diff --git a/content/_index.en.md b/content/_index.en.md
index ef992dd..439ade4 100644
--- a/content/_index.en.md
+++ b/content/_index.en.md
@@ -5,9 +5,9 @@ weight: 1
# RustDesk Documentation
-RustDesk is a full-featured open source remote control alternative for self-hosting and security with minimal configuration. You have full control of your data, with no concerns about security. The Client is open source and theres a choice between the fully featured Professional Server available to purchase on our [website](https://rustdesk.com) and the basic free and OSS Server based on our Professional Server.
+RustDesk is a full-featured open source remote control alternative for self-hosting and security with minimal configuration. You have full control of your data, with no concerns about security. The Client is open source and theres a choice between the fully featured **Professional Server** available to purchase on our [website](https://rustdesk.com) and the basic free and OSS Server based on our **Professional Server**.
-## Features
+### Features
- Works on Windows, macOS, Linux, iOS, Android, Web.
- Supports VP8 / VP9 / AV1 software codecs, and H264 / H265 hardware codecs.
- Own your data, easily set up self-hosting solution on your infrastructure.
@@ -15,10 +15,11 @@ RustDesk is a full-featured open source remote control alternative for self-host
- No administrative privileges or installation needed for Windows, elevate privilege locally or from remote on demand.
- We like to keep things simple and will strive to make simpler where possible.
-## GitHub Repos
-Main Client Repo: https://github.com/rustdesk/rustdesk
-Open source Server Repo: https://github.com/rustdesk/rustdesk-server
-Pro Server Repo: https://github.com/rustdesk/rustdesk-server-pro
-Docs Repo: https://github.com/rustdesk/doc.rustdesk.com
+### GitHub Repositories
+Main Client Repository: https://github.com/rustdesk/rustdesk
+Open source Server Repository: https://github.com/rustdesk/rustdesk-server
+Pro Server Repository: https://github.com/rustdesk/rustdesk-server-pro
+Doc Repository: https://github.com/rustdesk/doc.rustdesk.com
{{% children depth="3" showhidden="true" %}}
+
diff --git a/content/client/Windows Portable Elevation/_index.en.md b/content/client/Windows Portable Elevation/_index.en.md
index 281eab2..bc5be90 100644
--- a/content/client/Windows Portable Elevation/_index.en.md
+++ b/content/client/Windows Portable Elevation/_index.en.md
@@ -14,7 +14,7 @@ By elevating privileges, RustDesk can create a process with administrator privil
This way, remote users don't need to request elevation when connecting. There are two methods:
-* Method 1: Change the name of the portable program to include `-qs-` (1.2.0, 1.2.1, 1.2.2 versions end with `qs.exe`). Click the left mouse button to run, click `Accept` in the UAC window.
+* Method 1: Change the name of the portable program to include `-qs-` (1.2.0, 1.2.1, 1.2.2, 1.2.3 versions end with `qs.exe`). Click the left mouse button to run, click `Accept` in the UAC window.
* Method 2: Right-click and run as administrator.
@@ -28,7 +28,7 @@ The controlled end can directly click `Accept and Elevate` when connecting, or c
### Request elevation at the control end
-After selecting `Request Elevation` from the action menu, the following dialog box will appear. If you choose `Ask the remote user for authentication`, you won't need to input a username and password, but the user on the remote computer must have administrator privileges. If you select `Transmit the username and password of administrator"`, the user on the remote computer only needs to accept in the UAC window. After sending the request, please wait for the user on the other side to accept the UAC window. Upon confirmation, a success message will appear. Note that **both methods require someone on the controlled end to accept the UAC window**. Therefore, if there is no one available on the other side, elevation should not be requested at the control end.
+After selecting `Request Elevation` from the action menu, the following dialog box will appear. If you choose `Ask the remote user for authentication`, you won't need to input a username and password, but the user on the remote computer must have administrator privileges. If you select `Transmit the username and password of administrator`, the user on the remote computer only needs to accept in the UAC window. After sending the request, please wait for the user on the other side to accept the UAC window. Upon confirmation, a success message will appear. Note that **both methods require someone on the controlled end to accept the UAC window**. Therefore, if there is no one available on the other side, elevation should not be requested at the control end.
| Menu | Dialog |
| :---: | :---: |
diff --git a/content/client/_index.en.md b/content/client/_index.en.md
index b19ad08..eb2ec45 100755
--- a/content/client/_index.en.md
+++ b/content/client/_index.en.md
@@ -12,7 +12,7 @@ The RustDesk Client is used on devices to connect via our RustDesk Server either
- macOS
- Debian Derivatives (Ubuntu, Mint, etc.)
- Redhat Derivatives (Centos, Rocky, etc.)
-- Arch/Manjaro
+- Arch Linux/Manjaro
- openSUSE
- AppImage / Flatpak
- Android
@@ -54,7 +54,7 @@ sudo apt install -fy ./rustdesk-.deb
sudo yum localinstall ./rustdesk-.rpm
```
-#### Arch/Manjaro
+#### Arch Linux/Manjaro
```sh
sudo pacman -U ./rustdesk-.pkg.tar.zst
diff --git a/content/client/linux/SELinux/_index.en.md b/content/client/linux/SELinux/_index.en.md
index 5d50c55..d5bd0c8 100644
--- a/content/client/linux/SELinux/_index.en.md
+++ b/content/client/linux/SELinux/_index.en.md
@@ -9,7 +9,7 @@ You can run `sestatus` in the terminal to check whether SELinux is enabled.
Depending on whether it is enabled or not, you can see two different outputs as follows:
-```bash
+```sh
# Enabled
SELinux status: enabled
...
@@ -19,39 +19,39 @@ SELinux status: disabled
...
```
-## Add SELinux Policies
+### Add SELinux Policies
For an introduction to SELinux, please refer to [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials).
Here we take Fedora 38 as an example to introduce how to add SELinux policies.
-```bash
+```sh
sudo dnf install selinux-policy-devel make
```
Adding SELinux policies requires determining the type of service, which is in the security context of the process.
-```bash
+```sh
$ ps -eZ | grep rustdesk
system_u:system_r:init_t:s0 80439 ? 00:00:02 rustdesk
```
-`system_u:system_r:init_t:s0` is the security context of the rustdesk process, where the third field `init_t` is the type of the process.
+`system_u:system_r:init_t:s0` is the security context of the RustDesk process, where the third field `init_t` is the type of the process.
There are two ways to write SELinux type rules:
1. Add rules to the default `init_t`.
2. Add a new type `rustdesk_t` and add rules.
-The first method has relatively minor modifications, but because the default `init_t` is changed, it is equivalent to adding authorization to other services using the `init_t` type. **Not recommended for use**.
+The first method has relatively minor modifications, but because the default `init_t` is changed, it is equivalent to adding authorization to other services using the `init_t` type. **Not recommended for use.**
The second method is to add rules from scratch. There will be many rules that need to be added, and different systems may have differences. It may be necessary to make some adjustments during actual use.
-### Use The Default Type
+#### Use The Default Type
-The default type of the RustDesk service is `init_t``, which is determined by [the context inheritance rules of SELinux](https://wiki.gentoo.org/wiki/SELinux/Tutorials/How_does_a_process_get_into_a_certain_context).
+The default type of the RustDesk service is `init_t`, which is determined by [the context inheritance rules of SELinux](https://wiki.gentoo.org/wiki/SELinux/Tutorials/How_does_a_process_get_into_a_certain_context).
-**CAUTION**: Modifying the default type means that the policies of other services may also change. Please use this method with caution!
+**Caution**: Modifying the default type means that the policies of other services may also change. Please use this method with caution!
Edit the rule file rustdesk.te:
@@ -108,15 +108,15 @@ allow init_t user_tmp_t:file map;
Run:
-```bash
+```sh
$ checkmodule -M -m -o rustdesk.mod rustdesk.te && semodule_package -o rustdesk.pp -m rustdesk.mod && sudo semodule -i rustdesk.pp
$ sudo semodule -l | grep rustdesk
```
-### Create A Type "rustdesk_t"
+#### Create a type `rustdesk_t`
-1. Create a new directory. `mkdir rustdesk-selinux-1.0`.
-2. Create SELinux policy files. `touch Makefile rustdesk.te rustdesk.fc rustdesk.if`.
+1. Create a new directory: `mkdir rustdesk-selinux-1.0`.
+2. Create SELinux policy files: `touch Makefile rustdesk.te rustdesk.fc rustdesk.if`.
```text
.
@@ -129,15 +129,15 @@ $ sudo semodule -l | grep rustdesk
`rustdesk.te` is the main policy file.
In this example, this file mainly comes from 3 parts:
-1. [`init.te`](https://github.com/fedora-selinux/selinux-policy/blob/rawhide/policy/modules/system/init.te) in github’s selinux-policy repository.
+1. [`init.te`](https://github.com/fedora-selinux/selinux-policy/blob/rawhide/policy/modules/system/init.te) in GitHub’s selinux-policy repository.
2. Audit log, `grep rustdesk /var/log/audit/audit.log | audit2allow -a -M test`.
3. The test system's `init_t` policy, `sesearch -A | grep 'allow init_t ' | sed 's/allow init_t /allow rustdesk_t /g'`.
-Some policies are duplicates and some are redundant, but this is ok since it works on rustdesk_t.
+Some policies are duplicates and some are redundant, but this is ok since it works on `rustdesk_t`.
The contents of each file are as follows.
-rustdes.te:
+`rustdesk.te`:
```text
@@ -541,7 +541,7 @@ gen_require(`
###############################################################################
#
-# Part 1. The following rules are mainly from the opensource `init.te`
+# Part 1. The following rules are mainly from the open source `init.te`
# https://github.com/fedora-selinux/selinux-policy/blob/rawhide/policy/modules/system/init.te
#
# Note: Part 1 will probably be mostly the same as Part 3. But it's acceptable for now.
@@ -831,7 +831,7 @@ allow rustdesk_t self:unix_dgram_socket { create_socket_perms sendto };
allow rustdesk_t self:process { setkeycreate setsockcreate setfscreate setrlimit setexec };
allow rustdesk_t self:process { getcap setcap };
allow rustdesk_t self:unix_stream_socket { create_stream_socket_perms connectto recvfrom };
-allow rustdesk_t self:netlink_kobject_uevent_socket create_socket_perms;
+allow rustdesk_t self:netlink_kobject_uevent_socket create_socket_perms;
allow rustdesk_t self:netlink_selinux_socket create_socket_perms;
allow rustdesk_t self:unix_dgram_socket lock;
# Until systemd is fixed
@@ -1074,7 +1074,7 @@ allow rustdesk_t amanda_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t antivirus_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t apcupsd_power_t:file { ioctl lock open read };
allow rustdesk_t auditd_etc_t:dir { add_name remove_name write };
-allow rustdesk_t auditd_etc_t:file { append create ioctl link lock open read rename setattr unlink watch watch_reads write };
+allow rustdesk_t auditd_etc_t:file { append create ioctl link lock open read rename setattr unlink watch watch_reads write };
allow rustdesk_t autofs_device_t:chr_file { append ioctl lock open read write };
allow rustdesk_t base_ro_file_type:file { execute execute_no_trans map };
allow rustdesk_t binfmt_misc_fs_t:file { append ioctl lock open read write };
@@ -1082,7 +1082,7 @@ allow rustdesk_t bitlbee_exec_t:file ioctl;
allow rustdesk_t bitlbee_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t boltd_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
allow rustdesk_t boltd_var_lib_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t boltd_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
+allow rustdesk_t boltd_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
allow rustdesk_t boltd_var_lib_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
allow rustdesk_t boltd_var_run_t:dir mounton;
allow rustdesk_t boolean_type:dir { getattr ioctl lock open read search };
@@ -1120,14 +1120,14 @@ allow rustdesk_t configfile:file { ioctl lock open read };
allow rustdesk_t configfile:lnk_file read;
allow rustdesk_t console_device_t:chr_file { read watch watch_reads };
allow rustdesk_t consolekit_log_t:dir { add_name remove_name write };
-allow rustdesk_t consolekit_log_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
+allow rustdesk_t consolekit_log_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
allow rustdesk_t container_kvm_t:dbus send_msg;
allow rustdesk_t container_runtime_domain:dbus send_msg;
allow rustdesk_t container_runtime_tmpfs_t:file { ioctl lock open read };
allow rustdesk_t container_runtime_tmpfs_t:lnk_file read;
allow rustdesk_t container_var_lib_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t container_var_lib_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t container_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
+allow rustdesk_t container_var_lib_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
+allow rustdesk_t container_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
allow rustdesk_t crack_t:dbus send_msg;
allow rustdesk_t cups_brf_t:dbus send_msg;
allow rustdesk_t cupsd_exec_t:file ioctl;
@@ -1139,7 +1139,7 @@ allow rustdesk_t cvs_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t daemon:fifo_file { append getattr ioctl lock open write };
allow rustdesk_t daemon:process siginh;
allow rustdesk_t daemon:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t daemon:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
+allow rustdesk_t daemon:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
allow rustdesk_t daemon:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
allow rustdesk_t daemon:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
allow rustdesk_t dbskkd_exec_t:file { execute ioctl map open read };
@@ -1178,14 +1178,14 @@ allow rustdesk_t dri_device_t:chr_file { append ioctl lock map open read write }
allow rustdesk_t dspam_script_t:dbus send_msg;
allow rustdesk_t efivarfs_t:file { ioctl lock open read setattr };
allow rustdesk_t etc_aliases_t:dir { add_name remove_name write };
-allow rustdesk_t etc_aliases_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
+allow rustdesk_t etc_aliases_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
allow rustdesk_t etc_aliases_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
-allow rustdesk_t etc_runtime_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
+allow rustdesk_t etc_runtime_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
allow rustdesk_t etc_runtime_t:file { append create link rename setattr unlink watch_reads write };
-allow rustdesk_t etc_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
+allow rustdesk_t etc_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
allow rustdesk_t etc_t:dir { create link mounton rename reparent rmdir setattr unlink watch_reads };
allow rustdesk_t etc_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t faillog_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
+allow rustdesk_t faillog_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
allow rustdesk_t faillog_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
allow rustdesk_t faillog_t:file { create link open read rename setattr unlink watch_reads write };
allow rustdesk_t fetchmail_t:dbus send_msg;
@@ -1223,8 +1223,8 @@ allow rustdesk_t getty_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t gitd_exec_t:file ioctl;
allow rustdesk_t git_system_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t gnome_home_type:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t gnome_home_type:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t gnome_home_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
+allow rustdesk_t gnome_home_type:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
+allow rustdesk_t gnome_home_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
allow rustdesk_t gnome_home_type:sock_file { append create ioctl link lock open read rename setattr unlink write };
allow rustdesk_t gnomesystemmm_t:dbus send_msg;
allow rustdesk_t guest_t:dbus send_msg;
@@ -1256,7 +1256,7 @@ allow rustdesk_t init_script_file_type:file { execute ioctl map open read };
allow rustdesk_t init_script_file_type:service { disable enable reload start status stop };
allow rustdesk_t init_t:association sendto;
allow rustdesk_t init_t:bpf { map_create map_read map_write prog_load prog_run };
-allow rustdesk_t init_t:capability2 { audit_read block_suspend bpf checkpoint_restore epolwakeup perfmon syslog wake_alarm };
+allow rustdesk_t init_t:capability2 { audit_read block_suspend bpf checkpoint_restore epolwakeup perfmon syslog wake_alarm };
allow rustdesk_t init_t:capability { audit_write audit_control sys_module chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
allow rustdesk_t init_t:cap_userns { audit_control audit_write chown dac_override dac_read_search fowner fsetid ipc_lock ipc_owner kill lease linux_immutable mknod net_admin net_bind_service net_broadcast net_raw setfcap setgid setpcap setuid sys_admin sys_boot sys_chroot sys_module sys_nice sys_pacct sys_ptrace sys_rawio sys_resource sys_time sys_tty_config };
allow rustdesk_t init_t:dir watch;
@@ -1265,7 +1265,7 @@ allow rustdesk_t init_t:file { append mounton write };
allow rustdesk_t init_t:key { create read setattr view write };
allow rustdesk_t init_t:lnk_file { ioctl lock };
allow rustdesk_t init_t:lockdown { confidentiality integrity };
-allow rustdesk_t init_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
+allow rustdesk_t init_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
allow rustdesk_t init_tmp_t:file { create link map open rename setattr unlink watch_reads write };
allow rustdesk_t init_tmp_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
allow rustdesk_t init_tmp_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
@@ -1281,14 +1281,14 @@ allow rustdesk_t init_t:service { disable enable reload start status stop };
allow rustdesk_t init_t:shm { associate create destroy getattr lock read setattr unix_read unix_write write };
allow rustdesk_t init_t:system { disable enable halt ipc_info module_load module_request reboot reload start status stop syslog_console syslog_mod syslog_read undefined };
allow rustdesk_t init_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
-allow rustdesk_t init_t:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
+allow rustdesk_t init_t:udp_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
allow rustdesk_t init_t:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read sendto setattr setopt shutdown write };
allow rustdesk_t init_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read recvfrom sendto setattr setopt shutdown write };
allow rustdesk_t init_t:user_namespace create;
allow rustdesk_t init_var_lib_t:dir { add_name create link mounton remove_name rename reparent rmdir setattr unlink watch_reads write };
allow rustdesk_t init_var_lib_t:dir { create link mounton rename reparent rmdir setattr unlink watch_reads };
-allow rustdesk_t init_var_lib_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
-allow rustdesk_t init_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
+allow rustdesk_t init_var_lib_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
+allow rustdesk_t init_var_lib_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
allow rustdesk_t init_var_lib_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
allow rustdesk_t init_var_run_t:blk_file { append create ioctl link lock open read rename setattr unlink write };
allow rustdesk_t init_var_run_t:chr_file { append create ioctl link lock open read rename setattr unlink write };
@@ -1321,7 +1321,7 @@ allow rustdesk_t kernel_t:fd use;
allow rustdesk_t kernel_t:fifo_file { append getattr ioctl lock read write };
allow rustdesk_t kernel_t:system ipc_info;
allow rustdesk_t kernel_t:unix_dgram_socket { getattr ioctl read write };
-allow rustdesk_t kernel_t:unix_stream_socket { append bind connect getopt ioctl lock read setattr setopt shutdown write };
+allow rustdesk_t kernel_t:unix_stream_socket { append bind connect getopt ioctl lock read setattr setopt shutdown write };
allow rustdesk_t kmod_exec_t:file ioctl;
allow rustdesk_t kmod_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t kmscon_t:dbus send_msg;
@@ -1335,10 +1335,10 @@ allow rustdesk_t lastlog_t:file { open read setattr write };
allow rustdesk_t ld_so_cache_t:file { append write };
allow rustdesk_t lldpad_t:dbus send_msg;
allow rustdesk_t loadkeys_t:dbus send_msg;
-allow rustdesk_t locale_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
+allow rustdesk_t locale_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
allow rustdesk_t locale_t:file { append create link rename setattr unlink watch_reads write };
allow rustdesk_t locale_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
-allow rustdesk_t lockfile:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
+allow rustdesk_t lockfile:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
allow rustdesk_t lockfile:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
allow rustdesk_t lockfile:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
allow rustdesk_t login_userdomain:process2 nnp_transition;
@@ -1408,7 +1408,7 @@ allow rustdesk_t passwd_file_t:file { append create link rename setattr unlink w
allow rustdesk_t pcscd_t:unix_stream_socket connectto;
allow rustdesk_t pdns_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t pegasus_openlmi_domain:dbus send_msg;
-allow rustdesk_t pidfile:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
+allow rustdesk_t pidfile:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
allow rustdesk_t pidfile:fifo_file { create open unlink };
allow rustdesk_t pidfile:file { ioctl lock map open read unlink };
allow rustdesk_t pidfile:lnk_file read;
@@ -1422,9 +1422,9 @@ allow rustdesk_t policykit_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t port_type:tcp_socket name_bind;
allow rustdesk_t port_type:udp_socket name_bind;
allow rustdesk_t postfix_exec_t:file { execute execute_no_trans ioctl lock map open read };
-allow rustdesk_t print_spool_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
+allow rustdesk_t print_spool_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
allow rustdesk_t print_spool_t:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t print_spool_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
+allow rustdesk_t print_spool_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
allow rustdesk_t print_spool_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
allow rustdesk_t proc_net_t:lnk_file { getattr read };
allow rustdesk_t proc_security_t:file { append write };
@@ -1443,7 +1443,7 @@ allow rustdesk_t quota_t:process transition;
allow rustdesk_t quota_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen lock read setattr setopt shutdown write };
allow rustdesk_t radiusd_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t random_device_t:chr_file { ioctl lock open read };
-allow rustdesk_t random_seed_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
+allow rustdesk_t random_seed_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
allow rustdesk_t rdisc_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t rhsmcertd_t:dbus send_msg;
allow rustdesk_t rlogind_exec_t:file ioctl;
@@ -1478,7 +1478,7 @@ allow rustdesk_t rustdesk_t:lnk_file { ioctl lock };
allow rustdesk_t rustdesk_t:lockdown { confidentiality integrity };
allow rustdesk_t rustdesk_t:netlink_audit_socket { append bind connect create lock nlmsg_read nlmsg_relay nlmsg_tty_audit setattr shutdown };
allow rustdesk_t rustdesk_t:netlink_kobject_uevent_socket { append bind connect create lock setattr shutdown };
-allow rustdesk_t rustdesk_t:netlink_route_socket { append bind connect create lock nlmsg_read nlmsg_write setattr shutdown };
+allow rustdesk_t rustdesk_t:netlink_route_socket { append bind connect create lock nlmsg_read nlmsg_write setattr shutdown };
allow rustdesk_t rustdesk_t:netlink_selinux_socket { append bind connect create lock setattr shutdown };
allow rustdesk_t rustdesk_t:packet_socket { append bind connect create lock setattr shutdown };
allow rustdesk_t rustdesk_t:peer recv;
@@ -1491,7 +1491,7 @@ allow rustdesk_t rustdesk_t:unix_stream_socket { connectto recvfrom };
allow rustdesk_t rustdesk_t:user_namespace create;
allow rustdesk_t sblim_domain:dbus send_msg;
allow rustdesk_t security_t:file map;
-allow rustdesk_t security_t:security { check_context compute_av compute_create compute_relabel compute_user load_policy };
+allow rustdesk_t security_t:security { check_context compute_av compute_create compute_relabel compute_user load_policy };
allow rustdesk_t selinux_config_t:file { ioctl lock open read };
allow rustdesk_t selinux_config_t:lnk_file read;
allow rustdesk_t selinux_login_config_t:file { ioctl lock open read };
@@ -1521,8 +1521,8 @@ allow rustdesk_t svc_start_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t svirt_file_type:chr_file { append create ioctl link lock open read rename setattr unlink write };
allow rustdesk_t svirt_file_type:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
allow rustdesk_t svirt_file_type:fifo_file { append create ioctl link lock open read rename setattr unlink write };
-allow rustdesk_t svirt_file_type:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t svirt_file_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
+allow rustdesk_t svirt_file_type:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
+allow rustdesk_t svirt_file_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
allow rustdesk_t svirt_sandbox_domain:process transition;
allow rustdesk_t svirt_sandbox_domain:unix_dgram_socket sendto;
allow rustdesk_t svirt_tcg_t:dbus send_msg;
@@ -1546,8 +1546,8 @@ allow rustdesk_t system_dbusd_var_run_t:sock_file { read watch };
allow rustdesk_t systemd_coredump_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t systemd_gpt_generator_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t systemd_home_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
-allow rustdesk_t systemd_home_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
-allow rustdesk_t systemd_home_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
+allow rustdesk_t systemd_home_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
+allow rustdesk_t systemd_home_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
allow rustdesk_t systemd_hostnamed_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t systemd_hwdb_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t systemd_importd_t:process2 { nnp_transition nosuid_transition };
@@ -1601,7 +1601,7 @@ allow rustdesk_t systemd_unit_file_type:dir { add_name create link remove_name r
allow rustdesk_t systemd_unit_file_type:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
allow rustdesk_t systemd_unit_file_type:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
allow rustdesk_t systemd_unit_file_type:service { disable enable reload start status stop };
-allow rustdesk_t systemd_userdbd_runtime_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
+allow rustdesk_t systemd_userdbd_runtime_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
allow rustdesk_t systemd_userdbd_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t systemprocess:process { dyntransition siginh };
allow rustdesk_t systemprocess:unix_dgram_socket { append bind connect create getattr getopt ioctl lock read setattr setopt shutdown write };
@@ -1657,7 +1657,7 @@ allow rustdesk_t userdomain:unix_stream_socket connectto;
allow rustdesk_t user_home_dir_t:lnk_file read;
allow rustdesk_t user_home_t:file unlink;
allow rustdesk_t user_t:fd use;
-allow rustdesk_t user_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
+allow rustdesk_t user_tmp_t:dir { add_name create link remove_name rename reparent rmdir setattr unlink watch_reads write };
allow rustdesk_t user_tmp_t:dir { create link rename reparent rmdir setattr unlink watch_reads };
allow rustdesk_t user_tmp_t:sock_file { append create ioctl link lock open read rename setattr unlink write };
allow rustdesk_t user_tty_device_t:chr_file { open watch watch_reads };
@@ -1668,14 +1668,14 @@ allow rustdesk_t uuidd_t:process2 { nnp_transition nosuid_transition };
allow rustdesk_t uuidd_var_run_t:fifo_file { append ioctl link lock read rename setattr write };
allow rustdesk_t uuidd_var_run_t:lnk_file { append create ioctl link lock rename setattr unlink watch_reads write };
allow rustdesk_t uuidd_var_run_t:sock_file { ioctl link lock read rename };
-allow rustdesk_t var_lib_nfs_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
+allow rustdesk_t var_lib_nfs_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
allow rustdesk_t var_lib_t:dir { add_name create remove_name setattr write };
allow rustdesk_t var_lib_t:dir { create setattr };
allow rustdesk_t var_lib_t:file { append create ioctl link lock open read rename setattr unlink watch_reads write };
allow rustdesk_t var_lib_t:lnk_file { create read write };
allow rustdesk_t var_log_t:dir { add_name create remove_name setattr write };
allow rustdesk_t var_log_t:dir { create setattr };
-allow rustdesk_t var_log_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
+allow rustdesk_t var_log_t:file { append create ioctl link lock map open read rename setattr unlink watch_reads write };
allow rustdesk_t var_log_t:file { create link map open read rename setattr unlink watch_reads write };
allow rustdesk_t var_log_t:lnk_file { append create ioctl link lock read rename setattr unlink watch_reads write };
allow rustdesk_t var_run_t:file { append execute execute_no_trans write };
@@ -1710,21 +1710,21 @@ allow rustdesk_t xserver_t:unix_stream_socket connectto;
```
-rustdesk.fc:
+`rustdesk.fc`:
```text
/usr/bin/rustdesk -- gen_context(system_u:object_r:rustdesk_exec_t,s0)
```
-rustdesk.if:
+`rustdesk.if`:
```text
## RustDesk
```
-Makefile:
+`Makefile`:
```makefile
@@ -1758,9 +1758,9 @@ install: man
```
-#### Enable Directly
+##### Enable directly
-View the security context of rustdesk before modification:
+View the security context of RustDesk before modification:
```sh
$ ls -lZ /usr/lib/rustdesk/rustdesk
@@ -1792,14 +1792,14 @@ $ ps -eZ | grep rustdesk
system_u:system_r:rustdesk_t:s0 110565 ? 00:00:00 rustdesk
```
-#### Enable through rpm installation
+##### Enable through rpm installation
You can use the `sepolicy generate` command:
-```bash
+```sh
$ # install deps
$ sudo dnf install -y rpm rpm-build binutils
-$ # generate
+$ # generate
$ sepolicy generate --init /usr/lib/rustdesk/rustdesk
$ tree
.
@@ -1819,9 +1819,9 @@ $ # restart the service
$ sudo systemctl restart rustdesk
```
-## Troubleshooting
+### Troubleshooting
-### Iteratively Add Policies
+#### Iteratively Add Policies
```sh
$ cd /tmp
@@ -1831,8 +1831,9 @@ $ # merge rustdesk_tmp.te to rustdesk.te
$ make clean && make && sudo make install-policy
```
-## References
+### References
+
+- [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials)
+- [SELinux Policy module installation](https://fedoraproject.org/wiki/SELinux/IndependentPolicy#SELinux_Policy_module_installation)
+- [How to create SELinux custom policy rpm package](https://lukas-vrabec.com/index.php/2015/07/07/how-to-create-selinux-custom-policy-rpm-package/)
-1. [SELinux/Tutorials](https://wiki.gentoo.org/wiki/SELinux/Tutorials)
-1. [SELinux_Policy_module_installation](https://fedoraproject.org/wiki/SELinux/IndependentPolicy#SELinux_Policy_module_installation)
-1. [how-to-create-selinux-custom-policy-rpm-package](https://lukas-vrabec.com/index.php/2015/07/07/how-to-create-selinux-custom-policy-rpm-package/)
diff --git a/content/client/linux/_index.en.md b/content/client/linux/_index.en.md
index de9b23b..d3edfb2 100755
--- a/content/client/linux/_index.en.md
+++ b/content/client/linux/_index.en.md
@@ -18,7 +18,7 @@ sudo apt install -fy ./rustdesk-.deb
sudo yum localinstall ./rustdesk-.rpm
```
-#### Arch/Manjaro
+#### Arch Linux/Manjaro
```sh
sudo pacman -U ./rustdesk-.pkg.tar.zst
@@ -39,11 +39,11 @@ RustDesk now has experimental Wayland support since v1.2.0.
[Ubuntu](https://askubuntu.com/questions/1260142/ubuntu-set-default-login-desktop) |
[Fedora](https://docs.fedoraproject.org/en-US/quick-docs/configuring-xorg-as-default-gnome-session/) |
-[Arch](https://bbs.archlinux.org/viewtopic.php?id=218319)
+[Arch Linux](https://bbs.archlinux.org/viewtopic.php?id=218319)
#### Login Screen
-Login screen using Wayland is not supporte yet. If you wanna access login screen after reboot or logout with RustDesk, you need to change login screen to X11, please modify below line to `WaylandEnable=false` in `/etc/gdm/custom.conf` or `/etc/gdm3/custom.conf`:
+Login screen using Wayland is not supported yet. If you wanna access login screen after reboot or logout with RustDesk, you need to change login screen to X11, please modify below line to `WaylandEnable=false` in `/etc/gdm/custom.conf` or `/etc/gdm3/custom.conf`:
```ini
#WaylandEnable=false
@@ -59,11 +59,14 @@ If SELinux is enabled, RustDesk will not work properly in either X11 or Wayland
You can run:
-```bash
+```sh
$ sudo grep 'comm="rustdesk"' /var/log/audit/audit.log | tail -1
type=AVC msg=audit(1697902459.165:707): avc: denied { name_connect } for pid=31346 comm="rustdesk" dest=53330 scontext=system_u:system_r:init_t:s0 tcontext=system_u:object_r:ephemeral_port_t:s0 tclass=tcp_socket permissive=0
```
-**NOTE**: The number in parentheses after audit is timestamp.
+{{% notice note %}}
+The number in parentheses after `audit` is timestamp.
+{{% /notice %}}
+
+If the output contains `avc: denied`, you need to add SELinux policies, please refer to [SELinux](https://rustdesk.com/docs/en/client/linux/selinux/).
-If the output contains `avc: denied`, you need to add SElinux policies, please refer to [SELinux](./selinux/).
diff --git a/content/dev/build/android/_index.en.md b/content/dev/build/android/_index.en.md
index cd5ae47..c94b608 100644
--- a/content/dev/build/android/_index.en.md
+++ b/content/dev/build/android/_index.en.md
@@ -110,8 +110,7 @@ sudo tar xzf dep.tar.gz
popd
```
-##### Warning
-It requires vcpkg directory to be at `$HOME`, if `Building rustdesk lib` part of this instruction will throw errors like:
+**Warning:** It requires vcpkg directory to be at `$HOME`, if `Building rustdesk lib` part of this instruction will throw errors like:
```yaml
error: failed to run custom build command for `magnum-opus v0.4.0 (https://github.com/rustdesk/magnum-opus#79be072c)`
diff --git a/content/dev/build/linux/_index.en.md b/content/dev/build/linux/_index.en.md
index f810602..27cf27f 100644
--- a/content/dev/build/linux/_index.en.md
+++ b/content/dev/build/linux/_index.en.md
@@ -36,7 +36,7 @@ sudo apt install -y g++ gcc git curl wget nasm yasm libgtk-3-dev clang libxcb-ra
sudo yum -y install gcc-c++ git curl wget nasm yasm gcc gtk3-devel clang libxcb-devel libxdo-devel libXfixes-devel pulseaudio-libs-devel cmake alsa-lib-devel
```
-#### Arch (Manjaro)
+#### Arch Linux (Manjaro)
```sh
sudo pacman -Syu --needed unzip git cmake gcc curl wget yasm nasm zip make pkg-config clang gtk3 xdotool libxcb libxfixes alsa-lib pulseaudio
diff --git a/content/self-host/client-deployment/_index.en.md b/content/self-host/client-deployment/_index.en.md
index 38fdda6..896a119 100644
--- a/content/self-host/client-deployment/_index.en.md
+++ b/content/self-host/client-deployment/_index.en.md
@@ -35,7 +35,7 @@ if (-Not ([Security.Principal.WindowsPrincipal][Security.Principal.WindowsIdenti
$rdver = ((Get-ItemProperty "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RustDesk\").Version)
-if ($rdver -eq "1.2.2")
+if ($rdver -eq "1.2.3")
{
Write-Output "RustDesk $rdver is the newest version"
Exit
@@ -48,7 +48,7 @@ if (!(Test-Path C:\Temp))
cd C:\Temp
-Invoke-WebRequest "https://github.com/rustdesk/rustdesk/releases/download/1.2.2/rustdesk-1.2.2-x86_64.exe" -Outfile "rustdesk.exe"
+Invoke-WebRequest "https://github.com/rustdesk/rustdesk/releases/download/1.2.3/rustdesk-1.2.3-x86_64.exe" -Outfile "rustdesk.exe"
Start-Process .\rustdesk.exe --silent-install -wait
$ServiceName = 'Rustdesk'
@@ -109,7 +109,7 @@ REM ############################### Please Do Not Edit Below This Line #########
if not exist C:\Temp\ md C:\Temp\
cd C:\Temp\
-curl -L "https://github.com/rustdesk/rustdesk/releases/download/1.2.2/rustdesk-1.2.2-x86_64.exe" -o rustdesk.exe
+curl -L "https://github.com/rustdesk/rustdesk/releases/download/1.2.3/rustdesk-1.2.3-x86_64.exe" -o rustdesk.exe
rustdesk.exe --silent-install
timeout /t 20
@@ -153,7 +153,7 @@ if [[ $EUID -ne 0 ]]; then
fi
# Specify the path to the rustdesk.dmg file
-dmg_file="/tmp/rustdesk-1.2.2-x86_64.dmg"
+dmg_file="/tmp/rustdesk-1.2.3-x86_64.dmg"
# Specify the mount point for the DMG (temporary directory)
mount_point="/Volumes/RustDesk"
@@ -162,9 +162,9 @@ mount_point="/Volumes/RustDesk"
echo "Downloading RustDesk Now"
if [[ $(arch) == 'arm64' ]]; then
- curl -L https://github.com/rustdesk/rustdesk/releases/download/1.2.2/rustdesk-1.2.2-aarch64.dmg --output "$dmg_file"
+ curl -L https://github.com/rustdesk/rustdesk/releases/download/1.2.3/rustdesk-1.2.3-aarch64.dmg --output "$dmg_file"
else
- curl -L https://github.com/rustdesk/rustdesk/releases/download/1.2.2/rustdesk-1.2.2-x86_64.dmg --output "$dmg_file"
+ curl -L https://github.com/rustdesk/rustdesk/releases/download/1.2.3/rustdesk-1.2.3-x86_64.dmg --output "$dmg_file"
fi
# Mount the DMG file to the specified mount point
@@ -276,11 +276,11 @@ fi
echo "Installing RustDesk"
if [ "${ID}" = "debian" ] || [ "$OS" = "Ubuntu" ] || [ "$OS" = "Debian" ] || [ "${UPSTREAM_ID}" = "ubuntu" ] || [ "${UPSTREAM_ID}" = "debian" ]; then
- wget https://github.com/rustdesk/rustdesk/releases/download/1.2.2/rustdesk-1.2.2-x86_64.deb
- apt-get install -fy ./rustdesk-1.2.2-x86_64.deb > null
+ wget https://github.com/rustdesk/rustdesk/releases/download/1.2.3/rustdesk-1.2.3-x86_64.deb
+ apt-get install -fy ./rustdesk-1.2.3-x86_64.deb > null
elif [ "$OS" = "CentOS" ] || [ "$OS" = "RedHat" ] || [ "$OS" = "Fedora Linux" ] || [ "${UPSTREAM_ID}" = "rhel" ] || [ "$OS" = "Almalinux" ] || [ "$OS" = "Rocky*" ] ; then
- wget https://github.com/rustdesk/rustdesk/releases/download/1.2.2/rustdesk-1.2.2-0.x86_64.rpm
- yum localinstall ./rustdesk-1.2.2-0.x86_64.rpm -y > null
+ wget https://github.com/rustdesk/rustdesk/releases/download/1.2.3/rustdesk-1.2.3-0.x86_64.rpm
+ yum localinstall ./rustdesk-1.2.3-0.x86_64.rpm -y > null
else
echo "Unsupported OS"
# here you could ask the user for permission to try and install anyway
@@ -311,3 +311,4 @@ fi
echo "Password: $rustdesk_pw"
echo "..............................................."
```
+
diff --git a/content/self-host/client-deployment/integrations/tactical-rmm/_index.en.md b/content/self-host/client-deployment/integrations/tactical-rmm/_index.en.md
index d2e27d8..d74987f 100644
--- a/content/self-host/client-deployment/integrations/tactical-rmm/_index.en.md
+++ b/content/self-host/client-deployment/integrations/tactical-rmm/_index.en.md
@@ -23,7 +23,7 @@ if (!(Test-Path C:\Temp))
cd C:\Temp
-Invoke-WebRequest "https://github.com/rustdesk/rustdesk/releases/download/1.2.2/rustdesk-1.2.2-x86_64.exe" -Outfile "rustdesk.exe"
+Invoke-WebRequest "https://github.com/rustdesk/rustdesk/releases/download/1.2.3/rustdesk-1.2.3-x86_64.exe" -Outfile "rustdesk.exe"
Start-Process .\rustdesk.exe --silent-install -wait
$ServiceName = 'Rustdesk'
diff --git a/content/self-host/rustdesk-server-oss/install/_index.en.md b/content/self-host/rustdesk-server-oss/install/_index.en.md
index e6ccd97..0d1105d 100644
--- a/content/self-host/rustdesk-server-oss/install/_index.en.md
+++ b/content/self-host/rustdesk-server-oss/install/_index.en.md
@@ -70,7 +70,7 @@ We suggest you use [PM2](https://pm2.keymetrics.io/) for managing your service.
##### Option 1
Run hbbs/hbbr without PM2.
-```bash
+```sh
./hbbs -r
./hbbr
```
@@ -78,7 +78,7 @@ Run hbbs/hbbr without PM2.
##### Option 2
Run hbbs/hbbr with PM2.
-```bash
+```sh
pm2 start hbbs -- -r
pm2 start hbbr
```
@@ -140,13 +140,13 @@ Different from the old version, the key in this version is mandatory, but you do
If you did not fill in the `Key:` (the content in the public key file `id_ed25519.pub`) in the previous step, it does not affect the connection, but the connection cannot be encrypted.
-```bash
+```sh
cat ./id_ed25519.pub
```
If you want to prohibit users without the key from establishing non-encrypted connections, please add the `-k _` parameter when running `hbbs` and `hbbr`, for example:
-```bash
+```sh
./hbbs -r -k _
./hbbr -k _
```
diff --git a/content/self-host/rustdesk-server-pro/FAQ/_index.en.md b/content/self-host/rustdesk-server-pro/FAQ/_index.en.md
index 8476e8b..22a31b7 100644
--- a/content/self-host/rustdesk-server-pro/FAQ/_index.en.md
+++ b/content/self-host/rustdesk-server-pro/FAQ/_index.en.md
@@ -35,7 +35,7 @@ weight: 600
The services use systemd so can be started and stopped using `sudo systemctl stop|start|restart rustdesk-hbbs|rustdesk-hbbr` e.g. `sudo systemctl restart rustdesk-hbbs`.
### I installed with the script, how can I view the Linux logs?
-The logs are stored in /var/log/rustdesk-server, you can view them using `tail /var/log/rustdesk-server/hbbs.log` or `tail /var/log/rustdesk-server/hbbs.error`.
+The logs are stored in `/var/log/rustdesk-server`, you can view them using `tail /var/log/rustdesk-server/hbbs.log` or `tail /var/log/rustdesk-server/hbbs.error`.
### I installed with the script, how can I check the status of the RustDesk services?
To check the status `sudo systemctl status rustdesk-hbbs|rustdesk-hbbr` e.g. `sudo systemctl status rustdesk-hbbs`.
@@ -126,7 +126,7 @@ $ErrorActionPreference= 'silentlycontinue'
$rdver = ((Get-ItemProperty "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\RustDesk\").Version)
-if ($rdver -eq "1.2.2")
+if ($rdver -eq "1.2.3")
{
Write-Output "RustDesk $rdver is the newest version."
Exit
@@ -139,7 +139,7 @@ if (!(Test-Path C:\Temp))
cd C:\Temp
-Invoke-WebRequest "https://github.com/rustdesk/rustdesk/releases/download/1.2.2/rustdesk-1.2.2-x86_64.exe" -Outfile "rustdesk.exe"
+Invoke-WebRequest "https://github.com/rustdesk/rustdesk/releases/download/1.2.3/rustdesk-1.2.3-x86_64.exe" -Outfile "rustdesk.exe"
Start-Process .\rustdesk.exe --silent-install -wait
```
diff --git a/content/self-host/rustdesk-server-pro/console/_index.en.md b/content/self-host/rustdesk-server-pro/console/_index.en.md
index 25f9745..5734281 100644
--- a/content/self-host/rustdesk-server-pro/console/_index.en.md
+++ b/content/self-host/rustdesk-server-pro/console/_index.en.md
@@ -79,7 +79,7 @@ Gmail in this example
8. Click `Check` to save.
### Assign Device Users and Groups to Devices
-The User is the RustDesk User logged in on the device or assigned to the device by clicking `Edit` next to the device, click in the `User` box and drop down to select your user, this will auto assign the group based on the group the user as been assigned to.
+The User is the RustDesk User logged in on the device or assigned to the device by clicking `Edit` next to the device, click in the `User` box and drop-down to select your user, this will auto assign the group based on the group the user as been assigned to.
This can also be done via the API at command line on deployment or later by calling the RustDesk executable followed by `--assign --token --user_name `. You need to go to "Settings -> Tokens -> Create" and create a token with Device permissions first to do this. An example of this on windows would be `"C:\Program Files\RustDesk\rustdesk.exe" --assign --token --user_name `.
diff --git a/content/self-host/rustdesk-server-pro/installscript/Docker/RustDesk Server Layered Security Model/_index.en.md b/content/self-host/rustdesk-server-pro/installscript/Docker/RustDesk Server Layered Security Model/_index.en.md
index 8cb5b07..811131b 100644
--- a/content/self-host/rustdesk-server-pro/installscript/Docker/RustDesk Server Layered Security Model/_index.en.md
+++ b/content/self-host/rustdesk-server-pro/installscript/Docker/RustDesk Server Layered Security Model/_index.en.md
@@ -5,7 +5,7 @@ weight: 100
Kindly written up by [@I-Am-Skoot](https://github.com/I-Am-Skoot/RustDeskNPMDocker/commits?author=I-Am-Skoot).
-## Layers
+### Layers
- [RustDesk](https://github.com/rustdesk/rustdesk) Remote Support Tool
- [NPM](https://nginxproxymanager.com/) Proxy Manager Tool
- [Docker](https://www.docker.com) Containerization Tool
@@ -134,5 +134,5 @@ Configure the client:
- API Server: http://rustdesk.example.com (use HTTPS if you have configured SSL)
- Key: {Server Key Here}
-## End Result
+### End Result
Your solution will be accessible externally through the Proxy manager. You will have isolation of your RustDesk Servers from other systems. Especially if you use a split configuration system and have other applications / sites behind a common NPM.
diff --git a/content/self-host/rustdesk-server-pro/installscript/_index.en.md b/content/self-host/rustdesk-server-pro/installscript/_index.en.md
index 04d3a9f..6c99c33 100644
--- a/content/self-host/rustdesk-server-pro/installscript/_index.en.md
+++ b/content/self-host/rustdesk-server-pro/installscript/_index.en.md
@@ -17,8 +17,8 @@ What it does:
- Install some dependencies
- Setup UFW firewall if available
-- Create a working directory /var/lib/rustdesk-server and a log directory /var/log/rustdesk-server
-- Installs executables into /usr/bin
+- Create a working directory `/var/lib/rustdesk-server` and a log directory `/var/log/rustdesk-server`
+- Installs executables into `/usr/bin`
- Download and extract RustDesk Pro Services to the above folder
- Create systemd services for hbbs and hbbr (service names are rustdesk-hbbs.service and rustdesk-hbbr.service)
- If you choose Domain, it will install Nginx and Certbot, allowing the API to be available on port 443 (HTTPS) and get an SSL certificate over port 80, it is automatically renewed
@@ -45,8 +45,8 @@ What it does:
- Disable and removes the old services
- Install some dependencies
- Setup UFW firewall if available
-- Create a folder /var/lib/rustdesk-server and copy the certs here
-- Delete /var/log/rustdesk and create /var/log/rustdesk-server
+- Create a folder `/var/lib/rustdesk-server` and copy the certs here
+- Delete `/var/log/rustdesk` and create `/var/log/rustdesk-server`
- Download and extract RustDesk Pro Services to the above folder
- Create systemd services for hbbs and hbbr (service names are rustdesk-hbbs.service and rustdesk-hbbr.service)
- If you choose Domain, it will install Nginx and Certbot, allowing the API to be available on port 443 (HTTPS) and get an SSL certificate over port 80, it is automatically renewed
@@ -75,3 +75,4 @@ Copy the backup file into the same folder as the restore.sh file and then run `.
This will restore your server to how it was prior, you will need to revoke your [license](https://rustdesk.com/docs/en/self-host/rustdesk-server-pro/license/) to move it to the restored server.
+
diff --git a/content/self-host/rustdesk-server-pro/license/_index.en.md b/content/self-host/rustdesk-server-pro/license/_index.en.md
index 5bb61ed..c987297 100644
--- a/content/self-host/rustdesk-server-pro/license/_index.en.md
+++ b/content/self-host/rustdesk-server-pro/license/_index.en.md
@@ -3,13 +3,13 @@ title: License
weight: 15
---
-## Buy license
+### Buy license
Please get your license from [https://rustdesk.com/pricing.html](https://rustdesk.com/pricing.html), enter a valid email address in the Stripe checkout page. The license (and the invoice in a separate mail) will be sent to your email once payment is done successfully.

-## Set license
+### Set license
You will be required to enter license in the web console, or change license later.
@@ -17,7 +17,7 @@ You will be required to enter license in the web console, or change license late
| --- | --- |
|  |  |
-## Renew/upgrade license
+### Renew/upgrade license
Renew/upgrade license can be found via the [self-service license portal](https://rustdesk.com/self-host/account/) as described below.
@@ -29,7 +29,7 @@ After payment, you need to proceed to the web console to activate it manually as

-## Invoices, License Retrieval and Migration
+### Invoices, License Retrieval and Migration
The license can be only used on one machine (for hbbs only, hbbr does not require license), if you want to migrate to the other machine, retrieve your license or download invoices, please go to [https://rustdesk.com/self-host/account/](https://rustdesk.com/self-host/account/). Log in with the email address used for Stripe checkout, unbind the old machine you want to migrate from as below, when you set the license in the new servers web console it will assign the license and register automatically in the console.
diff --git a/content/self-host/rustdesk-server-pro/oidc/Azure/_index.en.md b/content/self-host/rustdesk-server-pro/oidc/Azure/_index.en.md
index 889d9a6..492d2b2 100644
--- a/content/self-host/rustdesk-server-pro/oidc/Azure/_index.en.md
+++ b/content/self-host/rustdesk-server-pro/oidc/Azure/_index.en.md
@@ -3,7 +3,7 @@ title: Azure
weight: 16
---
-## Configuration
+### Configuration
1. Sign in to the [Azure portal](https://portal.azure.com).
2. Search for and select **Microsoft Entra ID**.
@@ -32,9 +32,7 @@ weight: 16
13. In Azure, select **Authentication** menu. Then set up authorization, by choosing **ID tokens (used for implicit and hybrid flows)**.

-## Troubleshooting
-
-## References
+### References
- [Set up an OpenID Connect provider with Azure AD](https://learn.microsoft.com/en-us/power-pages/security/authentication/openid-settings)
- [OpenID Connect on the Microsoft identity platform](https://learn.microsoft.com/en-us/azure/active-directory/develop/v2-protocols-oidc)
diff --git a/content/self-host/rustdesk-server-pro/permissions/_index.en.md b/content/self-host/rustdesk-server-pro/permissions/_index.en.md
index 3fcb5bc..2b1c8c3 100644
--- a/content/self-host/rustdesk-server-pro/permissions/_index.en.md
+++ b/content/self-host/rustdesk-server-pro/permissions/_index.en.md
@@ -3,7 +3,7 @@ title: Access Control
weight: 16
---
-## Device access permissions
+### Device access permissions
There are two ways to associate a device with a user:
- Via console device page
@@ -15,7 +15,7 @@ The following two situations will prevent the device from being accessed:
The associated device can only be accessed by the devices of the same user or user group, or in correct cross-group settings.
-## Cross group settings
+### Cross group settings
Please go to group page in the web console, click on `Edit` to edit cross group settings as below.
diff --git a/content/self-host/rustdesk-server-pro/relay/_index.en.md b/content/self-host/rustdesk-server-pro/relay/_index.en.md
index 754d697..be02a68 100644
--- a/content/self-host/rustdesk-server-pro/relay/_index.en.md
+++ b/content/self-host/rustdesk-server-pro/relay/_index.en.md
@@ -3,7 +3,7 @@ title: Configure Relay Servers
weight: 17
---
-## RustDesk Pro - Install Additional Relay Servers with Geo Location using docker
+### RustDesk Pro - Install Additional Relay Servers with Geo Location using docker
You can have several relay servers running across the globe and leverage GeoLocation to use the closest relay server, giving you a faster experience when connecting to remote computers.
@@ -19,7 +19,7 @@ The volume hbbr should be located in `/var/lib/docker/volumes/hbbr/_data`.
2 - Copy the private key pair to the volume location, in this case we will use SCP to copy the files.
-The command syntax is: `scp username@server:`.
+The command syntax is `scp username@server:`.
```
# scp id_ed25519 root@100.100.100.100:/var/lib/docker/volumes/hbbr/_data
@@ -69,14 +69,14 @@ To Action From
21117,21119/tcp (v6) ALLOW Anywhere (v6)
```
-## Configure RustDesk Pro for Geo Location using Web Console
+### Configure RustDesk Pro for Geo Location using Web Console
-### Register and Download the GeoLite2 City database file
+#### Register and Download the GeoLite2 City database file
To use geo location, hbbs needs access to the MaxMind GeoLite2 City database. The database is free and you can register to download the file and get an API key.
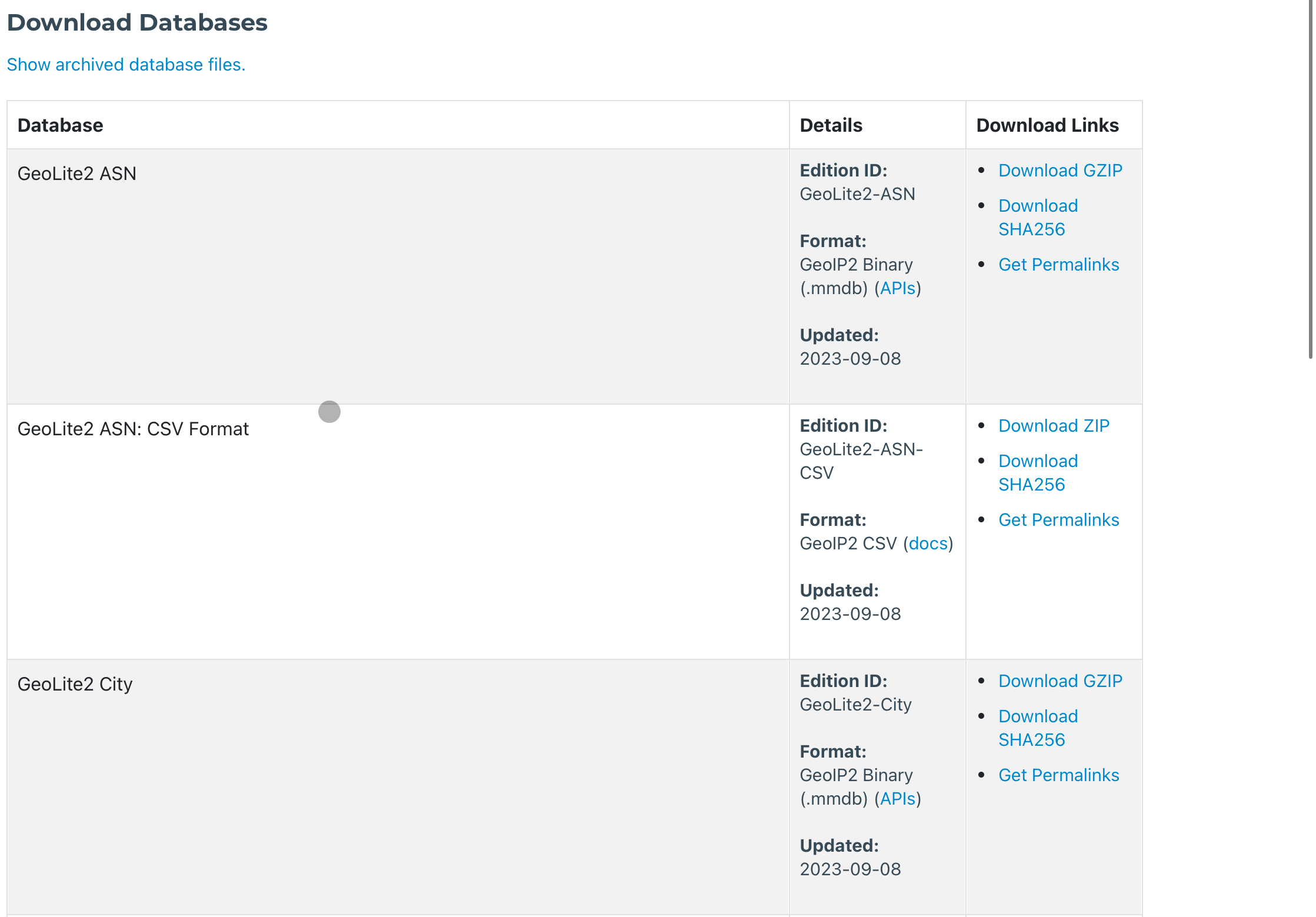
Start by creating an account (if you don’t have one) by going to the [website](https://www.maxmind.com/en/account/login).
-Go to `Download Databases` and download the GeoLite2 City, choose the gzip file and you should have the `mmdb` file when decompressing it.
+Go to `Download Databases` and download GeoLite2 City, choose the gzip file and you should have the `mmdb` file when decompressing it.
 @@ -99,7 +99,7 @@ You can automate the [download process](https://dev.maxmind.com/geoip/updating-d
/usr/bin/curl -L --silent 'https://download.maxmind.com/app/geoip_download?edition_id=GeoLite2-City&license_key={Your Access Key}&suffix=tar.gz' | /bin/tar -C '/var/lib/rustdesk-server/' -xvz --keep-newer-files --strip-components=1 --wildcards '*GeoLite2-City.mmdb'
```
-### Change settings in RustDesk Pro Web Console
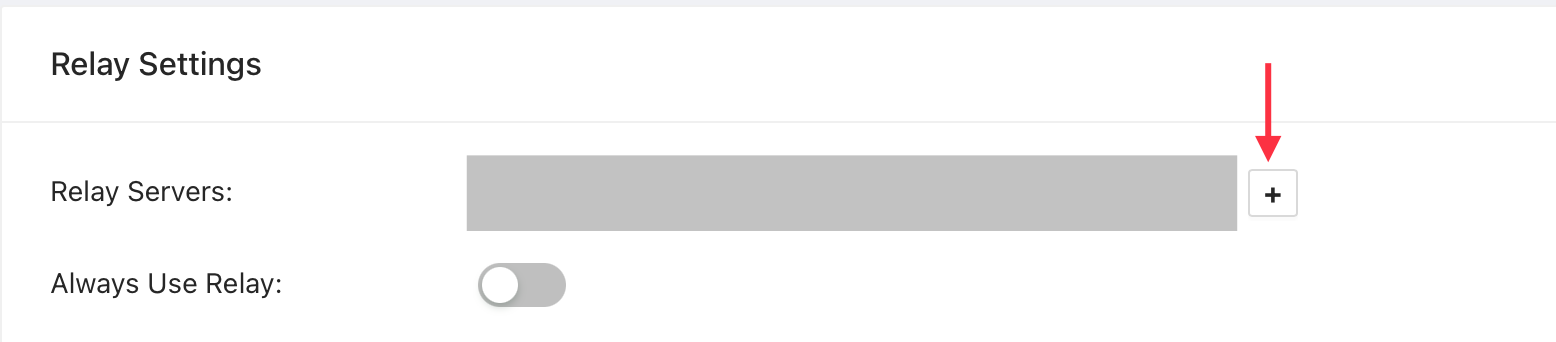
+#### Change settings in RustDesk Pro Web Console
Add your relay server IP addresses to the the Relay Server List, using just the IP address. **Do not add the port.**
@@ -99,7 +99,7 @@ You can automate the [download process](https://dev.maxmind.com/geoip/updating-d
/usr/bin/curl -L --silent 'https://download.maxmind.com/app/geoip_download?edition_id=GeoLite2-City&license_key={Your Access Key}&suffix=tar.gz' | /bin/tar -C '/var/lib/rustdesk-server/' -xvz --keep-newer-files --strip-components=1 --wildcards '*GeoLite2-City.mmdb'
```
-### Change settings in RustDesk Pro Web Console
+#### Change settings in RustDesk Pro Web Console
Add your relay server IP addresses to the the Relay Server List, using just the IP address. **Do not add the port.**
 @@ -134,3 +134,4 @@ You can also confirm the relay requests directly on your hbbr instances, simply
INFO [src/relay_server.rs:436] Relayrequest 0593e64e-4fe8-4a59-a94f-b3420ab043eb from [::ffff:100.100.123.233]:52038 got paired
INFO [src/relay_server.rs:442] Both are raw
```
+
diff --git a/content/self-host/rustdesk-server-pro/strategy/_index.en.md b/content/self-host/rustdesk-server-pro/strategy/_index.en.md
index b2ba698..dde8155 100644
--- a/content/self-host/rustdesk-server-pro/strategy/_index.en.md
+++ b/content/self-host/rustdesk-server-pro/strategy/_index.en.md
@@ -3,11 +3,11 @@ title: Strategy
weight: 200
---
-## Strategy
+### Strategy
Strategy is a tool for RustDesk administrators to update the security options of client settings pages in bulk. Administrators can create different strategies and apply them to different devices.
-### Create Strategies
+#### Create Strategies
You can create a new strategy by clicking the `+` button and perform various actions on the strategy by hovering over it and clicking the menu.
@@ -17,27 +17,27 @@ On the right side of the strategy menu, you can see the number of devices actual

-### Device Strategy and User Strategy
+#### Device Strategy and User Strategy
Each device can only be managed by one strategy, and device strategies take priority over user strategies. User strategies are responsible for managing all devices under the user that are not assigned a specific strategy.
-### Edit Devices
+#### Edit Devices
-When you click the `Edit Devices` menu, an editing dialog box displaying all the devices will open. You can change the selection status of the checkboxes and then click the `Save` button to apply the device changes made on the current page. If you need to modify devices on other pages, please navigate to those pages. You can also use the dropdown menu in the upper right corner to filter devices.
+When you click the `Edit Devices` menu, an editing dialog box displaying all the devices will open. You can change the selection status of the checkboxes and then click the `Save` button to apply the device changes made on the current page. If you need to modify devices on other pages, please navigate to those pages. You can also use the drop-down menu in the upper right corner to filter devices.
Here is an example of the dialog box that appears when you click `Edit Devices` on the "demo2" menu. In this example, the device "362587269" is applied to the "demo2" strategy. The device "157333666" was originally applied to the default strategy but will be applied to the "demo2" strategy after clicking `Save`. The device "232026634" has a device strategy for "demo1" and a user strategy for "demo2", since the device strategy takes priority, this device will be applied to the "demo1" strategy.

-### Edit Users
+#### Edit Users
-When you click the `Edit Users` menu, an editing dialog box displaying all the users will open. You can change the selection status of the checkboxes and then click the `Save` button to apply the user changes made on the current page. If you need to modify users on other pages, please navigate to those pages. You can also use the dropdown menu in the upper right corner to filter users.
+When you click the `Edit Users` menu, an editing dialog box displaying all the users will open. You can change the selection status of the checkboxes and then click the `Save` button to apply the user changes made on the current page. If you need to modify users on other pages, please navigate to those pages. You can also use the drop-down menu in the upper right corner to filter users.
Here is an example of the dialog box that appears when you click `Edit Users` on the "demo2" menu. In this example, the user "user2" was originally applied to the default strategy and will be applied to the "demo2" strategy after clicking `Save`. The user "user1" is applied to the default strategy, and the user "admin" is applied to the "demo2" strategy.

-### Strategy Synchronization
+#### Strategy Synchronization
Each device can only be managed by one strategy, and if that strategy is disabled, the device will not be managed by any strategy. When synchronizing strategies, RustDesk records the local and server strategy timestamps to determine whether synchronization is necessary. That is, after strategy synchronization is complete:
@@ -45,6 +45,7 @@ Each device can only be managed by one strategy, and if that strategy is disable
* If the administrator changes the strategy content, the client's options will be synchronized.
* If the administrator changes the strategy to which the device belongs, the client's options will be synchronized.
-### Edit Strategies
+#### Edit Strategies
At the bottom of the strategy, click `Edit`, make modifications and click `Submit`. The strategy will be synchronized to devices within 30 seconds.
+
@@ -134,3 +134,4 @@ You can also confirm the relay requests directly on your hbbr instances, simply
INFO [src/relay_server.rs:436] Relayrequest 0593e64e-4fe8-4a59-a94f-b3420ab043eb from [::ffff:100.100.123.233]:52038 got paired
INFO [src/relay_server.rs:442] Both are raw
```
+
diff --git a/content/self-host/rustdesk-server-pro/strategy/_index.en.md b/content/self-host/rustdesk-server-pro/strategy/_index.en.md
index b2ba698..dde8155 100644
--- a/content/self-host/rustdesk-server-pro/strategy/_index.en.md
+++ b/content/self-host/rustdesk-server-pro/strategy/_index.en.md
@@ -3,11 +3,11 @@ title: Strategy
weight: 200
---
-## Strategy
+### Strategy
Strategy is a tool for RustDesk administrators to update the security options of client settings pages in bulk. Administrators can create different strategies and apply them to different devices.
-### Create Strategies
+#### Create Strategies
You can create a new strategy by clicking the `+` button and perform various actions on the strategy by hovering over it and clicking the menu.
@@ -17,27 +17,27 @@ On the right side of the strategy menu, you can see the number of devices actual

-### Device Strategy and User Strategy
+#### Device Strategy and User Strategy
Each device can only be managed by one strategy, and device strategies take priority over user strategies. User strategies are responsible for managing all devices under the user that are not assigned a specific strategy.
-### Edit Devices
+#### Edit Devices
-When you click the `Edit Devices` menu, an editing dialog box displaying all the devices will open. You can change the selection status of the checkboxes and then click the `Save` button to apply the device changes made on the current page. If you need to modify devices on other pages, please navigate to those pages. You can also use the dropdown menu in the upper right corner to filter devices.
+When you click the `Edit Devices` menu, an editing dialog box displaying all the devices will open. You can change the selection status of the checkboxes and then click the `Save` button to apply the device changes made on the current page. If you need to modify devices on other pages, please navigate to those pages. You can also use the drop-down menu in the upper right corner to filter devices.
Here is an example of the dialog box that appears when you click `Edit Devices` on the "demo2" menu. In this example, the device "362587269" is applied to the "demo2" strategy. The device "157333666" was originally applied to the default strategy but will be applied to the "demo2" strategy after clicking `Save`. The device "232026634" has a device strategy for "demo1" and a user strategy for "demo2", since the device strategy takes priority, this device will be applied to the "demo1" strategy.

-### Edit Users
+#### Edit Users
-When you click the `Edit Users` menu, an editing dialog box displaying all the users will open. You can change the selection status of the checkboxes and then click the `Save` button to apply the user changes made on the current page. If you need to modify users on other pages, please navigate to those pages. You can also use the dropdown menu in the upper right corner to filter users.
+When you click the `Edit Users` menu, an editing dialog box displaying all the users will open. You can change the selection status of the checkboxes and then click the `Save` button to apply the user changes made on the current page. If you need to modify users on other pages, please navigate to those pages. You can also use the drop-down menu in the upper right corner to filter users.
Here is an example of the dialog box that appears when you click `Edit Users` on the "demo2" menu. In this example, the user "user2" was originally applied to the default strategy and will be applied to the "demo2" strategy after clicking `Save`. The user "user1" is applied to the default strategy, and the user "admin" is applied to the "demo2" strategy.

-### Strategy Synchronization
+#### Strategy Synchronization
Each device can only be managed by one strategy, and if that strategy is disabled, the device will not be managed by any strategy. When synchronizing strategies, RustDesk records the local and server strategy timestamps to determine whether synchronization is necessary. That is, after strategy synchronization is complete:
@@ -45,6 +45,7 @@ Each device can only be managed by one strategy, and if that strategy is disable
* If the administrator changes the strategy content, the client's options will be synchronized.
* If the administrator changes the strategy to which the device belongs, the client's options will be synchronized.
-### Edit Strategies
+#### Edit Strategies
At the bottom of the strategy, click `Edit`, make modifications and click `Submit`. The strategy will be synchronized to devices within 30 seconds.
+