de [Techahold](https://github.com/techahold/rustdeskinstall).
+
+Desde allí, tome nota de la IP/DNS y la clave que se muestran al final de la instalación e insértelas en los campos `Servidor ID` y `Clave` de Configuración > Red > Servidor ID/Retransmisión del cliente, respectivamente, dejando los otros campos en blanco (ver nota a continuación).
+
+### Método 3: Instale su propio servidor como servicio systemd usando archivo deb para distribuciones debian
+
+Por favor [descargue](https://github.com/rustdesk/rustdesk-server/releases/latest) los archivos deb usted mismo e instálelos con `apt-get -f install .deb` o `dpkg -i .deb`.
+
+## Configurar cliente
+Por favor consulte [esto](/docs/en/self-host/client-configuration/#2-manual-config).
diff --git a/content/self-host/rustdesk-server-oss/install/_index.fr.md b/content/self-host/rustdesk-server-oss/install/_index.fr.md
index 2fd7e99..d48b400 100644
--- a/content/self-host/rustdesk-server-oss/install/_index.fr.md
+++ b/content/self-host/rustdesk-server-oss/install/_index.fr.md
@@ -1,6 +1,52 @@
---
title: Installation
-weight: 10
+weight: 1
---
-[English](/docs/en/self-host/rustdesk-server-oss/install/)
+## Tutoriels vidéo
+Il existe de nombreux tutoriels vidéo sur YouTube, https://github.com/rustdesk/rustdesk/wiki/FAQ#video-tutorials.
+
+## Exigences du serveur
+Les exigences matérielles sont très faibles ; la configuration minimale d'un serveur cloud de base est suffisante, et les exigences en CPU et mémoire sont minimales. Vous pouvez également utiliser un Raspberry Pi ou quelque chose de similaire. Concernant la taille du réseau, si la connexion directe par perçage TCP échoue, le trafic de relais sera consommé. Le trafic d'une connexion relais se situe entre 30 K/s et 3 M/s (écran 1920x1080) selon les paramètres de résolution et de mise à jour de l'écran. S'il s'agit uniquement d'une demande de travail de bureau, le trafic est d'environ 100 K/s.
+
+## Pare-feu
+Si vous avez UFW installé, utilisez les commandes suivantes pour configurer le pare-feu :
+```
+ufw allow 21114:21119/tcp
+ufw allow 21116/udp
+sudo ufw enable
+```
+
+## Installation
+### Méthode 1 : Docker (Recommandé)
+
+```
+bash <(wget -qO- https://get.docker.com)
+wget rustdesk.com/oss.yml -O compose.yml
+sudo docker compose up -d
+```
+
+Pour plus de détails, veuillez consulter [Docker](/docs/en/self-host/rustdesk-server-oss/docker/).
+
+### Méthode 2 : Installer votre propre serveur en tant que service systemd à l'aide d'un script d'installation simple
+Le script est hébergé sur [Techahold](https://github.com/techahold/rustdeskinstall) et pris en charge sur notre [Discord](https://discord.com/invite/nDceKgxnkV).
+
+Actuellement, le script téléchargera et configurera les serveurs de relais et de signal (hbbr et hbbs), générera des configurations et les hébergera sur une page Web protégée par mot de passe pour un déploiement simple sur les clients.
+
+Exécutez les commandes suivantes :
+```
+wget https://raw.githubusercontent.com/techahold/rustdeskinstall/master/install.sh
+chmod +x install.sh
+./install.sh
+```
+
+Il y a aussi un script de mise à jour sur le dépôt de [Techahold](https://github.com/techahold/rustdeskinstall).
+
+À partir de là, notez l'IP/DNS et la clé affichés à la fin de l'installation et insérez-les dans les champs `Serveur ID` et `Clé` de Paramètres > Réseau > Serveur ID/Relais du client, respectivement, en laissant les autres champs vides (voir note ci-dessous).
+
+### Méthode 3 : Installer votre propre serveur en tant que service systemd en utilisant un fichier deb pour les distributions debian
+
+Veuillez [télécharger](https://github.com/rustdesk/rustdesk-server/releases/latest) les fichiers deb vous-même et les installer avec `apt-get -f install .deb` ou `dpkg -i .deb`.
+
+## Configurer le client
+Veuillez consulter [ceci](/docs/en/self-host/client-configuration/#2-manual-config).
diff --git a/content/self-host/rustdesk-server-oss/install/_index.it.md b/content/self-host/rustdesk-server-oss/install/_index.it.md
index 0261799..d189f2f 100644
--- a/content/self-host/rustdesk-server-oss/install/_index.it.md
+++ b/content/self-host/rustdesk-server-oss/install/_index.it.md
@@ -1,6 +1,52 @@
---
title: Installazione
-weight: 10
+weight: 1
---
-[English](/docs/en/self-host/rustdesk-server-oss/install)
\ No newline at end of file
+## Tutorial video
+Ci sono molti tutorial video su YouTube, https://github.com/rustdesk/rustdesk/wiki/FAQ#video-tutorials.
+
+## Requisiti del server
+I requisiti hardware sono molto bassi; la configurazione minima di un server cloud di base è sufficiente e i requisiti di CPU e memoria sono minimi. Puoi anche utilizzare un Raspberry Pi o qualcosa di simile. Per quanto riguarda la dimensione della rete, se la connessione diretta con perforazione TCP fallisce, verrà consumato il traffico di relay. Il traffico di una connessione relay è compreso tra 30 K/s e 3 M/s (schermo 1920x1080) a seconda delle impostazioni di risoluzione e aggiornamento dello schermo. Se è solo per esigenze di lavoro d'ufficio, il traffico è di circa 100 K/s.
+
+## Firewall
+Se hai UFW installato, usa i seguenti comandi per configurare il firewall:
+```
+ufw allow 21114:21119/tcp
+ufw allow 21116/udp
+sudo ufw enable
+```
+
+## Installazione
+### Metodo 1: Docker (Consigliato)
+
+```
+bash <(wget -qO- https://get.docker.com)
+wget rustdesk.com/oss.yml -O compose.yml
+sudo docker compose up -d
+```
+
+Per maggiori dettagli, consulta [Docker](/docs/en/self-host/rustdesk-server-oss/docker/).
+
+### Metodo 2: Installa il tuo server come servizio systemd usando uno script di installazione semplice
+Lo script è ospitato su [Techahold](https://github.com/techahold/rustdeskinstall) e supportato sul nostro [Discord](https://discord.com/invite/nDceKgxnkV).
+
+Attualmente lo script scaricherà e configurerà i server Relay e Signal (hbbr e hbbs), genererà le configurazioni e le ospiterà su una pagina web protetta da password per una semplice distribuzione ai client.
+
+Esegui i seguenti comandi:
+```
+wget https://raw.githubusercontent.com/techahold/rustdeskinstall/master/install.sh
+chmod +x install.sh
+./install.sh
+```
+
+C'è anche uno script di aggiornamento nel repository di [Techahold](https://github.com/techahold/rustdeskinstall).
+
+Da lì, prendi nota dell'IP/DNS e della chiave mostrati alla fine dell'installazione e inseriscili nei campi `Server ID` e `Chiave` di Impostazioni > Rete > Server ID/Relay del client, rispettivamente, lasciando vuoti gli altri campi (vedi nota sotto).
+
+### Metodo 3: Installa il tuo server come servizio systemd usando file deb per distribuzioni debian
+
+Si prega di [scaricare](https://github.com/rustdesk/rustdesk-server/releases/latest) i file deb e installarli con `apt-get -f install .deb` o `dpkg -i .deb`.
+
+## Configurare il client
+Si prega di consultare [questo](/docs/en/self-host/client-configuration/#2-manual-config).
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-oss/install/_index.ja.md b/content/self-host/rustdesk-server-oss/install/_index.ja.md
index cac8ad9..9ab3f0a 100644
--- a/content/self-host/rustdesk-server-oss/install/_index.ja.md
+++ b/content/self-host/rustdesk-server-oss/install/_index.ja.md
@@ -1,6 +1,52 @@
---
title: インストール
-weight: 10
+weight: 1
---
-[English](/docs/en/self-host/rustdesk-server-oss/install/)
+## ビデオチュートリアル
+YouTubeには多くのビデオチュートリアルがあります、https://github.com/rustdesk/rustdesk/wiki/FAQ#video-tutorials。
+
+## サーバー要件
+ハードウェア要件は非常に低く、基本的なクラウドサーバーの最小構成で十分で、CPUとメモリの要件は最小限です。Raspberry Piや同様のものも使用できます。ネットワークサイズに関しては、TCPホールパンチング直接接続が失敗した場合、リレートラフィックが消費されます。リレー接続のトラフィックは、解像度設定と画面更新に応じて30 K/sから3 M/s(1920x1080画面)の間です。オフィス作業の需要のみの場合、トラフィックは約100 K/sです。
+
+## ファイアウォール
+UFWをインストールしている場合は、次のコマンドを使用してファイアウォールを設定してください:
+```
+ufw allow 21114:21119/tcp
+ufw allow 21116/udp
+sudo ufw enable
+```
+
+## インストール
+### 方法1:Docker(推奨)
+
+```
+bash <(wget -qO- https://get.docker.com)
+wget rustdesk.com/oss.yml -O compose.yml
+sudo docker compose up -d
+```
+
+詳細については、[Docker](/docs/en/self-host/rustdesk-server-oss/docker/)をご確認ください。
+
+### 方法2:シンプルなインストールスクリプトを使用してsystemdサービスとして独自のサーバーをインストール
+スクリプトは[Techahold](https://github.com/techahold/rustdeskinstall)でホストされており、私たちの[Discord](https://discord.com/invite/nDceKgxnkV)でサポートされています。
+
+現在、スクリプトはリレーおよびシグナルサーバー(hbbrとhbbs)をダウンロードしてセットアップし、設定を生成し、クライアントへの簡単なデプロイのためにパスワード保護されたWebページでホストします。
+
+次のコマンドを実行してください:
+```
+wget https://raw.githubusercontent.com/techahold/rustdeskinstall/master/install.sh
+chmod +x install.sh
+./install.sh
+```
+
+[Techahold](https://github.com/techahold/rustdeskinstall)のリポジトリには更新スクリプトもあります。
+
+そこから、インストールの最後に表示されるIP/DNSとキーをメモし、それらをクライアントの設定 > ネットワーク > ID/リレーサーバーの`IDサーバー`と`キー`フィールドにそれぞれ挿入し、他のフィールドは空白のままにしてください(下記の注を参照)。
+
+### 方法3:Debianディストリビューション用のdebファイルを使用してsystemdサービスとして独自のサーバーをインストール
+
+[ダウンロード](https://github.com/rustdesk/rustdesk-server/releases/latest)からdebファイルを自分でダウンロードし、`apt-get -f install .deb`または`dpkg -i .deb`でインストールしてください。
+
+## クライアントの設定
+[こちら](/docs/en/self-host/client-configuration/#2-manual-config)をご確認ください。
diff --git a/content/self-host/rustdesk-server-oss/install/_index.zh-cn.md b/content/self-host/rustdesk-server-oss/install/_index.zh-cn.md
index 9838b2e..b44592a 100644
--- a/content/self-host/rustdesk-server-oss/install/_index.zh-cn.md
+++ b/content/self-host/rustdesk-server-oss/install/_index.zh-cn.md
@@ -1,6 +1,52 @@
---
title: 安装
-weight: 10
+weight: 1
---
-[English](/docs/en/self-host/rustdesk-server-oss/install/)
+## 视频教程
+YouTube上有许多视频教程,https://github.com/rustdesk/rustdesk/wiki/FAQ#video-tutorials。
+
+## 服务器要求
+硬件要求非常低;基本云服务器的最低配置就足够了,CPU和内存要求极低。您也可以使用树莓派或类似设备。关于网络规模,如果TCP打洞直连失败,将消耗中继流量。中继连接的流量根据分辨率设置和屏幕更新在30 K/s到3 M/s(1920x1080屏幕)之间。如果仅用于办公需求,流量约为100 K/s。
+
+## 防火墙
+如果您安装了UFW,请使用以下命令配置防火墙:
+```
+ufw allow 21114:21119/tcp
+ufw allow 21116/udp
+sudo ufw enable
+```
+
+## 安装
+### 方法1:Docker(推荐)
+
+```
+bash <(wget -qO- https://get.docker.com)
+wget rustdesk.com/oss.yml -O compose.yml
+sudo docker compose up -d
+```
+
+更多详情,请查看 [Docker](/docs/en/self-host/rustdesk-server-oss/docker/)。
+
+### 方法2:使用简单的安装脚本将您自己的服务器安装为systemd服务
+脚本托管在 [Techahold](https://github.com/techahold/rustdeskinstall),并在我们的 [Discord](https://discord.com/invite/nDceKgxnkV) 上提供支持。
+
+目前,该脚本将下载并设置中继和信号服务器(hbbr和hbbs),生成配置并将其托管在受密码保护的网页上,以便简单部署到客户端。
+
+运行以下命令:
+```
+wget https://raw.githubusercontent.com/techahold/rustdeskinstall/master/install.sh
+chmod +x install.sh
+./install.sh
+```
+
+[Techahold](https://github.com/techahold/rustdeskinstall) 的仓库中还有一个更新脚本。
+
+从那里,记下安装结束时显示的IP/DNS和密钥,并将它们分别插入客户端设置 > 网络 > ID/中继服务器的`ID服务器`和`密钥`字段中,其他字段留空(见下面的注释)。
+
+### 方法3:使用deb文件为debian发行版安装您自己的服务器作为systemd服务
+
+请自行[下载](https://github.com/rustdesk/rustdesk-server/releases/latest) deb文件,并使用`apt-get -f install .deb`或`dpkg -i .deb`进行安装。
+
+## 配置客户端
+请查看[这里](/docs/en/self-host/client-configuration/#2-manual-config)。
diff --git a/content/self-host/rustdesk-server-oss/install/_index.zh-tw.md b/content/self-host/rustdesk-server-oss/install/_index.zh-tw.md
index 0048fb1..2afa61d 100644
--- a/content/self-host/rustdesk-server-oss/install/_index.zh-tw.md
+++ b/content/self-host/rustdesk-server-oss/install/_index.zh-tw.md
@@ -1,6 +1,52 @@
---
title: 安裝
-weight: 10
+weight: 1
---
-[English](/docs/en/self-host/rustdesk-server-oss/install/)
+## 影片教學
+YouTube上有許多影片教學,https://github.com/rustdesk/rustdesk/wiki/FAQ#video-tutorials。
+
+## 伺服器需求
+硬體需求非常低;基本雲端伺服器的最低配置就足夠了,CPU和記憶體需求極低。您也可以使用樹莓派或類似裝置。關於網路規模,如果TCP打洞直連失敗,將消耗中繼流量。中繼連線的流量根據解析度設定和螢幕更新在30 K/s到3 M/s(1920x1080螢幕)之間。如果僅用於辦公需求,流量約為100 K/s。
+
+## 防火牆
+如果您安裝了UFW,請使用以下命令設定防火牆:
+```
+ufw allow 21114:21119/tcp
+ufw allow 21116/udp
+sudo ufw enable
+```
+
+## 安裝
+### 方法1:Docker(建議)
+
+```
+bash <(wget -qO- https://get.docker.com)
+wget rustdesk.com/oss.yml -O compose.yml
+sudo docker compose up -d
+```
+
+更多詳情,請查看 [Docker](/docs/en/self-host/rustdesk-server-oss/docker/)。
+
+### 方法2:使用簡單的安裝腳本將您自己的伺服器安裝為systemd服務
+腳本託管在 [Techahold](https://github.com/techahold/rustdeskinstall),並在我們的 [Discord](https://discord.com/invite/nDceKgxnkV) 上提供支援。
+
+目前,該腳本將下載並設定中繼和訊號伺服器(hbbr和hbbs),產生設定並將其託管在受密碼保護的網頁上,以便簡單部署到用戶端。
+
+執行以下命令:
+```
+wget https://raw.githubusercontent.com/techahold/rustdeskinstall/master/install.sh
+chmod +x install.sh
+./install.sh
+```
+
+[Techahold](https://github.com/techahold/rustdeskinstall) 的儲存庫中還有一個更新腳本。
+
+從那裡,記下安裝結束時顯示的IP/DNS和金鑰,並將它們分別插入用戶端設定 > 網路 > ID/中繼伺服器的`ID伺服器`和`金鑰`欄位中,其他欄位留空(見下面的註解)。
+
+### 方法3:使用deb檔案為debian發行版安裝您自己的伺服器作為systemd服務
+
+請自行[下載](https://github.com/rustdesk/rustdesk-server/releases/latest) deb檔案,並使用`apt-get -f install .deb`或`dpkg -i .deb`進行安裝。
+
+## 設定用戶端
+請查看[這裡](/docs/en/self-host/client-configuration/#2-manual-config)。
diff --git a/content/self-host/rustdesk-server-oss/synology/_index.es.md b/content/self-host/rustdesk-server-oss/synology/_index.es.md
index 9804a04..2a667ea 100644
--- a/content/self-host/rustdesk-server-oss/synology/_index.es.md
+++ b/content/self-host/rustdesk-server-oss/synology/_index.es.md
@@ -2,7 +2,10 @@
title: Synology
weight: 22
---
-Synology has two type of Docker, "Docker" and "Container Manager", if you're using DSM 7.2 and latter, please follow the guide for DSM 7.2, or follow the DSM 6 guide if you're on older system.
+Synology tiene dos tipos de Docker, "Docker" y "Container Manager". Si está usando DSM 7.2 o posterior, siga la guía para DSM 7.2, o siga la guía de DSM 6 si está en un sistema más antiguo.
+
+Si está utilizando Synology con Portainer, consulte [este tutorial](https://mariushosting.com/how-to-install-rustdesk-on-your-synology-nas/).
+
{{% children depth="3" showhidden="true" %}}
For DSM 7.2, please check [English](/docs/en/self-host/rustdesk-server-oss/synology/dsm-7/).
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-oss/synology/_index.fr.md b/content/self-host/rustdesk-server-oss/synology/_index.fr.md
index 9804a04..49b4060 100644
--- a/content/self-host/rustdesk-server-oss/synology/_index.fr.md
+++ b/content/self-host/rustdesk-server-oss/synology/_index.fr.md
@@ -2,7 +2,10 @@
title: Synology
weight: 22
---
-Synology has two type of Docker, "Docker" and "Container Manager", if you're using DSM 7.2 and latter, please follow the guide for DSM 7.2, or follow the DSM 6 guide if you're on older system.
+Synology a deux types de Docker, "Docker" et "Container Manager". Si vous utilisez DSM 7.2 ou une version ultérieure, veuillez suivre le guide pour DSM 7.2, ou suivez le guide DSM 6 si vous êtes sur un système plus ancien.
+
+Si vous utilisez Synology avec Portainer, veuillez consulter [ce tutoriel](https://mariushosting.com/how-to-install-rustdesk-on-your-synology-nas/).
+
{{% children depth="3" showhidden="true" %}}
For DSM 7.2, please check [English](/docs/en/self-host/rustdesk-server-oss/synology/dsm-7/).
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-oss/synology/_index.it.md b/content/self-host/rustdesk-server-oss/synology/_index.it.md
index ebdc4ab..b437407 100644
--- a/content/self-host/rustdesk-server-oss/synology/_index.it.md
+++ b/content/self-host/rustdesk-server-oss/synology/_index.it.md
@@ -1,6 +1,10 @@
---
-title: Synology DSM 6
+title: Synology
weight: 22
---
-[English](/docs/en/self-host/rustdesk-server-oss/synology)
+Synology ha due tipi di Docker, "Docker" e "Container Manager". Se stai usando DSM 7.2 e versioni successive, segui la guida per DSM 7.2, altrimenti segui la guida DSM 6 se sei su un sistema più vecchio.
+
+Se stai usando Synology con Portainer, fai riferimento a [questo tutorial](https://mariushosting.com/how-to-install-rustdesk-on-your-synology-nas/).
+
+{{% children depth="3" showhidden="true" %}}
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-oss/synology/_index.ja.md b/content/self-host/rustdesk-server-oss/synology/_index.ja.md
index 9804a04..3c130e6 100644
--- a/content/self-host/rustdesk-server-oss/synology/_index.ja.md
+++ b/content/self-host/rustdesk-server-oss/synology/_index.ja.md
@@ -2,7 +2,10 @@
title: Synology
weight: 22
---
-Synology has two type of Docker, "Docker" and "Container Manager", if you're using DSM 7.2 and latter, please follow the guide for DSM 7.2, or follow the DSM 6 guide if you're on older system.
+SynologyにはDockerの種類が2つあります。「Docker」と「Container Manager」です。DSM 7.2以降を使用している場合は、DSM 7.2のガイドに従ってください。古いシステムを使用している場合は、DSM 6のガイドに従ってください。
+
+PortainerでSynologyを使用している場合は、[このチュートリアル](https://mariushosting.com/how-to-install-rustdesk-on-your-synology-nas/)を参照してください。
+
{{% children depth="3" showhidden="true" %}}
For DSM 7.2, please check [English](/docs/en/self-host/rustdesk-server-oss/synology/dsm-7/).
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-oss/synology/_index.zh-cn.md b/content/self-host/rustdesk-server-oss/synology/_index.zh-cn.md
index 77b4f86..42702f8 100644
--- a/content/self-host/rustdesk-server-oss/synology/_index.zh-cn.md
+++ b/content/self-host/rustdesk-server-oss/synology/_index.zh-cn.md
@@ -3,6 +3,9 @@ title: 群晖
weight: 22
---
Synology 有两种 Docker, "Docker" 和 "Container Manager", 如果您使用 DSM 7.2 和更新版本, 请参阅 DSM 7.2 的说明,或如果您使用较旧的系统,请参阅 DSM 6 的说明。
+
+如果您在 Synology 上使用 Portainer,请参考[此教程](https://mariushosting.com/how-to-install-rustdesk-on-your-synology-nas/)。
+
{{% children depth="3" showhidden="true" %}}
DSM 7 請先看[繁體中文](/docs/zh-tw/self-host/rustdesk-server-oss/synology/dsm-7/)版本
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-oss/synology/_index.zh-tw.md b/content/self-host/rustdesk-server-oss/synology/_index.zh-tw.md
index 8b0a77b..daf4062 100644
--- a/content/self-host/rustdesk-server-oss/synology/_index.zh-tw.md
+++ b/content/self-host/rustdesk-server-oss/synology/_index.zh-tw.md
@@ -3,4 +3,7 @@ title: Synology 群暉
weight: 22
---
Synology 有兩種 Docker, "Docker" 和 "Container Manager", 如果您使用 DSM 7.2 和更新版本, 請參閱 DSM 7.2 的說明,或如果您使用較舊的系統,請參閱 DSM 6 的說明。
+
+如果您使用 Synology 搭配 Portainer,請參考[此教學](https://mariushosting.com/how-to-install-rustdesk-on-your-synology-nas/)。
+
{{% children depth="3" showhidden="true" %}}
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.de.md b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.de.md
index c94988c..7f66a8e 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.de.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.de.md
@@ -15,32 +15,32 @@ Nach dem DSM 7.2 Update wurde Docker auf den neuen "Container Manager" aktualisi
| Paketzentrum öffnen | Docker installieren |
| --- | --- |
-|  |  |
+|  |  |
## RustDesk Server installieren
| Suchen Sie rustdesk-server in Docker's Registry und installieren Sie per Doppelklick | Installiertes rustdesk-server Image, doppelklicken Sie um rustdesk-server Container zu erstellen |
| --- | --- |
-|  |  |
+|  |  |
## hbbs Container erstellen
Wie oben erwähnt, doppelklicken Sie auf das rustdesk-server Image um einen neuen Container zu erstellen, setzen Sie den Namen auf `hbbs`.
-
+
Klicken Sie auf die obigen `Erweiterte Einstellungen`.
- Aktivieren Sie `Automatischen Neustart aktivieren`.
-
+
- Aktivieren Sie `Dasselbe Netzwerk wie Docker Host verwenden`. Für mehr über Host-Netz, bitte [prüfen Sie](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/docker/#net-host).
-
+
- Mounten Sie ein Host-Verzeichnis (z.B. `/home/rustdesk/`) zu `/root`, hbbs wird einige Dateien (Datenbank und `key` Dateien) in diesem Verzeichnis generieren, die über Neustarts hinweg bestehen bleiben müssen.
| Mount | Dateien generiert im Host-Verzeichnis |
| --- | --- |
-|  |  |
+|  |  |
- Befehl setzen
{{% notice note %}}
@@ -48,7 +48,7 @@ Synology's OS ist Debian-basiert, daher funktioniert Host-Netz (--net=host) gut,
{{% /notice %}}
-
+
- Fertig
@@ -56,15 +56,15 @@ Synology's OS ist Debian-basiert, daher funktioniert Host-Netz (--net=host) gut,
Bitte wiederholen Sie die obigen `hbbs` Schritte, aber benennen Sie den Container `hbbr` und der Befehl (für Befehl setzen Schritt) sollte `hbbr` sein.
-
+
## hbbr/hbbs Container
-
+
| Doppelklicken Sie auf Container und prüfen Sie das Log | Doppelt bestätigen Sie hbbs/hbbr verwenden Host-Netzwerk |
| --- | --- |
-|  |  |
+|  |  |
## Ihren Schlüssel abrufen
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.en.md b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.en.md
index 9108209..6b7026c 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.en.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.en.md
@@ -15,32 +15,32 @@ After DSM 7.2 update, the Docker is upgraded to new "Container Manager", please
| Open Package Center | Install Docker |
| --- | --- |
-|  |  |
+|  |  |
## Install RustDesk Server
| Search rustdesk-server in Docker's registry and install by double click | Installed rustdesk-server image, double click to create rustdesk-server container |
| --- | --- |
-|  |  |
+|  |  |
## Create hbbs container
As mentioned above, double click on rustdesk-server image to create new container, set it name to `hbbs`.
-
+
Click on above `Advanced Settings`.
- Enable `Enable auto-restart`.
-
+
- Enable `Use the same network as Docker Host`. For more about host net, please [check](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/docker/#net-host).
-
+
- Mount a host directory (e.g. `/home/rustdesk/`) to `/root`, hbbs will generate some files (database and `key` files) in this directory which need to be persistent over reboots.
| Mount | Files generated in the host directory |
| --- | --- |
-|  |  |
+|  |  |
- Set command
{{% notice note %}}
@@ -48,7 +48,7 @@ Synology's OS is Debian based, so host net (--net=host) works fine, we do not ne
{{% /notice %}}
-
+
- Done
@@ -56,15 +56,15 @@ Synology's OS is Debian based, so host net (--net=host) works fine, we do not ne
Please repeat above `hbbs` steps, but name the container `hbbr` and command (for Set Command Step) should be `hbbr`.
-
+
## hbbr/hbbs containers
-
+
| Double click on container and check log | Double confirm hbbs/hbbr using host network |
| --- | --- |
-|  |  |
+|  |  |
## Retrieve your Key
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.es.md b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.es.md
index 7e4ca9a..a063012 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.es.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.es.md
@@ -15,32 +15,32 @@ Después de la actualización DSM 7.2, Docker fue actualizado al nuevo "Containe
| Abrir Centro de Paquetes | Instalar Docker |
| --- | --- |
-|  |  |
+|  |  |
## Instalar RustDesk Server
| Buscar rustdesk-server en el registro de Docker e instalar haciendo doble clic | Imagen rustdesk-server instalada, hacer doble clic para crear contenedor rustdesk-server |
| --- | --- |
-|  |  |
+|  |  |
## Crear contenedor hbbs
Como se mencionó anteriormente, haga doble clic en la imagen rustdesk-server para crear un nuevo contenedor, establezca el nombre como `hbbs`.
-
+
Haga clic en `Configuración Avanzada` arriba.
- Habilite `Habilitar reinicio automático`.
-
+
- Habilite `Usar la misma red que Docker Host`. Para más sobre host net, por favor [verifique](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/docker/#net-host).
-
+
- Monte un directorio host (ej. `/home/rustdesk/`) a `/root`, hbbs generará algunos archivos (base de datos y archivos `key`) en este directorio que necesitan persistir a través de reinicios.
| Montar | Archivos generados en el directorio host |
| --- | --- |
-|  |  |
+|  |  |
- Establecer comando
{{% notice note %}}
@@ -48,7 +48,7 @@ El SO de Synology está basado en Debian, por lo que host net (--net=host) funci
{{% /notice %}}
-
+
- ¡Listo!
@@ -56,15 +56,15 @@ El SO de Synology está basado en Debian, por lo que host net (--net=host) funci
Por favor repita los pasos `hbbs` anteriores, pero nombre el contenedor `hbbr` y el comando (para el Paso Establecer Comando) debe ser `hbbr`.
-
+
## contenedores hbbr/hbbs
-
+
| Haga doble clic en el contenedor y verifique el log | Confirme doblemente que hbbs/hbbr usan red host |
| --- | --- |
-|  |  |
+|  |  |
## Recuperar su Clave
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.fr.md b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.fr.md
index 611bf70..cd85963 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.fr.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.fr.md
@@ -15,32 +15,32 @@ Après la mise à jour DSM 7.2, Docker a été mis à niveau vers le nouveau "Co
| Ouvrir le Centre de Paquets | Installer Docker |
| --- | --- |
-|  |  |
+|  |  |
## Installer RustDesk Server
| Rechercher rustdesk-server dans le registre Docker et installer en double-cliquant | Image rustdesk-server installée, double-cliquer pour créer le conteneur rustdesk-server |
| --- | --- |
-|  |  |
+|  |  |
## Créer le conteneur hbbs
Comme mentionné ci-dessus, double-cliquez sur l'image rustdesk-server pour créer un nouveau conteneur, définissez le nom sur `hbbs`.
-
+
Cliquez sur `Paramètres Avancés` ci-dessus.
- Activez `Activer le redémarrage automatique`.
-
+
- Activez `Utiliser le même réseau que l'Hôte Docker`. Pour plus d'infos sur host net, veuillez [vérifier](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/docker/#net-host).
-
+
- Montez un répertoire hôte (ex. `/home/rustdesk/`) vers `/root`, hbbs va générer quelques fichiers (base de données et fichiers `key`) dans ce répertoire qui doivent persister à travers les redémarrages.
| Monter | Fichiers générés dans le répertoire hôte |
| --- | --- |
-|  |  |
+|  |  |
- Définir la commande
{{% notice note %}}
@@ -48,7 +48,7 @@ L'OS de Synology est basé sur Debian, donc host net (--net=host) fonctionne bie
{{% /notice %}}
-
+
- Terminé
@@ -56,15 +56,15 @@ L'OS de Synology est basé sur Debian, donc host net (--net=host) fonctionne bie
Veuillez répéter les étapes `hbbs` ci-dessus, mais nommez le conteneur `hbbr` et la commande (pour l'Étape Définir Commande) devrait être `hbbr`.
-
+
## conteneurs hbbr/hbbs
-
+
| Double-cliquez sur le conteneur et vérifiez le log | Double confirmez que hbbs/hbbr utilisent le réseau hôte |
| --- | --- |
-|  |  |
+|  |  |
## Récupérer votre Clé
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.it.md b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.it.md
index dc4b03c..2f61f2d 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.it.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.it.md
@@ -15,32 +15,32 @@ Dopo l'aggiornamento DSM 7.2, Docker è stato aggiornato al nuovo "Container Man
| Aprire Centro Pacchetti | Installare Docker |
| --- | --- |
-|  |  |
+|  |  |
## Installare RustDesk Server
| Cercare rustdesk-server nel registry Docker e installare facendo doppio clic | Immagine rustdesk-server installata, fare doppio clic per creare il contenitore rustdesk-server |
| --- | --- |
-|  |  |
+|  |  |
## Creare contenitore hbbs
Come menzionato sopra, fare doppio clic sull'immagine rustdesk-server per creare un nuovo contenitore, impostare il nome su `hbbs`.
-
+
Cliccare su `Impostazioni Avanzate` sopra.
- Abilitare `Abilita riavvio automatico`.
-
+
- Abilitare `Usa la stessa rete dell'Host Docker`. Per maggiori informazioni su host net, si prega di [controllare](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/docker/#net-host).
-
+
- Montare una directory host (es. `/home/rustdesk/`) su `/root`, hbbs genererà alcuni file (database e file `key`) in questa directory che devono persistere attraverso i riavvii.
| Montare | File generati nella directory host |
| --- | --- |
-|  |  |
+|  |  |
- Impostare comando
{{% notice note %}}
@@ -48,7 +48,7 @@ L'OS di Synology è basato su Debian, quindi host net (--net=host) funziona bene
{{% /notice %}}
-
+
- Fatto
@@ -56,15 +56,15 @@ L'OS di Synology è basato su Debian, quindi host net (--net=host) funziona bene
Si prega di ripetere i passaggi `hbbs` sopra, ma nominare il contenitore `hbbr` e il comando (per il Passaggio Impostare Comando) dovrebbe essere `hbbr`.
-
+
## contenitori hbbr/hbbs
-
+
| Fare doppio clic sul contenitore e controllare il log | Riconfermare che hbbs/hbbr usano la rete host |
| --- | --- |
-|  |  |
+|  |  |
## Recuperare la tua Chiave
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.ja.md b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.ja.md
index edaee5f..101c1fe 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.ja.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.ja.md
@@ -15,32 +15,32 @@ DSM 7.2 アップデート後、Docker は新しい「Container Manager」にア
| パッケージセンターを開く | Docker をインストール |
| --- | --- |
-|  |  |
+|  |  |
## RustDesk Server をインストール
| Docker のレジストリで rustdesk-server を検索し、ダブルクリックでインストール | インストールされた rustdesk-server イメージ、ダブルクリックで rustdesk-server コンテナを作成 |
| --- | --- |
-|  |  |
+|  |  |
## hbbs コンテナを作成
上記の通り、rustdesk-server イメージをダブルクリックして新しいコンテナを作成し、名前を `hbbs` に設定します。
-
+
上記の `詳細設定` をクリックします。
- `自動再起動を有効にする` を有効にします。
-
+
- `Docker ホストと同じネットワークを使用する` を有効にします。ホストネットについて詳しくは、[こちら](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/docker/#net-host)をご確認ください。
-
+
- ホストディレクトリ(例:`/home/rustdesk/`)を `/root` にマウントします。hbbs はこのディレクトリにいくつかのファイル(データベースと `key` ファイル)を生成し、これらは再起動後も永続化される必要があります。
| マウント | ホストディレクトリに生成されるファイル |
| --- | --- |
-|  |  |
+|  |  |
- コマンドを設定
{{% notice note %}}
@@ -48,7 +48,7 @@ Synology の OS は Debian ベースなので、ホストネット(--net=host
{{% /notice %}}
-
+
- 完了
@@ -56,15 +56,15 @@ Synology の OS は Debian ベースなので、ホストネット(--net=host
上記の `hbbs` の手順を繰り返しますが、コンテナ名を `hbbr` にし、コマンド(コマンド設定ステップ)は `hbbr` にしてください。
-
+
## hbbr/hbbs コンテナ
-
+
| コンテナをダブルクリックしてログを確認 | hbbs/hbbr がホストネットワークを使用していることを再確認 |
| --- | --- |
-|  |  |
+|  |  |
## キーを取得
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.pt.md b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.pt.md
index 683eec1..b043f2b 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.pt.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.pt.md
@@ -15,32 +15,32 @@ Após a atualização do DSM 7.2, o Docker foi atualizado para o novo "Container
| Abrir Central de Pacotes | Instalar Docker |
| --- | --- |
-|  |  |
+|  |  |
## Instalar RustDesk Server
| Procurar rustdesk-server no registro do Docker e instalar clicando duas vezes | Imagem rustdesk-server instalada, clique duas vezes para criar contêiner rustdesk-server |
| --- | --- |
-|  |  |
+|  |  |
## Criar contêiner hbbs
Como mencionado acima, clique duas vezes na imagem rustdesk-server para criar novo contêiner, defina o nome como `hbbs`.
-
+
Clique nas `Configurações Avançadas` acima.
- Habilite `Habilitar reinício automático`.
-
+
- Habilite `Usar a mesma rede que o Host Docker`. Para mais sobre host net, verifique [aqui](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/docker/#net-host).
-
+
- Monte um diretório host (ex. `/home/rustdesk/`) para `/root`, hbbs irá gerar alguns arquivos (banco de dados e arquivos `key`) neste diretório que precisam ser persistentes ao longo de reinicializações.
| Montar | Arquivos gerados no diretório host |
| --- | --- |
-|  |  |
+|  |  |
- Definir comando
{{% notice note %}}
@@ -48,7 +48,7 @@ O SO do Synology é baseado no Debian, então host net (--net=host) funciona bem
{{% /notice %}}
-
+
- Concluído
@@ -56,15 +56,15 @@ O SO do Synology é baseado no Debian, então host net (--net=host) funciona bem
Repita os passos `hbbs` acima, mas nomeie o contêiner `hbbr` e o comando (para o Passo Definir Comando) deve ser `hbbr`.
-
+
## contêineres hbbr/hbbs
-
+
| Clique duas vezes no contêiner e verifique o log | Confirme novamente hbbs/hbbr usando rede host |
| --- | --- |
-|  |  |
+|  |  |
## Recuperar sua Chave
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.zh-cn.md b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.zh-cn.md
index c50d5f9..754d20c 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.zh-cn.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.zh-cn.md
@@ -15,32 +15,32 @@ DSM 7.2 更新后,Docker 升级为新的 "Container Manager",请查看[这
| 打开套件中心 | 安装 Docker |
| --- | --- |
-|  |  |
+|  |  |
## 安装 RustDesk Server
| 在 Docker 注册表中搜索 rustdesk-server 并双击安装 | 已安装 rustdesk-server 镜像,双击创建 rustdesk-server 容器 |
| --- | --- |
-|  |  |
+|  |  |
## 创建 hbbs 容器
如上所述,双击 rustdesk-server 镜像创建新容器,设置名称为 `hbbs`。
-
+
点击上面的 `高级设置`。
- 启用 `启用自动重新启动`。
-
+
- 启用 `使用与 Docker Host 相同的网络`。关于主机网络的更多信息,请[查看](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/docker/#net-host)。
-
+
- 挂载主机目录(例如 `/home/rustdesk/`)到 `/root`,hbbs 将在此目录中生成一些文件(数据库和 `key` 文件),这些文件需要在重启后持久保存。
| 挂载 | 在主机目录中生成的文件 |
| --- | --- |
-|  |  |
+|  |  |
- 设置命令
{{% notice note %}}
@@ -48,7 +48,7 @@ Synology 的操作系统基于 Debian,所以主机网络 (--net=host) 工作
{{% /notice %}}
-
+
- 完成
@@ -56,15 +56,15 @@ Synology 的操作系统基于 Debian,所以主机网络 (--net=host) 工作
请重复上面的 `hbbs` 步骤,但将容器命名为 `hbbr`,命令(设置命令步骤)应该是 `hbbr`。
-
+
## hbbr/hbbs 容器
-
+
| 双击容器并查看日志 | 再次确认 hbbs/hbbr 使用主机网络 |
| --- | --- |
-|  |  |
+|  |  |
## 获取您的密钥
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.zh-tw.md b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.zh-tw.md
index 5e2e342..38bbd5d 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.zh-tw.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-6/_index.zh-tw.md
@@ -15,32 +15,32 @@ DSM 7.2 更新後,Docker 升級為新的 "Container Manager",請查看[這
| 開啟套件中心 | 安裝 Docker |
| --- | --- |
-|  |  |
+|  |  |
## 安裝 RustDesk Server
| 在 Docker 註冊表中搜尋 rustdesk-server 並雙擊安裝 | 已安裝 rustdesk-server 映像,雙擊建立 rustdesk-server 容器 |
| --- | --- |
-|  |  |
+|  |  |
## 建立 hbbs 容器
如上所述,雙擊 rustdesk-server 映像建立新容器,設定名稱為 `hbbs`。
-
+
點擊上面的 `進階設定`。
- 啟用 `啟用自動重新啟動`。
-
+
- 啟用 `使用與 Docker Host 相同的網路`。關於主機網路的更多資訊,請[查看](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/docker/#net-host)。
-
+
- 掛載主機目錄(例如 `/home/rustdesk/`)到 `/root`,hbbs 將在此目錄中產生一些檔案(資料庫和 `key` 檔案),這些檔案需要在重啟後持久保存。
| 掛載 | 在主機目錄中產生的檔案 |
| --- | --- |
-|  |  |
+|  |  |
- 設定命令
{{% notice note %}}
@@ -48,7 +48,7 @@ Synology 的作業系統基於 Debian,所以主機網路 (--net=host) 工作
{{% /notice %}}
-
+
- 完成
@@ -56,15 +56,15 @@ Synology 的作業系統基於 Debian,所以主機網路 (--net=host) 工作
請重複上面的 `hbbs` 步驟,但將容器命名為 `hbbr`,命令(設定命令步驟)應該是 `hbbr`。
-
+
## hbbr/hbbs 容器
-
+
| 雙擊容器並查看日誌 | 再次確認 hbbs/hbbr 使用主機網路 |
| --- | --- |
-|  |  |
+|  |  |
## 獲取您的金鑰
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.de.md b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.de.md
index 74d30c2..d81d9b4 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.de.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.de.md
@@ -14,7 +14,7 @@ In den meisten Fällen müssen Sie für die Installation von Docker und RustDesk
Öffnen Sie das "Package Center", suchen und installieren Sie "Container Manager".
-
+
## 2. Ordner erstellen
@@ -22,7 +22,7 @@ Nach der Installation von "Container Manager" wird ein gemeinsamer Ordner `docke
Öffnen Sie Ihre File Station, erstellen Sie einen Ordner `rustdesk-server` (oder wie immer Sie wollen). Dann erstellen Sie darin einen Ordner `data`, genau wie auf dem Bild.
-
+
## 3. Container erstellen
@@ -30,7 +30,7 @@ Nach der Installation von "Container Manager" wird ein gemeinsamer Ordner `docke
Geben Sie den Projektnamen `rustdesk-server` ein, ändern Sie Source von "Upload compose.yml" zu "Create compose.yml" und kopieren Sie den folgenden Inhalt in das Feld.
-
+
```yaml
services:
@@ -71,7 +71,7 @@ Bitte überspringen Sie `Web portal settings`, dann ist das erledigt.
Der öffentliche Schlüssel sieht wie folgt aus:
-
+
Lesen Sie [hier](/docs/de/client), wie Sie Ihren Client einrichten. Nur `ID-Server` und `Key` werden benötigt. `Relais-Server` wird nicht benötigt, da wir ihn in `hbbs` festgelegt haben. Diese Informationen werden von `hbbs` automatisch bereitgestellt.
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.en.md b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.en.md
index 20b7a9e..86ef10c 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.en.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.en.md
@@ -14,7 +14,7 @@ Most of time you won't need to install extra RAM for install Docker and RustDesk
Open "Package Center", search and install "Container Manager".
-
+
## 2. Create folder
@@ -22,7 +22,7 @@ After you installed "Container Manager", it will create a Shared Folder called `
Open your File Station, create a folder named `rustdesk-server`(or whatever you like). Then create a folder named `data` in it just like the picture.
-
+
## 3. Create container
@@ -30,7 +30,7 @@ Open your Container Manager, go to Project and click Create.
Enter the project name `rustdesk-server` and change Source from "Upload compose.yml" to "Create compose.yml", and copy following contents to the box.
-
+
```yaml
services:
@@ -71,7 +71,7 @@ Open your File Station, you should see `id_ed25519`, `id_ed25519.pub` on your `d
The public key will looks like this:
-
+
Check [here](/docs/en/client) to set up your client. Only `ID server` and `Key` is needed. `Relay server` isn't needed because we've set it in `hbbs`, `hbbs` will provide this information automatically.
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.es.md b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.es.md
index 46d9b2b..82349d4 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.es.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.es.md
@@ -14,7 +14,7 @@ La mayoría de las veces no necesitará instalar RAM extra para instalar Docker
Abra "Centro de Paquetes", busque e instale "Container Manager".
-
+
## 2. Crear carpeta
@@ -22,7 +22,7 @@ Después de instalar "Container Manager", creará una Carpeta Compartida llamada
Abra su File Station, cree una carpeta llamada `rustdesk-server` (o como guste). Luego cree una carpeta llamada `data` en ella como en la imagen.
-
+
## 3. Crear contenedor
@@ -30,7 +30,7 @@ Abra su Container Manager, vaya a Proyecto y haga clic en Crear.
Ingrese el nombre del proyecto `rustdesk-server` y cambie Fuente de "Subir compose.yml" a "Crear compose.yml", y copie el siguiente contenido en el cuadro.
-
+
```yaml
services:
@@ -71,7 +71,7 @@ Abra su File Station, debería ver `id_ed25519`, `id_ed25519.pub` en su carpeta
La clave pública se verá así:
-
+
Verifique [aquí](/docs/en/client) para configurar su cliente. Solo se necesita `servidor ID` y `Clave`. `Servidor relay` no es necesario porque lo hemos configurado en `hbbs`, `hbbs` proporcionará esta información automáticamente.
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.fr.md b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.fr.md
index d70952e..3517f4d 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.fr.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.fr.md
@@ -14,7 +14,7 @@ La plupart du temps, vous n'aurez pas besoin d'installer de RAM supplémentaire
Ouvrez "Centre de Paquets", recherchez et installez "Container Manager".
-
+
## 2. Créer un dossier
@@ -22,7 +22,7 @@ Après avoir installé "Container Manager", il créera un Dossier Partagé appel
Ouvrez votre File Station, créez un dossier nommé `rustdesk-server` (ou comme vous le souhaitez). Puis créez un dossier nommé `data` dedans comme sur l'image.
-
+
## 3. Créer un conteneur
@@ -30,7 +30,7 @@ Ouvrez votre Container Manager, allez dans Projet et cliquez sur Créer.
Entrez le nom de projet `rustdesk-server` et changez Source de "Télécharger compose.yml" à "Créer compose.yml", et copiez le contenu suivant dans la boîte.
-
+
```yaml
services:
@@ -71,7 +71,7 @@ Ouvrez votre File Station, vous devriez voir `id_ed25519`, `id_ed25519.pub` dans
La clé publique ressemblera à ceci :
-
+
Vérifiez [ici](/docs/en/client) pour configurer votre client. Seuls `serveur ID` et `Clé` sont nécessaires. `Serveur relay` n'est pas nécessaire car nous l'avons configuré dans `hbbs`, `hbbs` fournira cette information automatiquement.
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.it.md b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.it.md
index efddb9b..ef4020e 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.it.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.it.md
@@ -14,7 +14,7 @@ La maggior parte delle volte non avrai bisogno di installare RAM extra per insta
Apri "Centro Pacchetti", cerca e installa "Container Manager".
-
+
## 2. Creare cartella
@@ -22,7 +22,7 @@ Dopo aver installato "Container Manager", creerà una Cartella Condivisa chiamat
Apri il tuo File Station, crea una cartella chiamata `rustdesk-server` (o come preferisci). Quindi crea una cartella chiamata `data` al suo interno proprio come nell'immagine.
-
+
## 3. Creare contenitore
@@ -30,7 +30,7 @@ Apri il tuo Container Manager, vai su Progetto e clicca Crea.
Inserisci il nome del progetto `rustdesk-server` e cambia Origine da "Carica compose.yml" a "Crea compose.yml", e copia il seguente contenuto nella casella.
-
+
```yaml
services:
@@ -71,7 +71,7 @@ Apri il tuo File Station, dovresti vedere `id_ed25519`, `id_ed25519.pub` nella t
La chiave pubblica apparirà così:
-
+
Controlla [qui](/docs/en/client) per configurare il tuo client. Solo `server ID` e `Chiave` sono necessari. `Server relay` non è necessario perché l'abbiamo impostato in `hbbs`, `hbbs` fornirà queste informazioni automaticamente.
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.ja.md b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.ja.md
index ce7f296..0bb59e2 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.ja.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.ja.md
@@ -14,7 +14,7 @@ Container Manager は J シリーズなどの一部のローエンドモデル
「パッケージセンター」を開き、「Container Manager」を検索してインストールします。
-
+
## 2. フォルダを作成
@@ -22,7 +22,7 @@ Container Manager は J シリーズなどの一部のローエンドモデル
File Station を開き、`rustdesk-server`(またはお好みの名前)という名前のフォルダを作成します。次に、画像のようにその中に `data` という名前のフォルダを作成します。
-
+
## 3. コンテナを作成
@@ -30,7 +30,7 @@ Container Manager を開き、プロジェクトに移動して作成をクリ
プロジェクト名 `rustdesk-server` を入力し、ソースを「compose.yml をアップロード」から「compose.yml を作成」に変更し、以下の内容をボックスにコピーします。
-
+
```yaml
services:
@@ -71,7 +71,7 @@ File Station を開くと、`docker/rustdesk-server/data` フォルダに `id_ed
公開キーは次のようになります:
-
+
クライアントの設定については[こちら](/docs/en/client)をご確認ください。`ID サーバー` と `キー` のみが必要です。`hbbs` で設定しているため `リレーサーバー` は不要で、`hbbs` がこの情報を自動的に提供します。
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.pt.md b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.pt.md
index 5b19a49..53707e1 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.pt.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.pt.md
@@ -14,7 +14,7 @@ Na maioria das vezes você não precisará instalar RAM extra para instalar Dock
Abra "Central de Pacotes", pesquise e instale "Container Manager".
-
+
## 2. Criar pasta
@@ -22,7 +22,7 @@ Após instalar "Container Manager", ele criará uma Pasta Compartilhada chamada
Abra seu File Station, crie uma pasta chamada `rustdesk-server` (ou como desejar). Em seguida, crie uma pasta chamada `data` nela como na imagem.
-
+
## 3. Criar contêiner
@@ -30,7 +30,7 @@ Abra seu Container Manager, vá para Projeto e clique em Criar.
Digite o nome do projeto `rustdesk-server` e mude Origem de "Carregar compose.yml" para "Criar compose.yml", e copie o seguinte conteúdo para a caixa.
-
+
```yaml
services:
@@ -71,7 +71,7 @@ Abra seu File Station, você deve ver `id_ed25519`, `id_ed25519.pub` na sua past
A chave pública ficará assim:
-
+
Verifique [aqui](/docs/en/client) para configurar seu cliente. Apenas `servidor ID` e `Chave` são necessários. `Servidor relay` não é necessário porque definimos em `hbbs`, `hbbs` fornecerá esta informação automaticamente.
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.zh-cn.md b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.zh-cn.md
index 8bae26b..3744b38 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.zh-cn.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.zh-cn.md
@@ -14,7 +14,7 @@ Container Manager 为一些低端型号(如 J 系列)带来了 ARM64 支持
打开"套件中心",搜索并安装"Container Manager"。
-
+
## 2. 创建文件夹
@@ -22,7 +22,7 @@ Container Manager 为一些低端型号(如 J 系列)带来了 ARM64 支持
打开您的 File Station,创建一个名为 `rustdesk-server`(或您喜欢的任何名称)的文件夹。然后在其中创建一个名为 `data` 的文件夹,如图所示。
-
+
## 3. 创建容器
@@ -30,7 +30,7 @@ Container Manager 为一些低端型号(如 J 系列)带来了 ARM64 支持
输入项目名称 `rustdesk-server` 并将源从"上传 compose.yml"更改为"创建 compose.yml",并将以下内容复制到框中。
-
+
```yaml
services:
@@ -71,7 +71,7 @@ services:
公钥看起来像这样:
-
+
查看[这里](/docs/en/client)设置您的客户端。只需要 `ID 服务器` 和 `密钥`。不需要 `中继服务器`,因为我们已在 `hbbs` 中设置,`hbbs` 将自动提供此信息。
diff --git a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.zh-tw.md b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.zh-tw.md
index 201374d..c1d2a6b 100644
--- a/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.zh-tw.md
+++ b/content/self-host/rustdesk-server-oss/synology/dsm-7/_index.zh-tw.md
@@ -12,7 +12,7 @@ Container Manager 為部分低階的 ARM64 的機型帶來支援,例如 j 系
開啟"套件中心",搜尋並安裝 "Container Manager"。
-
+
# 2. 建立資料夾
@@ -20,7 +20,7 @@ Container Manager 為部分低階的 ARM64 的機型帶來支援,例如 j 系
打開您的 File Station,建立一個名叫 `rustdesk-server`(或您想要的名字)的資料夾,接著在其建立名為 `data` 的資料夾,如圖所示。
-
+
# 3. 建立容器
@@ -28,7 +28,7 @@ Container Manager 為部分低階的 ARM64 的機型帶來支援,例如 j 系
輸入您的專案名稱 `rustdesk-server` 然後變更來源從"上傳 compose.yml" 至 "建立 compose.yml",接著複製下方內容到框框。
-
+
````yaml
services:
@@ -68,7 +68,7 @@ services:
公鑰看起來會像這個樣子:
-
+
看看[這裡](/docs/zh-tw/client)來設置您的客戶端,只有 `ID 伺服器` 以及 `Key` 是需要的,中繼伺服器不需設定,因為我們已經把它設置在 `hbbs` 了,hbbs 會自動提供這項資訊。
diff --git a/content/self-host/rustdesk-server-oss/windows/_index.es.md b/content/self-host/rustdesk-server-oss/windows/_index.es.md
index 66aea0d..d599a8d 100644
--- a/content/self-host/rustdesk-server-oss/windows/_index.es.md
+++ b/content/self-host/rustdesk-server-oss/windows/_index.es.md
@@ -1,32 +1,114 @@
---
-title: Windows & pm2
+title: Windows & PM2 o NSSM
weight: 20
---
+{{% notice note %}}
+La política de seguridad de Windows es complicada, si este tutorial no funciona para usted, o encuentra una conexión inestable, por favor migre a un servidor Linux.
+{{% /notice %}}
-## Instalar NodeJs
-Por favor [Download](https://nodejs.org/dist/v16.14.2/node-v16.14.2-x86.msi) e instalar
-NodeJs es el entorno de tiempo de ejecución de pm2, por lo que primero debe instalar NodeJs。
+{{% notice note %}}
+La versión GUI, `RustDeskServer.setup.exe` ya no se mantiene, no se recomienda.
+{{% /notice %}}
-## Instalar pm2
-Ingrese los siguientes en cmd.exe, presione la tecla Intro para cada línea y ejecútelos línea por línea.
+## Una encrucijada
+Ahora tiene dos opciones, puede usar PM2 (más fácil) o NSSM (un poco más difícil) para iniciar el servidor RustDesk
+Hay algunos beneficios al usar NSSM:
+- Compatibilidad con versiones anteriores de Windows (Windows Server 2008 R2/Windows 7 y anteriores aunque no probado).
+- Ideal para Windows Server
+- Inicio automático en el arranque sin inicio de sesión (El usuario que creó la entrada de inicio no necesita iniciar sesión para que se inicie).
+- Ejecutar ambos binarios como Servicios.
+- Independiente (sin dependencia de Node.js)
+
+Mientras que los beneficios de PM2 incluyen:
+- Buena idea si ejecuta el servidor en la misma computadora que su computadora de trabajo principal
+- Inicia sesión regularmente en el usuario que creó la entrada de inicio de RustDesk
+- Más fácil de usar
+
+## Instalación usando NSSM
+
+### Instalando NSSM
+Por favor [descargue](https://github.com/dkxce/NSSM/releases/download/v2.25/NSSM_v2.25.zip) y extraiga NSSM seleccione la arquitectura apropiada para su sistema Windows (si x86 use el contenido de la carpeta win32, si x64 use el contenido de la carpeta win64). También es una buena práctica mover el binario de NSSM al directorio `Program Files\NSSM` (NSSM una vez iniciado como servicio, no se puede mover del directorio en el que se colocó. por lo tanto, es mejor guardarlo en `Program Files`) de su unidad de instalación (generalmente la unidad C:). También es recomendable agregar la ruta (como `C:\Program Files\NSSM`) a la variable de ruta.
+
+### Verificando si NSSM está instalado correctamente
+Si ha hecho todo correctamente, la carpeta `C:\Program Files\NSSM` (en este ejemplo uso la unidad C: pero puede usar cualquier unidad en la que instaló Windows o cualquier ruta que desee) solo debe contener el archivo `nssm.exe`.
+
+Usaremos `C:\Program Files\NSSM` en este ejemplo.
+
+Abra el símbolo del sistema y ejecute `nssm` si ve una página de ayuda, está listo para pasar al siguiente paso.
+
+### Ejecutar hbbr y hbbs
+Descargue la versión de Windows de [RustDesk Server](https://github.com/rustdesk/rustdesk-server/releases).
+Descomprima el programa en `C:\Program Files\RustDesk Server` (o en cualquier lugar que desee, solo asegúrese de que no cambie después de instalar el servicio). Ahora vuelva al símbolo del sistema.
+
+Usaremos `C:\Program Files\RustDesk Server` en este ejemplo.
+```cmd
+nssm install "RustDesk hbbs service" "C:\Program Files\RustDesk Server\hbbs.exe"
+nssm install "RustDesk hbbr service" "C:\Program Files\RustDesk Server\hbbr.exe"
```
+**Nota:**
+- Puede cambiar `RustDesk hbbs service` a lo que desee para nombrar el servicio hbbs
+- Puede cambiar `RustDesk hbbr service` a lo que desee para nombrar el servicio hbbr
+- Puede cambiar `C:\Program Files\RustDesk Server\hbbs.exe` a donde haya colocado los binarios de RustDesk
+- Puede cambiar `C:\Program Files\RustDesk Server\hbbr.exe` a donde haya colocado los binarios de RustDesk
+
+**Plantillas de comando:**
+
+La plantilla de comando en caso de que solo quiera copiar, pegar y editar.
+
+```cmd
+nssm install
+nssm install
+```
+
+**Iniciar servicios**
+
+Después de la instalación exitosa de los servicios, deben iniciarse.
+```cmd
+nssm start
+nssm start
+```
+
+**¡Listo!**
+
+(El método anterior ha sido probado en Windows Server Core 2022 Standard).
+
+## o
+
+## Instalación usando PM2
+
+### Instalar Node.js
+
+Por favor [descargue](https://nodejs.org/dist/v16.14.2/node-v16.14.2-x86.msi) e instale Node.js.
+Node.js es el entorno de tiempo de ejecución de PM2, por lo que primero debe instalar Node.js.
+
+### Instalar PM2
+
+Ingrese lo siguiente en `cmd.exe`, presione la tecla Enter para cada línea, y ejecútelas línea por línea.
+
+```cmd
npm install -g pm2
npm install pm2-windows-startup -g
pm2-startup install
```
-## Ejecutar hbbr y hbbs
-Descargue la versión de Windows de [server program](https://github.com/rustdesk/rustdesk-server/releases), suponiendo que lo descomprima en la unidad C. Ejecute las siguientes cuatro líneas de comandos respectivamente.
-```
-cd c:\rustdesk-server-windows-x64
-pm2 start hbbs.exe
-pm2 start hbbr.exe
+### Ejecutar hbbr y hbbs
+
+Descargue la versión de Windows de [RustDesk Server](https://github.com/rustdesk/rustdesk-server/releases). Descomprima el programa en la unidad C:. Ejecute los siguientes cuatro comandos:
+
+```cmd
+cd C:\rustdesk-server-windows-x64
+pm2 start hbbs.exe
+pm2 start hbbr.exe
pm2 save
```
-## Ver registro
-```
+### Ver el registro
+
+```cmd
pm2 log hbbr
pm2 log hbbs
```
+
+## Tutoriales alternativos
+https://pedja.supurovic.net/setting-up-self-hosted-rustdesk-server-on-windows/?lang=lat
diff --git a/content/self-host/rustdesk-server-oss/windows/_index.fr.md b/content/self-host/rustdesk-server-oss/windows/_index.fr.md
index 473afc2..238ee30 100644
--- a/content/self-host/rustdesk-server-oss/windows/_index.fr.md
+++ b/content/self-host/rustdesk-server-oss/windows/_index.fr.md
@@ -1,32 +1,114 @@
---
-title: Windows & pm2
+title: Windows & PM2 ou NSSM
weight: 20
---
+{{% notice note %}}
+La politique de sécurité de Windows est délicate, si ce tutoriel ne fonctionne pas pour vous, ou si vous rencontrez une connexion instable, veuillez migrer vers un serveur Linux.
+{{% /notice %}}
-## Installer NodeJs
-Veuillez [Télécharger](https://nodejs.org/dist/v16.14.2/node-v16.14.2-x86.msi) et installer.
-NodeJs est l'environnement d'exécution de pm2, vous devez donc d'abord installer NodeJs。
+{{% notice note %}}
+La version GUI, `RustDeskServer.setup.exe` n'est plus maintenue, non recommandée.
+{{% /notice %}}
-## Installer pm2
-Entrez ci-dessous dans cmd.exe, appuyez sur la touche Entrée pour chaque ligne et exécutez-les ligne par ligne.
+## Un carrefour
+Vous avez maintenant deux choix, vous pouvez soit utiliser PM2 (plus facile) ou NSSM (un peu plus difficile) pour démarrer le serveur RustDesk
+Il y a certains avantages à utiliser NSSM :
+- Compatibilité avec les anciennes versions de Windows (Windows Server 2008 R2/Windows 7 et antérieures bien que non testé).
+- Idéal pour Windows Server
+- Démarrage automatique au démarrage sans connexion (L'utilisateur qui a créé l'entrée de démarrage n'a pas besoin de se connecter pour qu'elle démarre).
+- Exécution des deux binaires en tant que Services.
+- Autonome (aucune dépendance à Node.js)
+
+Tandis que les avantages de PM2 incluent :
+- Bonne idée si vous exécutez le serveur sur le même ordinateur que votre ordinateur de travail principal
+- Vous vous connectez régulièrement à l'utilisateur qui a créé l'entrée de démarrage RustDesk
+- Plus convivial
+
+## Installation avec NSSM
+
+### Installation de NSSM
+Veuillez [télécharger](https://github.com/dkxce/NSSM/releases/download/v2.25/NSSM_v2.25.zip) et extraire NSSM en sélectionnant l'architecture appropriée pour votre système Windows (si x86 utilisez le contenu du dossier win32, si x64 utilisez le contenu du dossier win64). Il est également recommandé de déplacer le binaire de NSSM dans le répertoire `Program Files\NSSM` (NSSM une fois démarré en tant que service, ne peut pas être déplacé du répertoire où il a été placé. il est donc préférable de le ranger dans `Program Files`) de votre lecteur d'installation (généralement le lecteur C:). Il est également conseillé d'ajouter le chemin (tel que `C:\Program Files\NSSM`) à la variable de chemin.
+
+### Vérifier si NSSM est correctement installé
+Si vous avez tout fait correctement, le dossier `C:\Program Files\NSSM` (dans cet exemple j'utilise le lecteur C: mais vous pouvez utiliser n'importe quel lecteur sur lequel vous avez installé Windows ou n'importe quel chemin que vous désirez) ne devrait contenir que le fichier `nssm.exe`.
+
+Nous utiliserons `C:\Program Files\NSSM` dans cet exemple.
+
+Ouvrez l'invite de commande et exécutez `nssm` si vous voyez une page d'aide, vous êtes prêt à passer à l'étape suivante.
+
+### Exécuter hbbr et hbbs
+Téléchargez la version Windows de [RustDesk Server](https://github.com/rustdesk/rustdesk-server/releases).
+Décompressez le programme dans `C:\Program Files\RustDesk Server` (ou n'importe où vous le désirez, assurez-vous simplement que cela ne change pas après l'installation du service). Maintenant, revenez à l'invite de commande.
+
+Nous utiliserons `C:\Program Files\RustDesk Server` dans cet exemple.
+```cmd
+nssm install "RustDesk hbbs service" "C:\Program Files\RustDesk Server\hbbs.exe"
+nssm install "RustDesk hbbr service" "C:\Program Files\RustDesk Server\hbbr.exe"
```
+**Note :**
+- Vous pouvez changer `RustDesk hbbs service` par ce que vous désirez pour nommer le service hbbs
+- Vous pouvez changer `RustDesk hbbr service` par ce que vous désirez pour nommer le service hbbr
+- Vous pouvez changer `C:\Program Files\RustDesk Server\hbbs.exe` par l'endroit où vous avez placé les binaires RustDesk
+- Vous pouvez changer `C:\Program Files\RustDesk Server\hbbr.exe` par l'endroit où vous avez placé les binaires RustDesk
+
+**Modèles de commande :**
+
+Le modèle de commande au cas où vous souhaiteriez simplement copier, coller et modifier.
+
+```cmd
+nssm install
+nssm install
+```
+
+**Démarrer les services**
+
+Après l'installation réussie des services, ils doivent être démarrés.
+```cmd
+nssm start
+nssm start
+```
+
+**Terminé !**
+
+(La méthode ci-dessus a été testée sur Windows Server Core 2022 Standard).
+
+## ou
+
+## Installation avec PM2
+
+### Installer Node.js
+
+Veuillez [télécharger](https://nodejs.org/dist/v16.14.2/node-v16.14.2-x86.msi) et installer Node.js.
+Node.js est l'environnement d'exécution de PM2, vous devez donc d'abord installer Node.js.
+
+### Installer PM2
+
+Entrez ce qui suit dans `cmd.exe`, appuyez sur la touche Entrée pour chaque ligne, et exécutez-les ligne par ligne.
+
+```cmd
npm install -g pm2
npm install pm2-windows-startup -g
pm2-startup install
```
-## Exécutez hbbr et hbbs
-Téléchargez la version Windows du [programme serveur](https://github.com/rustdesk/rustdesk-server/releases), en supposant que vous la décompressez sur le lecteur C. Exécutez respectivement les quatre lignes de commandes suivantes.
-```
-cd c:\rustdesk-server-windows-x64
+### Exécuter hbbr et hbbs
+
+Téléchargez la version Windows de [RustDesk Server](https://github.com/rustdesk/rustdesk-server/releases). Décompressez le programme sur le lecteur C:. Exécutez les quatre commandes suivantes :
+
+```cmd
+cd C:\rustdesk-server-windows-x64
+pm2 start hbbs.exe
pm2 start hbbr.exe
-pm2 start hbbs.exe
pm2 save
```
-## Afficher le journal
-```
+### Afficher le journal
+
+```cmd
pm2 log hbbr
pm2 log hbbs
```
+
+## Tutoriels alternatifs
+https://pedja.supurovic.net/setting-up-self-hosted-rustdesk-server-on-windows/?lang=lat
diff --git a/content/self-host/rustdesk-server-oss/windows/_index.it.md b/content/self-host/rustdesk-server-oss/windows/_index.it.md
index f4bd160..ad1441a 100644
--- a/content/self-host/rustdesk-server-oss/windows/_index.it.md
+++ b/content/self-host/rustdesk-server-oss/windows/_index.it.md
@@ -1,6 +1,114 @@
---
-title: Windows & pm2
+title: Windows & PM2 o NSSM
weight: 20
---
-[English](/docs/en/self-host/rustdesk-server-oss/windows)
+{{% notice note %}}
+La politica di sicurezza di Windows è complessa. Se questo tutorial non funziona per te o riscontri connessioni instabili, ti consigliamo di migrare a un server Linux.
+{{% /notice %}}
+
+{{% notice note %}}
+La versione GUI, `RustDeskServer.setup.exe`, non è più mantenuta e non è raccomandata.
+{{% /notice %}}
+
+## Un bivio
+Ora hai due scelte: puoi usare PM2 (più facile) o NSSM (un po' più difficile) per avviare il server RustDesk.
+Ci sono alcuni vantaggi nell'usare NSSM:
+- Compatibilità con versioni precedenti di Windows (Windows Server 2008 R2/Windows 7 e precedenti, anche se non testato).
+- Ideale per Windows Server
+- Avvio automatico all'accensione senza login (L'utente che ha creato la voce di avvio non deve effettuare l'accesso per avviarla).
+- Esecuzione di entrambi i binari come servizi.
+- Autonomo (nessuna dipendenza da Node.js)
+
+Mentre i vantaggi di PM2 includono:
+- Buona idea se esegui il server sullo stesso computer del tuo computer di lavoro principale
+- Effettui regolarmente l'accesso all'utente che ha creato la voce di avvio di RustDesk
+- Più user-friendly
+
+## Installazione usando NSSM
+
+### Installazione di NSSM
+Per favore [scarica](https://github.com/dkxce/NSSM/releases/download/v2.25/NSSM_v2.25.zip) ed estrai NSSM, seleziona l'architettura appropriata per il tuo sistema Windows (se x86 usa il contenuto della cartella win32, se x64 usa il contenuto della cartella win64). È anche buona prassi spostare il binario di NSSM nella directory `Program Files\NSSM` (NSSM una volta avviato come servizio, non può essere spostato dalla directory in cui è stato posizionato, quindi è meglio riporlo in `Program Files`) del tuo drive di installazione (solitamente il drive C:). È anche consigliabile aggiungere il percorso (come `C:\Program Files\NSSM`) alla variabile path.
+
+### Verifica se NSSM è installato correttamente
+Se hai fatto tutto correttamente, la cartella `C:\Program Files\NSSM` (in questo esempio uso il drive C: ma puoi usare qualsiasi drive dove hai installato Windows o qualsiasi percorso desideri) dovrebbe contenere solo il file `nssm.exe`.
+
+Useremo `C:\Program Files\NSSM` in questo esempio.
+
+Apri il prompt dei comandi ed esegui `nssm`, se vedi una pagina di aiuto sei pronto per passare al passo successivo.
+
+### Eseguire hbbr e hbbs
+Scarica la versione Windows di [RustDesk Server](https://github.com/rustdesk/rustdesk-server/releases).
+Decomprimi il programma in `C:\Program Files\RustDesk Server` (o dove preferisci, assicurati solo che non cambi dopo l'installazione del servizio). Ora torna al prompt dei comandi.
+
+Useremo `C:\Program Files\RustDesk Server` in questo esempio.
+```cmd
+nssm install "RustDesk hbbs service" "C:\Program Files\RustDesk Server\hbbs.exe"
+nssm install "RustDesk hbbr service" "C:\Program Files\RustDesk Server\hbbr.exe"
+```
+**Nota:**
+- Puoi cambiare `RustDesk hbbs service` con qualsiasi nome desideri per il servizio hbbs
+- Puoi cambiare `RustDesk hbbr service` con qualsiasi nome desideri per il servizio hbbr
+- Puoi cambiare `C:\Program Files\RustDesk Server\hbbs.exe` con il percorso dove hai posizionato i binari di RustDesk
+- Puoi cambiare `C:\Program Files\RustDesk Server\hbbr.exe` con il percorso dove hai posizionato i binari di RustDesk
+
+**Template dei comandi:**
+
+Il template del comando nel caso tu voglia solo copiare, incollare e modificare.
+
+```cmd
+nssm install
+nssm install
+```
+
+**Avviare i servizi**
+
+Dopo l'installazione riuscita dei servizi, devono essere avviati.
+```cmd
+nssm start
+nssm start
+```
+
+**Fatto!**
+
+(Il metodo sopra è stato testato su Windows Server Core 2022 Standard).
+
+## oppure
+
+## Installazione usando PM2
+
+### Installa Node.js
+
+Per favore [scarica](https://nodejs.org/dist/v16.14.2/node-v16.14.2-x86.msi) e installa Node.js.
+Node.js è l'ambiente di runtime di PM2, quindi devi installare prima Node.js.
+
+### Installa PM2
+
+Inserisci i seguenti comandi in `cmd.exe`, premi il tasto Invio per ogni riga ed eseguili riga per riga.
+
+```cmd
+npm install -g pm2
+npm install pm2-windows-startup -g
+pm2-startup install
+```
+
+### Eseguire hbbr e hbbs
+
+Scarica la versione Windows di [RustDesk Server](https://github.com/rustdesk/rustdesk-server/releases). Decomprimi il programma nel drive C:. Esegui i seguenti quattro comandi:
+
+```cmd
+cd C:\rustdesk-server-windows-x64
+pm2 start hbbs.exe
+pm2 start hbbr.exe
+pm2 save
+```
+
+### Visualizzare il log
+
+```cmd
+pm2 log hbbr
+pm2 log hbbs
+```
+
+## Tutorial alternativi
+https://pedja.supurovic.net/setting-up-self-hosted-rustdesk-server-on-windows/?lang=lat
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-oss/windows/_index.ja.md b/content/self-host/rustdesk-server-oss/windows/_index.ja.md
index 26acaff..ba25c03 100644
--- a/content/self-host/rustdesk-server-oss/windows/_index.ja.md
+++ b/content/self-host/rustdesk-server-oss/windows/_index.ja.md
@@ -1,32 +1,114 @@
---
-title: Windows & pm2
+title: Windows & PM2 または NSSM
weight: 20
---
+{{% notice note %}}
+Windowsのセキュリティポリシーは扱いが難しく、このチュートリアルがうまくいかない場合、または不安定な接続に遭遇した場合は、Linuxサーバーに移行してください。
+{{% /notice %}}
-## NodeJs をインストール
-[ダウンロード](https://nodejs.org/dist/v16.14.2/node-v16.14.2-x86.msi) してインストールしてください。
-NodeJs は pm2 の実行環境ですので先にNodeJsをインストールする必要があります。
+{{% notice note %}}
+GUI版の `RustDeskServer.setup.exe` はもうメンテナンスされていないため、推奨されません。
+{{% /notice %}}
-## pm2 をインストール
-cmd.exe に下記を入力し1行ごとにEnterキーを押して1行ずつ実行します。
+## 分岐点
+RustDeskサーバーを起動するために、PM2(より簡単)またはNSSM(少し難しい)のいずれかを使用する2つの選択肢があります。
+NSSMを使用する利点:
+- 古いWindowsとの下位互換性(Windows Server 2008 R2/Windows 7以前、ただし未テスト)。
+- Windows Serverに最適
+- ログインなしでの起動時の自動開始(起動エントリを作成したユーザーがログオンする必要がありません)。
+- 両方のバイナリをサービスとして実行。
+- スタンドアロン(Node.jsへの依存なし)
+
+一方、PM2の利点:
+- メインの作業用コンピュータと同じコンピュータでサーバーを実行する場合に適しています
+- RustDeskの起動エントリを作成したユーザーに定期的にログオンする場合
+- よりユーザーフレンドリー
+
+## NSSMを使用したインストール
+
+### NSSMのインストール
+[ダウンロード](https://github.com/dkxce/NSSM/releases/download/v2.25/NSSM_v2.25.zip)してNSSMを展開し、Windowsシステムに適したアーキテクチャを選択してください(x86の場合はwin32フォルダの内容を使用、x64の場合はwin64フォルダの内容を使用)。また、NSSMのバイナリをインストールドライブ(通常はC:ドライブ)の`Program Files\NSSM`ディレクトリに移動することをお勧めします(NSSMはサービスとして開始されると、配置されたディレクトリから移動できないため、`Program Files`に格納しておくのが最善です)。パス(`C:\Program Files\NSSM`など)をパス変数に追加することも推奨されます。
+
+### NSSMが正しくインストールされているか確認
+すべて正しく行った場合、`C:\Program Files\NSSM`フォルダ(この例ではC:ドライブを使用していますが、Windowsをインストールしたドライブや任意のパスを使用できます)には`nssm.exe`ファイルのみが含まれているはずです。
+
+この例では`C:\Program Files\NSSM`を使用します。
+
+コマンドプロンプトを開いて`nssm`を実行し、ヘルプページが表示されたら次のステップに進む準備ができています。
+
+### hbbrとhbbsの実行
+[RustDesk Server](https://github.com/rustdesk/rustdesk-server/releases)のWindows版をダウンロードしてください。
+プログラムを`C:\Program Files\RustDesk Server`に解凍します(または任意の場所に解凍しますが、サービスがインストールされた後に変更されないようにしてください)。コマンドプロンプトに戻ります。
+
+この例では`C:\Program Files\RustDesk Server`を使用します。
+```cmd
+nssm install "RustDesk hbbs service" "C:\Program Files\RustDesk Server\hbbs.exe"
+nssm install "RustDesk hbbr service" "C:\Program Files\RustDesk Server\hbbr.exe"
```
+**注意:**
+- `RustDesk hbbs service`はhbbsサービスに付けたい名前に変更できます
+- `RustDesk hbbr service`はhbbrサービスに付けたい名前に変更できます
+- `C:\Program Files\RustDesk Server\hbbs.exe`はRustDeskバイナリを配置した場所に変更できます
+- `C:\Program Files\RustDesk Server\hbbr.exe`はRustDeskバイナリを配置した場所に変更できます
+
+**コマンドテンプレート:**
+
+コピー、ペースト、編集するためのコマンドテンプレート。
+
+```cmd
+nssm install <希望のhbbsサービス名>
+nssm install <希望のhbbrサービス名>
+```
+
+**サービスの開始**
+
+サービスのインストールが成功したら、それらを開始する必要があります。
+```cmd
+nssm start <希望のhbbsサービス名>
+nssm start <希望のhbbrサービス名>
+```
+
+**完了!**
+
+(上記の方法はWindows Server Core 2022 Standardでテストされています)。
+
+## または
+
+## PM2を使用したインストール
+
+### Node.js をインストール
+
+[ダウンロード](https://nodejs.org/dist/v16.14.2/node-v16.14.2-x86.msi)してNode.jsをインストールしてください。
+Node.jsはPM2の実行環境ですので、最初にNode.jsをインストールする必要があります。
+
+### PM2 をインストール
+
+`cmd.exe`に以下を入力し、各行でEnterキーを押して、1行ずつ実行してください。
+
+```cmd
npm install -g pm2
npm install pm2-windows-startup -g
pm2-startup install
```
-## hbbr と hbbs を実行
-Windows版のサーバープログラムをダウンロードします。Cドライブに解凍するのであれば以下の4行のコマンドをそれぞれ実行します。
-```
-cd c:\rustdesk-server-windows-x64
-pm2 start hbbs.exe
-pm2 start hbbr.exe
+### hbbr と hbbs を実行
+
+[RustDesk Server](https://github.com/rustdesk/rustdesk-server/releases)のWindows版をダウンロードしてください。プログラムをC:ドライブに解凍します。次の4つのコマンドを実行してください:
+
+```cmd
+cd C:\rustdesk-server-windows-x64
+pm2 start hbbs.exe
+pm2 start hbbr.exe
pm2 save
```
-## ログを確認
-```
+### ログを表示
+
+```cmd
pm2 log hbbr
pm2 log hbbs
```
+
+## 代替チュートリアル
+https://pedja.supurovic.net/setting-up-self-hosted-rustdesk-server-on-windows/?lang=lat
diff --git a/content/self-host/rustdesk-server-oss/windows/_index.zh-cn.md b/content/self-host/rustdesk-server-oss/windows/_index.zh-cn.md
index e3c018d..c5d8cc9 100644
--- a/content/self-host/rustdesk-server-oss/windows/_index.zh-cn.md
+++ b/content/self-host/rustdesk-server-oss/windows/_index.zh-cn.md
@@ -3,7 +3,7 @@ title: WINDOWS & PM2 或者 NSSM
weight: 20
---
-# 选择哪个?
+## 选择哪个?
现在您有两种选择,可以使用 PM2(更简单)或 NSSM(更难)来启动 RustDesk 服务器
使用 NSSM 有一些好处:
- 向后兼容旧版 Windows(Windows Server 2008R2/Windows 7 及更早版本,但未经测试)。
@@ -17,9 +17,9 @@ PM2 的好处包括:
- 您定期登录创建 rustdesk 启动项的用户
- 更加用户友好
-# 使用 NSSM 安装
+## 使用 NSSM 安装
-## 安装 NSSM
+### 安装 NSSM
请[下载](https://nssm.cc/release/nssm-2.24.zip)并解压NSSM选择合适的
体系结构到您的 Windows 系统(如果 x86 使用 win32 文件夹的内容,如果 x64 使用
win64 文件夹的内容)。 将 NSSM 的二进制文件移至
@@ -27,7 +27,7 @@ win64 文件夹的内容)。 将 NSSM 的二进制文件移至
因此最好将其存放在安装驱动器(通常是 C 驱动器)的 Program files)目录中。
还建议将路径(例如`C:\Program Files\NSSM`)添加到路径变量中。
-## 检查 NSSM 是否安装正确
+### 检查 NSSM 是否安装正确
如果您已正确完成所有操作,则文件夹`C:\Program Files\NSSM`(在本例中我使用 C:
驱动器,但您可以使用安装 Windows 的任何驱动器或您想要的任何路径)
仅包含文件`nssm.exe`。
@@ -36,7 +36,7 @@ win64 文件夹的内容)。 将 NSSM 的二进制文件移至
打开命令提示符并运行`nssm`,如果您看到帮助页面,则您已准备好进入下一步
-## 运行 hbbr 和 hbbs
+### 运行 hbbr 和 hbbs
下载Windows版本的[服务器程序](https://github.com/rustdesk/rustdesk-server/releases)。
将程序解压缩到`C:\Program Files\RustDesk Server`(或您想要的任何地方,只需确保它
安装服务后不会改变)。 现在回到命令提示符
@@ -75,15 +75,15 @@ nssm start
(以上方法已在Windows Server Core 2022 Standard上测试)。
-# 或者
+## 或者
-# 使用 PM2 安装
+## 使用 PM2 安装
-## 安装NodeJs
+### 安装NodeJs
请点击[下载](https://nodejs.org/dist/v16.14.2/node-v16.14.2-x86.msi)安装,可能会有点慢,如果卡顿太久,尝试关掉重新安装。
NodeJs是pm2的运行时环境,所以要先安装NodeJs。
-## 安装pm2
+### 安装pm2
在cmd.exe中分别输入下面三行,每一行都要按回车键,一行一行运行。
```
npm install -g pm2
@@ -91,7 +91,7 @@ npm install pm2-windows-startup -g
pm2-startup install
```
-## 运行hbbr和hbbs
+### 运行hbbr和hbbs
下载Windows版本[服务器程序](https://github.com/rustdesk/rustdesk-server/releases),假设你解压缩到了C盘下。分别运行下面四行命令。
```
cd c:\rustdesk-server-windows-x64
@@ -100,7 +100,7 @@ pm2 start hbbr.exe
pm2 save
```
-## 查看log
+### 查看log
```
pm2 log hbbr
pm2 log hbbs
diff --git a/content/self-host/rustdesk-server-oss/windows/_index.zh-tw.md b/content/self-host/rustdesk-server-oss/windows/_index.zh-tw.md
index afd86d8..fd6d89e 100644
--- a/content/self-host/rustdesk-server-oss/windows/_index.zh-tw.md
+++ b/content/self-host/rustdesk-server-oss/windows/_index.zh-tw.md
@@ -1,67 +1,72 @@
---
-title: Windows & pm2
+title: Windows & PM2 或 NSSM
weight: 20
---
+
{{% notice note %}}
-Windows 安全政策較為複雜,如果這份教程對您不適用,或您遇到連線不穩定的情況,請考慮轉移到 `Linux` 伺服器。
+Windows 安全政策較為複雜,如果這份教程對您不適用,或您遇到連線不穩定的情況,請轉移到 Linux 伺服器。
{{% /notice %}}
-# 十字路口
+{{% notice note %}}
+GUI 版本 `RustDeskServer.setup.exe` 已不再維護,不建議使用。
+{{% /notice %}}
-您現在有兩個選擇,您可以使用 pm2 (較簡單) 或 NSSM (稍難) 來啟動 RustDesk 伺服器
+## 分岔路口
+您現在有兩個選擇,您可以使用 PM2(較簡單)或 NSSM(稍難)來啟動 RustDesk 伺服器
使用 NSSM 的好處:
-- 與舊版 Windows(Windows Server 2008 R2/Windows 7 及更早版本,雖未經測試)的向下兼容。
-- 適合 Windows 伺服器使用
-- 開機自動啟動,無需登入(建立啟動項目的用戶無需登入即可啟動)。
-- 將兩個執行檔作為服務運行。
-- 獨立運行(不依賴於 nodejs)。
+- 與舊版 Windows(Windows Server 2008 R2/Windows 7 及更早版本,雖未經測試)的向下相容。
+- 適合 Windows Server 使用
+- 開機自動啟動,無需登入(建立啟動項目的使用者無需登入即可啟動)。
+- 將兩個執行檔作為服務執行。
+- 獨立運行(不依賴於 Node.js)
-使用 pm2 的好處:
-- 如果您在主要工作的電腦上運行伺服器,這是一個好主意。
-- 您會定期登入創建 RustDesk 啟動項目的使用者帳戶。
-- 對使用者友好
+使用 PM2 的好處包括:
+- 如果您在主要工作的電腦上執行伺服器,這是一個好主意
+- 您會定期登入建立 RustDesk 啟動項目的使用者帳戶
+- 更加使用者友好
## 使用 NSSM 安裝
### 安裝 NSSM
-請[下載](https://nssm.cc/release/nssm-2.24.zip)並解壓縮 NSSM,選擇適合您的 Windows 系統架構的版本(如果是 x86,使用 win32 資料夾內的檔案;如果是 x64,則使用 win64 資料夾)。最佳做法是將 NSSM 的執行檔移動到 `Program Files\NSSM` 目錄(一旦作為服務啟動,NSSM 不能從其放置的目錄中移動,因此最好放在 `Program Files` 中)。建議將路徑(如 `C:\Program Files\NSSM`)添加到環境變數中。
+請[下載](https://github.com/dkxce/NSSM/releases/download/v2.25/NSSM_v2.25.zip)並解壓縮 NSSM,選擇適合您的 Windows 系統架構的版本(如果是 x86,使用 win32 資料夾內的檔案;如果是 x64,則使用 win64 資料夾內容)。最佳做法是將 NSSM 的二進位檔移動到 `Program Files\NSSM` 目錄(一旦作為服務啟動,NSSM 不能從其放置的目錄中移動,因此最好將其收納在 `Program Files` 中)。建議將路徑(如 `C:\Program Files\NSSM`)新增到路徑變數中。
### 檢查 NSSM 是否正確安裝
如果一切正確,`C:\Program Files\NSSM` 資料夾(在這個例子中使用 C: 磁碟,但您可以使用安裝 Windows 的任何磁碟或所需的任何路徑)應該只包含 `nssm.exe` 檔案。
-我們將在範例中使用 `C:\Program Files\NSSM`。
+我們將在此範例中使用 `C:\Program Files\NSSM`。
-打開命令提示字元並運行 `nssm`,如果您看到幫助頁面,則可以進行下一步。
+開啟命令提示字元並執行 `nssm`,如果您看到說明頁面,則可以進行下一步。
-### 運行 hbbr 和 hbbs
-下載 [RustDesk 伺服器](https://github.com/rustdesk/rustdesk-server/releases)的 Windows 版本。解壓縮至 `C:\Program Files\RustDesk Server`(或任何您想要的地方,只要確保在服務安裝後不會改變)。現在回到命令提示字元。
+### 執行 hbbr 和 hbbs
+下載 [RustDesk Server](https://github.com/rustdesk/rustdesk-server/releases) 的 Windows 版本。
+將程式解壓縮至 `C:\Program Files\RustDesk Server`(或任何您想要的地方,只要確保在服務安裝後不會改變)。現在回到命令提示字元。
-我們將在範例中使用 `C:\Program Files\RustDesk Server`。
+我們將在此範例中使用 `C:\Program Files\RustDesk Server`。
```cmd
-nssm install "RustDesk hbbs service" "C:\Program Files\RustDesk Server\hbbs.exe"
-nssm install "RustDesk hbbr service" "C:\Program Files\RustDesk Server\hbbr.exe"
+nssm install "RustDesk hbbs service" "C:\Program Files\RustDesk Server\hbbs.exe"
+nssm install "RustDesk hbbr service" "C:\Program Files\RustDesk Server\hbbr.exe"
```
**注意:**
-- 您可以將 `RustDesk hbbs service` 改為任何您希望命名 hbbs 的服務名稱。
-- 您可以將 `RustDesk hbbr service` 改為任何您希望命名 hbbr 的服務名稱。
-- 您可以將 `C:\Program Files\RustDesk Server\hbbs.exe` 改為 RustDesk 執行檔所在的位置。
-- 您可以將 `C:\Program Files\RustDesk Server\hbbr.exe` 改為 RustDesk 執行檔所在的位置。
+- 您可以將 `RustDesk hbbs service` 改為任何您希望命名 hbbs 服務的名稱
+- 您可以將 `RustDesk hbbr service` 改為任何您希望命名 hbbr 服務的名稱
+- 您可以將 `C:\Program Files\RustDesk Server\hbbs.exe` 改為您放置 RustDesk 二進位檔的位置
+- 您可以將 `C:\Program Files\RustDesk Server\hbbr.exe` 改為您放置 RustDesk 二進位檔的位置
-**指令範例:**
+**命令範本:**
-如果您只想複製並貼上並編輯,這是指令的範例。
+如果您只想複製貼上並編輯,這是命令範本。
```cmd
-nssm install <所需的 hbbs 服務名稱>
-nssm install <所需的 hbbr 服務名稱>
+nssm install <想要的 hbbs 服務名稱>
+nssm install <想要的 hbbr 服務名稱>
```
**啟動服務**
成功安裝服務後,需要啟動它們。
```cmd
-nssm start <所需的 hbbs 服務名稱>
-nssm start <所需的 hbbr 服務名稱>
+nssm start <想要的 hbbs 服務名稱>
+nssm start <想要的 hbbr 服務名稱>
```
**完成!**
@@ -75,11 +80,11 @@ nssm start <所需的 hbbr 服務名稱>
### 安裝 Node.js
請[下載](https://nodejs.org/dist/v16.14.2/node-v16.14.2-x86.msi)並安裝 Node.js。
-Node.js 是 PM2 的運行環境,所以您需要先安裝 Node.js。
+Node.js 是 PM2 的執行環境,所以您需要先安裝 Node.js。
### 安裝 PM2
-在 `cmd.exe` 中輸入以下內容,每行輸入後按 Enter 鍵,逐行運行。
+在 `cmd.exe` 中輸入以下內容,每行輸入後按 Enter 鍵,逐行執行。
```cmd
npm install -g pm2
@@ -87,13 +92,13 @@ npm install pm2-windows-startup -g
pm2-startup install
```
-### 運行 hbbr 和 hbbs
+### 執行 hbbr 和 hbbs
-下載 [RustDesk 伺服器](https://github.com/rustdesk/rustdesk-server/releases)的 Windows 版本。將程序解壓縮到 C: 磁碟。執行以下四個命令:
+下載 [RustDesk Server](https://github.com/rustdesk/rustdesk-server/releases) 的 Windows 版本。將程式解壓縮到 C: 磁碟。執行以下四個命令:
```cmd
cd C:\rustdesk-server-windows-x64
-pm2 start hbbs.exe
+pm2 start hbbs.exe
pm2 start hbbr.exe
pm2 save
```
@@ -104,3 +109,6 @@ pm2 save
pm2 log hbbr
pm2 log hbbs
```
+
+## 替代教程
+https://pedja.supurovic.net/setting-up-self-hosted-rustdesk-server-on-windows/?lang=lat
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-pro/console/_index.zh-cn.md b/content/self-host/rustdesk-server-pro/console/_index.zh-cn.md
index da9381c..af01975 100644
--- a/content/self-host/rustdesk-server-pro/console/_index.zh-cn.md
+++ b/content/self-host/rustdesk-server-pro/console/_index.zh-cn.md
@@ -3,28 +3,105 @@ title: 网页控制台
weight: 10
---
+网页控制台集成在 RustDesk 服务器专业版中,由 `21114` 端口提供服务。
+
功能:
-- 新增/变更使用者和使用者群组
-- 变更设备存取权限
-- 浏览设备访问和其他日志
+- 浏览设备
+- 新增/修改用户和用户组
+- 修改设备访问权限
+- 浏览设备连接日志和其他日志
- 更新设置
-- 管理客户端设定同步策略
+- 管理客户端设置同步策略
+- 管理共享通讯录
+- 生成自定义客户端
## 登录
-如同之前所述,网页控制台的预设端口为 21114。在浏览器输入 `http://:21114` 以进入控制台页面。如下图所示 (hbbs 执行在 IP 为 192.168.1.143 的服务器上):
+网页控制台的默认端口是 21114。在浏览器中输入 `http://<服务器 ip>:21114` 进入控制台页面,如下图所示。默认管理员用户名/密码是 `admin`/`test1234`:
+

-如果您需要 https,请安装如 `Nginx` 的网页服务器。
+如果您需要 HTTPS 支持,请安装如 `Nginx` 的网页服务器,或在 Windows 上使用 `IIS`。
-预设管理员帐号/密码为 admin/test1234,请记得在登入后变更密码,在右上角的帐号选单选择 "设定" 以进入密码变更页面,如下图所示。您也可以建立另一个管理员帐号,并删除预设帐号,建议启用电子邮件登入验证。
+登录后请务必更改密码,在右上角的账户菜单中选择 `设置` 进入密码修改页面,如下图所示。您也可以创建另一个管理员账户并删除这个。建议启用邮箱登录验证。

-非管理员使用者也可以登入来浏览他们的设备和日志,以及变更他们的使用者设定。
+非管理员用户也可以登录查看他们的设备和日志,更改他们的用户设置。
-## Windows EXE
+## 自动配置
+点击 `Windows EXE` 您将能够获得您自己的 RustDesk 服务器专业版的配置,这将帮助配置您的客户端。
-对于 Windows 客户端,您可以省略自定义服务器配置,并将配置信息放在`RustDesk.exe`文件名中。 如上图,请进入控制台欢迎页面,点击`Windows EXE`。 **`客户端 >=1.1.9`**。
+对于 Windows 客户端,您可以省略自定义服务器配置,将配置信息放在 `rustdesk.exe` 文件名中。如上所示,请进入控制台欢迎页面并点击 `Windows EXE`。**需要客户端 ≥ 1.1.9。**
+
+您可以结合[客户端配置](https://rustdesk.com/docs/zh-cn/self-host/client-configuration/)和[部署脚本](https://rustdesk.com/docs/zh-cn/self-host/client-deployment/)来设置您的客户端。
+
+## 创建除默认 `admin` 用户之外的新用户
+
+{{% notice note %}}
+`个人版` 计划没有此功能。
+{{% /notice %}}
+
+1. 点击左侧菜单的 `用户`。
+2. 创建另一个启用了 `管理员` 权限的账户。
+3. 使用新的管理员账户登录。
+4. 在 `用户` 页面删除 `admin`。
+
+## 创建新用户
+1. 点击左侧菜单的 `用户`。
+2. 创建新用户。
+3. 选择他们应该所属的组(如果需要添加新组,请继续阅读)。
+
+## 添加新组
+1. 点击左侧菜单的 `组`。
+2. 创建新组。
+3. 创建后,您可以允许组之间相互访问,点击 `编辑`。
+4. 选择您想要访问的相关组(它会自动将它们添加到相应的组中)。
+
+## 设置多个中继服务器
+1. 进入左侧菜单的 `设置`。
+2. 点击子菜单的 `中继`。
+3. 点击 `中继服务器` 旁边的 `+`。
+4. 在现在显示的框中输入中继服务器 DNS 地址或 IP 地址,然后按 Enter。
+5. 如果您有多个中继服务器,可以继续点击 `+` 并根据需要调整地理位置设置(记住并将您的密钥复制到其他服务器)。
+
+## 设置或更改许可证
+1. 进入左侧菜单的 `设置`。
+2. 点击子菜单的 `许可证`。
+3. 点击 `编辑` 并粘贴您的许可证代码。
+4. 点击 `确定`。
+
+## 查看日志
+点击左侧的 `日志`。
+
+## 设置邮箱
+以 Gmail 为例
+
+1. 进入左侧菜单的 `设置`。
+2. 点击子菜单的 `SMTP`。
+3. 输入 SMTP 地址 `smtp.gmail.com`。
+4. 在 `SMTP 端口` 中输入端口 587。
+5. 在 `邮箱账户` 中输入 Gmail 账户,例如 `myrustdeskserver@gmail.com`。
+6. 输入您的密码(您可能需要应用专用密码)。
+7. 在 `发件人` 中输入您的 Gmail 账户,例如 `myrustdeskserver@gmail.com`。
+8. 点击 `检查` 保存。
+
+## 将设备用户/组/策略/设备组分配给设备
+用户是登录在设备上的 RustDesk 用户,或通过点击设备旁边的 `编辑` 分配给设备的用户,点击 `用户` 框并从下拉菜单中选择您的用户,这将根据用户被分配到的组自动分配组。
+
+这也可以通过 API 在部署时或之后在命令行中完成,调用 RustDesk 可执行文件后跟 `--assign --token <生成的令牌> --user_name <用户名>`。您需要先进入 `设置 → 令牌 → 创建` 并创建具有设备权限的令牌。在 Windows 上的示例为 `"C:\Program Files\RustDesk\rustdesk.exe" --assign --token <生成的令牌> --user_name <新用户>`。
+
+您也可以通过这种方式分配策略,例如 `--assign --token <生成的令牌> --strategy_name <策略名称>`。
+
+您也可以通过这种方式分配通讯录,例如 `--assign --token <生成的令牌> --address_book_name <通讯录名称>` 或 `--assign --token <生成的令牌> --address_book_name <通讯录名称> --address_book_tag <通讯录标签> --address_book_alias <别名>`。`--address_book_alias` 需要 RustDesk 服务器专业版 >=1.5.8 和客户端 >=1.4.1。
+
+您也可以通过这种方式分配设备组名称,例如 `--assign --token <生成的令牌> --device_group_name <设备组名称>`。
+
+Windows 上的命令行默认没有输出。要获得输出,请这样运行:`"C:\Program Files\RustDesk\rustdesk.exe" <参数1> <参数2> ... | more` 或 `"C:\Program Files\RustDesk\rustdesk.exe" <参数1> <参数2> ... | Out-String`,参见[这里](https://github.com/rustdesk/rustdesk/discussions/6377#discussioncomment-8094952)。
+
+## 搜索设备
+1. 进入设备页面。
+2. 在设备名称搜索字段中输入名称并点击 `查询` 或按 Enter。
+3. 要使用通配符,请在搜索词的开头、结尾或两端添加 `%`。
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-pro/console/_index.zh-tw.md b/content/self-host/rustdesk-server-pro/console/_index.zh-tw.md
index 9820ddc..2b0742f 100644
--- a/content/self-host/rustdesk-server-pro/console/_index.zh-tw.md
+++ b/content/self-host/rustdesk-server-pro/console/_index.zh-tw.md
@@ -3,28 +3,105 @@ title: 網頁控制台
weight: 10
---
+網頁控制台整合在 RustDesk 伺服器專業版中,由 `21114` 連接埠提供服務。
+
功能:
-- 新增/變更使用者和使用者群組
-- 變更裝置存取權限
-- 瀏覽裝置連線和其他紀錄檔
+- 瀏覽裝置
+- 新增/修改使用者和使用者群組
+- 修改裝置存取權限
+- 瀏覽裝置連線記錄和其他記錄
- 更新設定
- 管理客戶端設定同步策略
+- 管理共享通訊錄
+- 產生自訂客戶端
## 登入
-如同之前所述,網頁控制台的預設連接埠為 21114。在瀏覽器輸入 `http://:21114` 以進入控制台頁面。如下圖所示 (hbbs 執行在 IP 為 192.168.1.143 的伺服器上):
+網頁控制台的預設連接埠是 21114。在瀏覽器中輸入 `http://<伺服器 ip>:21114` 進入控制台頁面,如下圖所示。預設管理員使用者名稱/密碼是 `admin`/`test1234`:
+

-如果您需要 https,請安裝如 `Nginx` 的網頁伺服器。
+如果您需要 HTTPS 支援,請安裝如 `Nginx` 的網頁伺服器,或在 Windows 上使用 `IIS`。
-預設管理員帳號/密碼為 admin/test1234,請記得在登入後變更密碼,在右上角的帳號選單選擇 "設定" 以進入密碼變更頁面,如下圖所示。您也可以建立另一個管理員帳號,並刪除預設帳號,建議啟用電子郵件登入驗證。
+登入後請務必變更密碼,在右上角的帳號選單中選擇 `設定` 進入密碼修改頁面,如下圖所示。您也可以建立另一個管理員帳號並刪除這個。建議啟用電子郵件登入驗證。

-非管理員使用者也可以登入來瀏覽他們的裝置和記錄,以及變更他們的使用者設定。
+非管理員使用者也可以登入查看他們的裝置和記錄,變更他們的使用者設定。
-## Windows EXE
+## 自動設定
+點選 `Windows EXE` 您將能夠取得您自己的 RustDesk 伺服器專業版的設定,這將協助設定您的客戶端。
-For Windows clients, you can leave out the custom server configuration and put the configuration information in the `RustDesk.exe` filename instead. As shown above, please go to the console welcome page and click on `Windows EXE`. **`Client >=1.1.9 Required`**。
+對於 Windows 客戶端,您可以省略自訂伺服器設定,將設定資訊放在 `rustdesk.exe` 檔案名稱中。如上所示,請進入控制台歡迎頁面並點選 `Windows EXE`。**需要客戶端 ≥ 1.1.9。**
+
+您可以結合[客戶端設定](https://rustdesk.com/docs/zh-tw/self-host/client-configuration/)和[部署腳本](https://rustdesk.com/docs/zh-tw/self-host/client-deployment/)來設定您的客戶端。
+
+## 建立除預設 `admin` 使用者之外的新使用者
+
+{{% notice note %}}
+`個人版` 方案沒有此功能。
+{{% /notice %}}
+
+1. 點選左側選單的 `使用者`。
+2. 建立另一個啟用了 `管理員` 權限的帳號。
+3. 使用新的管理員帳號登入。
+4. 在 `使用者` 頁面刪除 `admin`。
+
+## 建立新使用者
+1. 點選左側選單的 `使用者`。
+2. 建立新使用者。
+3. 選擇他們應該所屬的群組(如果需要新增新群組,請繼續閱讀)。
+
+## 新增新群組
+1. 點選左側選單的 `群組`。
+2. 建立新群組。
+3. 建立後,您可以允許群組之間相互存取,點選 `編輯`。
+4. 選擇您想要存取的相關群組(它會自動將它們新增到相應的群組中)。
+
+## 設定多個中繼伺服器
+1. 進入左側選單的 `設定`。
+2. 點選子選單的 `中繼`。
+3. 點選 `中繼伺服器` 旁邊的 `+`。
+4. 在現在顯示的方塊中輸入中繼伺服器 DNS 位址或 IP 位址,然後按 Enter。
+5. 如果您有多個中繼伺服器,可以繼續點選 `+` 並根據需要調整地理位置設定(記住並將您的金鑰複製到其他伺服器)。
+
+## 設定或變更授權
+1. 進入左側選單的 `設定`。
+2. 點選子選單的 `授權`。
+3. 點選 `編輯` 並貼上您的授權碼。
+4. 點選 `確定`。
+
+## 檢視記錄
+點選左側的 `記錄`。
+
+## 設定電子郵件
+以 Gmail 為例
+
+1. 進入左側選單的 `設定`。
+2. 點選子選單的 `SMTP`。
+3. 輸入 SMTP 位址 `smtp.gmail.com`。
+4. 在 `SMTP 連接埠` 中輸入連接埠 587。
+5. 在 `郵件帳號` 中輸入 Gmail 帳號,例如 `myrustdeskserver@gmail.com`。
+6. 輸入您的密碼(您可能需要應用程式專用密碼)。
+7. 在 `寄件者` 中輸入您的 Gmail 帳號,例如 `myrustdeskserver@gmail.com`。
+8. 點選 `檢查` 儲存。
+
+## 將裝置使用者/群組/策略/裝置群組指派給裝置
+使用者是登入在裝置上的 RustDesk 使用者,或透過點選裝置旁邊的 `編輯` 指派給裝置的使用者,點選 `使用者` 方塊並從下拉式選單中選擇您的使用者,這將根據使用者被指派到的群組自動指派群組。
+
+這也可以透過 API 在部署時或之後在命令列中完成,呼叫 RustDesk 執行檔後接 `--assign --token <產生的權杖> --user_name <使用者名稱>`。您需要先進入 `設定 → 權杖 → 建立` 並建立具有裝置權限的權杖。在 Windows 上的範例為 `"C:\Program Files\RustDesk\rustdesk.exe" --assign --token <產生的權杖> --user_name <新使用者>`。
+
+您也可以透過這種方式指派策略,例如 `--assign --token <產生的權杖> --strategy_name <策略名稱>`。
+
+您也可以透過這種方式指派通訊錄,例如 `--assign --token <產生的權杖> --address_book_name <通訊錄名稱>` 或 `--assign --token <產生的權杖> --address_book_name <通訊錄名稱> --address_book_tag <通訊錄標籤> --address_book_alias <別名>`。`--address_book_alias` 需要 RustDesk 伺服器專業版 >=1.5.8 和客戶端 >=1.4.1。
+
+您也可以透過這種方式指派裝置群組名稱,例如 `--assign --token <產生的權杖> --device_group_name <裝置群組名稱>`。
+
+Windows 上的命令列預設沒有輸出。要取得輸出,請這樣執行:`"C:\Program Files\RustDesk\rustdesk.exe" <參數1> <參數2> ... | more` 或 `"C:\Program Files\RustDesk\rustdesk.exe" <參數1> <參數2> ... | Out-String`,參見[這裡](https://github.com/rustdesk/rustdesk/discussions/6377#discussioncomment-8094952)。
+
+## 搜尋裝置
+1. 進入裝置頁面。
+2. 在裝置名稱搜尋欄位中輸入名稱並點選 `查詢` 或按 Enter。
+3. 要使用萬用字元,請在搜尋詞的開頭、結尾或兩端新增 `%`。
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-pro/faq/_index.de.md b/content/self-host/rustdesk-server-pro/faq/_index.de.md
index 2e4ab1e..3853472 100644
--- a/content/self-host/rustdesk-server-pro/faq/_index.de.md
+++ b/content/self-host/rustdesk-server-pro/faq/_index.de.md
@@ -449,3 +449,14 @@ sudo firewall-cmd --permanent --add-port=443/tcp
```
Danach führen Sie `sudo firewall-cmd --reload` aus, um die Firewall neu zu laden.
+
+## Nach dem Ändern des Administrator-Passworts in der Webkonsole kann ich mich nicht anmelden. Gibt es eine einfache Möglichkeit, das Passwort zurückzusetzen?
+1. Stellen Sie sicher, dass Sie `rustdesk-utils` installiert haben. Wenn nicht, können Sie es [hier](https://github.com/rustdesk/rustdesk-server-pro) erhalten. Außerdem müssen Sie den Befehl aus dem Ordner ausführen, in dem sich die Datenbank befindet, d.h. `/var/lib/rustdesk-server`.
+2. Der Befehl lautet `rustdesk-utils set_password username password`. Wenn es funktioniert, wird *Done* angezeigt.
+
+Sie haben auch die folgenden anderen Befehle `genkeypair`, `validatekeypair [public key] [secret key]`, `doctor [rustdesk-server]`, `reset_email_verification` und `reset_2fa_verification`, die mit `rustdesk-utils` verwendet werden können.
+
+https://github.com/rustdesk/rustdesk-server-pro/discussions/183
+
+## Root-CA-Zertifikat in Docker-Container hinzufügen (für TLS-Fehler mit SMTP, OIDC usw.)
+https://github.com/rustdesk/rustdesk-server-pro/issues/99#issuecomment-2235014703
diff --git a/content/self-host/rustdesk-server-pro/faq/_index.es.md b/content/self-host/rustdesk-server-pro/faq/_index.es.md
index ba8bd65..7717ccf 100644
--- a/content/self-host/rustdesk-server-pro/faq/_index.es.md
+++ b/content/self-host/rustdesk-server-pro/faq/_index.es.md
@@ -447,3 +447,24 @@ sudo firewall-cmd --permanent --add-port=21116/udp
## Agregar certificado CA raíz al contenedor Docker (para falla TLS con SMTP, OIDC etc.)
https://github.com/rustdesk/rustdesk-server-pro/issues/99#issuecomment-2235014703
+
+Si usas IP:
+
+```sh
+sudo firewall-cmd --permanent --add-port=21114/tcp
+```
+
+Si usas DNS/Dominio:
+
+```sh
+sudo firewall-cmd --permanent --add-port=80/tcp
+sudo firewall-cmd --permanent --add-port=443/tcp
+```
+
+Después de lo anterior, ejecuta `sudo firewall-cmd --reload` para recargar el firewall.
+
+También necesitas ejecutar el comando desde la carpeta donde está la base de datos, es decir, `/var/lib/rustdesk-server`.
+
+También tienes los siguientes otros comandos `genkeypair`, `validatekeypair [public key] [secret key]`, `doctor [rustdesk-server]`, `reset_email_verification` y `reset_2fa_verification` que se pueden usar con `rustdesk-utils`.
+
+https://github.com/rustdesk/rustdesk-server-pro/discussions/183
diff --git a/content/self-host/rustdesk-server-pro/faq/_index.it.md b/content/self-host/rustdesk-server-pro/faq/_index.it.md
index d4aa232..94dd3d5 100644
--- a/content/self-host/rustdesk-server-pro/faq/_index.it.md
+++ b/content/self-host/rustdesk-server-pro/faq/_index.it.md
@@ -432,3 +432,114 @@ sudo firewall-cmd --reload
## Aggiungere certificato CA radice nel container Docker (per fallimento TLS con SMTP, OIDC ecc.)
https://github.com/rustdesk/rustdesk-server-pro/issues/99#issuecomment-2235014703
+
+## C'è una nuova versione di RustDesk Server Pro, come posso aggiornare?
+È meglio fare prima il backup dei file di dati (file sqlite3 ecc.), https://github.com/rustdesk/rustdesk-server-pro/discussions/184#discussioncomment-8013375.
+- ### Se hai installato con script (`install.sh`)
+Esegui [update.sh](/docs/en/self-host/rustdesk-server-pro/installscript/script/#upgrade).
+- ### Docker Compose
+```
+sudo docker compose down
+sudo docker compose pull
+sudo docker compose up -d
+```
+Ma questo dipende dalla tua versione di docker, per maggiori discussioni, controlla [questo](https://stackoverflow.com/questions/37685581/how-to-get-docker-compose-to-use-the-latest-image-from-repository).
+- ### Docker
+```
+sudo docker ps
+## puoi anche usare , es. `hbbs` e `hbbr` se segui il nostro manuale.
+sudo docker stop
+sudo docker rm
+sudo docker rmi
+sudo docker run ..... # uguale a come l'hai installato prima
+```
+
+es.
+
+```
+root@hz:~# sudo docker ps
+CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
+30822972c220 rustdesk/rustdesk-server-pro "hbbr" 10 seconds ago Restarting (1) 2 seconds ago hbbr
+0f3a6f185be3 rustdesk/rustdesk-server-pro "hbbs" 15 seconds ago Up 14 seconds hbbs
+root@hz:~# sudo docker kill hbbr hbbs
+hbbr
+hbbs
+root@hz:~# sudo docker ps
+CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
+root@hz:~# sudo docker rm hbbr hbbs
+hbbr
+hbbs
+root@hz:~# sudo docker rmi rustdesk/rustdesk-server-pro
+Untagged: rustdesk/rustdesk-server-pro:latest
+Untagged: rustdesk/rustdesk-server-pro@sha256:401b8344323addf777622d0463bd7b964dd18a01599e42e20d8b3818dae71ad2
+Deleted: sha256:a3d9d43a3d1dd84b10c39fe0abf7767b18a87819ff0981443ce9e9a52604c889
+Deleted: sha256:65ae79ecc0f8b1c8a21085d04af7c8d8f368dd5ad844982d4c7b3ac1f38ba33a
+Deleted: sha256:9274a824aef10f2ef106d8f85fbd1905037169cf610951f63dc5109dae4b0825
+Deleted: sha256:aa89ac8b57a49f49f041c01b9c0f016060e611cf282e3fda281bc6bebbabaf3f
+Deleted: sha256:4af9839016f72586a46f915cae8a5ccf3380ba88a2f79532692d3b1d7020387e
+Deleted: sha256:e900a7ffc2fc14fa432cc04823740dcbb78c0aa3508abbbe287ce8b274541ada
+Deleted: sha256:503eeab76c11e8316a2a450ef0790d31c5af203309e9c5b44d1bf8a601e6e587
+Deleted: sha256:825683356e7dbfcbaabcbf469c9aeb34d36ebeab0308170432b9553e28203116
+Deleted: sha256:24a48d4af45bab05d8712fe22abec5761a7781283500e32e34bdff5798c09399
+root@hz:~# sudo docker images
+REPOSITORY TAG IMAGE ID CREATED SIZE
+rustdesk/makepkg latest 86a981e2e18f 2 months ago 2.23GB
+root@hz:~# sudo docker run --name hbbs -v ./data:/root -td --net=host --restart unless-stopped rustdesk/rustdesk-server-pro hbbs
+Unable to find image 'rustdesk/rustdesk-server-pro:latest' locally
+latest: Pulling from rustdesk/rustdesk-server-pro
+4ce000a43472: Pull complete
+1543f88421d3: Pull complete
+9b209c1f5a8d: Pull complete
+d717f548a400: Pull complete
+1e60b98f5660: Pull complete
+a86960d9bced: Pull complete
+acb361c4bbf6: Pull complete
+4f4fb700ef54: Pull complete
+Digest: sha256:401b8344323addf777622d0463bd7b964dd18a01599e42e20d8b3818dae71ad2
+Status: Downloaded newer image for rustdesk/rustdesk-server-pro:latest
+0cc5387efa8d2099c0d8bc657b10ed153a6b642cd7bbcc56a6c82790a6e49b04
+root@hz:~# sudo docker run --name hbbr -v ./data:/root -td --net=host --restart unless-stopped rustdesk/rustdesk-server-pro hbbr
+4eb9da2dc460810547f6371a1c40a9294750960ef2dbd84168079e267e8f371a
+root@hz:~# sudo docker ps
+CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
+4eb9da2dc460 rustdesk/rustdesk-server-pro "hbbr" 5 seconds ago Restarting (1) Less than a second ago hbbr
+0cc5387efa8d rustdesk/rustdesk-server-pro "hbbs" 8 seconds ago Up 7 seconds hbbs
+root@hz:~# sudo docker images
+REPOSITORY TAG IMAGE ID CREATED SIZE
+rustdesk/rustdesk-server-pro latest a3d9d43a3d1d 5 days ago 193MB
+rustdesk/makepkg latest 86a981e2e18f 2 months ago 2.23GB
+```
+
+Per maggiori dettagli, controlla [questo](https://www.cherryservers.com/blog/how-to-update-docker-image).
+
+Il tuo server mail potrebbe non usare la porta 25. Assicurati di usare le porte corrette.
+
+Se il tuo `hbbr` non gira sulla stessa macchina di `hbbs`, o hai più server relay, o non lo esegui sulla porta predefinita `21117`, devi dirlo esplicitamente a `hbbs`. Controlla [qui](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/relay/).
+
+Hai anche i seguenti altri comandi `genkeypair`, `validatekeypair [public key] [secret key]`, `doctor [rustdesk-server]`, `reset_email_verification` e `reset_2fa_verification` che possono essere usati con `rustdesk-utils`.
+
+https://github.com/rustdesk/rustdesk-server-pro/discussions/183
+
+- [AWS] https://docs.aws.amazon.com/network-firewall/latest/developerguide/getting-started.html
+- [Azure] https://learn.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
+- [Google] https://cloud.google.com/firewall/docs/firewalls
+- [DigitalOcean] https://docs.digitalocean.com/products/networking/firewalls/
+
+RustDesk imposta il firewall con `ufw`. Potrebbe non funzionare su alcune distribuzioni come CentOS 9, puoi provare con `firewall-cmd`:
+
+Se usi IP:
+
+```sh
+sudo firewall-cmd --permanent --add-port=21114/tcp
+```
+
+Se usi DNS/Dominio:
+
+```sh
+sudo firewall-cmd --permanent --add-port=80/tcp
+sudo firewall-cmd --permanent --add-port=443/tcp
+```
+
+Dopo quanto sopra, esegui `sudo firewall-cmd --reload` per ricaricare il firewall.
+
+Inoltre devi eseguire il comando dalla cartella dove si trova il database, cioè `/var/lib/rustdesk-server`.
diff --git a/content/self-host/rustdesk-server-pro/faq/_index.ja.md b/content/self-host/rustdesk-server-pro/faq/_index.ja.md
index ef6392d..fd24c2e 100644
--- a/content/self-host/rustdesk-server-pro/faq/_index.ja.md
+++ b/content/self-host/rustdesk-server-pro/faq/_index.ja.md
@@ -432,3 +432,114 @@ sudo firewall-cmd --reload
## DockerコンテナにルートCA証明書を追加(SMTP、OIDCなどのTLS障害用)
https://github.com/rustdesk/rustdesk-server-pro/issues/99#issuecomment-2235014703
+
+## RustDesk Server Proの新バージョンが出ました。アップグレードするには?
+まずデータファイル(sqlite3ファイルなど)をバックアップすることをお勧めします、https://github.com/rustdesk/rustdesk-server-pro/discussions/184#discussioncomment-8013375。
+- ### スクリプト(`install.sh`)でインストールした場合
+[update.sh](/docs/en/self-host/rustdesk-server-pro/installscript/script/#upgrade)を実行してください。
+- ### Docker Compose
+```
+sudo docker compose down
+sudo docker compose pull
+sudo docker compose up -d
+```
+しかし、これはあなたのdockerバージョンに依存します。詳細な議論については、[こちら](https://stackoverflow.com/questions/37685581/how-to-get-docker-compose-to-use-the-latest-image-from-repository)を確認してください。
+- ### Docker
+```
+sudo docker ps
+## マニュアルに従っている場合は、も使用できます。例:`hbbs`と`hbbr`。
+sudo docker stop
+sudo docker rm
+sudo docker rmi
+sudo docker run ..... # 以前にインストールしたのと同じ
+```
+
+例:
+
+```
+root@hz:~# sudo docker ps
+CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
+30822972c220 rustdesk/rustdesk-server-pro "hbbr" 10 seconds ago Restarting (1) 2 seconds ago hbbr
+0f3a6f185be3 rustdesk/rustdesk-server-pro "hbbs" 15 seconds ago Up 14 seconds hbbs
+root@hz:~# sudo docker kill hbbr hbbs
+hbbr
+hbbs
+root@hz:~# sudo docker ps
+CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
+root@hz:~# sudo docker rm hbbr hbbs
+hbbr
+hbbs
+root@hz:~# sudo docker rmi rustdesk/rustdesk-server-pro
+Untagged: rustdesk/rustdesk-server-pro:latest
+Untagged: rustdesk/rustdesk-server-pro@sha256:401b8344323addf777622d0463bd7b964dd18a01599e42e20d8b3818dae71ad2
+Deleted: sha256:a3d9d43a3d1dd84b10c39fe0abf7767b18a87819ff0981443ce9e9a52604c889
+Deleted: sha256:65ae79ecc0f8b1c8a21085d04af7c8d8f368dd5ad844982d4c7b3ac1f38ba33a
+Deleted: sha256:9274a824aef10f2ef106d8f85fbd1905037169cf610951f63dc5109dae4b0825
+Deleted: sha256:aa89ac8b57a49f49f041c01b9c0f016060e611cf282e3fda281bc6bebbabaf3f
+Deleted: sha256:4af9839016f72586a46f915cae8a5ccf3380ba88a2f79532692d3b1d7020387e
+Deleted: sha256:e900a7ffc2fc14fa432cc04823740dcbb78c0aa3508abbbe287ce8b274541ada
+Deleted: sha256:503eeab76c11e8316a2a450ef0790d31c5af203309e9c5b44d1bf8a601e6e587
+Deleted: sha256:825683356e7dbfcbaabcbf469c9aeb34d36ebeab0308170432b9553e28203116
+Deleted: sha256:24a48d4af45bab05d8712fe22abec5761a7781283500e32e34bdff5798c09399
+root@hz:~# sudo docker images
+REPOSITORY TAG IMAGE ID CREATED SIZE
+rustdesk/makepkg latest 86a981e2e18f 2 months ago 2.23GB
+root@hz:~# sudo docker run --name hbbs -v ./data:/root -td --net=host --restart unless-stopped rustdesk/rustdesk-server-pro hbbs
+Unable to find image 'rustdesk/rustdesk-server-pro:latest' locally
+latest: Pulling from rustdesk/rustdesk-server-pro
+4ce000a43472: Pull complete
+1543f88421d3: Pull complete
+9b209c1f5a8d: Pull complete
+d717f548a400: Pull complete
+1e60b98f5660: Pull complete
+a86960d9bced: Pull complete
+acb361c4bbf6: Pull complete
+4f4fb700ef54: Pull complete
+Digest: sha256:401b8344323addf777622d0463bd7b964dd18a01599e42e20d8b3818dae71ad2
+Status: Downloaded newer image for rustdesk/rustdesk-server-pro:latest
+0cc5387efa8d2099c0d8bc657b10ed153a6b642cd7bbcc56a6c82790a6e49b04
+root@hz:~# sudo docker run --name hbbr -v ./data:/root -td --net=host --restart unless-stopped rustdesk/rustdesk-server-pro hbbr
+4eb9da2dc460810547f6371a1c40a9294750960ef2dbd84168079e267e8f371a
+root@hz:~# sudo docker ps
+CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
+4eb9da2dc460 rustdesk/rustdesk-server-pro "hbbr" 5 seconds ago Restarting (1) Less than a second ago hbbr
+0cc5387efa8d rustdesk/rustdesk-server-pro "hbbs" 8 seconds ago Up 7 seconds hbbs
+root@hz:~# sudo docker images
+REPOSITORY TAG IMAGE ID CREATED SIZE
+rustdesk/rustdesk-server-pro latest a3d9d43a3d1d 5 days ago 193MB
+rustdesk/makepkg latest 86a981e2e18f 2 months ago 2.23GB
+```
+
+詳細については、[こちら](https://www.cherryservers.com/blog/how-to-update-docker-image)を確認してください。
+
+あなたのメールサーバーはポート25を使用していない可能性があります。正しいポートを使用していることを確認してください。
+
+あなたの`hbbr`が`hbbs`と同じマシンで実行されていない場合、または複数のリレーサーバーがある場合、またはデフォルトポート`21117`で実行していない場合は、`hbbs`に明示的に伝える必要があります。[こちら](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/relay/)を確認してください。
+
+また、`rustdesk-utils`で使用できる次のその他のコマンドがあります:`genkeypair`、`validatekeypair [public key] [secret key]`、`doctor [rustdesk-server]`、`reset_email_verification`、`reset_2fa_verification`。
+
+https://github.com/rustdesk/rustdesk-server-pro/discussions/183
+
+- [AWS] https://docs.aws.amazon.com/network-firewall/latest/developerguide/getting-started.html
+- [Azure] https://learn.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
+- [Google] https://cloud.google.com/firewall/docs/firewalls
+- [DigitalOcean] https://docs.digitalocean.com/products/networking/firewalls/
+
+RustDeskは`ufw`でファイアウォールを設定します。CentOS 9のような一部のディストリビューションでは動作しない可能性があります。`firewall-cmd`を試すことができます:
+
+IPを使用する場合:
+
+```sh
+sudo firewall-cmd --permanent --add-port=21114/tcp
+```
+
+DNS/ドメインを使用する場合:
+
+```sh
+sudo firewall-cmd --permanent --add-port=80/tcp
+sudo firewall-cmd --permanent --add-port=443/tcp
+```
+
+上記の後、`sudo firewall-cmd --reload`を実行してファイアウォールをリロードします。
+
+また、データベースがある場所、つまり`/var/lib/rustdesk-server`からコマンドを実行する必要があります。
diff --git a/content/self-host/rustdesk-server-pro/faq/_index.pt.md b/content/self-host/rustdesk-server-pro/faq/_index.pt.md
index 70bd4ed..022924c 100644
--- a/content/self-host/rustdesk-server-pro/faq/_index.pt.md
+++ b/content/self-host/rustdesk-server-pro/faq/_index.pt.md
@@ -431,3 +431,9 @@ sudo firewall-cmd --reload
## Adicionar certificado CA raiz no contêiner Docker (para falha TLS com SMTP, OIDC etc.)
https://github.com/rustdesk/rustdesk-server-pro/issues/99#issuecomment-2235014703
+
+Você também precisa executar o comando da pasta onde o banco de dados está, ou seja, `/var/lib/rustdesk-server`.
+
+Você também tem os seguintes outros comandos `genkeypair`, `validatekeypair [public key] [secret key]`, `doctor [rustdesk-server]`, `reset_email_verification` e `reset_2fa_verification` que podem ser usados com `rustdesk-utils`.
+
+https://github.com/rustdesk/rustdesk-server-pro/discussions/183
diff --git a/content/self-host/rustdesk-server-pro/installscript/Script/_index.zh-cn.md b/content/self-host/rustdesk-server-pro/installscript/Script/_index.zh-cn.md
index 89a7730..38f3892 100644
--- a/content/self-host/rustdesk-server-pro/installscript/Script/_index.zh-cn.md
+++ b/content/self-host/rustdesk-server-pro/installscript/Script/_index.zh-cn.md
@@ -4,7 +4,9 @@ weight: 4
---
{{% notice note %}}
-别忘了从 https://rustdesk.com/pricing.html 取得授权,查阅[授权](/docs/en/self-host/rustdesk-server-pro/license)页面以了解详情。
+别忘了从 [https://rustdesk.com/pricing/](https://rustdesk.com/pricing/) 取得授权,查阅[授权](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/license/)页面以了解详情。
+
+请在进行这个简单安装之前先阅读[OSS安装](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/install/)。您可以在那里了解更多底层细节。
{{% /notice %}}
## 安装
@@ -13,15 +15,33 @@ weight: 4
`wget -qO- https://raw.githubusercontent.com/rustdesk/rustdesk-server-pro/main/install.sh | bash`
-流程:
+{{% notice note %}}
+我建议使用[Docker镜像](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/installscript/docker/#docker-compose);它极大地简化了部署解决方案以及更新的过程。资源消耗非常低。
-- 安装依赖包
-- 在可用情况下设定 ufw 防火墙
-- 建立文件夹 /var/lib/rustdesk-server 和 /var/log/rustdesk-server
-- 在 /usr/bin 安装可执行文件
-- 下载 RustDesk 专业版服务并解压缩到上述文件料夹
-- 为 hbbs 和 hbbr 建立 systemd 服务
-- 如果您选择了 Domain,将安装 Nginx 和 certbot,让 API 能够在端口 443 (https) 存取,并透过端口 80 取得 SSL 证书,这将自动更新
+并且请在您的主目录下运行上述命令,而不是在您没有写权限的目录。
+{{% /notice %}}
+
+它做了什么:
+
+- 安装一些依赖项
+- 在可用情况下设定 UFW 防火墙
+- 创建工作目录 `/var/lib/rustdesk-server` 和日志目录 `/var/log/rustdesk-server`
+- 将可执行文件安装到 `/usr/bin`
+- 下载并解压 RustDesk Pro 服务到上述文件夹
+- 为 hbbs 和 hbbr 创建 systemd 服务(服务名称为 `rustdesk-hbbs.service` 和 `rustdesk-hbbr.service`)
+- 如果您选择了域名,它将安装 Nginx 和 Certbot,让 API 能够在端口 `443` (HTTPS) 上访问,并通过端口 `80` 获取 SSL 证书,它会自动续期。当 https 准备就绪后,请使用 `https://yourdomain.com` 访问,而不是 `https://yourdomain.com:21114`。
+
+{{% notice note %}}
+如何[手动为 Web 控制台设置 HTTPS](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/faq/#set-up-https-for-web-console-manually)。
+{{% /notice %}}
+
+{{% notice note %}}
+如果 systemd 服务启动失败,可能与 SELinux 有关,请查看[这里](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/faq/#selinux)。
+{{% /notice %}}
+
+{{% notice note %}}
+如果您的客户端无法连接到您的服务器或您无法访问 Web 控制台,请查看[这里](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/faq/#firewall)。
+{{% /notice %}}
## 升级
@@ -29,7 +49,13 @@ weight: 4
`wget -qO- https://raw.githubusercontent.com/rustdesk/rustdesk-server-pro/main/update.sh | bash`
-流程:
+{{% notice note %}}
+如果您在使用此脚本时遇到问题,我建议您浏览脚本并逐步手动执行步骤。
+
+并且请在您的主目录下运行上述命令,而不是在您没有写权限的目录。
+{{% /notice %}}
+
+它做了什么:
- 检查 RustDesk-Server-Pro 的新版本
- 如果找到新版本,移除 API 文件并下载新可执行文件和 API 文件
@@ -40,13 +66,21 @@ weight: 4
`wget -qO- https://raw.githubusercontent.com/rustdesk/rustdesk-server-pro/main/convertfromos.sh | bash`
-流程:
+{{% notice note %}}
+请将 `21114` TCP 端口添加到您的防火墙,这是 Web 控制台和 RustDesk 客户端中用户登录的额外端口。
+{{% /notice %}}
+
+{{% notice note %}}
+如果您在使用此脚本时遇到问题,我建议切换到 Docker 安装。或者,您可以浏览脚本并逐步手动执行步骤。
+{{% /notice %}}
+
+它做了什么:
- 停用并移除旧服务
- 安装依赖包
-- 在可用情况下设定 ufw 防火墙
-- 建立文件夹 /var/lib/rustdesk-server 并将证书复制到该文件夹
-- 删除 /var/log/rustdesk 并建立 /var/log/rustdesk-server
-- 下载 RustDesk 专业版服务并解压缩到上述文件夹
-- 为 hbbs 和 hbbr 建立 systemd 服务
-- 如果您选择了 Domain,将安装 Nginx 和 certbot,让 API 能够在端口 443 (https) 存取,并透过端口 80 取得 SSL 证书,这将自动更新
+- 在可用情况下设定 UFW 防火墙
+- 创建文件夹 `/var/lib/rustdesk-server` 并将证书复制到这里
+- 删除 `/var/log/rustdesk` 并创建 `/var/log/rustdesk-server`
+- 下载并解压 RustDesk Pro 服务到上述文件夹
+- 为 hbbs 和 hbbr 创建 systemd 服务(服务名称为 rustdesk-hbbs.service 和 rustdesk-hbbr.service)
+- 如果您选择了域名,它将安装 Nginx 和 Certbot,让 API 能够在端口 443 (HTTPS) 上访问,并通过端口 80 获取 SSL 证书,它会自动续期
diff --git a/content/self-host/rustdesk-server-pro/installscript/Script/_index.zh-tw.md b/content/self-host/rustdesk-server-pro/installscript/Script/_index.zh-tw.md
index 4f358c4..3997a45 100644
--- a/content/self-host/rustdesk-server-pro/installscript/Script/_index.zh-tw.md
+++ b/content/self-host/rustdesk-server-pro/installscript/Script/_index.zh-tw.md
@@ -4,7 +4,9 @@ weight: 4
---
{{% notice note %}}
-別忘了從 https://rustdesk.com/pricing.html 取得授權,查閱[授權](/docs/en/self-host/rustdesk-server-pro/license)頁面以了解詳情。
+別忘了從 [https://rustdesk.com/pricing/](https://rustdesk.com/pricing/) 取得授權,查閱[授權](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/license/)頁面以了解詳情。
+
+請在進行這個簡單安裝之前先閱讀[OSS安裝](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/install/)。您可以在那裡了解更多底層細節。
{{% /notice %}}
## 安裝
@@ -13,15 +15,33 @@ weight: 4
`wget -qO- https://raw.githubusercontent.com/rustdesk/rustdesk-server-pro/main/install.sh | bash`
-流程:
+{{% notice note %}}
+我建議使用[Docker映像](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/installscript/docker/#docker-compose);它極大地簡化了部署解決方案以及更新的過程。資源消耗非常低。
-- 安裝依賴套件
-- 在可用情況下設定 ufw 防火牆
-- 建立資料夾 /var/lib/rustdesk-server 和 /var/log/rustdesk-server
-- 在 /usr/bin 安裝執行檔
-- 下載 RustDesk 專業版服務並解壓縮到上述資料夾
-- 為 hbbs 和 hbbr 建立 systemd 服務
-- 如果您選擇了 Domain,將安裝 Nginx 和 certbot,讓 API 能夠在連接埠 443 (https) 存取,並透過連接埠 80 取得 SSL 證書,這將自動更新
+並且請在您的主目錄下執行上述命令,而不是在您沒有寫權限的目錄。
+{{% /notice %}}
+
+它做了什麼:
+
+- 安裝一些依賴項
+- 在可用情況下設定 UFW 防火牆
+- 創建工作目錄 `/var/lib/rustdesk-server` 和日誌目錄 `/var/log/rustdesk-server`
+- 將可執行檔案安裝到 `/usr/bin`
+- 下載並解壓 RustDesk Pro 服務到上述資料夾
+- 為 hbbs 和 hbbr 創建 systemd 服務(服務名稱為 `rustdesk-hbbs.service` 和 `rustdesk-hbbr.service`)
+- 如果您選擇了網域,它將安裝 Nginx 和 Certbot,讓 API 能夠在連接埠 `443` (HTTPS) 上存取,並透過連接埠 `80` 獲取 SSL 證書,它會自動續期。當 https 準備就緒後,請使用 `https://yourdomain.com` 存取,而不是 `https://yourdomain.com:21114`。
+
+{{% notice note %}}
+如何[手動為 Web 控制台設定 HTTPS](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/faq/#set-up-https-for-web-console-manually)。
+{{% /notice %}}
+
+{{% notice note %}}
+如果 systemd 服務啟動失敗,可能與 SELinux 有關,請查看[這裡](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/faq/#selinux)。
+{{% /notice %}}
+
+{{% notice note %}}
+如果您的客戶端無法連接到您的伺服器或您無法存取 Web 控制台,請查看[這裡](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/faq/#firewall)。
+{{% /notice %}}
## 升級
@@ -29,7 +49,13 @@ weight: 4
`wget -qO- https://raw.githubusercontent.com/rustdesk/rustdesk-server-pro/main/update.sh | bash`
-流程:
+{{% notice note %}}
+如果您在使用此腳本時遇到問題,我建議您瀏覽腳本並逐步手動執行步驟。
+
+並且請在您的主目錄下執行上述命令,而不是在您沒有寫權限的目錄。
+{{% /notice %}}
+
+它做了什麼:
- 檢查 RustDesk-Server-Pro 的新版本
- 如果找到新版本,移除 API 檔案並下載新執行檔和 API 檔案
@@ -40,13 +66,33 @@ weight: 4
`wget -qO- https://raw.githubusercontent.com/rustdesk/rustdesk-server-pro/main/convertfromos.sh | bash`
-流程:
+{{% notice note %}}
+請將 `21114` TCP 連接埠加入到您的防火牆,這是 Web 控制台和 RustDesk 客戶端中使用者登入的額外連接埠。
+{{% /notice %}}
+
+{{% notice note %}}
+如果您在使用此腳本時遇到問題,我建議切換到 Docker 安裝。或者,您可以瀏覽腳本並逐步手動執行步驟。
+{{% /notice %}}
+
+它做了什麼:
- 停用並移除舊服務
- 安裝依賴套件
-- 在可用情況下設定 ufw 防火牆
-- 建立資料夾 /var/lib/rustdesk-server 並將證書複製到該資料夾
-- 刪除 /var/log/rustdesk 並建立 /var/log/rustdesk-server
-- 下載 RustDesk 專業版服務並解壓縮到上述資料夾
-- 為 hbbs 和 hbbr 建立 systemd 服務
-- 如果您選擇了 Domain,將安裝 Nginx 和 certbot,讓 API 能夠在連接埠 443 (https) 存取,並透過連接埠 80 取得 SSL 證書,這將自動更新
+- 在可用情況下設定 UFW 防火牆
+- 創建資料夾 `/var/lib/rustdesk-server` 並將證書複製到這裡
+- 刪除 `/var/log/rustdesk` 並創建 `/var/log/rustdesk-server`
+- 下載並解壓 RustDesk Pro 服務到上述資料夾
+- 為 hbbs 和 hbbr 創建 systemd 服務(服務名稱為 `rustdesk-hbbs.service` 和 `rustdesk-hbbr.service`)
+- 如果您選擇了網域,它將安裝 Nginx 和 Certbot,讓 API 能夠在連接埠 `443` (HTTPS) 上存取,並透過連接埠 `80` 獲取 SSL 證書,它會自動續期。當 https 準備就緒後,請使用 `https://yourdomain.com` 存取,而不是 `https://yourdomain.com:21114`。
+
+{{% notice note %}}
+如何[手動為 Web 控制台設定 HTTPS](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/faq/#set-up-https-for-web-console-manually)。
+{{% /notice %}}
+
+{{% notice note %}}
+如果 systemd 服務啟動失敗,可能與 SELinux 有關,請查看[這裡](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/faq/#selinux)。
+{{% /notice %}}
+
+{{% notice note %}}
+如果您的客戶端無法連接到您的伺服器或您無法存取 Web 控制台,請查看[這裡](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/faq/#firewall)。
+{{% /notice %}}
diff --git a/content/self-host/rustdesk-server-pro/license/_index.de.md b/content/self-host/rustdesk-server-pro/license/_index.de.md
index 448d272..ba57322 100644
--- a/content/self-host/rustdesk-server-pro/license/_index.de.md
+++ b/content/self-host/rustdesk-server-pro/license/_index.de.md
@@ -11,7 +11,7 @@ Bitte beziehen Sie Ihre Lizenz von [https://rustdesk.com/pricing.html](https://r
## Lizenz eingeben
-Sie müssen die Lizenz in der Webkonsole eingeben oder später ändern.
+Sie müssen die Lizenz in der Webkonsole (`http://:21114`) eingeben oder später ändern.
| Lizenz eingeben | Lizenz ändern |
| --- | --- |
@@ -19,12 +19,15 @@ Sie müssen die Lizenz in der Webkonsole eingeben oder später ändern.
## Lizenz verlängern bzw. aktualisieren
-Verlängerung bzw. Aktualisierung der Lizenz erfolgt über das [Self-Service-Lizenzportal](https://rustdesk.com/self-host/account/) wie unten beschrieben.
+Verlängerung bzw. Aktualisierung der Lizenz erfolgt über das [Self-Service-Lizenzportal](https://rustdesk.com/self-host/account/) wie unten beschrieben, melden Sie sich mit der E-Mail-Adresse an, die Sie zum Kauf der Lizenz verwendet haben, wie im obigen Bild gezeigt.
| Lizenzseite mit Verlängerungs-/Aktualisierungsaktionen | Aktualisierungsfenster |
| --- | --- |
|  |  |
+Nach der Zahlung aktualisieren Sie bitte die Lizenz [wie unten beschrieben](/docs/de/self-host/rustdesk-server-pro/license/#lizenz-aktualisieren), um sie zu aktivieren.
+
+### Lizenz aktualisieren
Nach der Zahlung müssen Sie die Webkonsole aufrufen, um sie manuell zu aktivieren. Klicken Sie einfach auf `Edit` und dann auf `OK`. Sie brauchen nichts zu bearbeiten, denn Ihr Lizenzschlüssel bleibt derselbe.

@@ -34,3 +37,10 @@ Nach der Zahlung müssen Sie die Webkonsole aufrufen, um sie manuell zu aktivier
Die Lizenz kann nur auf einem Rechner verwendet werden (nur für hbbs, hbbr benötigt keine Lizenz). Wenn Sie auf einen anderen Rechner migrieren, Ihre Lizenz abrufen oder Rechnungen herunterladen möchten, gehen Sie bitte auf [https://rustdesk.com/self-host/account/](https://rustdesk.com/self-host/account/). Melden Sie sich mit der auf der Bezahlseite von Stripe verwendeten E-Mail-Adresse an und heben Sie die Bindung des alten Rechners, von dem Sie migrieren möchten, wie unten zu sehen, auf. Wenn Sie die Lizenz in der Webkonsole des neuen Servers einrichten, wird die Lizenz zugewiesen und automatisch in der Konsole registriert.

+
+## Proxy
+Wenn Ihr Server nicht direkt auf das Internet zugreifen kann, um die Lizenz zu überprüfen, können Sie einen Proxy hinzufügen, z.B. `proxy=http://username:password@example.com:8080 ./hbbs`.
+
+Alternativ können Sie `proxy=http://username:password@example.com:8080` zur `.env`-Datei im Arbeitsverzeichnis hinzufügen (wo sich die Dateien `id_ed25519` / `db.sqlite3` befinden).
+
+`http` kann durch `https` oder `socks5` ersetzt werden. Wenn es keinen `username` / `password` / `port` gibt, kann es `proxy=http://example.com` sein.
diff --git a/content/self-host/rustdesk-server-pro/license/_index.zh-cn.md b/content/self-host/rustdesk-server-pro/license/_index.zh-cn.md
index e69b2c6..dd77859 100644
--- a/content/self-host/rustdesk-server-pro/license/_index.zh-cn.md
+++ b/content/self-host/rustdesk-server-pro/license/_index.zh-cn.md
@@ -5,20 +5,42 @@ weight: 15
## 购买授权
-请从 https://rustdesk.com/pricing.html 取得授权码,在 Stripe 结帐页面输入有效的电子邮件地址。授权码将在付款完成后寄送到您的电子邮件地址。
+请从 [https://rustdesk.com/pricing.html](https://rustdesk.com/pricing.html) 获取您的许可证,在Stripe结账页面输入有效的电子邮件地址。付款成功完成后,许可证(以及单独邮件中的发票)将发送到您的电子邮件。

## 设定授权
-您将须在网页控制台输入授权码,或变更授权。
+您将须在网页控制台(`http://:21114`)输入授权码,或稍后变更授权。
- | 设定授权 | 变更授权 |
- | -- | -- |
-  |  |
+| 设定授权 | 变更授权 |
+| --- | --- |
+|  |  |
-## 发票和迁移
+## 续期/升级许可证
-授权码只能在一台机器上使用 (仅 hbbs,hbbr 不需授权码),如果您想要迁移至其他机器,或下载发票,请前往 [https://rustdesk.com/self-host/account/](https://rustdesk.com/self-host/account/)。透过在 Stripe 支付页面输入的电子邮件地址登入,解除旧机器绑定,如下图所示。新机器将在您于网页控制台设定授权码时自动注册。
+续期/升级许可证可以通过[自助许可证门户](https://rustdesk.com/self-host/account/)找到,如下所述,使用您购买许可证时使用的电子邮件登录。
+
+| 带有续期/升级操作的许可证页面 | 升级窗口 |
+| --- | --- |
+|  |  |
+
+支付后,请按照[下面的方法](/docs/en/self-host/rustdesk-server-pro/license/#refresh-license)刷新许可证以激活它。
+
+### 刷新许可证
+支付后,您需要进入网页控制台手动激活,如下所示。只需点击`编辑`,然后点击`确定`,无需编辑任何内容,因为您的许可证密钥保持不变。
+
+
+
+## 发票、许可证检索和迁移
+
+许可证只能在一台机器上使用(仅限hbbs,hbbr不需要许可证),如果您想要迁移到其他机器、检索您的许可证或下载发票,请访问[https://rustdesk.com/self-host/account/](https://rustdesk.com/self-host/account/)。使用在Stripe结账时使用的电子邮件地址登录,解绑您要迁移的旧机器,如下所示,当您在新服务器的网页控制台中设置许可证时,它将自动分配许可证并在控制台中注册。

+
+## 代理
+如果您的服务器无法直接访问互联网以验证许可证,您可以添加代理,例如`proxy=http://username:password@example.com:8080 ./hbbs`。
+
+或者,您可以将`proxy=http://username:password@example.com:8080`添加到工作目录(`id_ed25519` / `db.sqlite3`文件所在的位置)下的`.env`文件中。
+
+`http`可以替换为`https`或`socks5`。如果没有`username` / `password` / `port`,可以使用`proxy=http://example.com`。
diff --git a/content/self-host/rustdesk-server-pro/license/_index.zh-tw.md b/content/self-host/rustdesk-server-pro/license/_index.zh-tw.md
index f2c9cd8..0222cfd 100644
--- a/content/self-host/rustdesk-server-pro/license/_index.zh-tw.md
+++ b/content/self-host/rustdesk-server-pro/license/_index.zh-tw.md
@@ -5,20 +5,42 @@ weight: 15
## 購買授權
-請從 https://rustdesk.com/pricing.html 取得授權,在 Stripe 結帳頁面輸入有效的電子郵件地址。授權將在付款完成後寄送到您的電子郵件地址。
+請從 [https://rustdesk.com/pricing.html](https://rustdesk.com/pricing.html) 獲取您的許可證,在Stripe結帳頁面輸入有效的電子郵件地址。付款成功完成後,許可證(以及單獨郵件中的發票)將發送到您的電子郵件。

## 設定授權
-您將須在網頁控制台輸入授權,或變更授權。
+您將須在網頁控制台(`http://:21114`)輸入授權,或稍後變更授權。
- | 設定授權 | 變更授權 |
- | -- | -- |
-  |  |
+| 設定授權 | 變更授權 |
+| --- | --- |
+|  |  |
-## 發票和轉移
+## 續期/升級許可證
-授權只能在一台機器上使用 (僅 hbbs,hbbr 不需授權),如果您想要轉移至其他機器,或下載發票,請前往 [https://rustdesk.com/self-host/account/](https://rustdesk.com/self-host/account/)。透過在 Stripe 結帳頁面輸入的電子郵件地址登入,解除綁定舊機器,如下圖所示。新機器將在您於網頁控制台設定授權時自動註冊。
+續期/升級許可證可以通過[自助許可證門戶](https://rustdesk.com/self-host/account/)找到,如下所述,使用您購買許可證時使用的電子郵件登錄。
+
+| 帶有續期/升級操作的許可證頁面 | 升級窗口 |
+| --- | --- |
+|  |  |
+
+支付後,請按照[下面的方法](/docs/en/self-host/rustdesk-server-pro/license/#refresh-license)刷新許可證以激活它。
+
+### 刷新許可證
+支付後,您需要進入網頁控制台手動激活,如下所示。只需點擊`編輯`,然後點擊`確定`,無需編輯任何內容,因為您的許可證密鑰保持不變。
+
+
+
+## 發票、許可證檢索和遷移
+
+許可證只能在一台機器上使用(僅限hbbs,hbbr不需要許可證),如果您想要遷移到其他機器、檢索您的許可證或下載發票,請訪問[https://rustdesk.com/self-host/account/](https://rustdesk.com/self-host/account/)。使用在Stripe結帳時使用的電子郵件地址登錄,解綁您要遷移的舊機器,如下所示,當您在新伺服器的網頁控制台中設置許可證時,它將自動分配許可證並在控制台中註冊。

+
+## 代理
+如果您的伺服器無法直接訪問互聯網以驗證許可證,您可以添加代理,例如`proxy=http://username:password@example.com:8080 ./hbbs`。
+
+或者,您可以將`proxy=http://username:password@example.com:8080`添加到工作目錄(`id_ed25519` / `db.sqlite3`文件所在的位置)下的`.env`文件中。
+
+`http`可以替換為`https`或`socks5`。如果沒有`username` / `password` / `port`,可以使用`proxy=http://example.com`。
diff --git a/content/self-host/rustdesk-server-pro/oidc/_index.de.md b/content/self-host/rustdesk-server-pro/oidc/_index.de.md
index 3e8002f..04d55e6 100644
--- a/content/self-host/rustdesk-server-pro/oidc/_index.de.md
+++ b/content/self-host/rustdesk-server-pro/oidc/_index.de.md
@@ -3,5 +3,8 @@ title: OIDC
weight: 16
---
-- Verwenden Sie Ihre bestehenden Konten bei `Google`, `Okta`, `Facebook`, `Azure`, `Github`, `Gitlab` usw., um Ihr `RustDesk Pro`-Konto einfach zu erstellen und sich dort anzumelden.
+- Verwenden Sie Ihre bestehenden Konten bei `Google`, `Okta`, `Facebook`, `Azure`, `GitHub`, `GitLab` usw., um Ihr `RustDesk Pro`-Konto einfach zu erstellen und sich dort anzumelden.
- Für die Spezifikation siehe [OpenID Connect Core 1.0 incorporating errata set 1](https://openid.net/specs/openid-connect-core-1_0.html).
+
+# Beispiele
+{{% children depth="4" showhidden="true" %}}
diff --git a/content/self-host/rustdesk-server-pro/oidc/_index.zh-cn.md b/content/self-host/rustdesk-server-pro/oidc/_index.zh-cn.md
index 0808e40..b753b52 100644
--- a/content/self-host/rustdesk-server-pro/oidc/_index.zh-cn.md
+++ b/content/self-host/rustdesk-server-pro/oidc/_index.zh-cn.md
@@ -3,5 +3,8 @@ title: OIDC
weight: 16
---
-- 使用现有的 Google,Okta,Facebook, Azure, Github, Gitlab 等账号,方便地创建和登录 RustDesk Pro 账户。
-- 说明。[openid-connect-core-1_0](https://openid.net/specs/openid-connect-core-1_0.html)
+- 使用您现有的 `Google`、`Okta`、`Facebook`、`Azure`、`GitHub`、`GitLab` 等账号,轻松创建和登录您的 `RustDesk Pro` 账户。
+- 规范说明请参见 [OpenID Connect Core 1.0 incorporating errata set 1](https://openid.net/specs/openid-connect-core-1_0.html)。
+
+# 示例
+{{% children depth="4" showhidden="true" %}}
diff --git a/content/self-host/rustdesk-server-pro/permissions/_index.de.md b/content/self-host/rustdesk-server-pro/permissions/_index.de.md
index 0eca2f3..a96b4f8 100644
--- a/content/self-host/rustdesk-server-pro/permissions/_index.de.md
+++ b/content/self-host/rustdesk-server-pro/permissions/_index.de.md
@@ -4,36 +4,48 @@ weight: 16
---
## Zugriffsberechtigungen für Geräte
+
Das Gerät kann entweder einem einzelnen Benutzer, einer einzelnen Gerätegruppe oder beiden zugewiesen werden.
-Wenn das Gerät einem Benutzer zugewiesen ist, kann es von diesem Benutzer, einer Benutzergruppe oder durch entsprechende gruppenübergreifende Einstellungen zugegriffen werden.
+Wenn das Gerät einem Benutzer zugewiesen ist, kann von diesem Benutzer, einer Benutzergruppe oder durch entsprechende gruppenübergreifende Einstellungen darauf zugegriffen werden.
-Wenn das Gerät einer Gerätegruppe zugewiesen ist, kann es über entsprechende gruppenübergreifende Geräteeinstellungen zugegriffen werden.
+Wenn das Gerät einer Gerätegruppe zugewiesen ist, kann über entsprechende Benutzer-Gerätegruppen-übergreifende Einstellungen darauf zugegriffen werden.
Es gibt drei Möglichkeiten, ein Gerät einem Benutzer zuzuweisen:
- Über die Konsolengeräteseite
- Anmeldung beim angegebenen Benutzerkonto auf der Clientseite
-- Zuweisung über die Befehlszeile
-
+- Zuweisungsbefehlszeile
+
Es gibt zwei Möglichkeiten, ein Gerät einer Gerätegruppe zuzuweisen:
- Über die Konsolengeräteseite
-- Zuweisung über die Befehlszeile
+- Zuweisungsbefehlszeile
Die folgenden zwei Situationen verhindern den Zugriff auf das Gerät:
- Gerät auf der Konsolengeräteseite `deaktivieren`
- Benutzer auf der Konsolenbenutzerseite `deaktivieren`
-## Gruppenübergreifende Einstellungen
+## Benutzergruppen-Zugriffseinstellungen
Gehen Sie bitte in der Webkonsole auf die Gruppenseite und klicken Sie auf `Bearbeiten`, um die gruppenübergreifenden Einstellungen wie unten beschrieben zu bearbeiten.
-Ihre Änderungen am `Zugriff für andere Gruppen` werden sofort wirksam, ohne dass Sie auf die Schaltfläche `OK` klicken müssen.
+Ihre Änderungen an `Zugriff mit anderen Gruppen` werden sofort wirksam, ohne dass Sie auf die Schaltfläche `OK` klicken müssen.
-Sowohl `Kann zugreifen auf` als auch `Kann zugegriffen werden von` dienen nahezu der gleichen Funktion, wir bieten beide Optionen für Ihren Komfort. Dies kann jedoch zu einiger Verwirrung führen.
+Sowohl `Kann zugreifen auf` als auch `Kann zugegriffen werden von` erfüllen nahezu die gleiche Funktion, wir bieten beide Optionen für Ihre Bequemlichkeit. Dies kann jedoch zu einiger Verwirrung führen.
{{% notice note %}}
-Der Benutzer und die Gruppe, die der steuernden Seite zugewiesen werden, werden durch den Benutzer bestimmt, der sich anmeldet, und nicht durch den Benutzer, der über die Webkonsole zugewiesen wird. Wir haben dies so konzipiert, weil bestimmte steuernden Seiten keine Geräte-ID haben, wie z. B. der iOS-Client und der Webclient.
+Der Benutzer und die Gruppe, die der steuernden Seite zugewiesen werden, werden durch den Benutzer bestimmt, der sich anmeldet, und nicht durch den Benutzer, der über die Webkonsole zugewiesen wird. Wir haben dies so konzipiert, weil bestimmte steuernde Seiten keine Geräte-ID haben, wie z. B. der iOS-Client und der Webclient.
{{% /notice %}}

+## Gerätegruppen-Zugriffseinstellungen
+
+Gerätegruppen bieten eine weitere Möglichkeit, Zugriffsberechtigungen zu verwalten. Hier sind die wichtigsten Regeln:
+
+1. Ein Gerät kann nur zu einer Gerätegruppe hinzugefügt werden
+2. Sie können Zugriffsberechtigungen für Benutzer oder Benutzergruppen zu Gerätegruppen festlegen. Diese Berechtigungen sind kumulativ mit den Benutzergruppen-Zugriffsberechtigungen - das bedeutet, dass der Zugriff gewährt wird, wenn entweder die Benutzergruppenberechtigungen oder die Gerätegruppenberechtigungen dies erlauben
+3. Wenn ein nicht zugewiesenes Gerät zu einer Gerätegruppe hinzugefügt wird, gilt es nicht mehr als "nicht zugewiesen"
+
+{{% notice note %}}
+Die Gerätegruppen-Funktion erfordert RustDesk Client >= 1.3.8 und RustDesk Server Pro >= 1.5.0
+{{% /notice %}}
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-pro/relay/_index.zh-cn.md b/content/self-host/rustdesk-server-pro/relay/_index.zh-cn.md
index b541e10..12649f0 100644
--- a/content/self-host/rustdesk-server-pro/relay/_index.zh-cn.md
+++ b/content/self-host/rustdesk-server-pro/relay/_index.zh-cn.md
@@ -8,7 +8,7 @@ weight: 17
{{% notice note %}}
[简单安装](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/installscript/)会在同一台机器上隐式创建一个中继服务器(`hbbr`进程),您无需显式指定中继服务器。
-如果您想在另一台机器上显式创建附加中继服务器,请按照[OSS安装](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/install/)运行`hbbr`。您可以在`rustdesk-server-linux-amd64.tar.gz`、`rustdesk-server-hbbr_<版本>-<架构>.deb`、`rustdesk-server-windows-x86_64.tar.gz`或`docker`(`sudo docker run ... rustdesk/rustdesk-server-pro hbbr`)中找到`hbbr`。
+如果您想在另一台机器上显式创建附加中继服务器,请按照[OSS安装](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/install/)运行`hbbr`。您可以在`rustdesk-server-linux-amd64.tar.gz`、`rustdesk-server-hbbr_-.deb`、`rustdesk-server-windows-x86_64.tar.gz`或`docker`(`sudo docker run ... rustdesk/rustdesk-server-pro hbbr`)中找到`hbbr`。
`hbbr`不需要许可证,与开源版本相同。
{{% /notice %}}
@@ -28,13 +28,17 @@ weight: 17
# docker volume create hbbr
```
-2. 将私钥对复制到卷位置:
+卷hbbr应该位于`/var/lib/docker/volumes/hbbr/_data`。
+
+2. 将私钥对复制到卷位置,在本例中我们将使用SCP复制文件。
+
+命令语法为`scp <路径/文件名> 用户名@服务器:`。
```
# scp id_ed25519 root@100.100.100.100:/var/lib/docker/volumes/hbbr/_data
# scp id_ed25519.pub root@100.100.100.100:/var/lib/docker/volumes/hbbr/_data
```
-3. 使用先前创建的卷部署hbbr容器:
+3. 使用先前创建的卷部署hbbr容器。该卷包含运行私有中继服务器所需的私钥对。
```
# sudo docker run --name hbbr -v hbbr:/root -td --net=host rustdesk/rustdesk-server hbbr -k _
```
@@ -42,14 +46,40 @@ weight: 17
4. 检查运行日志以验证hbbr正在使用您的密钥对运行:
```
# docker logs hbbr
+
+INFO [src/common.rs:121] **Private key comes from id_ed25519**
+NFO [src/relay_server.rs:581] Key: XXXXXXXXXXXXXXXXXXXXX
+INFO [src/relay_server.rs:60] #blacklist(blacklist.txt): 0
+INFO [src/relay_server.rs:75] #blocklist(blocklist.txt): 0
+INFO [src/relay_server.rs:81] Listening on tcp :21117
```
+根据您的操作系统,您可能希望使用防火墙阻止/允许IP。
+
+在我们的例子中,运行Ubuntu时,我们希望允许任何TCP连接到端口21117和21119。
+
# 防火墙配置
```
# sudo ufw allow proto tcp from any to any port 21117,21119
+```
+
+**启用防火墙**
+```
# sudo ufw enable
```
+**检查状态**
+```
+# ufw status
+
+Status: active
+
+To Action From
+-- ------ ----
+21117,21119/tcp ALLOW Anywhere
+21117,21119/tcp (v6) ALLOW Anywhere (v6)
+```
+
## 使用Web控制台为地理位置配置RustDesk Pro
### 注册并下载GeoLite2 City数据库文件
@@ -57,27 +87,61 @@ weight: 17
要使用地理位置,hbbs需要访问MaxMind GeoLite2 City数据库。该数据库是免费的,您可以注册下载文件并获取API密钥。
1. 在[网站](https://www.maxmind.com/en/account/login)创建账户
-2. 转到`Download Databases`并下载GeoLite2 City
-3. 选择gzip文件,解压缩后应该有`mmdb`文件
+首先通过访问[网站](https://www.maxmind.com/en/account/login)创建账户(如果您还没有)。
+转到`Download Databases`并下载GeoLite2 City,选择gzip文件,解压缩后应该有`mmdb`文件。
-对于Linux安装,`mmdb`文件需要移动到`/var/lib/rustdesk-server/`。
-对于Docker安装,文件应该在您映射到`/root`的卷中。
+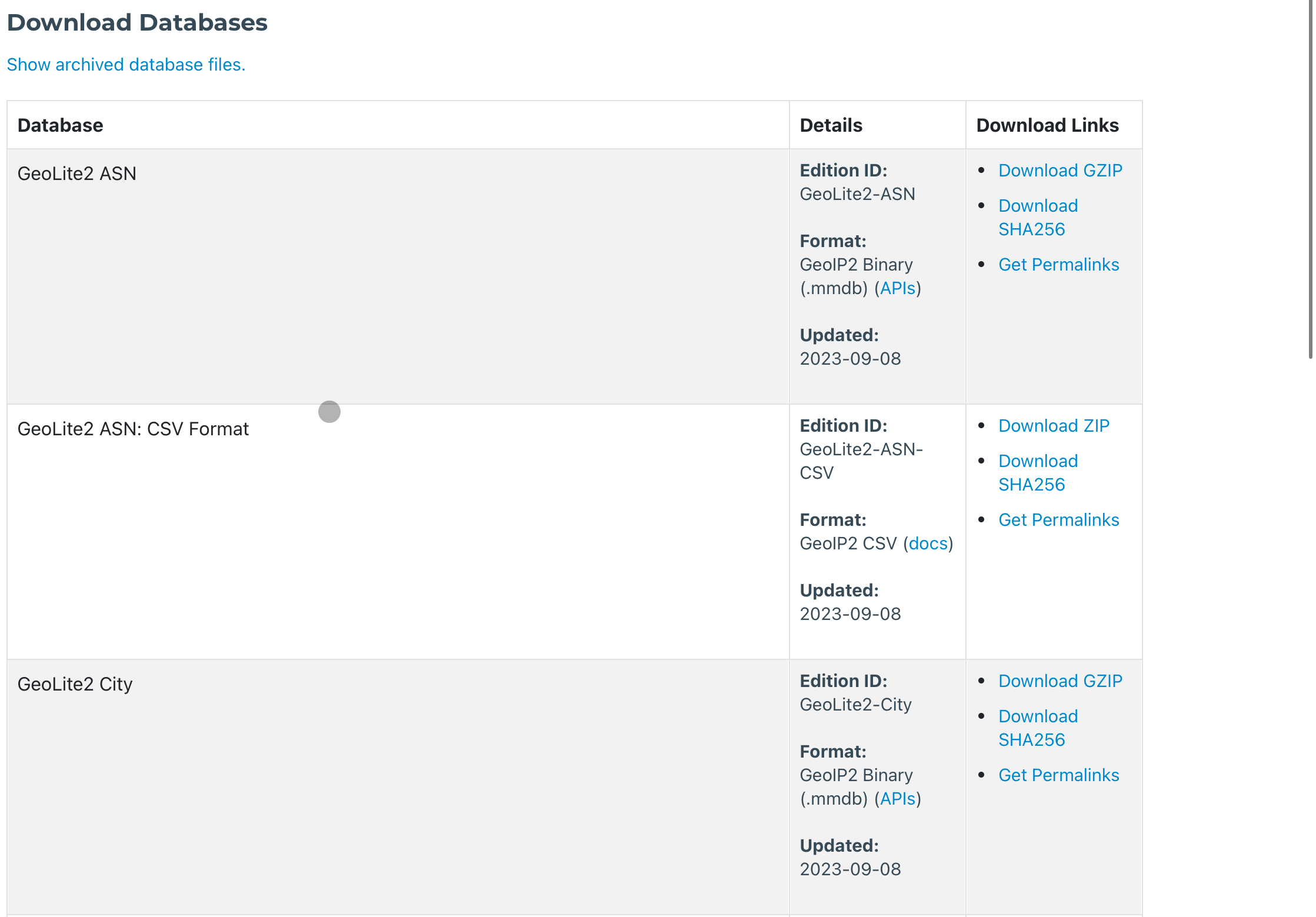 -### 获取API密钥以自动化流程
+如果您使用安装脚本在Linux机器上安装了RustDesk Pro,`mmdb`文件需要移动到`/var/lib/rustdesk-server/`。
-您需要定期更新此文件,可以使用cronjob来执行。您需要一个API密钥来访问下载链接,这是免费的。
+对于Docker安装,文件应该在部署容器时映射到`/root`的卷中。
-转到`Manage License Keys`并生成新的许可证密钥。
+### 获取API密钥以自动化流程 - Linux服务器
-自动化下载命令:
+您需要定期更新此文件,我们可以使用cronjob来执行。您需要一个API密钥来访问下载链接,这是免费的。
+
+转到`Manage License Keys`并生成新的许可证密钥。
-### 获取API密钥以自动化流程
+如果您使用安装脚本在Linux机器上安装了RustDesk Pro,`mmdb`文件需要移动到`/var/lib/rustdesk-server/`。
-您需要定期更新此文件,可以使用cronjob来执行。您需要一个API密钥来访问下载链接,这是免费的。
+对于Docker安装,文件应该在部署容器时映射到`/root`的卷中。
-转到`Manage License Keys`并生成新的许可证密钥。
+### 获取API密钥以自动化流程 - Linux服务器
-自动化下载命令:
+您需要定期更新此文件,我们可以使用cronjob来执行。您需要一个API密钥来访问下载链接,这是免费的。
+
+转到`Manage License Keys`并生成新的许可证密钥。
+ +
+
+ +
+您可以通过几种方式自动化[下载过程](https://dev.maxmind.com/geoip/updating-databases),但您可以将以下命令添加到您的crontab中,将{Your Access Key}替换为您从上一步获得的API密钥。
```
/usr/bin/curl -L --silent 'https://download.maxmind.com/app/geoip_download?edition_id=GeoLite2-City&license_key={Your Access Key}&suffix=tar.gz' | /bin/tar -C '/var/lib/rustdesk-server/' -xvz --keep-newer-files --strip-components=1 --wildcards '*GeoLite2-City.mmdb'
```
### 在RustDesk Pro Web控制台中更改设置
-1. 将中继服务器IP地址或DNS名称添加到`Relay Servers`(不需要端口,显式使用`21117`端口)
-2. 添加地理覆盖,通过添加服务器IP地址和服务器所在位置的坐标
-3. 点击`Reload Geo`
+将您的中继服务器IP地址或DNS名称(从版本1.1.11开始支持DNS)添加到`Relay Servers`。**不需要端口,显式使用`21117`端口。**
+
+您可以通过几种方式自动化[下载过程](https://dev.maxmind.com/geoip/updating-databases),但您可以将以下命令添加到您的crontab中,将{Your Access Key}替换为您从上一步获得的API密钥。
```
/usr/bin/curl -L --silent 'https://download.maxmind.com/app/geoip_download?edition_id=GeoLite2-City&license_key={Your Access Key}&suffix=tar.gz' | /bin/tar -C '/var/lib/rustdesk-server/' -xvz --keep-newer-files --strip-components=1 --wildcards '*GeoLite2-City.mmdb'
```
### 在RustDesk Pro Web控制台中更改设置
-1. 将中继服务器IP地址或DNS名称添加到`Relay Servers`(不需要端口,显式使用`21117`端口)
-2. 添加地理覆盖,通过添加服务器IP地址和服务器所在位置的坐标
-3. 点击`Reload Geo`
+将您的中继服务器IP地址或DNS名称(从版本1.1.11开始支持DNS)添加到`Relay Servers`。**不需要端口,显式使用`21117`端口。**
+ -要确认结果,在点击`Reload Geo`时检查您的hbbs日志,您应该看到显示中继服务器IP地址及其坐标的消息。
\ No newline at end of file
+通过添加服务器IP地址和服务器所在位置的坐标来添加地理覆盖。
-要确认结果,在点击`Reload Geo`时检查您的hbbs日志,您应该看到显示中继服务器IP地址及其坐标的消息。
\ No newline at end of file
+通过添加服务器IP地址和服务器所在位置的坐标来添加地理覆盖。
+ +
+点击`Reload Geo`,您的列表应该类似于此。
+
+点击`Reload Geo`,您的列表应该类似于此。
+ +
+要确认结果,在点击`Reload Geo`时检查您的hbbs日志,您应该看到显示中继服务器IP地址及其坐标的消息。
+
+> 如果您在Linux机器上运行RustDesk Pro,请使用命令`RUST_LOG=debug ./hbbs`查看日志。如果您在Docker容器上运行,请使用`docker logs hbbs`。
+
+```
+RUST_LOG=debug ./hbbs
+
+INFO [src/common.rs:130] GEOIP_FILE: ./GeoLite2-City.mmdb
+INFO [src/common.rs:159] override 1xx.xxx.xxx.x7: -1.xx 5x.xxx
+[src/common.rs:159] override 1xx.xxx.xxx.xx8: -3.xxx 5x.xxxx
+[src/common.rs:159] override 7xx.xxx.xxxx.xx1: 6.xxx 5x.xxxx
+GEOIP_FILE loaded, #overrides 3
+INFO [src/common.rs:119] relay-servers=["1xx.xxx.xxx.x7", "1xx.xxx.xxx.xx8", "7xx.xxx.xxx.xx1"]
+NFO [src/rendezvous_server.rs:1467] parsed relay servers: [("1xx.xxxx.xxx.xx7", Some((-1x, xxx))), ("1xx.xxx.xxx.xx8", Some((-3x, xxx))), ("7xx.xxx.xxx.xx1", Some((6x, xxx)))]
+```
+
+您还可以直接在hbbr实例上确认中继请求,只需检查容器日志即可。
+
+```
+# docker logs hbbr
+
+INFO [src/relay_server.rs:436] Relayrequest 0593e64e-4fe8-4a59-a94f-b3420ab043eb from [::ffff:100.100.123.233]:52038 got paired
+INFO [src/relay_server.rs:442] Both are raw
+```
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-pro/relay/_index.zh-tw.md b/content/self-host/rustdesk-server-pro/relay/_index.zh-tw.md
index dda34ba..42316c1 100644
--- a/content/self-host/rustdesk-server-pro/relay/_index.zh-tw.md
+++ b/content/self-host/rustdesk-server-pro/relay/_index.zh-tw.md
@@ -8,61 +8,139 @@ weight: 17
{{% notice note %}}
[簡單安裝](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/installscript/)會在同一台機器上隱式創建一個中繼伺服器(`hbbr`進程),您無需顯式指定中繼伺服器。
-如果您想在另一台機器上顯式創建附加中繼伺服器,請按照[OSS安裝](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/install/)運行`hbbr`。
+如果您想在另一台機器上顯式創建附加中繼伺服器,請按照[OSS安裝](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/install/)運行`hbbr`。您可以在`rustdesk-server-linux-amd64.tar.gz`、`rustdesk-server-hbbr_-.deb`、`rustdesk-server-windows-x86_64.tar.gz`或`docker`(`sudo docker run ... rustdesk/rustdesk-server-pro hbbr`)中找到`hbbr`。
`hbbr`不需要許可證,與開源版本相同。
{{% /notice %}}
您可以在全球運行多個中繼伺服器,並利用地理位置自動使用最近的中繼伺服器,從而在連接遠程計算機時獲得更快的體驗。`hbbs`每隔幾秒鐘自動檢查這些中繼伺服器是否在線,它只選擇在線的中繼伺服器。
+{{% notice note %}}
+已知問題:https://github.com/rustdesk/rustdesk/discussions/7934
+{{% /notice %}}
+
> 您需要私鑰對`id_ed25519`和`id_ed25519.pub`。
# 安裝步驟
-1. 如果已安裝docker,通過SSH連接到您的伺服器並為hbbr創建卷:
+1 - 如果已安裝docker,通過SSH連接到您的伺服器並為hbbr創建卷:
```
# docker volume create hbbr
```
-2. 將私鑰對複製到卷位置:
+卷hbbr應該位於`/var/lib/docker/volumes/hbbr/_data`。
+
+2 - 將私鑰對複製到卷位置,在本例中我們將使用SCP複製文件。
+
+命令語法為`scp <路徑/文件名> 用戶名@伺服器:`。
```
# scp id_ed25519 root@100.100.100.100:/var/lib/docker/volumes/hbbr/_data
# scp id_ed25519.pub root@100.100.100.100:/var/lib/docker/volumes/hbbr/_data
```
-3. 使用先前創建的卷部署hbbr容器:
+3 - 使用先前創建的卷部署hbbr容器。該卷包含運行私有中繼伺服器所需的私鑰對。
```
# sudo docker run --name hbbr -v hbbr:/root -td --net=host rustdesk/rustdesk-server hbbr -k _
```
-4. 檢查運行日誌以驗證hbbr正在使用您的密鑰對運行:
+4 - 檢查運行日誌以驗證hbbr正在使用您的密鑰對運行:
```
# docker logs hbbr
+
+INFO [src/common.rs:121] **Private key comes from id_ed25519**
+NFO [src/relay_server.rs:581] Key: XXXXXXXXXXXXXXXXXXXXX
+INFO [src/relay_server.rs:60] #blacklist(blacklist.txt): 0
+INFO [src/relay_server.rs:75] #blocklist(blocklist.txt): 0
+INFO [src/relay_server.rs:81] Listening on tcp :21117
```
-# 防火牆配置
+根據您的作業系統,您可能希望使用防火牆阻止/允許IP。
+
+在我們的例子中,運行Ubuntu時,我們希望允許任何TCP連接到端口21117和21119。
+
```
# sudo ufw allow proto tcp from any to any port 21117,21119
+```
+
+**啟用防火牆**
+```
# sudo ufw enable
```
+**檢查狀態**
+```
+# ufw status
+
+Status: active
+
+To Action From
+-- ------ ----
+21117,21119/tcp ALLOW Anywhere
+21117,21119/tcp (v6) ALLOW Anywhere (v6)
+```
+
## 使用Web控制台為地理位置配置RustDesk Pro
### 註冊並下載GeoLite2 City資料庫檔案
要使用地理位置,hbbs需要訪問MaxMind GeoLite2 City資料庫。該資料庫是免費的,您可以註冊下載檔案並獲取API密鑰。
-1. 在[網站](https://www.maxmind.com/en/account/login)創建帳戶
-2. 轉到`Download Databases`並下載GeoLite2 City
-3. 選擇gzip檔案,解壓縮後應該有`mmdb`檔案
+首先通過訪問[網站](https://www.maxmind.com/en/account/login)創建賬戶(如果您還沒有)。
+轉到`Download Databases`並下載GeoLite2 City,選擇gzip檔案,解壓縮後應該有`mmdb`檔案。
-對於Linux安裝,`mmdb`檔案需要移動到`/var/lib/rustdesk-server/`。
-對於Docker安裝,檔案應該在您映射到`/root`的卷中。
+
+
+要确认结果,在点击`Reload Geo`时检查您的hbbs日志,您应该看到显示中继服务器IP地址及其坐标的消息。
+
+> 如果您在Linux机器上运行RustDesk Pro,请使用命令`RUST_LOG=debug ./hbbs`查看日志。如果您在Docker容器上运行,请使用`docker logs hbbs`。
+
+```
+RUST_LOG=debug ./hbbs
+
+INFO [src/common.rs:130] GEOIP_FILE: ./GeoLite2-City.mmdb
+INFO [src/common.rs:159] override 1xx.xxx.xxx.x7: -1.xx 5x.xxx
+[src/common.rs:159] override 1xx.xxx.xxx.xx8: -3.xxx 5x.xxxx
+[src/common.rs:159] override 7xx.xxx.xxxx.xx1: 6.xxx 5x.xxxx
+GEOIP_FILE loaded, #overrides 3
+INFO [src/common.rs:119] relay-servers=["1xx.xxx.xxx.x7", "1xx.xxx.xxx.xx8", "7xx.xxx.xxx.xx1"]
+NFO [src/rendezvous_server.rs:1467] parsed relay servers: [("1xx.xxxx.xxx.xx7", Some((-1x, xxx))), ("1xx.xxx.xxx.xx8", Some((-3x, xxx))), ("7xx.xxx.xxx.xx1", Some((6x, xxx)))]
+```
+
+您还可以直接在hbbr实例上确认中继请求,只需检查容器日志即可。
+
+```
+# docker logs hbbr
+
+INFO [src/relay_server.rs:436] Relayrequest 0593e64e-4fe8-4a59-a94f-b3420ab043eb from [::ffff:100.100.123.233]:52038 got paired
+INFO [src/relay_server.rs:442] Both are raw
+```
\ No newline at end of file
diff --git a/content/self-host/rustdesk-server-pro/relay/_index.zh-tw.md b/content/self-host/rustdesk-server-pro/relay/_index.zh-tw.md
index dda34ba..42316c1 100644
--- a/content/self-host/rustdesk-server-pro/relay/_index.zh-tw.md
+++ b/content/self-host/rustdesk-server-pro/relay/_index.zh-tw.md
@@ -8,61 +8,139 @@ weight: 17
{{% notice note %}}
[簡單安裝](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/installscript/)會在同一台機器上隱式創建一個中繼伺服器(`hbbr`進程),您無需顯式指定中繼伺服器。
-如果您想在另一台機器上顯式創建附加中繼伺服器,請按照[OSS安裝](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/install/)運行`hbbr`。
+如果您想在另一台機器上顯式創建附加中繼伺服器,請按照[OSS安裝](https://rustdesk.com/docs/en/self-host/rustdesk-server-oss/install/)運行`hbbr`。您可以在`rustdesk-server-linux-amd64.tar.gz`、`rustdesk-server-hbbr_-.deb`、`rustdesk-server-windows-x86_64.tar.gz`或`docker`(`sudo docker run ... rustdesk/rustdesk-server-pro hbbr`)中找到`hbbr`。
`hbbr`不需要許可證,與開源版本相同。
{{% /notice %}}
您可以在全球運行多個中繼伺服器,並利用地理位置自動使用最近的中繼伺服器,從而在連接遠程計算機時獲得更快的體驗。`hbbs`每隔幾秒鐘自動檢查這些中繼伺服器是否在線,它只選擇在線的中繼伺服器。
+{{% notice note %}}
+已知問題:https://github.com/rustdesk/rustdesk/discussions/7934
+{{% /notice %}}
+
> 您需要私鑰對`id_ed25519`和`id_ed25519.pub`。
# 安裝步驟
-1. 如果已安裝docker,通過SSH連接到您的伺服器並為hbbr創建卷:
+1 - 如果已安裝docker,通過SSH連接到您的伺服器並為hbbr創建卷:
```
# docker volume create hbbr
```
-2. 將私鑰對複製到卷位置:
+卷hbbr應該位於`/var/lib/docker/volumes/hbbr/_data`。
+
+2 - 將私鑰對複製到卷位置,在本例中我們將使用SCP複製文件。
+
+命令語法為`scp <路徑/文件名> 用戶名@伺服器:`。
```
# scp id_ed25519 root@100.100.100.100:/var/lib/docker/volumes/hbbr/_data
# scp id_ed25519.pub root@100.100.100.100:/var/lib/docker/volumes/hbbr/_data
```
-3. 使用先前創建的卷部署hbbr容器:
+3 - 使用先前創建的卷部署hbbr容器。該卷包含運行私有中繼伺服器所需的私鑰對。
```
# sudo docker run --name hbbr -v hbbr:/root -td --net=host rustdesk/rustdesk-server hbbr -k _
```
-4. 檢查運行日誌以驗證hbbr正在使用您的密鑰對運行:
+4 - 檢查運行日誌以驗證hbbr正在使用您的密鑰對運行:
```
# docker logs hbbr
+
+INFO [src/common.rs:121] **Private key comes from id_ed25519**
+NFO [src/relay_server.rs:581] Key: XXXXXXXXXXXXXXXXXXXXX
+INFO [src/relay_server.rs:60] #blacklist(blacklist.txt): 0
+INFO [src/relay_server.rs:75] #blocklist(blocklist.txt): 0
+INFO [src/relay_server.rs:81] Listening on tcp :21117
```
-# 防火牆配置
+根據您的作業系統,您可能希望使用防火牆阻止/允許IP。
+
+在我們的例子中,運行Ubuntu時,我們希望允許任何TCP連接到端口21117和21119。
+
```
# sudo ufw allow proto tcp from any to any port 21117,21119
+```
+
+**啟用防火牆**
+```
# sudo ufw enable
```
+**檢查狀態**
+```
+# ufw status
+
+Status: active
+
+To Action From
+-- ------ ----
+21117,21119/tcp ALLOW Anywhere
+21117,21119/tcp (v6) ALLOW Anywhere (v6)
+```
+
## 使用Web控制台為地理位置配置RustDesk Pro
### 註冊並下載GeoLite2 City資料庫檔案
要使用地理位置,hbbs需要訪問MaxMind GeoLite2 City資料庫。該資料庫是免費的,您可以註冊下載檔案並獲取API密鑰。
-1. 在[網站](https://www.maxmind.com/en/account/login)創建帳戶
-2. 轉到`Download Databases`並下載GeoLite2 City
-3. 選擇gzip檔案,解壓縮後應該有`mmdb`檔案
+首先通過訪問[網站](https://www.maxmind.com/en/account/login)創建賬戶(如果您還沒有)。
+轉到`Download Databases`並下載GeoLite2 City,選擇gzip檔案,解壓縮後應該有`mmdb`檔案。
-對於Linux安裝,`mmdb`檔案需要移動到`/var/lib/rustdesk-server/`。
-對於Docker安裝,檔案應該在您映射到`/root`的卷中。
+ +
+如果您使用安裝腳本在Linux機器上安裝了RustDesk Pro,`mmdb`檔案需要移動到`/var/lib/rustdesk-server/`。
+
+對於Docker安裝,檔案應該在部署容器時映射到`/root`的卷中。
+
+### 獲取API密鑰以自動化流程 - Linux伺服器
+
+您需要定期更新此檔案,我們可以使用cronjob來執行。您需要一個API密鑰來訪問下載鏈接,這是免費的。
+
+轉到`Manage License Keys`並生成新的許可證密鑰。
+
+如果您使用安裝腳本在Linux機器上安裝了RustDesk Pro,`mmdb`檔案需要移動到`/var/lib/rustdesk-server/`。
+
+對於Docker安裝,檔案應該在部署容器時映射到`/root`的卷中。
+
+### 獲取API密鑰以自動化流程 - Linux伺服器
+
+您需要定期更新此檔案,我們可以使用cronjob來執行。您需要一個API密鑰來訪問下載鏈接,這是免費的。
+
+轉到`Manage License Keys`並生成新的許可證密鑰。
+ +
+
+ +
+您可以通過幾種方式自動化[下載過程](https://dev.maxmind.com/geoip/updating-databases),但您可以將以下命令添加到您的crontab中,將{Your Access Key}替換為您從上一步獲得的API密鑰。
+
+```
+/usr/bin/curl -L --silent 'https://download.maxmind.com/app/geoip_download?edition_id=GeoLite2-City&license_key={Your Access Key}&suffix=tar.gz' | /bin/tar -C '/var/lib/rustdesk-server/' -xvz --keep-newer-files --strip-components=1 --wildcards '*GeoLite2-City.mmdb'
+```
### 在RustDesk Pro Web控制台中更改設置
-1. 將中繼伺服器IP地址或DNS名稱添加到`Relay Servers`(不需要端口,顯式使用`21117`端口)
-2. 添加地理覆蓋,通過添加伺服器IP地址和伺服器所在位置的坐標
-3. 點擊`Reload Geo`
+將您的中繼伺服器IP地址或DNS名稱(從版本1.1.11開始支持DNS)添加到`Relay Servers`。**不需要端口,顯式使用`21117`端口。**
+
+您可以通過幾種方式自動化[下載過程](https://dev.maxmind.com/geoip/updating-databases),但您可以將以下命令添加到您的crontab中,將{Your Access Key}替換為您從上一步獲得的API密鑰。
+
+```
+/usr/bin/curl -L --silent 'https://download.maxmind.com/app/geoip_download?edition_id=GeoLite2-City&license_key={Your Access Key}&suffix=tar.gz' | /bin/tar -C '/var/lib/rustdesk-server/' -xvz --keep-newer-files --strip-components=1 --wildcards '*GeoLite2-City.mmdb'
+```
### 在RustDesk Pro Web控制台中更改設置
-1. 將中繼伺服器IP地址或DNS名稱添加到`Relay Servers`(不需要端口,顯式使用`21117`端口)
-2. 添加地理覆蓋,通過添加伺服器IP地址和伺服器所在位置的坐標
-3. 點擊`Reload Geo`
+將您的中繼伺服器IP地址或DNS名稱(從版本1.1.11開始支持DNS)添加到`Relay Servers`。**不需要端口,顯式使用`21117`端口。**
+ -要確認結果,在點擊`Reload Geo`時檢查您的hbbs日誌,您應該看到顯示中繼伺服器IP地址及其坐標的訊息。
\ No newline at end of file
+通過添加伺服器IP地址和伺服器所在位置的坐標來添加地理覆蓋。
-要確認結果,在點擊`Reload Geo`時檢查您的hbbs日誌,您應該看到顯示中繼伺服器IP地址及其坐標的訊息。
\ No newline at end of file
+通過添加伺服器IP地址和伺服器所在位置的坐標來添加地理覆蓋。
+ +
+點擊`Reload Geo`,您的列表應該類似於此。
+
+點擊`Reload Geo`,您的列表應該類似於此。
+ +
+要確認結果,在點擊`Reload Geo`時檢查您的hbbs日誌,您應該看到顯示中繼伺服器IP地址及其坐標的訊息。
+
+> 如果您在Linux機器上運行RustDesk Pro,請使用命令`RUST_LOG=debug ./hbbs`查看日誌。如果您在Docker容器上運行,請使用`docker logs hbbs`。
+
+```
+RUST_LOG=debug ./hbbs
+
+INFO [src/common.rs:130] GEOIP_FILE: ./GeoLite2-City.mmdb
+INFO [src/common.rs:159] override 1xx.xxx.xxx.x7: -1.xx 5x.xxx
+[src/common.rs:159] override 1xx.xxx.xxx.xx8: -3.xxx 5x.xxxx
+[src/common.rs:159] override 7xx.xxx.xxxx.xx1: 6.xxx 5x.xxxx
+GEOIP_FILE loaded, #overrides 3
+INFO [src/common.rs:119] relay-servers=["1xx.xxx.xxx.x7", "1xx.xxx.xxx.xx8", "7xx.xxx.xxx.xx1"]
+NFO [src/rendezvous_server.rs:1467] parsed relay servers: [("1xx.xxxx.xxx.xx7", Some((-1x, xxx))), ("1xx.xxx.xxx.xx8", Some((-3x, xxx))), ("7xx.xxx.xxx.xx1", Some((6x, xxx)))]
+```
+
+您還可以直接在hbbr實例上確認中繼請求,只需檢查容器日誌即可。
+
+```
+# docker logs hbbr
+
+INFO [src/relay_server.rs:436] Relayrequest 0593e64e-4fe8-4a59-a94f-b3420ab043eb from [::ffff:100.100.123.233]:52038 got paired
+INFO [src/relay_server.rs:442] Both are raw
+```
\ No newline at end of file
+
+要確認結果,在點擊`Reload Geo`時檢查您的hbbs日誌,您應該看到顯示中繼伺服器IP地址及其坐標的訊息。
+
+> 如果您在Linux機器上運行RustDesk Pro,請使用命令`RUST_LOG=debug ./hbbs`查看日誌。如果您在Docker容器上運行,請使用`docker logs hbbs`。
+
+```
+RUST_LOG=debug ./hbbs
+
+INFO [src/common.rs:130] GEOIP_FILE: ./GeoLite2-City.mmdb
+INFO [src/common.rs:159] override 1xx.xxx.xxx.x7: -1.xx 5x.xxx
+[src/common.rs:159] override 1xx.xxx.xxx.xx8: -3.xxx 5x.xxxx
+[src/common.rs:159] override 7xx.xxx.xxxx.xx1: 6.xxx 5x.xxxx
+GEOIP_FILE loaded, #overrides 3
+INFO [src/common.rs:119] relay-servers=["1xx.xxx.xxx.x7", "1xx.xxx.xxx.xx8", "7xx.xxx.xxx.xx1"]
+NFO [src/rendezvous_server.rs:1467] parsed relay servers: [("1xx.xxxx.xxx.xx7", Some((-1x, xxx))), ("1xx.xxx.xxx.xx8", Some((-3x, xxx))), ("7xx.xxx.xxx.xx1", Some((6x, xxx)))]
+```
+
+您還可以直接在hbbr實例上確認中繼請求,只需檢查容器日誌即可。
+
+```
+# docker logs hbbr
+
+INFO [src/relay_server.rs:436] Relayrequest 0593e64e-4fe8-4a59-a94f-b3420ab043eb from [::ffff:100.100.123.233]:52038 got paired
+INFO [src/relay_server.rs:442] Both are raw
+```
\ No newline at end of file